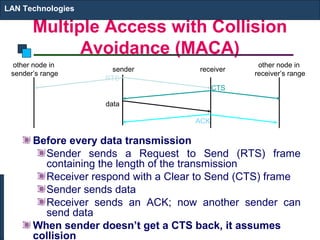
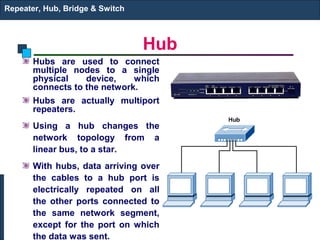
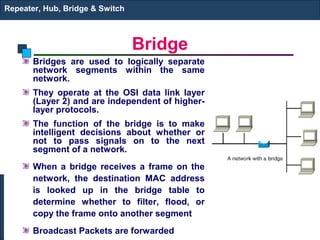
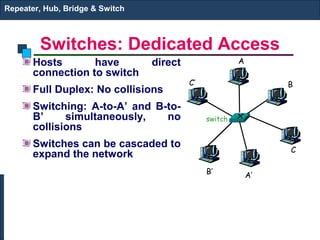
The document discusses various networking devices used to connect and extend local area networks (LANs). It describes repeaters as devices that receive and regenerate signals to allow them to travel longer distances. Hubs are multiport repeaters that connect multiple nodes to a single device. Bridges operate at the data link layer and logically separate network segments. Switches provide dedicated connections and are multiport bridges that separate collision domains for improved performance.