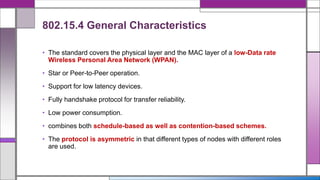
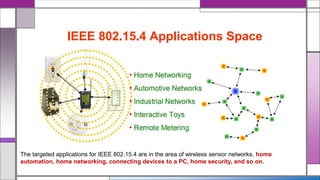
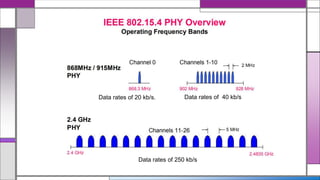
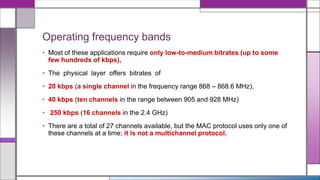
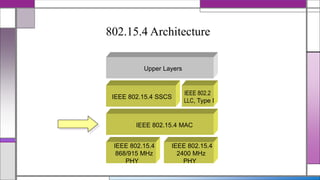
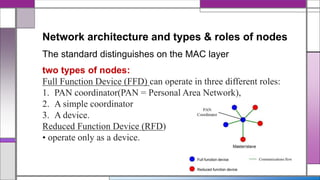
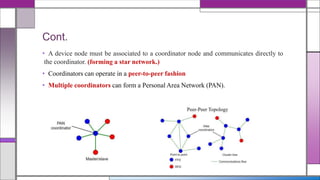
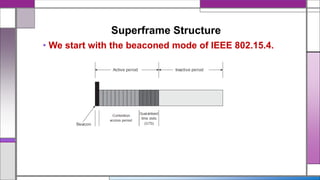
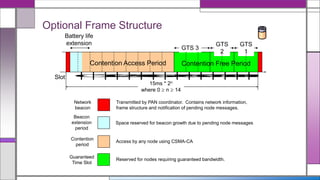
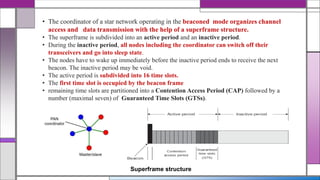
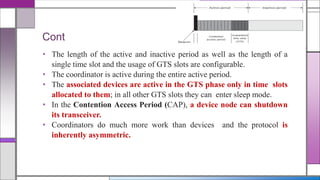
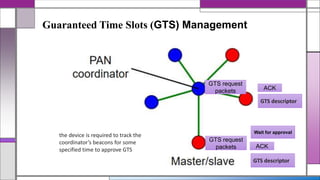
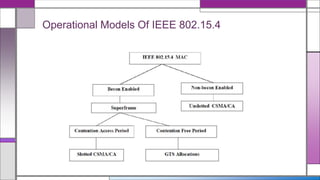
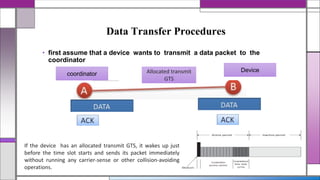
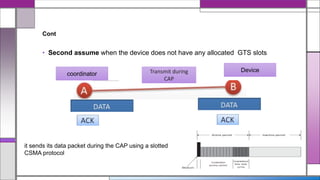
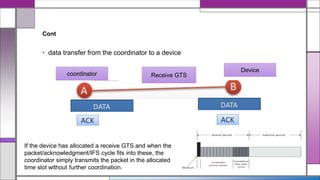
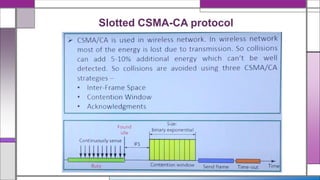
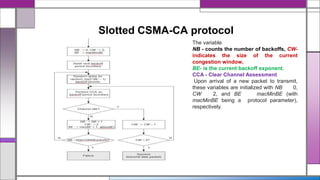
The document discusses the IEEE 802.15.4 MAC protocol, detailing its importance in wireless sensor networks and its roles in coordinating access to communication channels among devices. It outlines different types of MAC protocols, characteristics of IEEE 802.15.4, and the architecture of nodes involved, including full-function and reduced-function devices. Additionally, it explains the protocol's data transfer procedures and superframe structure used for efficient communication in low-power, low-data rate applications.