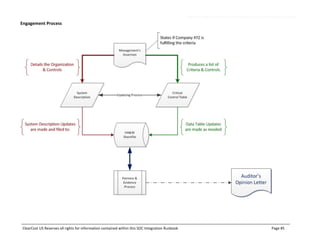
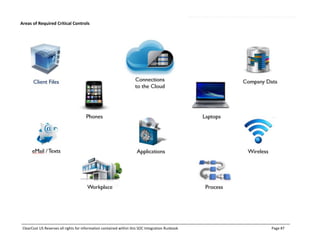
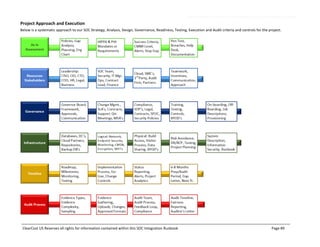
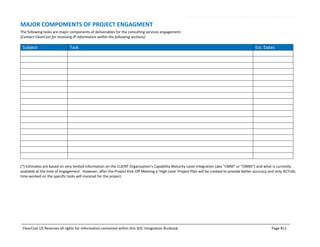
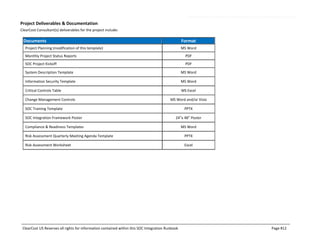
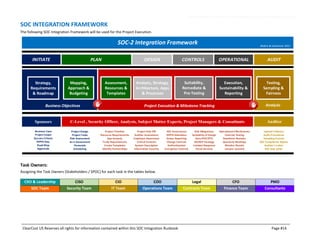
This document outlines the SOC certification integration runbook by ClearCost, detailing the planning, design, execution, and testing of critical controls necessary for SOC compliance. It specifies the roles and responsibilities of ClearCost and the client, as well as critical control areas such as security, availability, and confidentiality, alongside the necessary methodologies and deliverables. The document serves as a comprehensive guide for organizations engaging in SOC compliance efforts, emphasizing the importance of governance, risk management, and reporting processes.