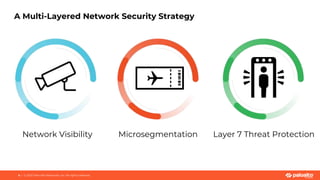
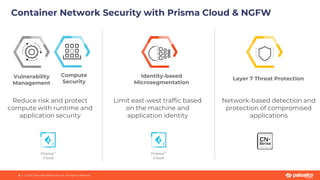
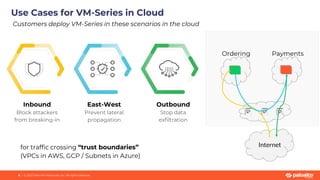
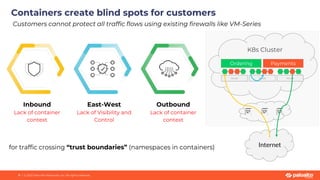
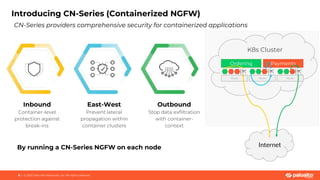
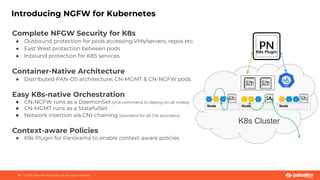
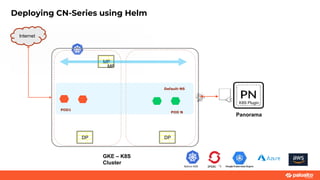
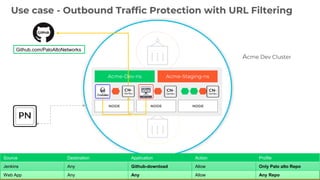
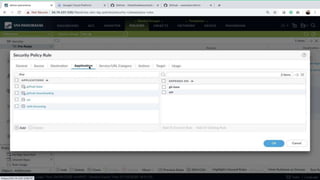
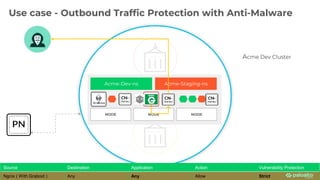
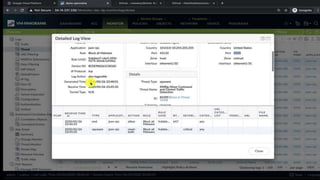
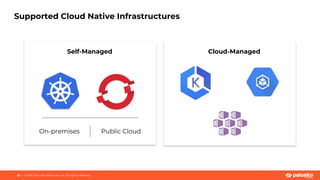
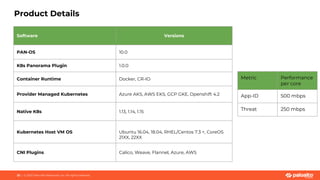
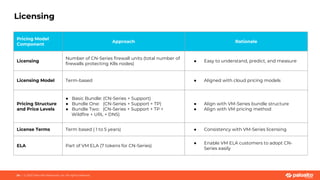
This document discusses Palo Alto Networks' CN-Series Kubernetes Next Generation Firewall (NGFW). It provides an overview of CN-Series' container network security capabilities including outbound traffic protection with URL filtering and threat prevention demonstrations. The document also reviews CN-Series' container-native architecture, easy Kubernetes orchestration using Helm charts, and product details such as supported infrastructures, software versions, performance metrics, and licensing model.