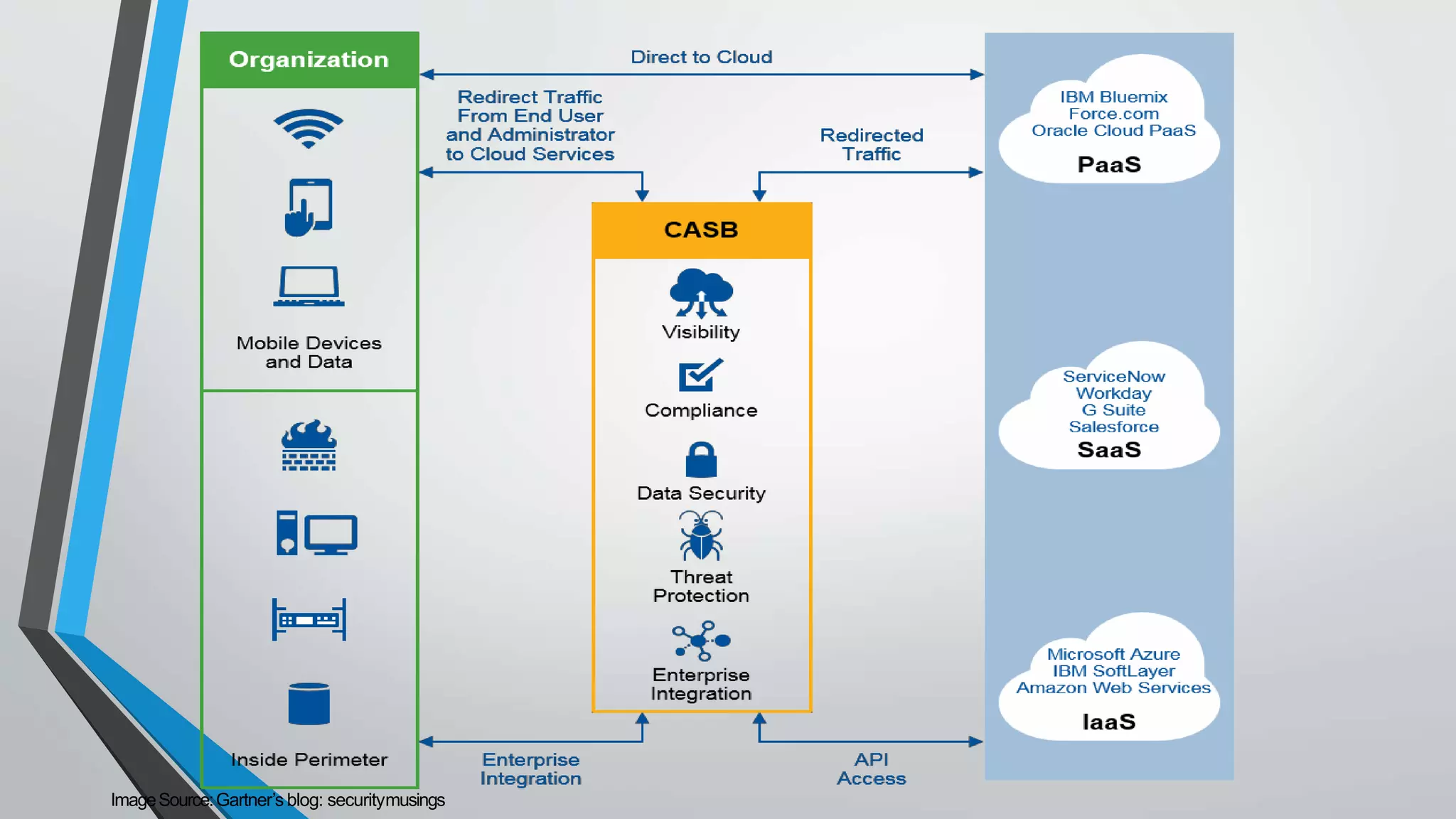
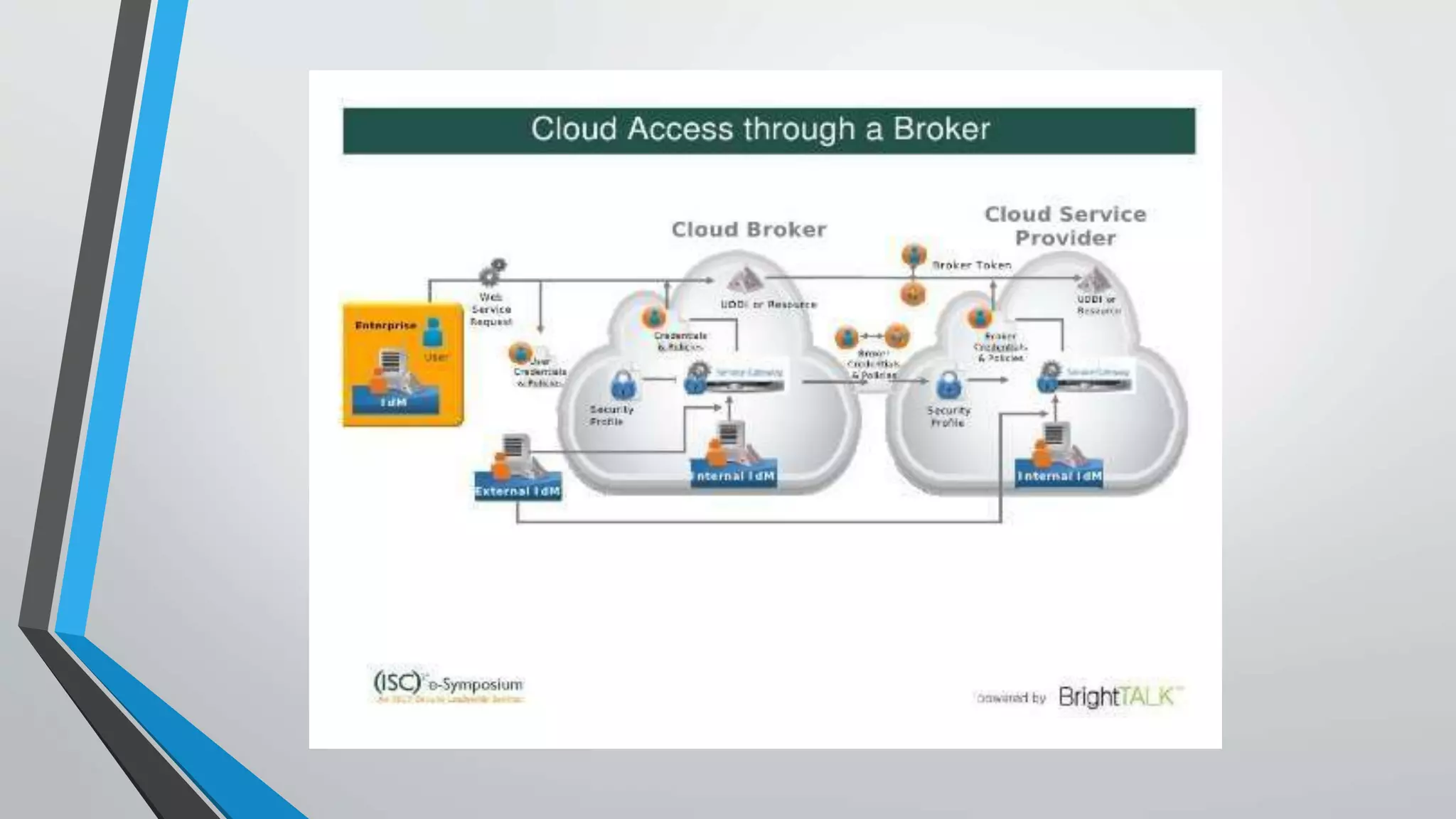
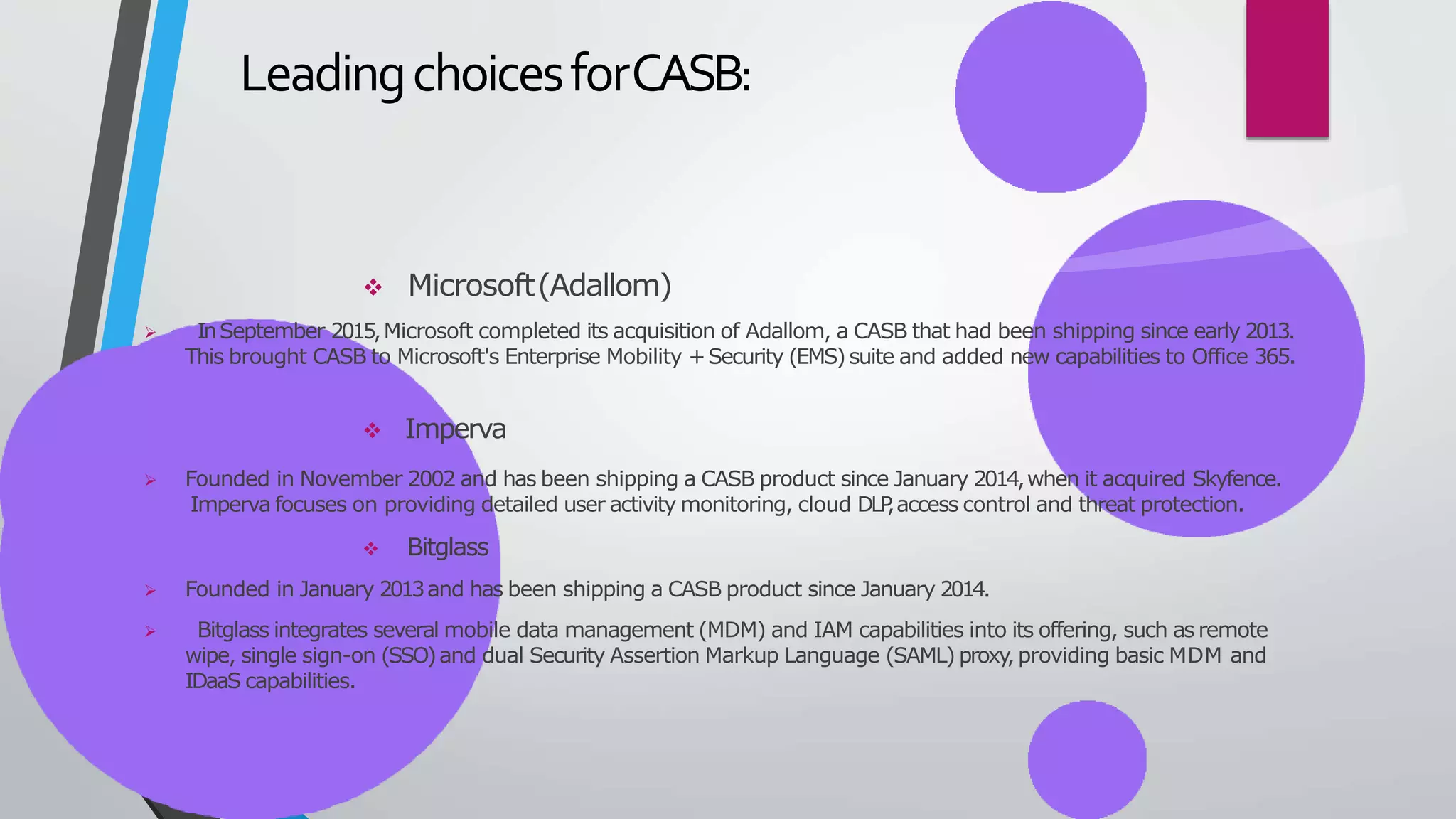
A cloud access security broker (CASB) sits between an organization's network and cloud providers to extend security policies to third-party cloud services and applications. CASBs allow organizations to identify and control cloud app usage, enforce data security policies, and protect against threats. CASBs are increasingly adopted due to growth in cloud services and the need to secure data outside of an organization's network. Common CASB functions include visibility, compliance, data security, and threat protection for cloud apps and services.