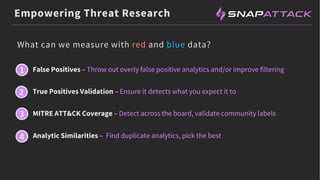
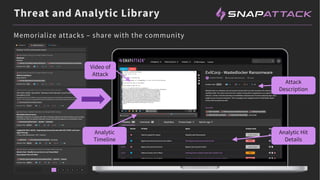
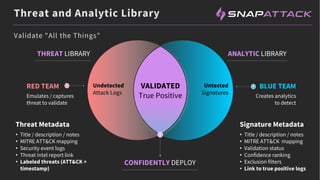
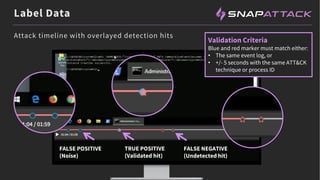
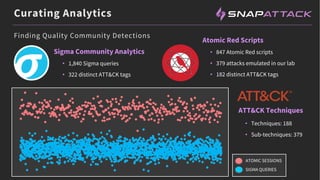
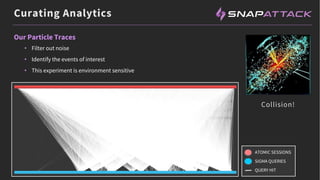
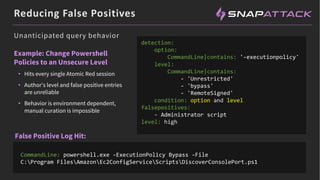
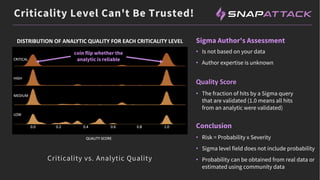
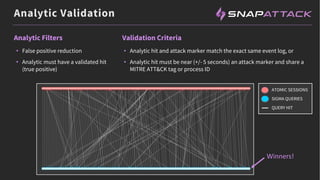
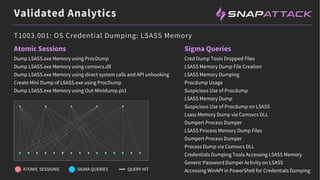
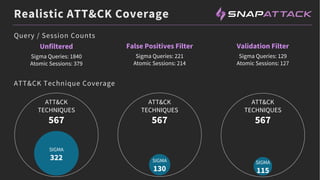
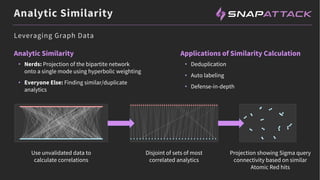
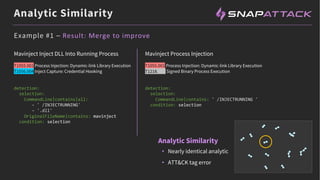
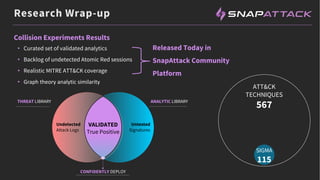
The document discusses the integration of red and blue team efforts to enhance threat detection and response using the MITRE ATT&CK framework. It highlights the importance of community collaboration in curating analytics, reducing false positives, and improving the validation of security measures. The presentation introduces the SnapAttack community platform, aiming to provide open access to threat intelligence while fostering community contributions and better analytic robustness.