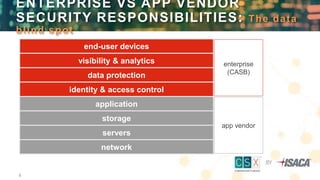
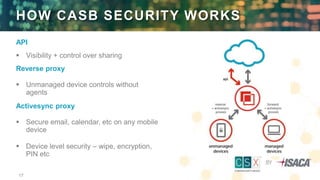
The document discusses the top five cloud security threats, which include external sharing, compromised credentials, lost and stolen devices, unmanaged device access, and unsanctioned apps. It emphasizes the importance of control measures such as Cloud Access Security Brokers (CASBs) and data loss prevention (DLP) solutions for managing these threats effectively. Additionally, it provides insights into how organizations can mitigate risks associated with cloud adoption while maintaining data protection and compliance.