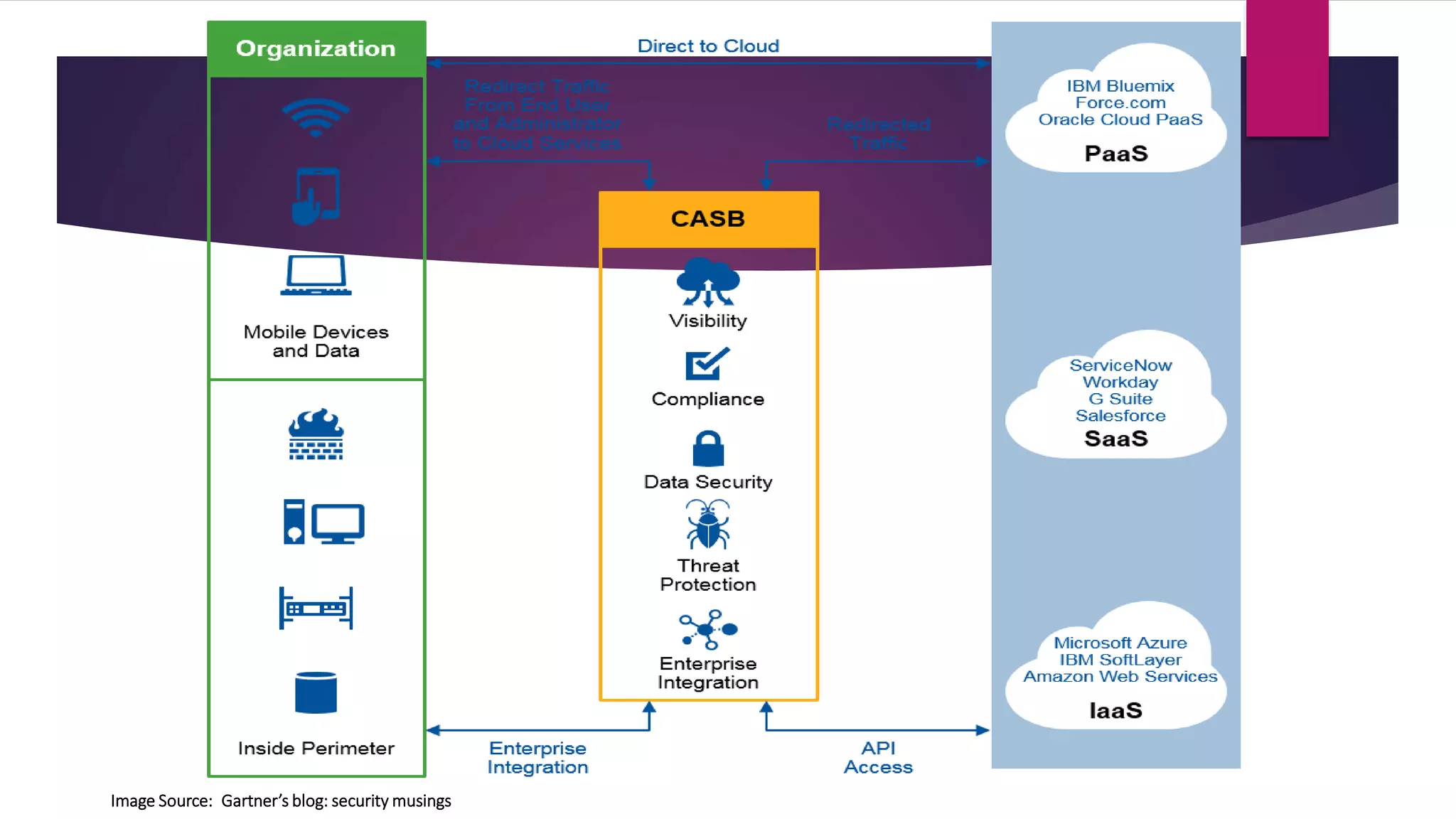
This document discusses Cloud Access Security Brokers (CASBs). It defines a CASB as a set of cloud security technologies that sits between an organization's on-premises infrastructure and a cloud provider's infrastructure to extend security policies to third-party software and storage. CASBs help identify and manage cloud apps, enforce policies, provide data security through encryption and activity monitoring, and integrate with other security solutions. The document discusses how CASBs work using proxies or APIs, compares architectural choices, and lists some leading CASB providers like Microsoft, Imperva, Bitglass, and Cisco CloudLock.