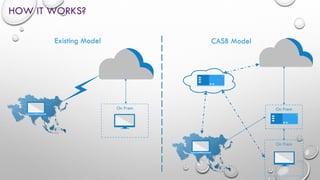
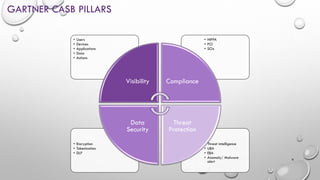
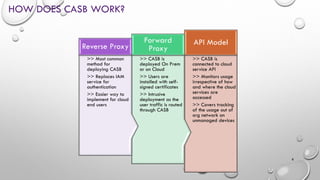
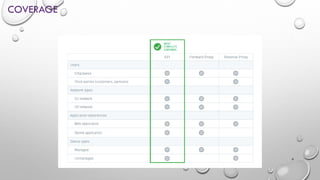
Cloud Access Security Brokers (CASBs) provide visibility and security controls for user activity and data access across cloud applications and services. CASBs work by connecting to cloud service APIs to monitor usage, covering both on-network and off-network access on managed and unmanaged devices. This helps CASBs enforce policies for compliance, data loss prevention, threat protection, and access control. Gartner recognizes several leading CASB vendors that offer capabilities across pillars like visibility, compliance, threat protection and data security when evaluating the CASB market.