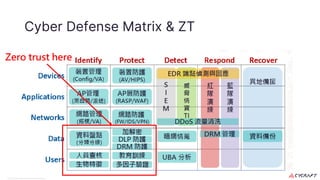
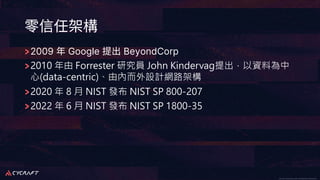
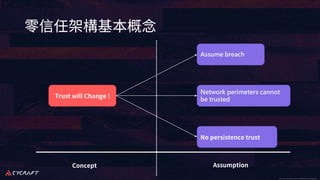
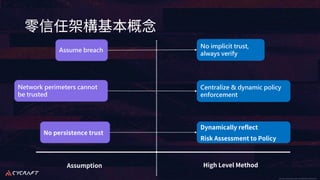
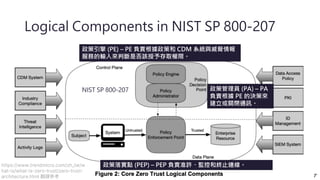
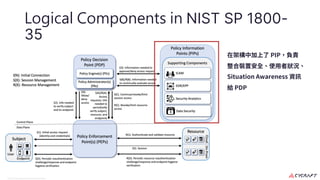
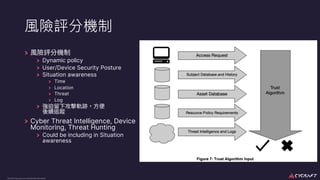
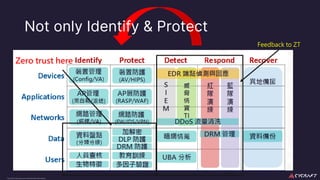
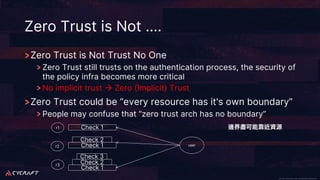
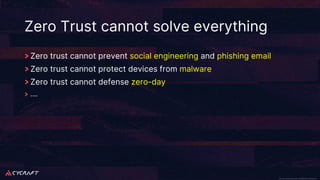
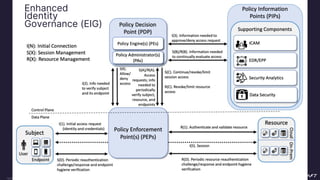
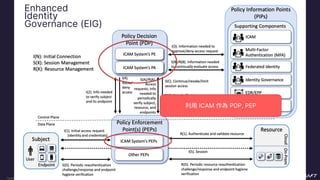
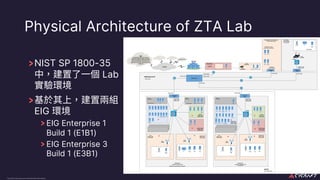
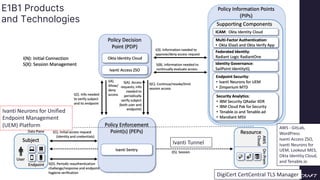
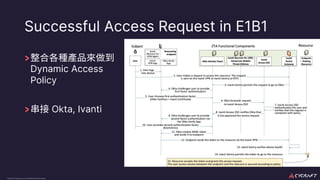
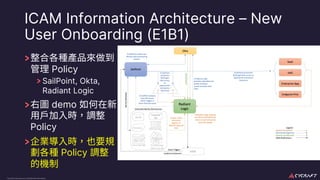
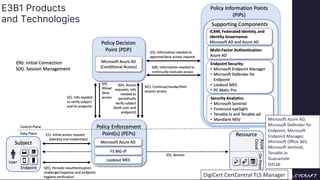
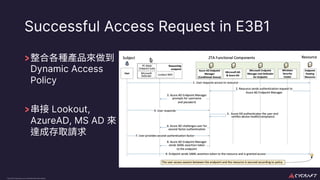
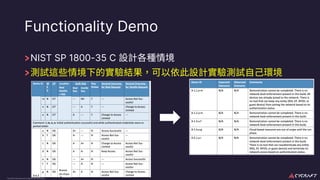
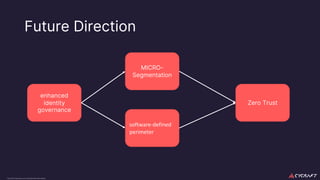
The document discusses implementing a zero trust architecture (ZTA) based on the guidance from NIST SP 1800-35. It describes how NIST SP 1800-35 uses enhanced identity governance (EIG) as the first step towards a ZTA. It outlines the physical and information architecture of the ZTA lab described in NIST SP 1800-35, including the use of Okta, Ivanti, and other identity and access management tools. It also summarizes the future directions discussed in NIST SP 1800-35, such as using micro-segmentation and software-defined perimeters to further a ZTA.