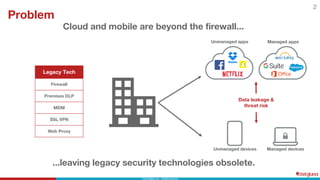
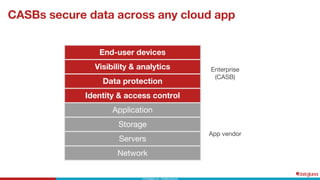
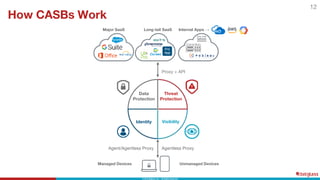
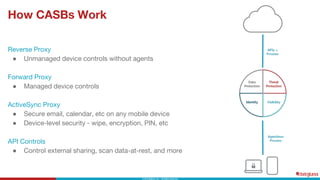
This document discusses the top 6 use cases for cloud access security broker (CASB) technology: 1) Prevent data loss with data loss prevention policies; 2) Control access from unmanaged devices; 3) Stop cloud malware and ransomware; 4) Limit risky external sharing; 5) Securely authenticate users; and 6) Control unsanctioned app usage. It provides examples of how CASBs can address these use cases for two organizations - a large university and a non-profit healthcare organization - by distinguishing managed and unmanaged devices, limiting access to protected health information from risky devices, and regularly scanning cloud apps for malware.