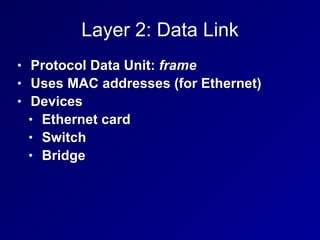
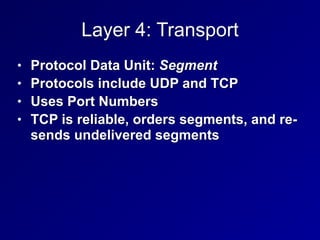
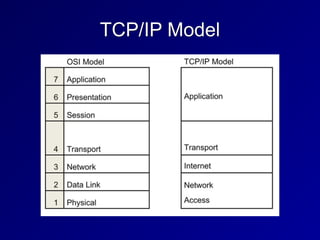
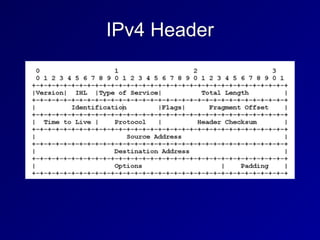
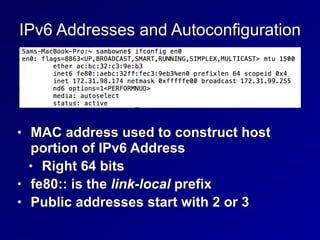
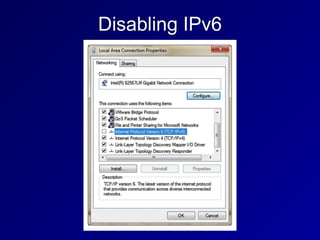
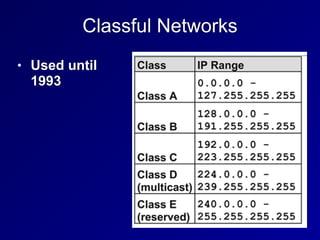
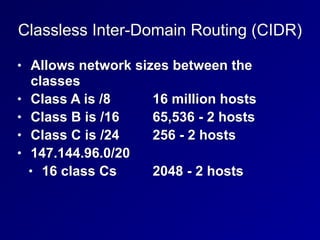
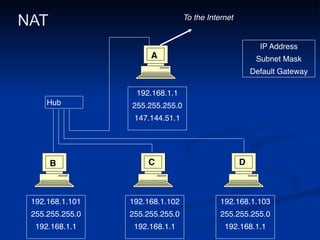
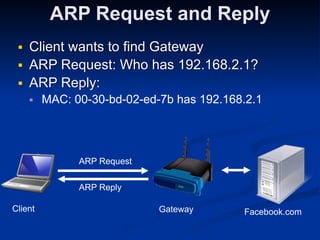
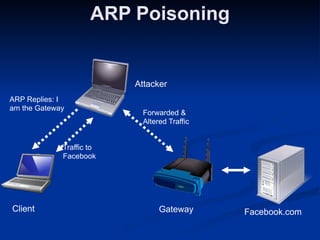
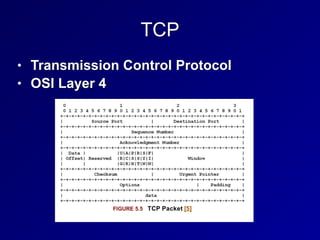
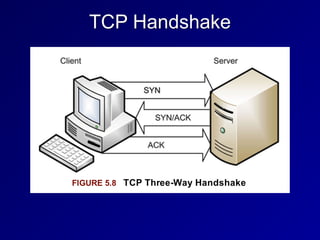
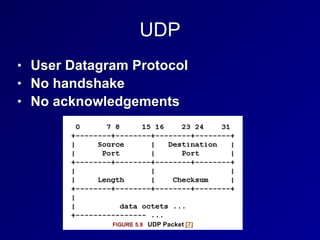
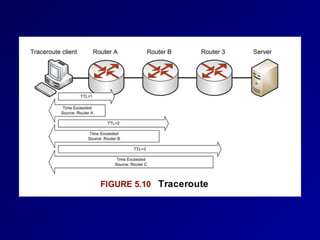
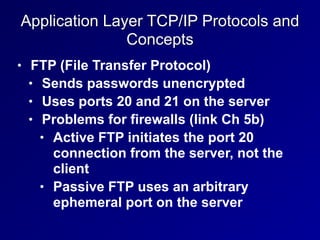
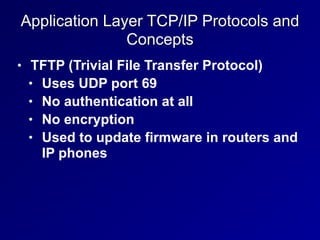
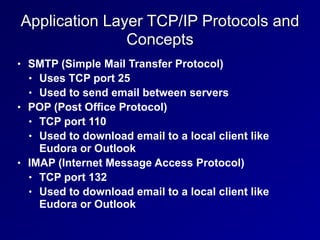
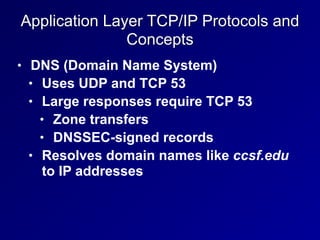
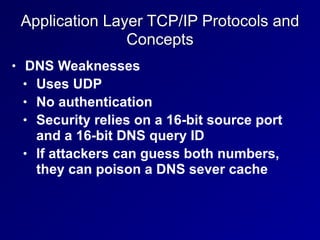
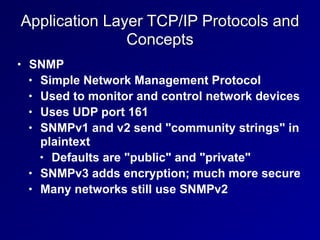
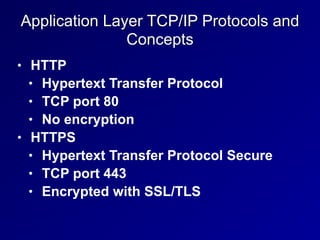
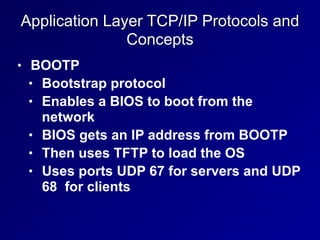
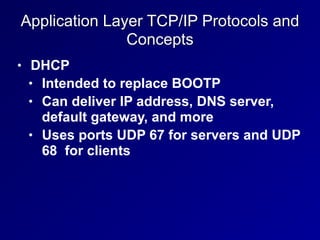
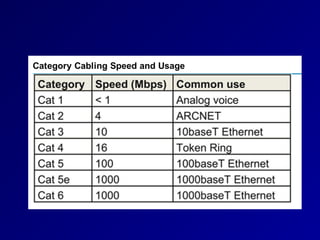
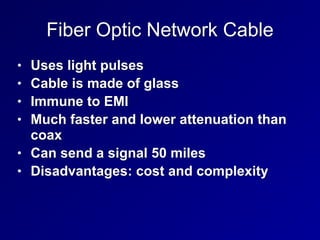
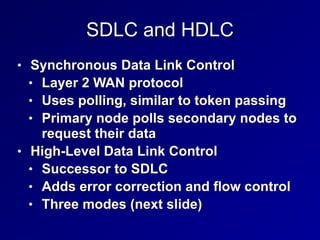
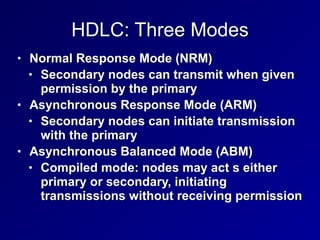
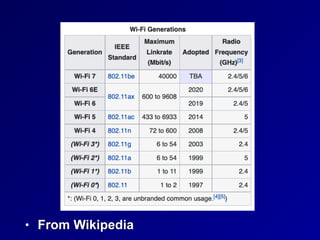
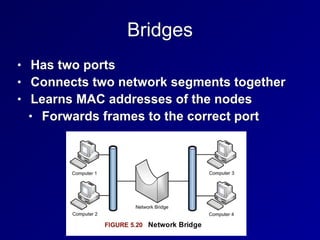
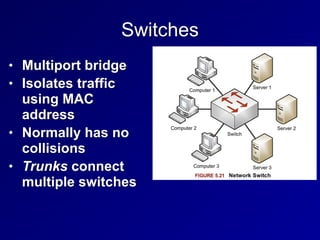
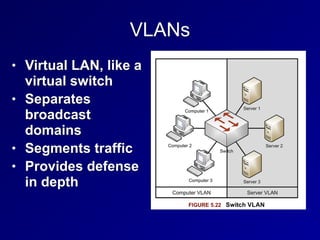
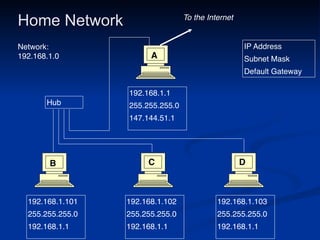
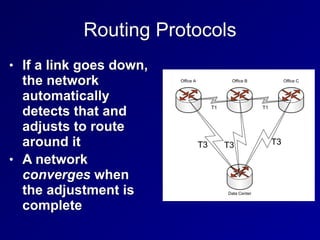
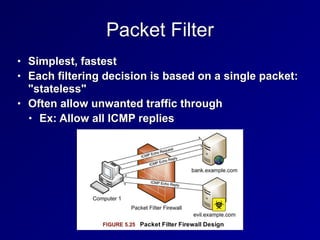
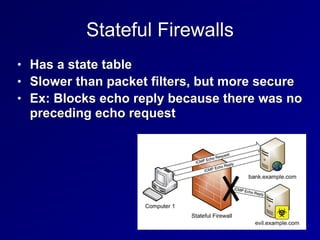
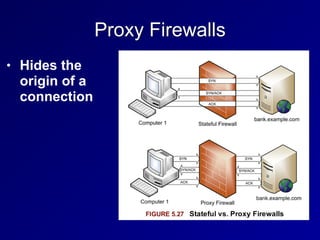
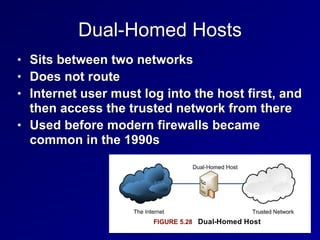
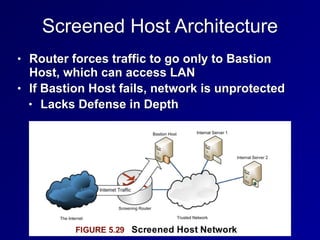
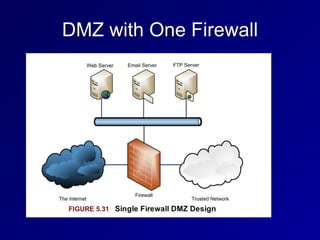
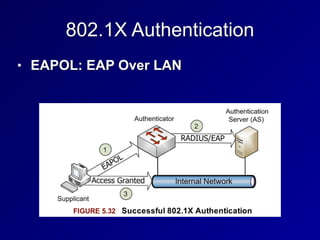
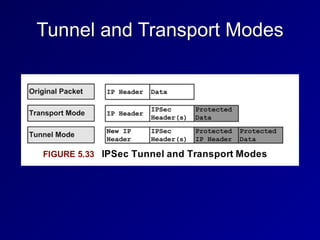
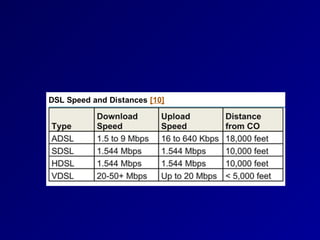
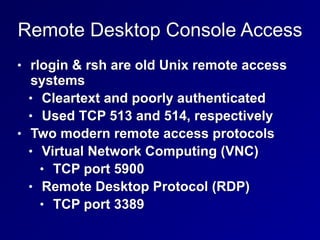
This document provides an overview of key concepts in communication and network security. It discusses fundamental network concepts such as simplex, half duplex, and full duplex transmission. It also covers the OSI model layers, TCP/IP model layers, protocols like IP, ARP, TCP, and UDP. Specific topics covered include MAC addresses, IPv4 and IPv6, NAT, ports, sockets, TCP and UDP flags/handshakes, ICMP, and application layer protocols like Telnet, FTP, and SSH.