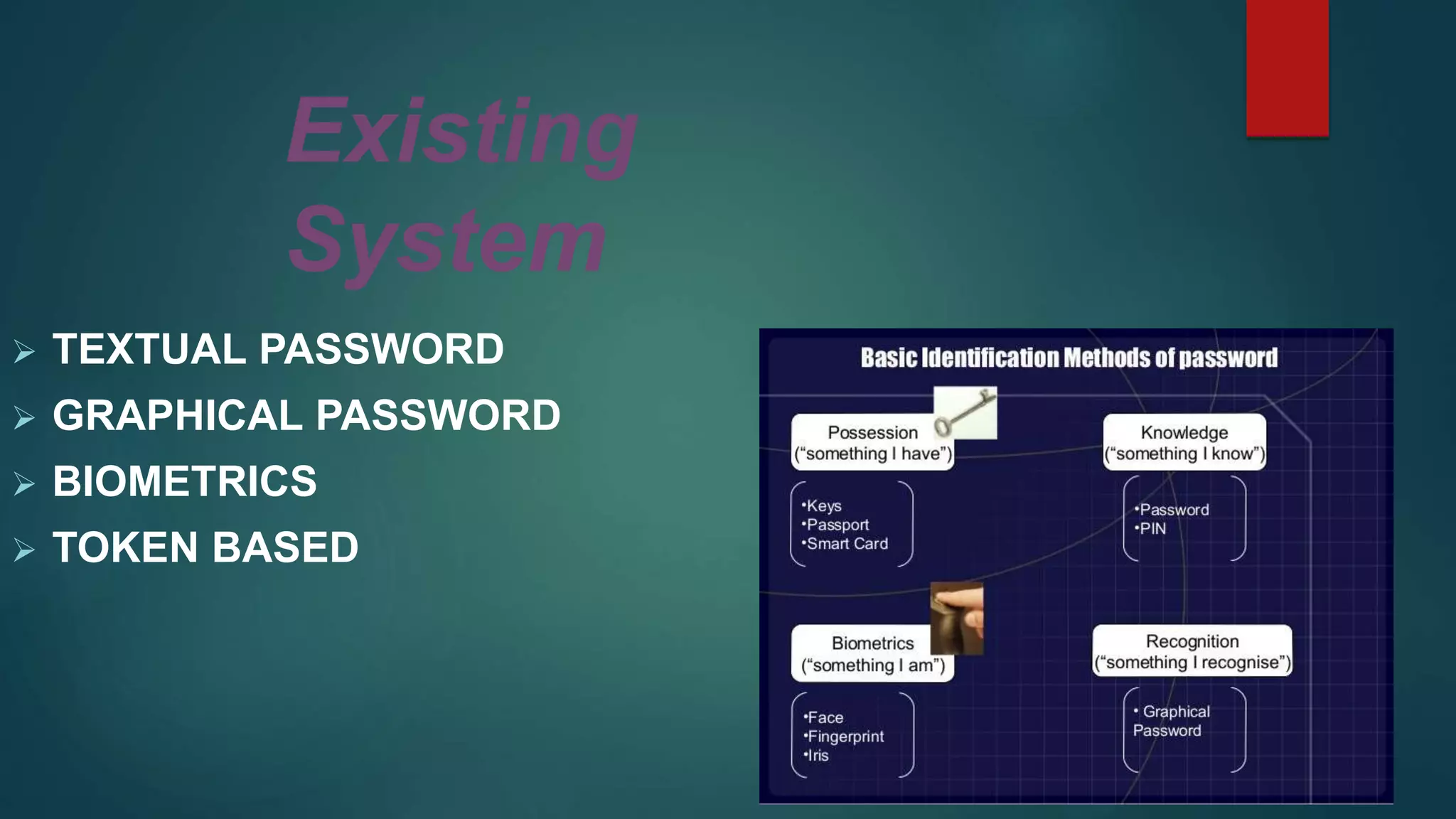
The document discusses 3-D password technology for more secure authentication. It describes existing authentication systems like textual passwords, graphical passwords, biometrics, and token-based systems. A 3-D password presents a virtual environment where the user interacts with virtual objects in a certain sequence and combination to authenticate. The virtual environment and objects can mimic real-life scenarios. 3-D passwords offer flexibility, strength, and ease of memorization while respecting privacy. Their main applications are for critical systems like servers, military facilities, and banks. The document also covers potential attacks and countermeasures for 3-D passwords.