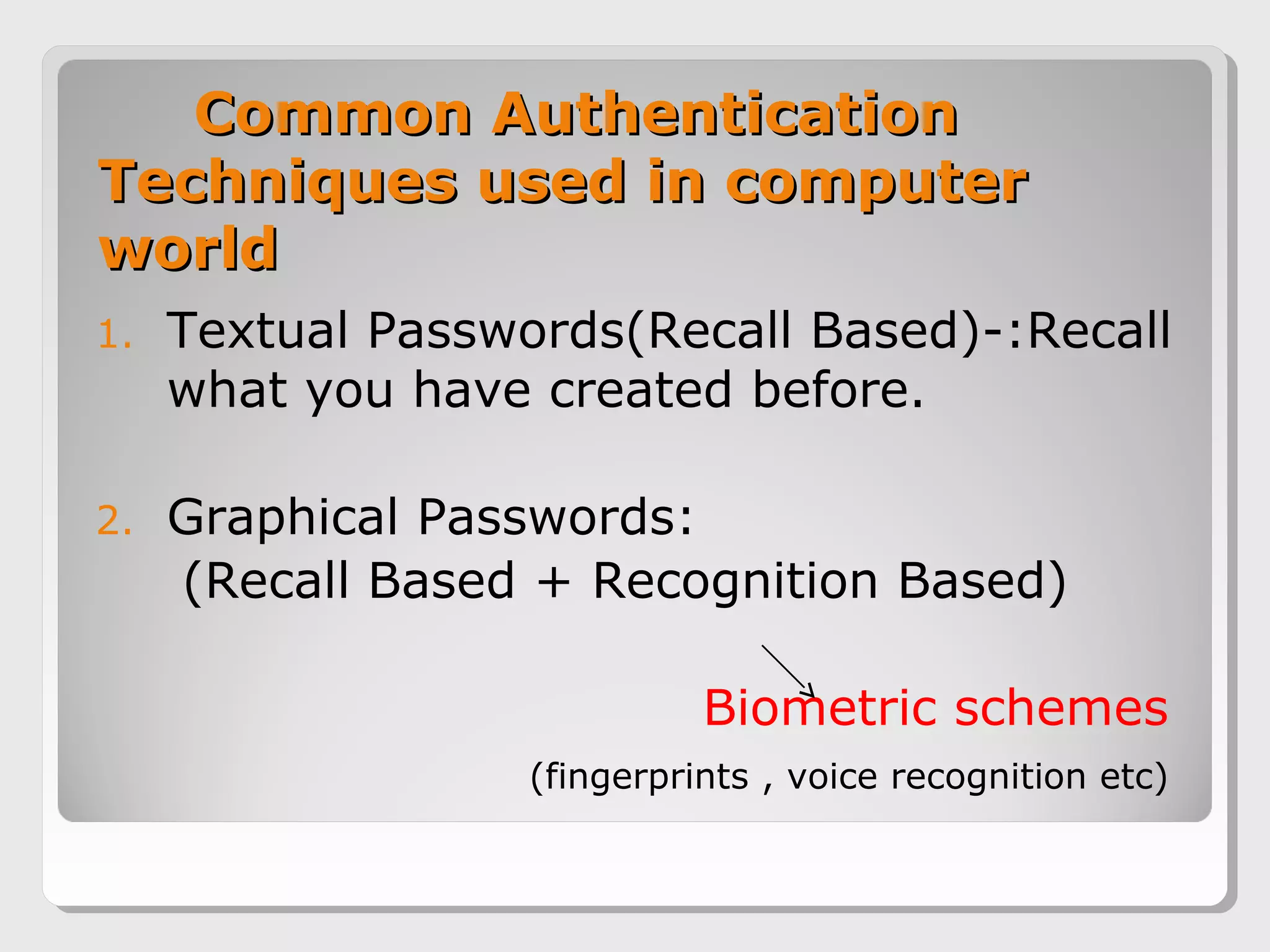
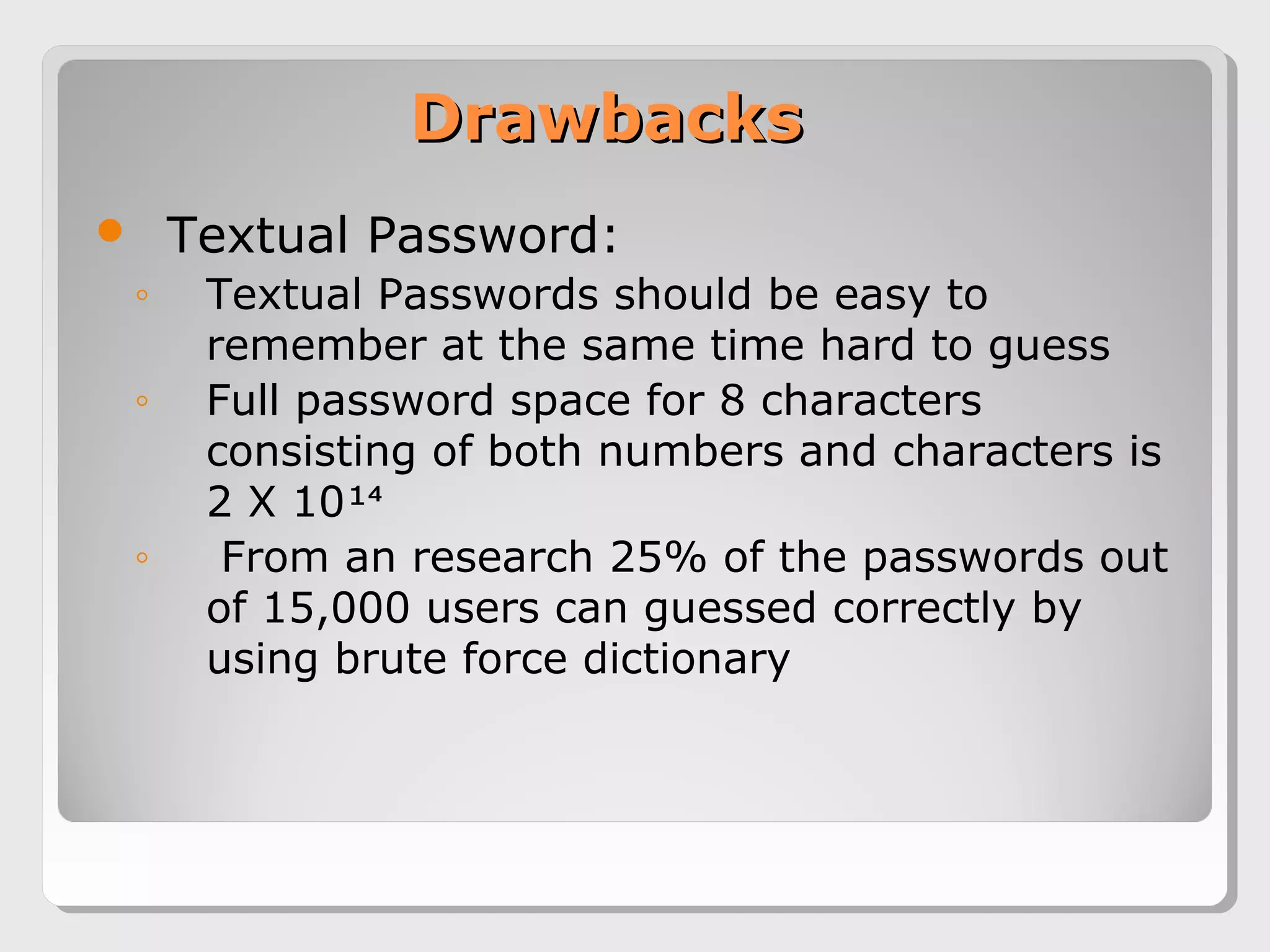
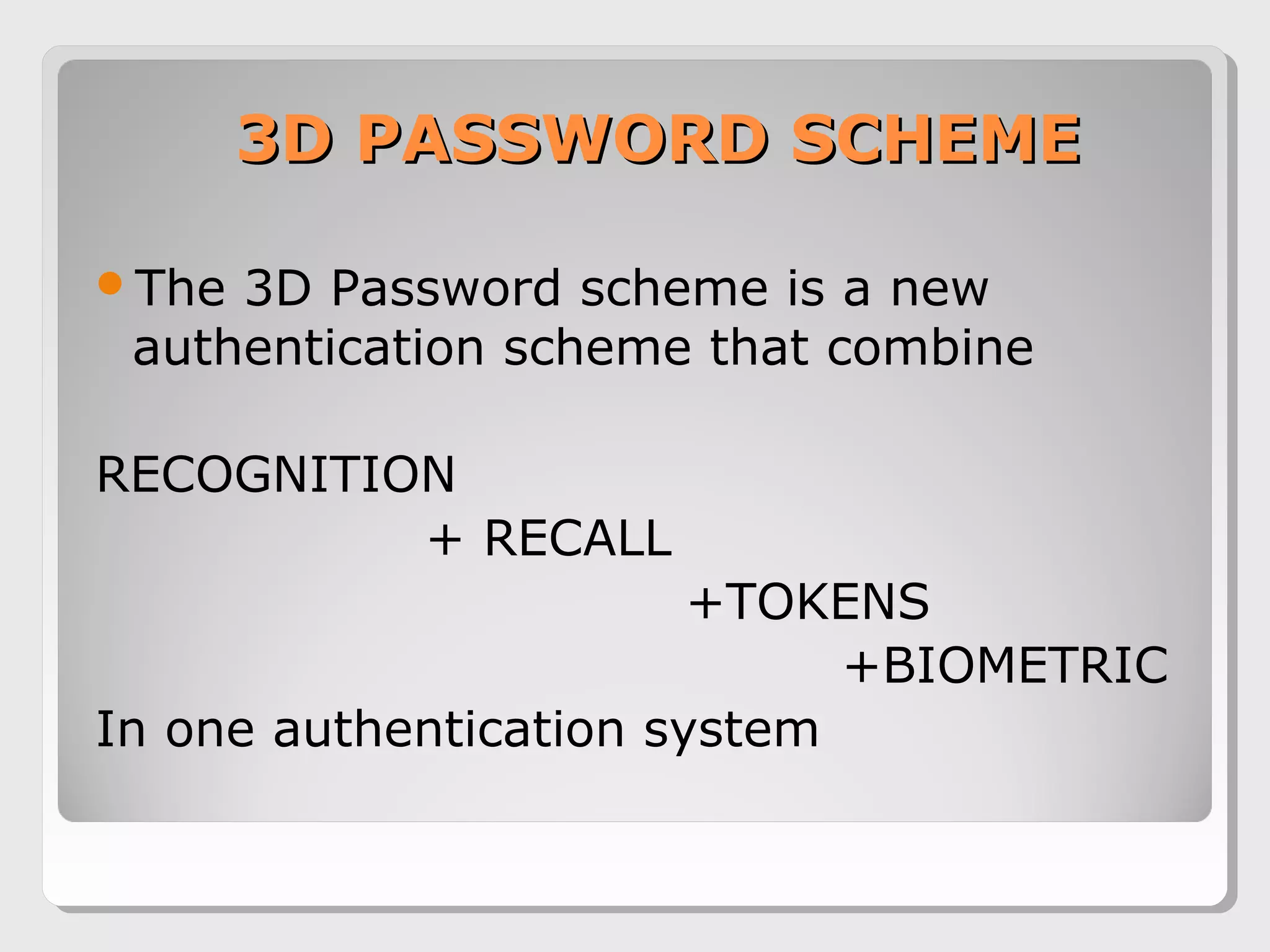
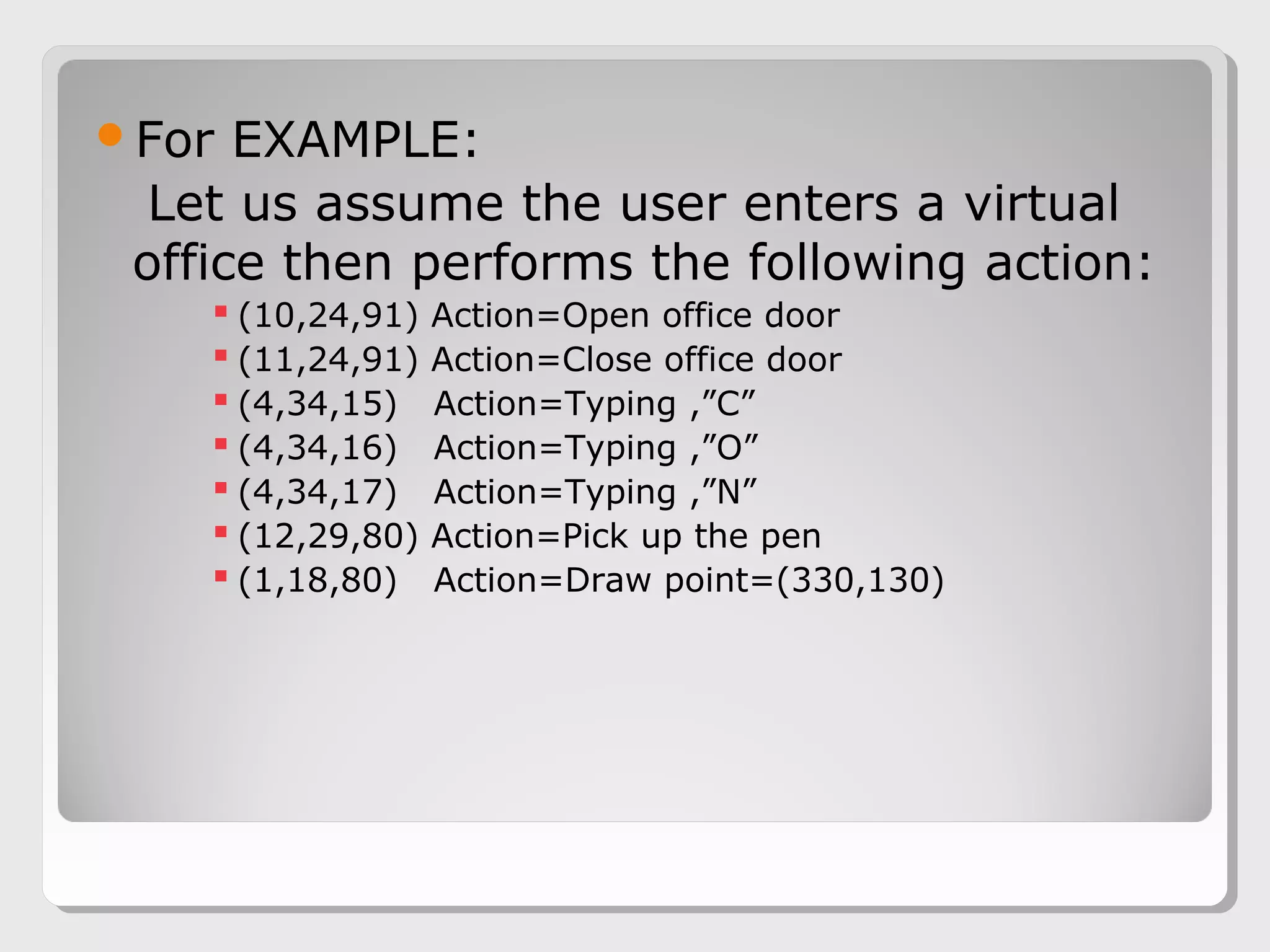
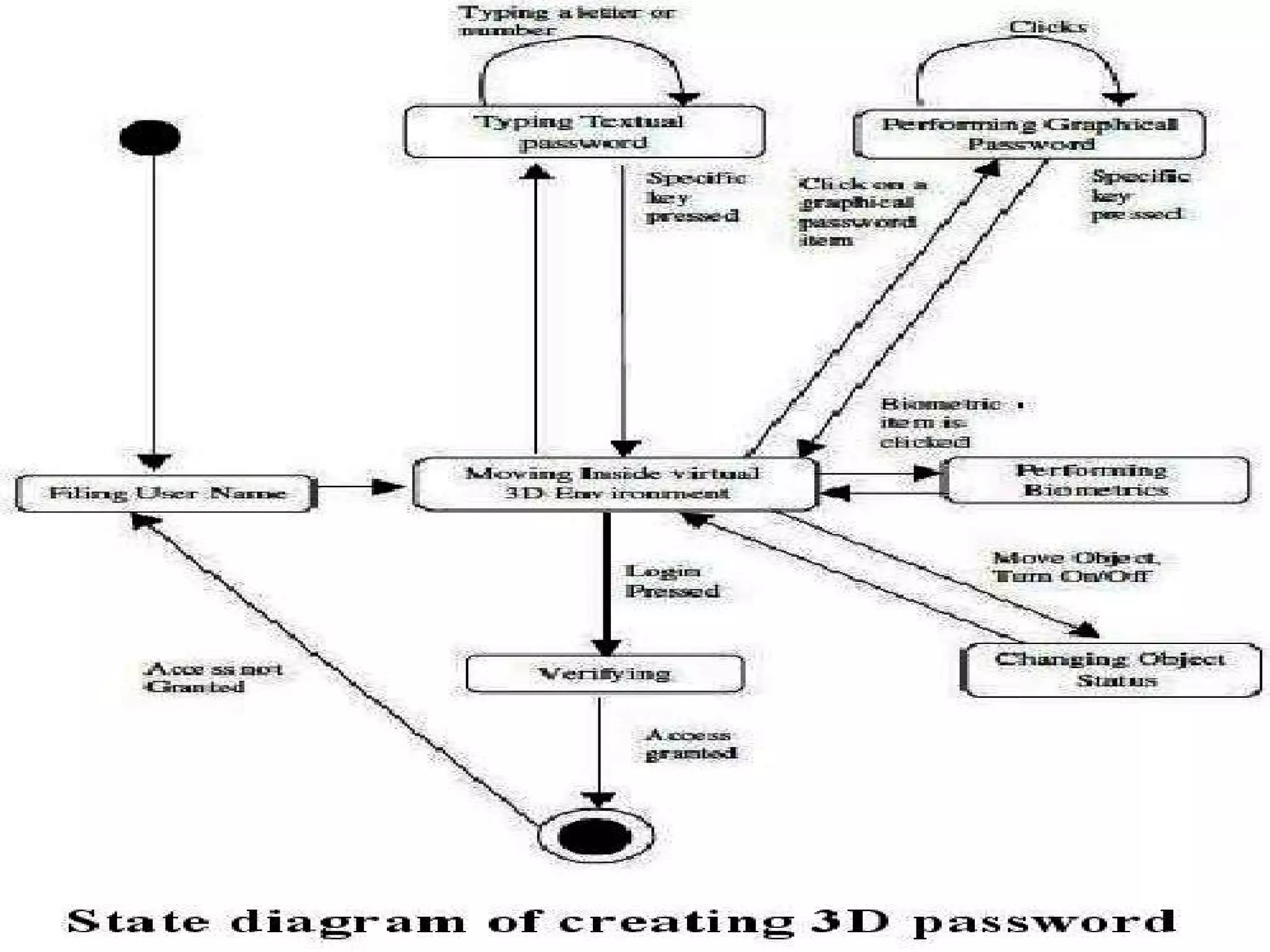
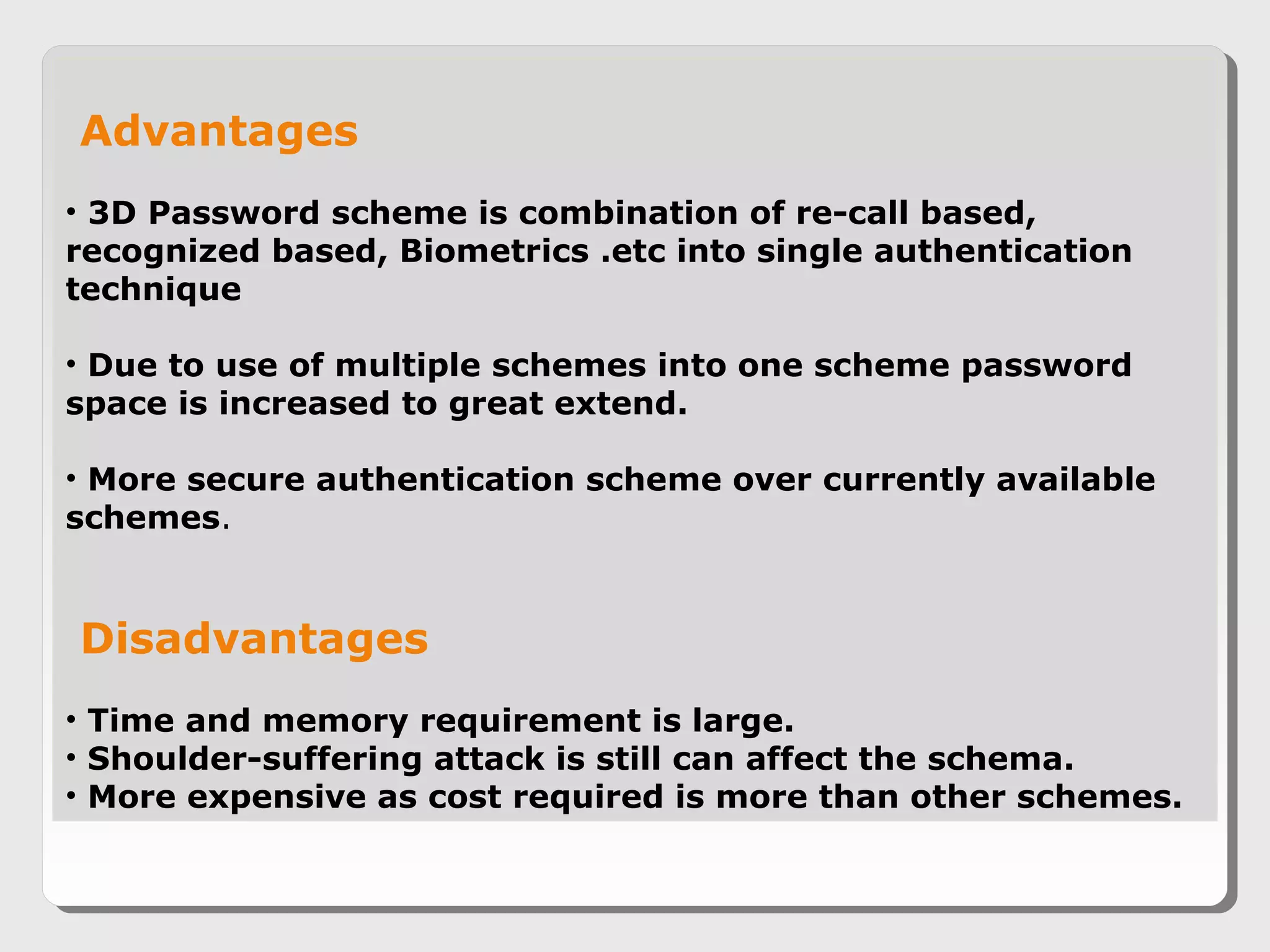
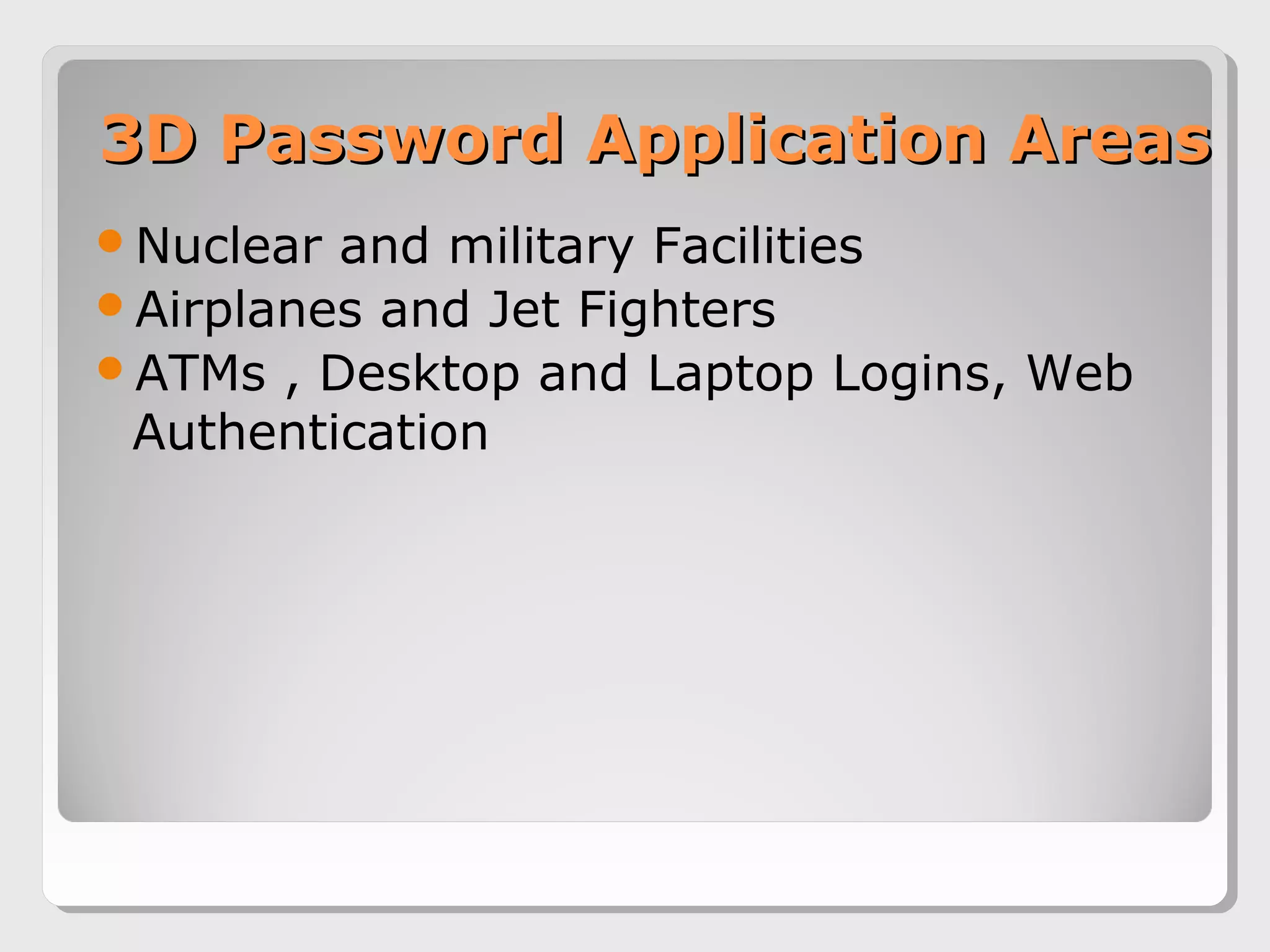
The document proposes a 3D password scheme that combines recognition, recall, tokens, and biometrics for more secure authentication. A virtual 3D environment contains objects the user interacts with in a specific sequence to form their password. This provides a large password space and allows for multifactor authentication in a format that is easy to remember. Some example uses are nuclear facilities, airplanes, ATMs, and desktop logins. The scheme aims to improve security over text and graphical passwords alone while respecting user privacy in selection of authentication methods.