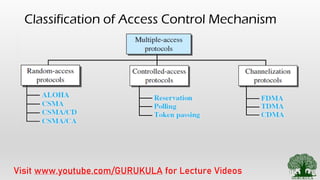
The document provides an overview of communication network access control in the data link layer, focusing on random access methods such as CSMA/CD and CSMA/CA. It covers essential concepts like framing, flow control, access control types, and specific protocols including Ethernet and WLAN. Additionally, it discusses the collision detection process in CSMA/CD and includes references for further study.
![Communication
Networks
Access Control
in datalink layer
[Random Access Methods]
Part – 2 – CSMA CD](https://image.slidesharecdn.com/2-200802171725/75/2-3a-access-control-random-access-methods-part-2-csma-cd-1-2048.jpg)

![1.C – CSMA – CD [Collision Detection]
Visit www.youtube.com/GURUKULA for Lecture Videos](https://image.slidesharecdn.com/2-200802171725/85/2-3a-access-control-random-access-methods-part-2-csma-cd-4-320.jpg)

![Session Summary
• Access Control [Similar to people accessing the cell tower]
• Random Access Methods [Checks the channel randomly, Idle –
Transmit, Busy – Check again]
• ALOHA [Pure ALOHA, Slotted ALOHA]
• CSMA [ 1 Persistent, n Persistent, p Persistent]
• CSMA – CD [widely used in Ethernet]
• CSMA – CA [widely used in WLAN]
Visit www.youtube.com/GURUKULA for Lecture Videos](https://image.slidesharecdn.com/2-200802171725/85/2-3a-access-control-random-access-methods-part-2-csma-cd-6-320.jpg)
