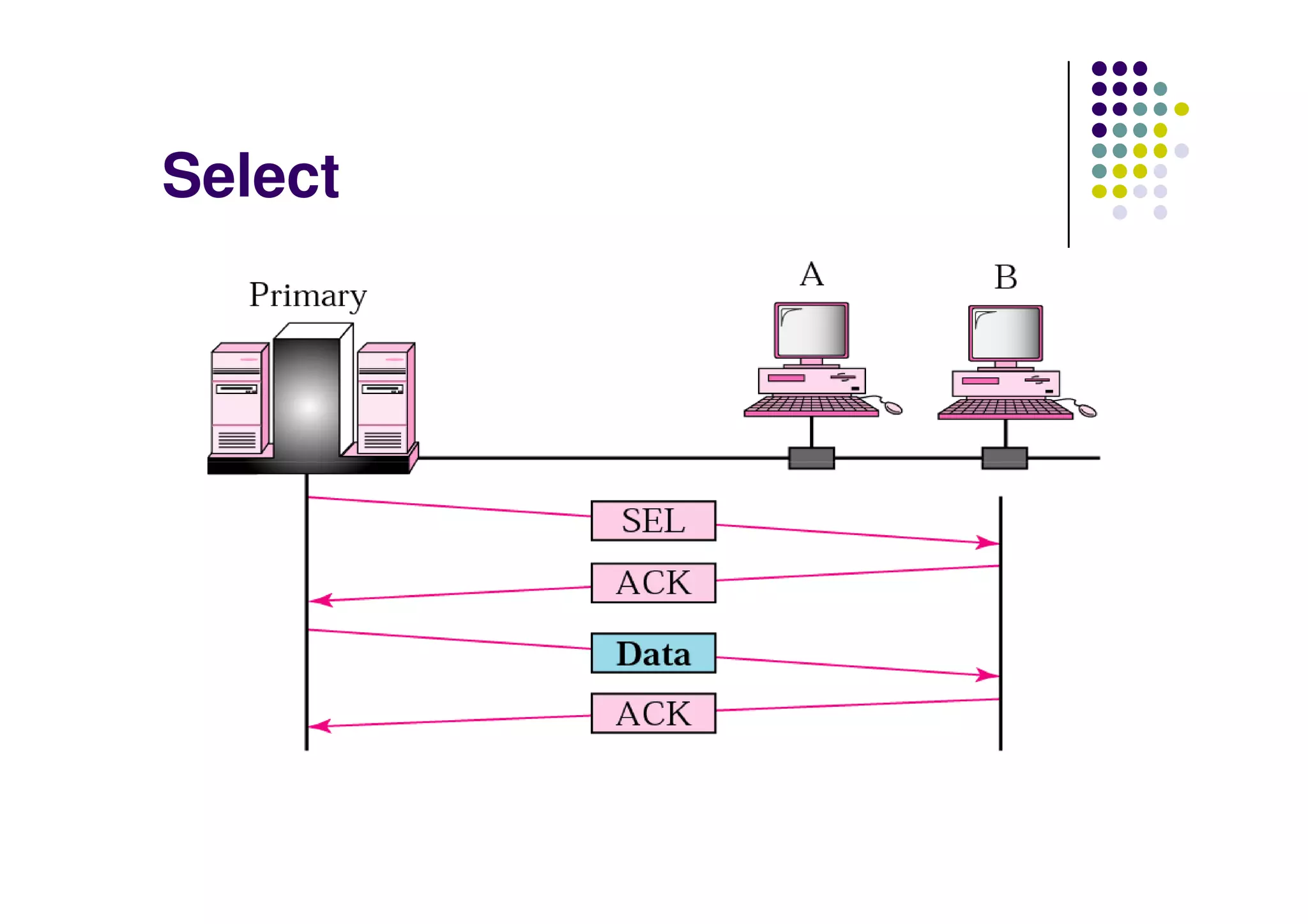
The document discusses data communication and computer networks, focusing on the data link layer which consists of the logical link control (LLC) and medium access control (MAC) sub-layers. It outlines multiple access protocols, particularly random access methods like ALOHA and Carrier Sense Multiple Access (CSMA), which help manage how devices share communication channels to prevent data collisions. Additionally, it addresses controlled access methods and channelization techniques for efficiently using available bandwidth.
![Data Communication
and Computer Networks
[EEE 314]
Mubashir Husain RehmaniMubashir Husain Rehmani
Assistant Professor
Department of Electrical Engineering
COMSATS Institute of Information Technology,
Wah Cantt, Pakistan](https://image.slidesharecdn.com/dccnlecture17compatibilitymode-170621222325/75/Wired-Lan-Ethernet-DATA-Link-Layer-1-2048.jpg)