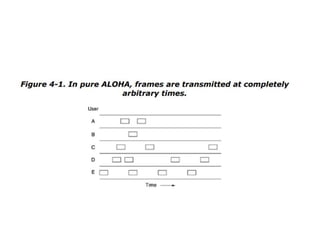
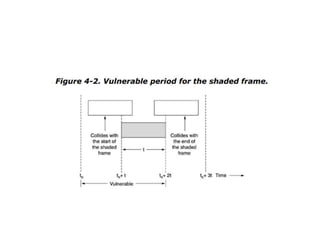
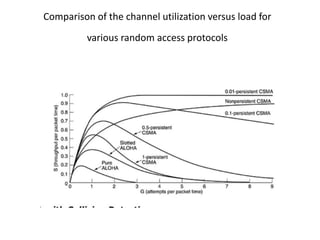
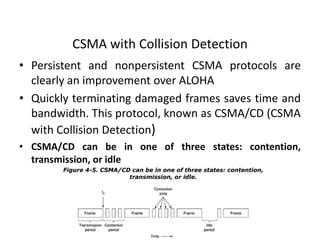
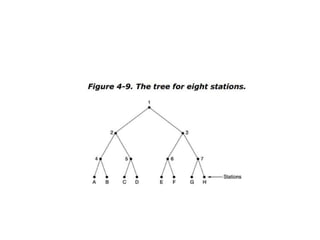
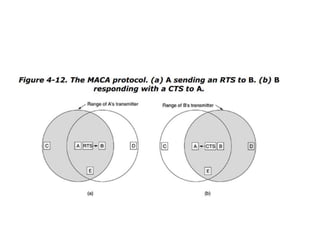
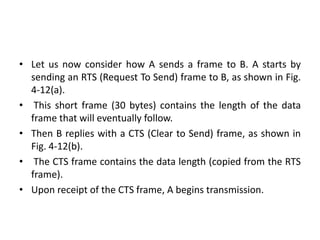
The document discusses various medium access control (MAC) protocols used for determining which device should access a shared communication channel. It covers multiple access protocols including ALOHA, slotted ALOHA, carrier sense multiple access (CSMA), CSMA with collision detection, and collision-free protocols like bit-map and binary countdown. It also discusses limited-contention protocols, the adaptive tree walk protocol, wavelength division multiple access, wireless LAN protocols like MACA and MACAW, and Ethernet.