The document discusses Ethernet networks and communication. It covers the evolution of Ethernet from standard Ethernet operating at 10 Mbps to 10 Gigabit Ethernet at 10 Gbps. It describes Ethernet's frame format including fields for preamble, start frame delimiter, destination/source addresses, length/type, data, padding, and CRC. It also discusses Ethernet addressing using MAC addresses and Ethernet's access method of CSMA/CD.











![Session Summary
Ethernet Concepts
• Evolution of Ethernet
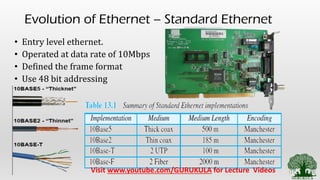
• Standard Ethernet and their variations
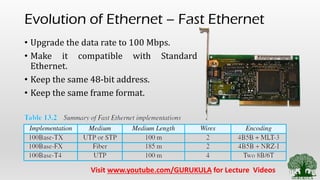
• Fast Ethernet and their variations
• Gigabit Ethernet and their variations
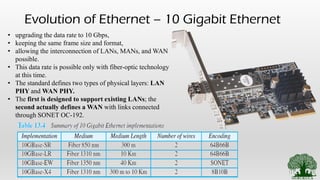
• 10 Gigabit Ethernet and their variations
• Frame Format of Ethernet
• Access Control for Ethernet – [CSMA – CD]
• Performance Evaluation of Ethernet](https://image.slidesharecdn.com/2-200809145203/85/2-6-ethernet-ieee-802-3-15-320.jpg)
