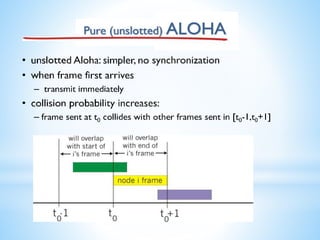
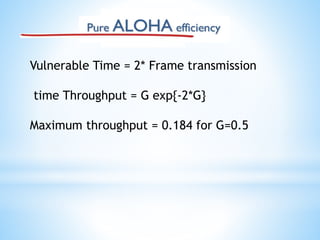
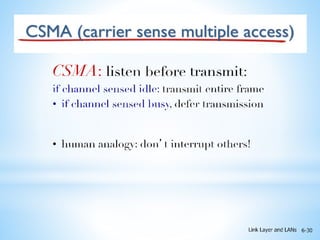
The presentation covers random access protocols in computer networks, detailing protocols like ALOHA and CSMA (with and without collision detection/avoidance). It emphasizes that in these protocols, all stations have equal priority for data transmission, which can lead to collisions. Key features include no fixed sending times or sequences, with mechanisms for collision detection and recovery.