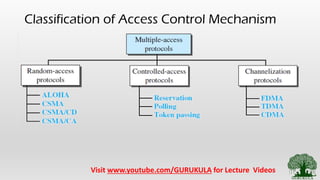
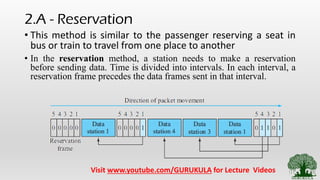
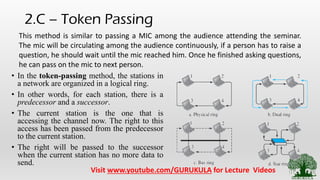
This document discusses access control methods in data link layer communication networks. It describes reservation, polling, and token passing as the three main types of access control. Reservation requires stations to reserve time intervals before transmitting data. Polling uses a primary station that polls secondary stations for data exchanges. Token passing organizes stations in a logical ring, passing a token from one station to the next to determine which has access to transmit.
![Communication
Networks
Access Control
in datalink layer
[Controlled Access Methods]](https://image.slidesharecdn.com/2-200809145158/85/2-4-access-control-controlled-access-methods-1-320.jpg)


![Session Summary
• Controlled Access Methods [Following a systematic
approach]
• Reservation – Similar to Reserving the seats in Bus or
train
• Polling – Similar to Master Slave Concept
• Token Passing – Similar to passing a Mic among the
audience in seminar
Visit www.youtube.com/GURUKULA for Lecture Videos](https://image.slidesharecdn.com/2-200809145158/85/2-4-access-control-controlled-access-methods-7-320.jpg)
