The document discusses the Linux kernel source code and recent security protections that have been merged, including capabilities, restrictions on dmesg and kernel pointers, controlling access to /proc directories, and Yama LSM. Examples of recent exploits like null pointer dereferences and privilege escalation via /proc/pid/mem writes are provided along with mitigation techniques. The talk is intended to provide a simple introduction to these topics with a focus on questions.






![Linux kernel and recent security protections
Linux kernel source code
Configuration and other Makefile options:
make help
make menuconfig
make defconfig
make mandocs
make cscope
Compilation:
make -j $n
make path/single_file.o
make path/module.ko
More from Linux Kernel in a Nutshell [1]. 9](https://image.slidesharecdn.com/linuxkernelandrecentsecurityprotections-120522045816-phpapp01/85/BSides-Algiers-Linux-Kernel-and-Recent-Security-Protections-Djallal-Harouni-9-320.jpg)
![Linux kernel and recent security protections
Linux kernel source code
Linux memory space:
Figure 1: Virtual to Physical [2]
Figure 2: Virtual address space [3]
10](https://image.slidesharecdn.com/linuxkernelandrecentsecurityprotections-120522045816-phpapp01/85/BSides-Algiers-Linux-Kernel-and-Recent-Security-Protections-Djallal-Harouni-10-320.jpg)
![Linux kernel and recent security protections
Linux kernel source code
Linux file system and syscalls:
Figure 3: Linux File system [4]
11](https://image.slidesharecdn.com/linuxkernelandrecentsecurityprotections-120522045816-phpapp01/85/BSides-Algiers-Linux-Kernel-and-Recent-Security-Protections-Djallal-Harouni-11-320.jpg)
![Linux kernel and recent security protections
Linux kernel source code
Interactive map of Linux kernel [5]
12](https://image.slidesharecdn.com/linuxkernelandrecentsecurityprotections-120522045816-phpapp01/85/BSides-Algiers-Linux-Kernel-and-Recent-Security-Protections-Djallal-Harouni-12-320.jpg)

![Linux kernel and recent security protections
Recent security protections
Introduction to Linux capabilities:
On UNIX a privileged process => euid 0 (root)
From Linux 2.2 superuser privileges were divided into
distinct units called capabilities (old not new).
Capabilities:
CAP_NET_ADMIN : network-related operations.
CAP_SETUID: arbitrary UIDs manipulations.
CAP_SYS_ADMIN: a lot of system administration operations (syslog,
mount/unmount,...)
CAP_SYS_MODULE: load/unload kernel modules.
…
15
More from Linux capabilities man page [6].](https://image.slidesharecdn.com/linuxkernelandrecentsecurityprotections-120522045816-phpapp01/85/BSides-Algiers-Linux-Kernel-and-Recent-Security-Protections-Djallal-Harouni-15-320.jpg)
![Linux kernel and recent security protections
Recent security protections
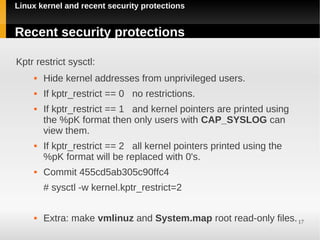
Dmesg restrict sysctl:
Restrict kernel syslog to users with CAP_SYS_ADMIN
Based on GRKERNSEC_DMESG grsecurity [7]
Commit eaf06b241b09135
# sysctl -w kernel.dmesg_restrict=1
or
# echo "1" > /proc/sys/kernel/dmesg_restrict
16](https://image.slidesharecdn.com/linuxkernelandrecentsecurityprotections-120522045816-phpapp01/85/BSides-Algiers-Linux-Kernel-and-Recent-Security-Protections-Djallal-Harouni-16-320.jpg)
![Linux kernel and recent security protections
Recent security protections
Restrict access to /proc/<pid>/ directories:
Procfs is a virtual file system.
Procfs is an interface to kernel data structures.
$ cat /proc/cpuinfo
processor : 0
vendor_id : GenuineIntel
cpu family : 6
/proc/<pid>/* contains information about a running process.
$ cat /proc/self/maps
00400000-0040b000 r-xp 00000000 08:0f 4456467 /bin/cat
0060a000-0060b000 r--p 0000a000 08:0f 4456467 /bin/cat
0060b000-0060c000 rw-p 0000b000 08:0f 4456467 /bin/cat
023ae000-023cf000 rw-p 00000000 00:00 0 [heap]
18
…](https://image.slidesharecdn.com/linuxkernelandrecentsecurityprotections-120522045816-phpapp01/85/BSides-Algiers-Linux-Kernel-and-Recent-Security-Protections-Djallal-Harouni-18-320.jpg)
![Linux kernel and recent security protections
Recent security protections
Restrict access to /proc/<pid>/ directories:
Use the new hidepid= and gid= mount options to restrict
access to these directories.
Origin of the patch is from -ow kernel patches [8] and
grsecurity [7].
If hidepid==0 no restrictions, classic mode.
If hidepid==1 users will access only their own pid directories.
If hidepid==2 restrict access to all /proc/<pid>/ directories.
Commit 97412950b10e64f347
Commit 0499680a42141d8641
Hint: use 'kill -0 $pid' to discover valid pids.
19](https://image.slidesharecdn.com/linuxkernelandrecentsecurityprotections-120522045816-phpapp01/85/BSides-Algiers-Linux-Kernel-and-Recent-Security-Protections-Djallal-Harouni-19-320.jpg)
![Linux kernel and recent security protections
Recent security protections
Yama LSM (Linux Security Module)
Ptrace scope restriction: a debugging process and its inferior
Origin of the patch -ow [8] and grsecurity [7]
If ptrace_scope == 0 classic ptrace permissions.
If ptrace_scope == 1 allow PTRACE_ATTACH only on its
descendants by default. Inferior can change its relationship
and choose its debugger with prctl(PR_SET_PTRACER,...)
Commit 2d514487faf188938a
Yama ptrace scope sysclt:
# sysctl -w kernel.yama.ptrace_scope=1
20](https://image.slidesharecdn.com/linuxkernelandrecentsecurityprotections-120522045816-phpapp01/85/BSides-Algiers-Linux-Kernel-and-Recent-Security-Protections-Djallal-Harouni-20-320.jpg)

![Linux kernel and recent security protections
Recent exploits and mitigation techniques
Null pointer dereferences:
Userspace and kernelspace share the virtual address
space.
mmap() at 0x00 + Null pointer dereference bug in the
kernel => potential null pointer vulnerability [9] [10] [11].
Check git logs (if the information is available):
git log -p –grep=”null.*pointer.*reference”
mmap_min_addr protection (old):
$ cat /proc/sys/vm/mmap_min_addr
65536
23](https://image.slidesharecdn.com/linuxkernelandrecentsecurityprotections-120522045816-phpapp01/85/BSides-Algiers-Linux-Kernel-and-Recent-Security-Protections-Djallal-Harouni-23-320.jpg)
![Linux kernel and recent security protections
Recent exploits and mitigation techniques
Linux Local Privilege Escalation via SUID /proc/pid/mem
Write [12]
/proc/<pid>/mem is used by debuggers.
/proc/<pid>/mem is also a source of vulnerabilities.
CVE-2012-0056
Fixed by commits:
e268337dfe26dfc7ef
6d08f2c7139790c26
Exploit bonus.
24](https://image.slidesharecdn.com/linuxkernelandrecentsecurityprotections-120522045816-phpapp01/85/BSides-Algiers-Linux-Kernel-and-Recent-Security-Protections-Djallal-Harouni-24-320.jpg)
![Linux kernel and recent security protections
Recent exploits and mitigation techniques
Uninitialized stack [13]:
Uninitialized contains data from before.
Is still the old data available ?
CVE-2010-2963
Fixed by commit 3e645d6b485446c54c
Protect with PaX [7]
25](https://image.slidesharecdn.com/linuxkernelandrecentsecurityprotections-120522045816-phpapp01/85/BSides-Algiers-Linux-Kernel-and-Recent-Security-Protections-Djallal-Harouni-25-320.jpg)
![Linux kernel and recent security protections
Recent exploits and mitigation techniques
Linux kernel modules:
Modules are also used by rootkits.
Modules autoloading abuses: CAP_NET_ADMIN can load
modules, and not only Net modules [14]. Load other modules:
# ifconfig ntfs
# lsmod | grep ntfs
Disable module autoloading:
# echo ”/bin/false” > /proc/sys/kernel/modprobe
# sysctl -w kernel.modprobe=”/bin/false”
Disable module loading permanently (paranoid):
# echo 1 > /proc/sys/kernel/modules_disabled 26](https://image.slidesharecdn.com/linuxkernelandrecentsecurityprotections-120522045816-phpapp01/85/BSides-Algiers-Linux-Kernel-and-Recent-Security-Protections-Djallal-Harouni-26-320.jpg)


![Linux kernel and recent security protections
Conclusion
More proactive security features in the mainline kernel.
The origin of some security protections presented here is
from:
Openwall [8]
grsecurity/PaX [7]
Openwall kernel hardening page [15].
29](https://image.slidesharecdn.com/linuxkernelandrecentsecurityprotections-120522045816-phpapp01/85/BSides-Algiers-Linux-Kernel-and-Recent-Security-Protections-Djallal-Harouni-29-320.jpg)
![Linux kernel and recent security protections
Conclusion
Other protections:
LSM: SELinux, AppArmor, TOMOYO, … [16].
GCC plugins and code instrumentation as security protections:
grsecurity/PaX gcc plugins [7]: constify pointers, stackleak, …
grsecurity's RBAC [7].
Seccomp (SECure COMPuting) with filters: filter system calls by
syscall numbers and arguments with BPF (Berkeley Packet
Filter) [17].
30](https://image.slidesharecdn.com/linuxkernelandrecentsecurityprotections-120522045816-phpapp01/85/BSides-Algiers-Linux-Kernel-and-Recent-Security-Protections-Djallal-Harouni-30-320.jpg)
![Linux kernel and recent security protections
References:
[1] Greg KH, Linux Kernel in a Nutshell, O'Reilly.
[2] http://www.ibm.com/developerworks/linux/library/l-kernel-memory-access/
[3] http://www.acm.uiuc.edu/projects/RingCycle/
[4] http://www.ibm.com/developerworks/linux/library/l-linux-filesystem/
[5] http://www.makelinux.net/kernel_map/
[6] http://linux.die.net/man/7/capabilities
[7] http://grsecurity.net/
[8] http://openwall.net/
[9] http://blog.cr0.org/2009/06/bypassing-linux-null-pointer.html
[10] http://blog.cr0.org/2009/08/linux-null-pointer-dereference-due-to.html
[11] http://seclists.org/fulldisclosure/2009/Aug/190
32](https://image.slidesharecdn.com/linuxkernelandrecentsecurityprotections-120522045816-phpapp01/85/BSides-Algiers-Linux-Kernel-and-Recent-Security-Protections-Djallal-Harouni-32-320.jpg)
![Linux kernel and recent security protections
References:
[12] http://blog.zx2c4.com/749
[13] https://media.defcon.org/dc-19/presentations/Cook/DEFCON-19-Cook-Kernel-
Exploitation.pdf
[14] https://lkml.org/lkml/2011/2/24/203
[15] http://openwall.info/wiki/Owl/kernel-hardening
[16] http://http://git.kernel.org/?
p=linux/kernel/git/torvalds/linux.git;a=tree;f=Documentation/security
[17] http://kernel.ubuntu.com/git?p=ubuntu/ubuntu-
precise.git;a=blob;f=Documentation/prctl/seccomp_filter.txt
33](https://image.slidesharecdn.com/linuxkernelandrecentsecurityprotections-120522045816-phpapp01/85/BSides-Algiers-Linux-Kernel-and-Recent-Security-Protections-Djallal-Harouni-33-320.jpg)