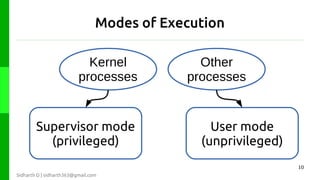
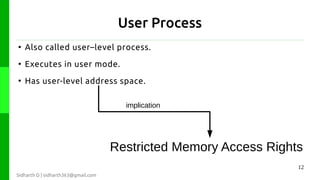
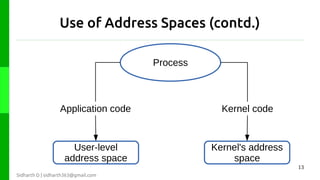
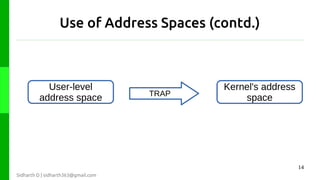
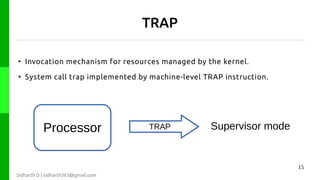
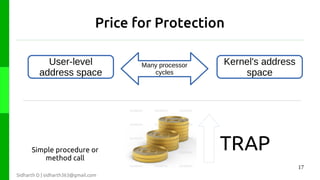
The document discusses protection in operating systems. It explains that resources require protection from illegitimate access to ensure only allowed processes can access objects. The principle of least privilege is discussed, where programs are given just enough privileges to perform tasks. Threats can come from malicious or buggy code. Protection is provided through type-safe languages, hardware support using a kernel, supervisor mode, address spaces, and traps invoked through system calls.








![Reference
[1] G. Coulouris, et. al., “Operating system support,” in
Distributed Systems Concepts and Design, 4 th ed. Noida,
India: Dorling Kindersley(India) Pvt. Ltd., 2009, ch. 6,
sec. 3, pp. 210-211
19
Sidharth D | sidharth363@gmail.com](https://image.slidesharecdn.com/presentation-protection-131020034157-phpapp01/85/Protection-in-Operating-System-Layer-19-320.jpg)
