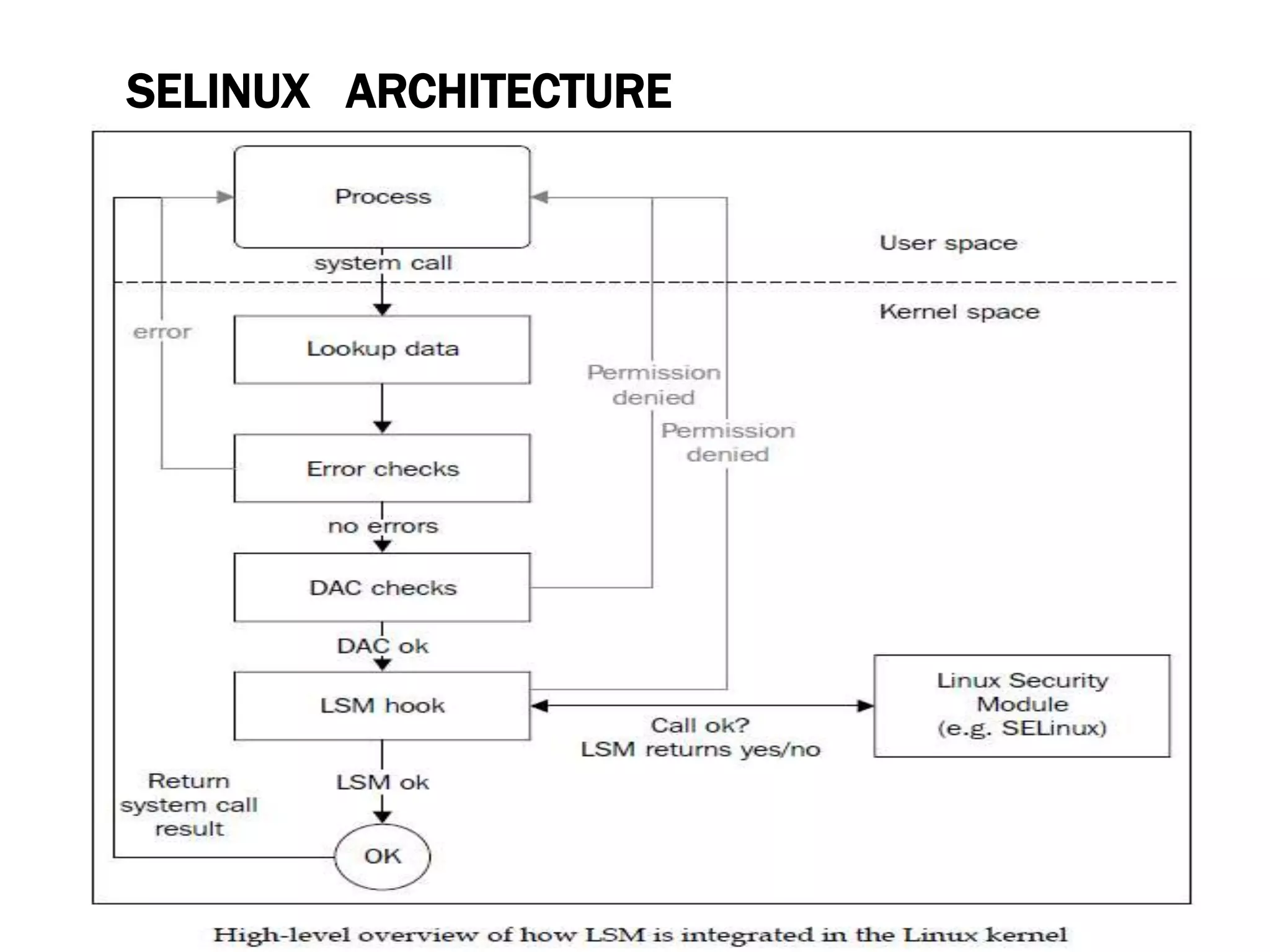
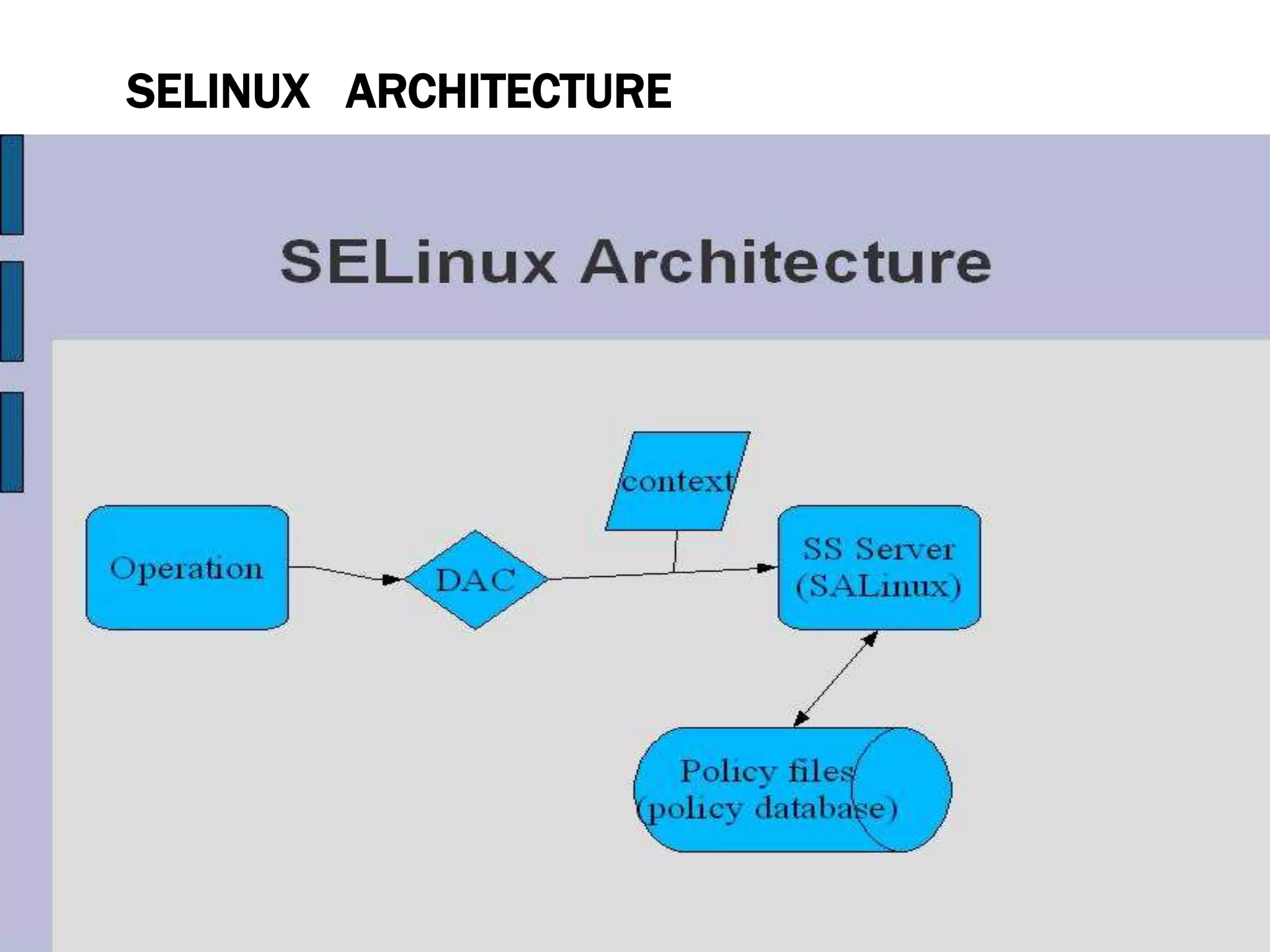
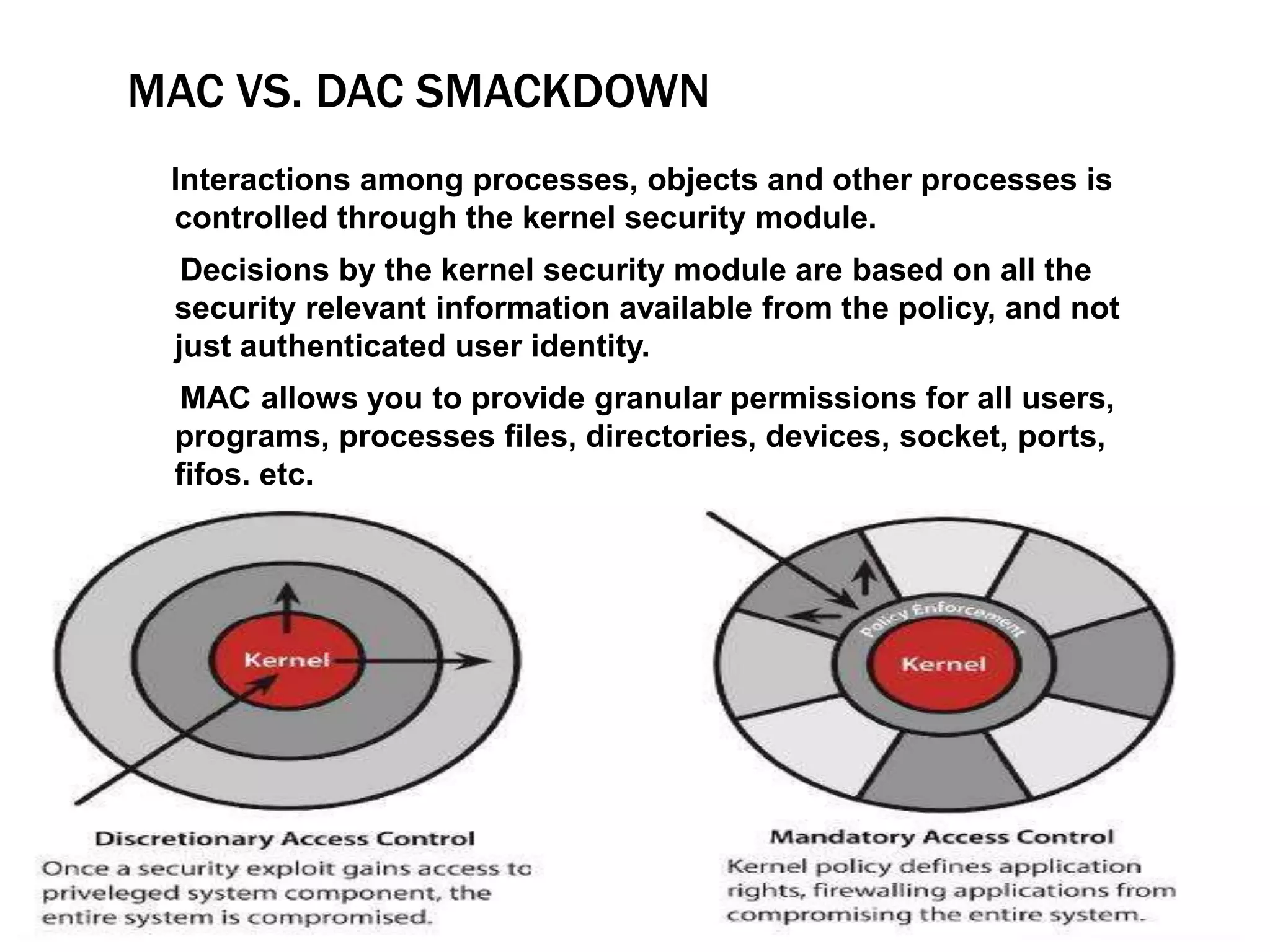
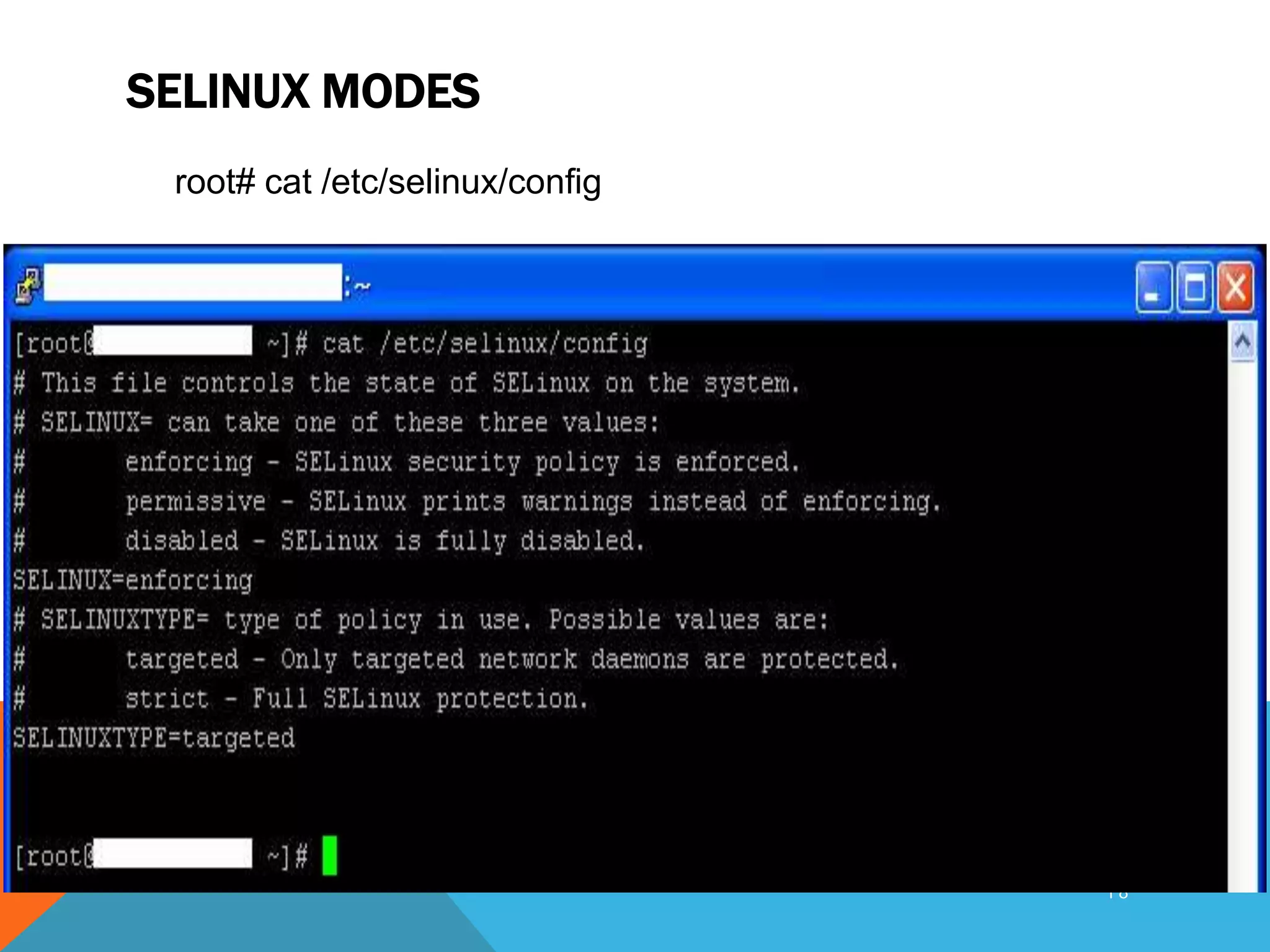
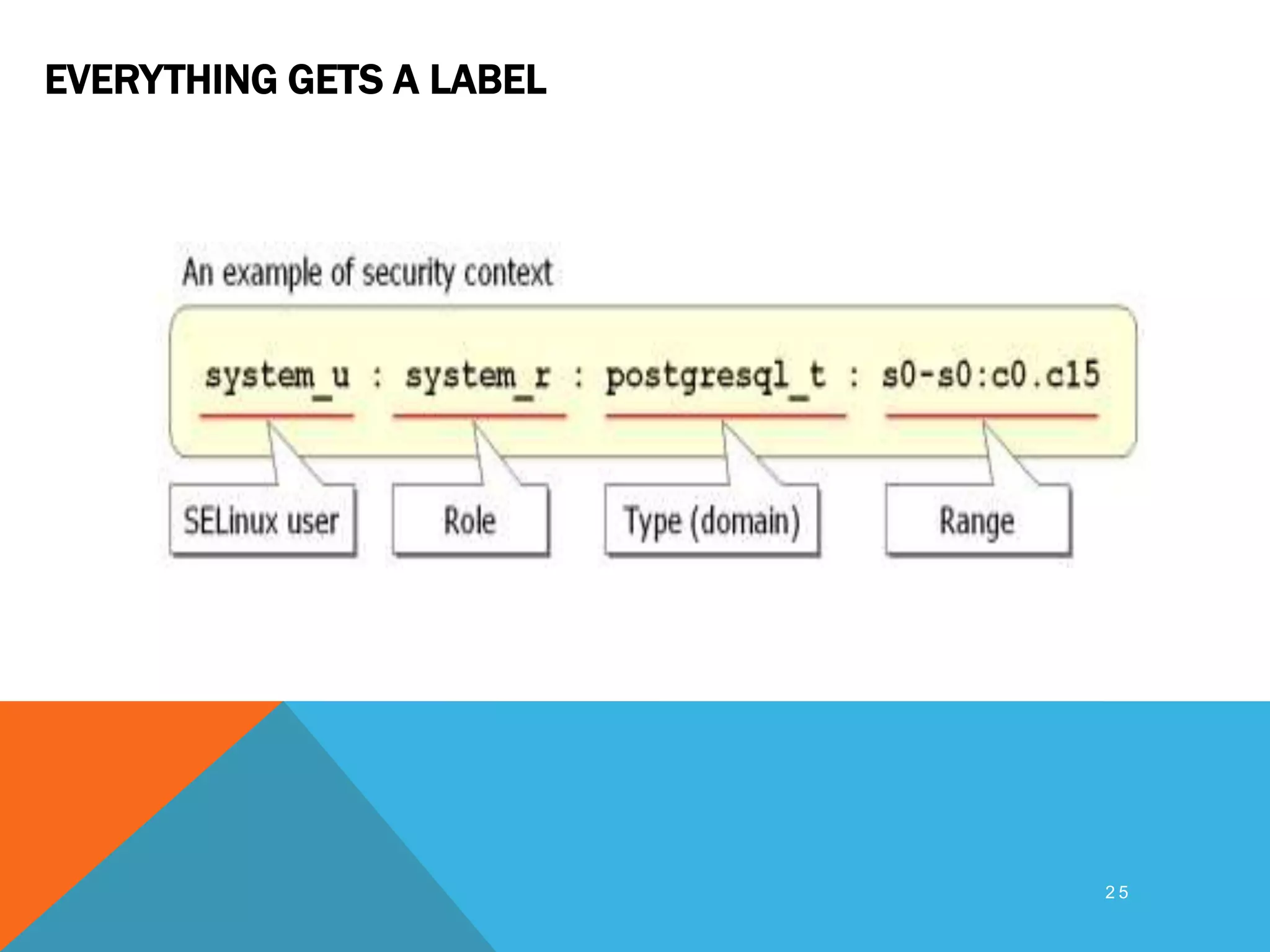
SELinux provides mandatory access control on Linux systems to confine processes and restrict what they can do. It works by labeling system resources like files, processes, and ports with security contexts. When a process tries to access a resource, SELinux checks if the process's security context is allowed to access the target resource based on the SELinux policy. This provides finer-grained access control than traditional Linux discretionary access control based on users and groups. The security context includes the SELinux user, role, and type (domain) that together determine the process's permissions.


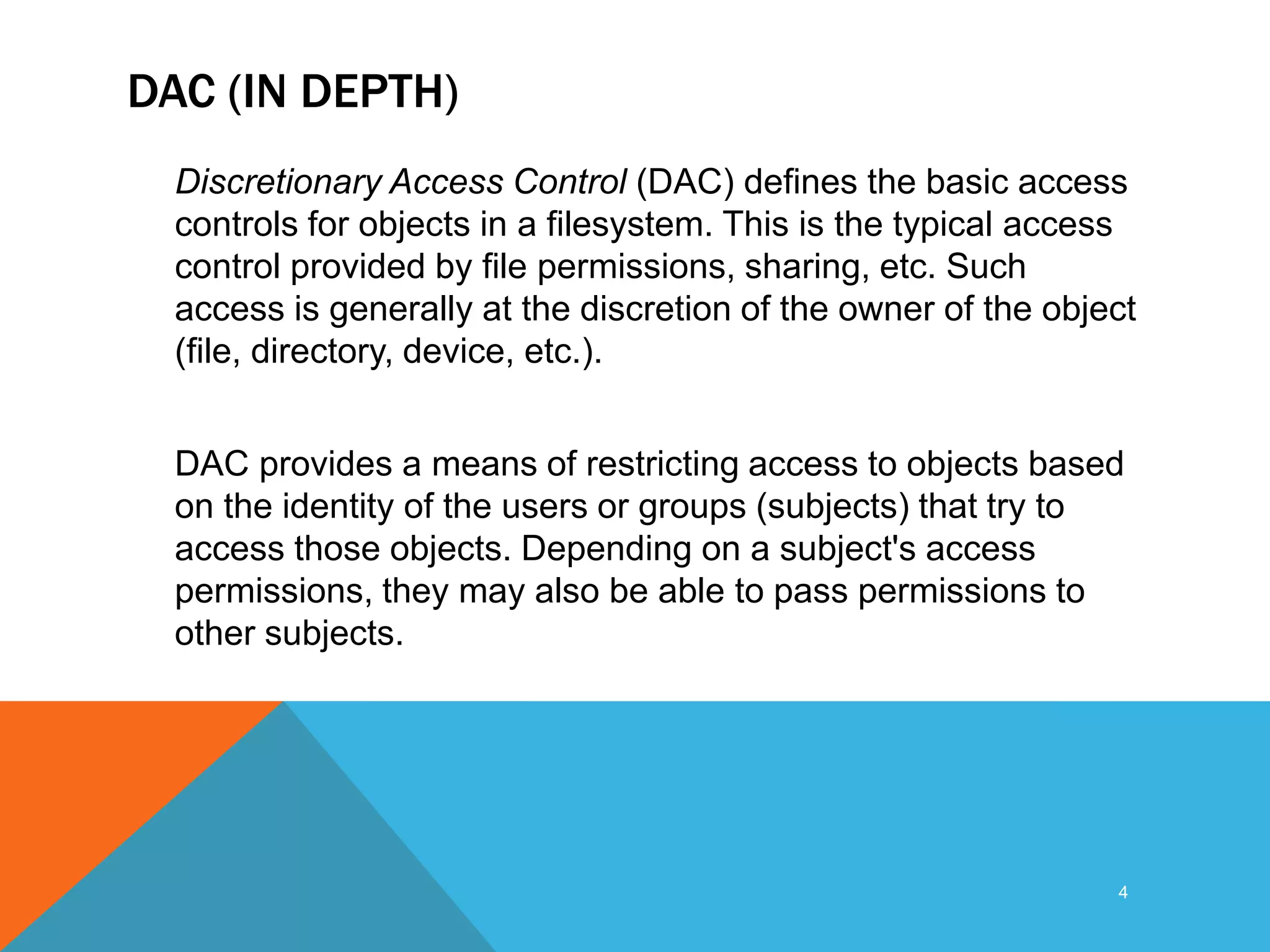
![( D A C )
5
~]$ ls -l file1 -rwxrw-r-- 1 use](https://image.slidesharecdn.com/7c0b94c3-75c2-45eb-ab10-f28d45c64a14-150304052837-conversion-gate01/75/SELinux_-gnu_group_meetup-5-2048.jpg)