The document discusses SELinux, its importance in system security, and highlights various aspects such as its policies, enforcement modes, and troubleshooting methods. It emphasizes the dangers of running applications as root and provides guidance on managing file security contexts and utilizing SELinux tools. Key topics include SELinux domains, the anatomy of access denials, and the use of audit2allow for policy adjustments.




![9
Problem: Application Trust Issues
● Trust apps are secure
●
CVEs happen, 0-days happen
● Trust apps are configured correctly
● Gartner reports 75% of mobile data breaches are configuration problems[0]
● Trust apps aren’t malware or nefarious
● SELinux does not address this
● Open source FTW
● Signed packages
● Reproducible Builds are important
● Open build systems
[0] http://www.gartner.com/newsroom/id/2753017?nicam=prsm13](https://image.slidesharecdn.com/understandingselinuxforthewin-170309225351/85/Understanding-SELinux-For-the-Win-9-320.jpg)

![17
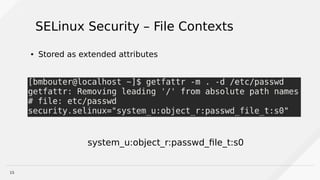
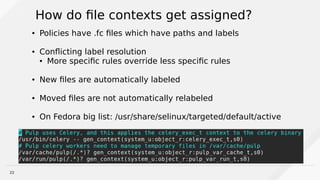
SELinux Security Context Anatomy
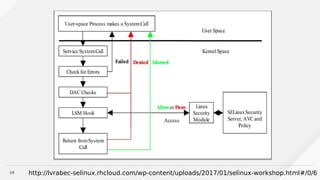
http://lvrabec-selinux.rhcloud.com/wp-content/uploads/2017/01/selinux-workshop.html#/0/11
system_u:object_r:passwd_file_t:s0
SELinux User
SELinux Role
SELinux Type
[sensitivity]](https://image.slidesharecdn.com/understandingselinuxforthewin-170309225351/85/Understanding-SELinux-For-the-Win-17-320.jpg)







![35
audit2allow
~]# audit2allow -a
#============= certwatch_t ==============
allow certwatch_t var_t:dir write;
https://access.redhat.com/documentation/en-US/Red_Hat_Enterprise_Linux/6/html/Security-Enhanced_Linux/sect-Security-
Enhanced_Linux-Fixing_Problems-Allowing_Access_audit2allow.html](https://image.slidesharecdn.com/understandingselinuxforthewin-170309225351/85/Understanding-SELinux-For-the-Win-35-320.jpg)
![36
Applying audit2allow Recommendations
~]# audit2allow -a -M mycertwatch
******************** IMPORTANT ***********************
To make this policy package active, execute:
semodule -i mycertwatch.pp
~]# ls
mycertwatch.pp mycertwatch.te
https://access.redhat.com/documentation/en-US/Red_Hat_Enterprise_Linux/6/html/Security-Enhanced_Linux/sect-Security-
Enhanced_Linux-Fixing_Problems-Allowing_Access_audit2allow.html](https://image.slidesharecdn.com/understandingselinuxforthewin-170309225351/85/Understanding-SELinux-For-the-Win-36-320.jpg)
![37
What about if AVC denials from 2+ processes
~]# grep certwatch /var/log/audit/audit.log | audit2allow -M
mycertwatch2
******************** IMPORTANT ***********************
To make this policy package active, execute:
~]# semodule -i mycertwatch2.pp
https://access.redhat.com/documentation/en-US/Red_Hat_Enterprise_Linux/6/html/Security-Enhanced_Linux/sect-Security-
Enhanced_Linux-Fixing_Problems-Allowing_Access_audit2allow.html](https://image.slidesharecdn.com/understandingselinuxforthewin-170309225351/85/Understanding-SELinux-For-the-Win-37-320.jpg)

