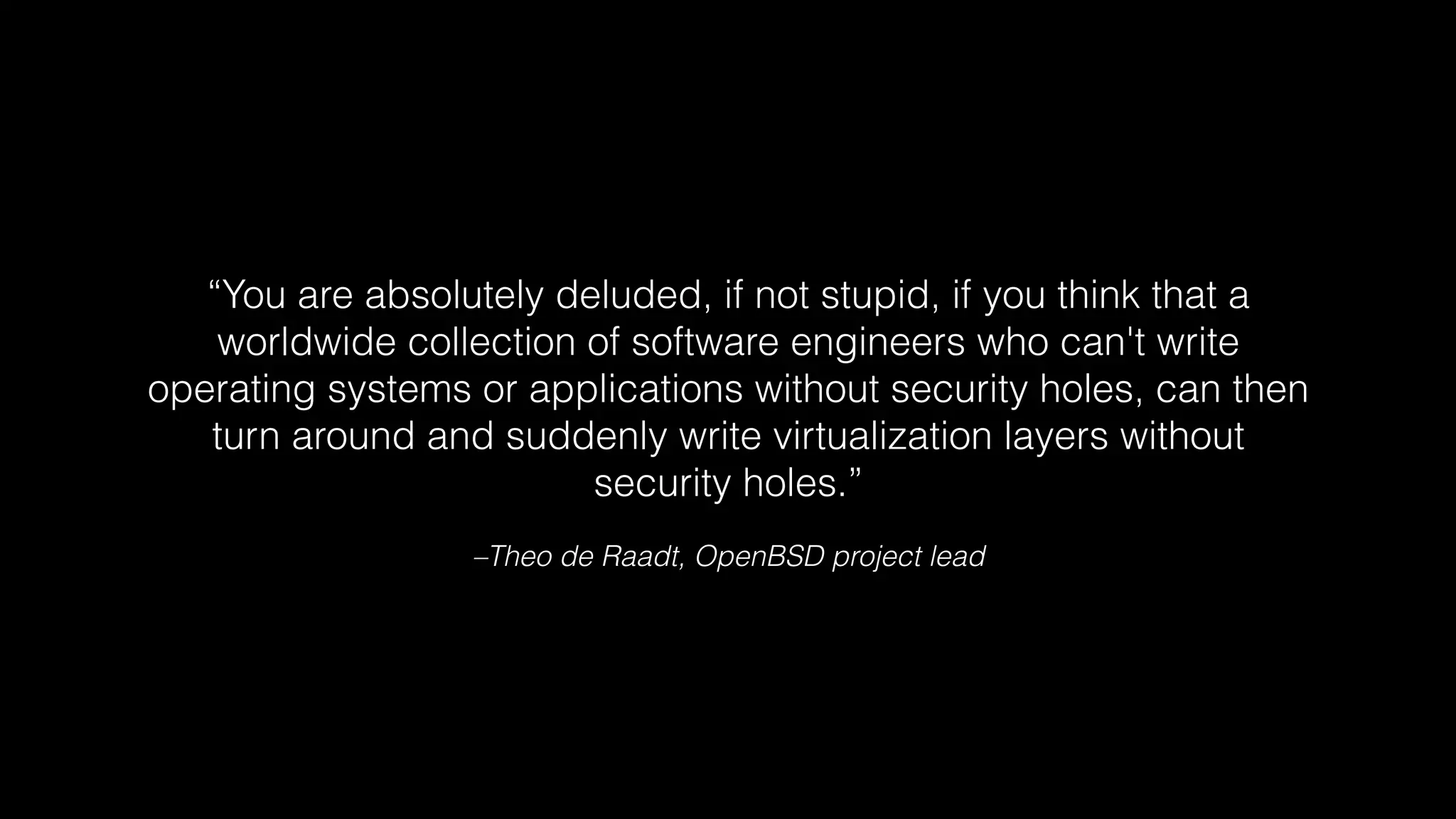
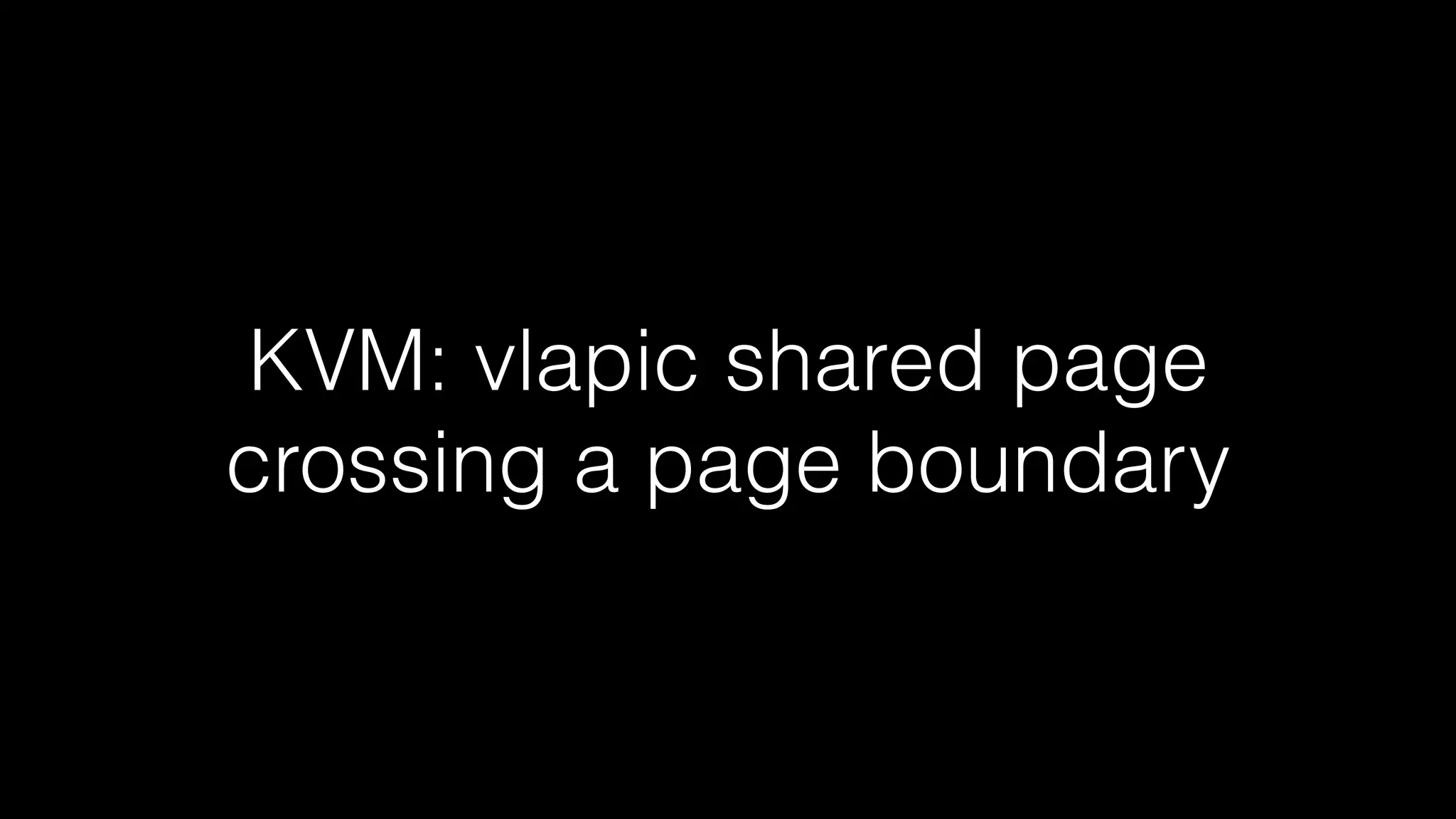
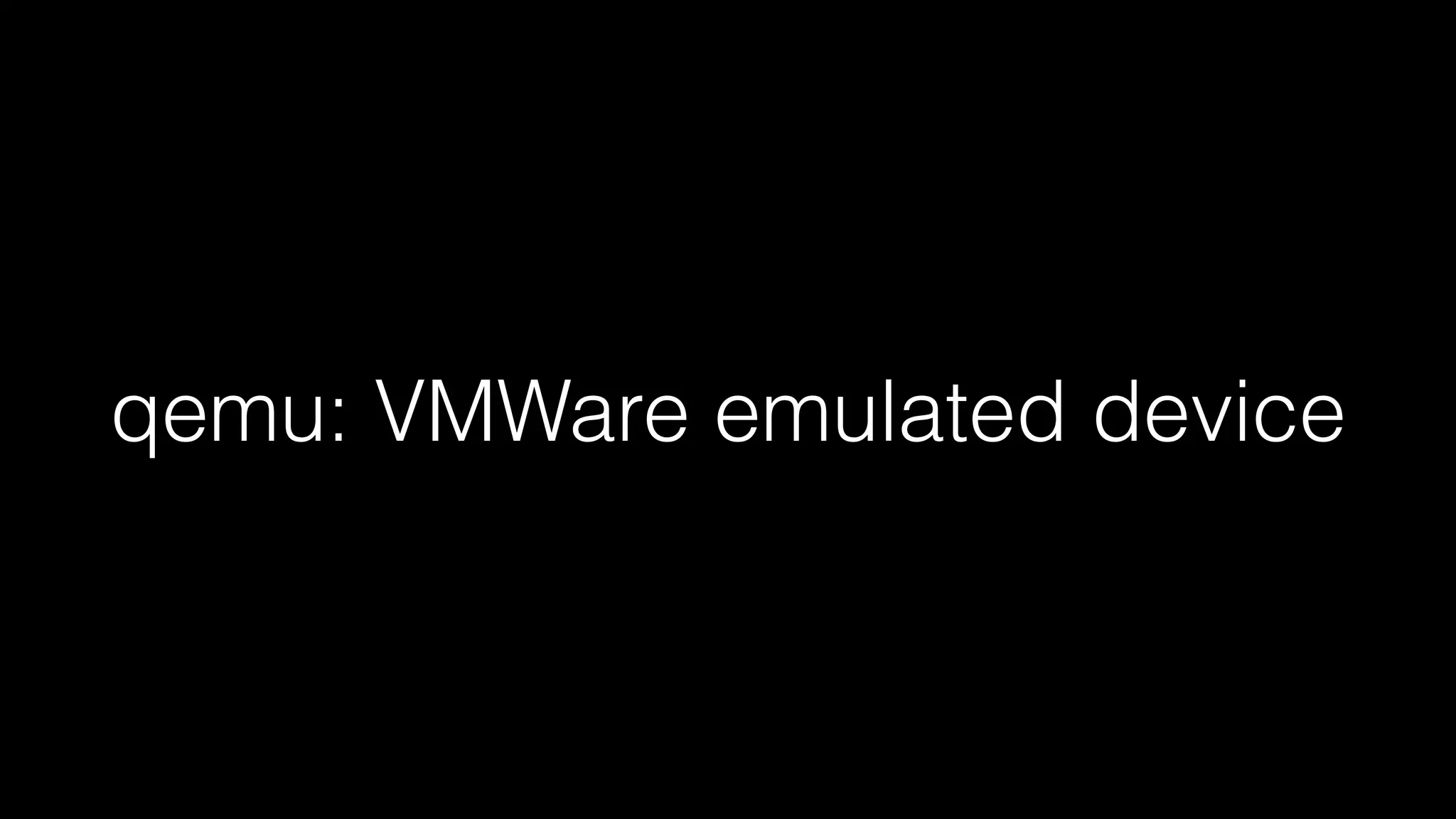
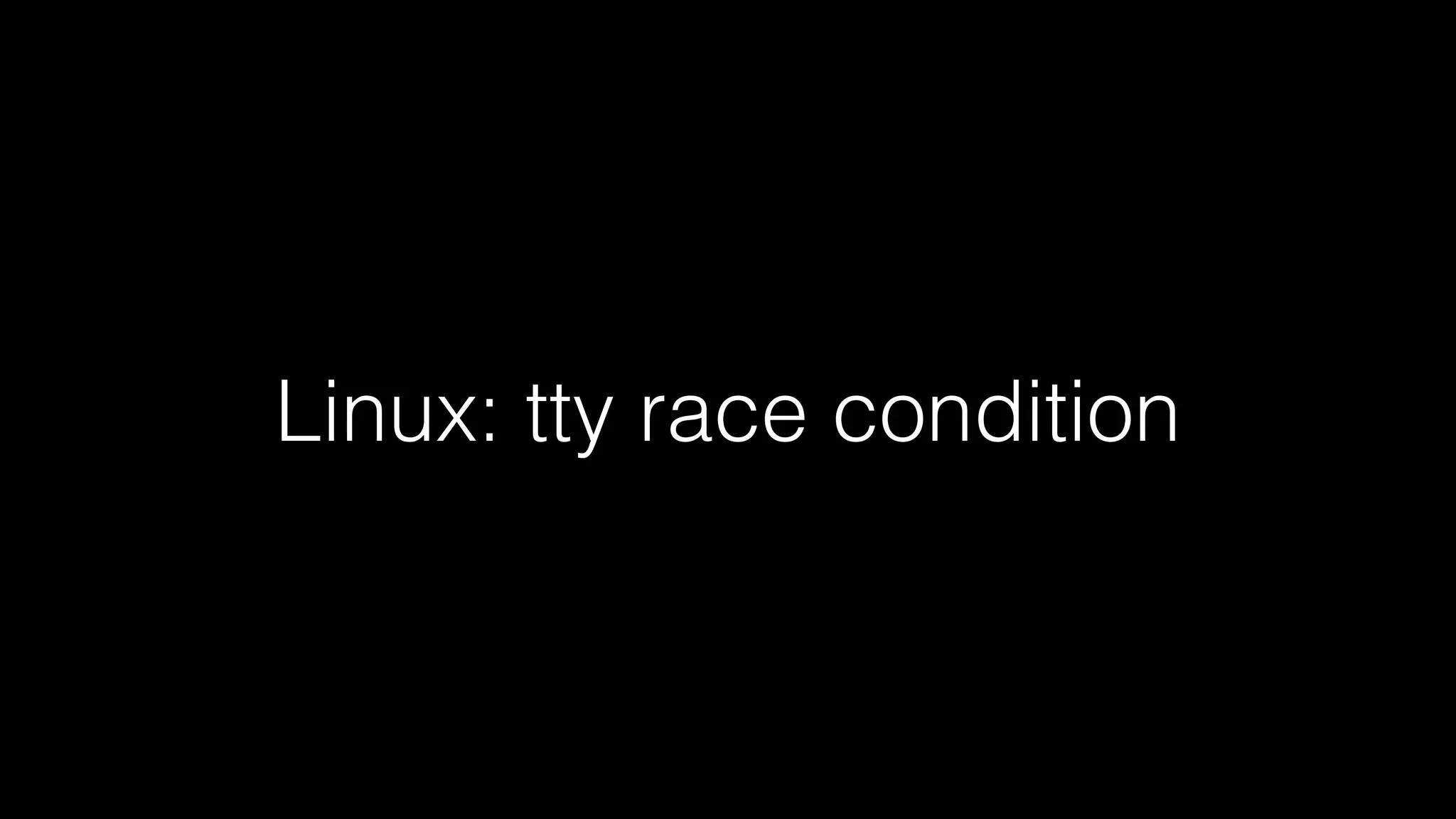
The document discusses the security comparisons between containers and virtual machines, citing varying expert opinions on their relative safety and vulnerabilities. It highlights the ongoing debate about the security of virtualization layers and contains specific examples of known vulnerabilities in Xen, KVM, QEMU, and Linux. The overarching theme emphasizes the importance of configuration and the potential for mistakes in security management across all systems.