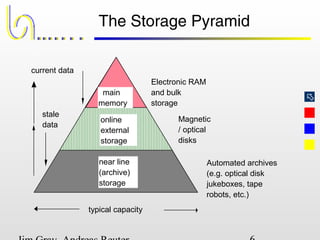
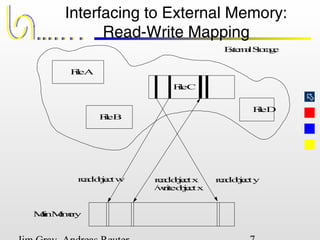
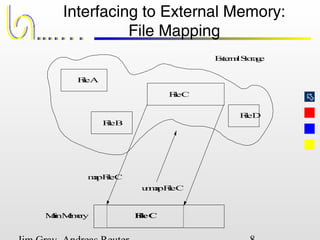
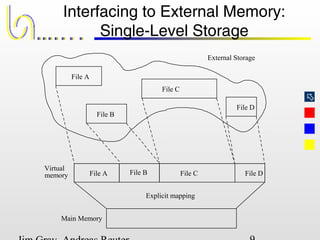
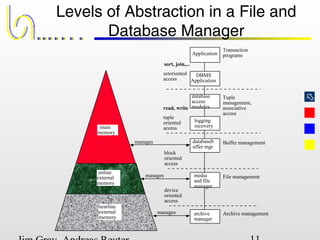
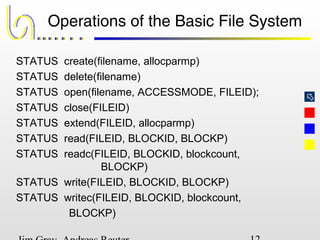
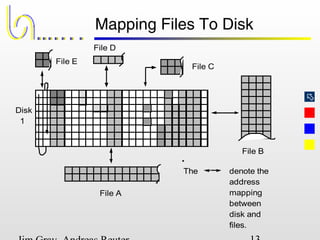
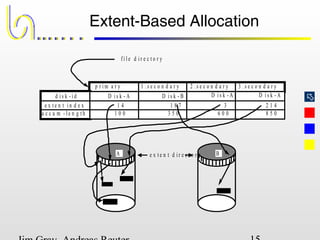
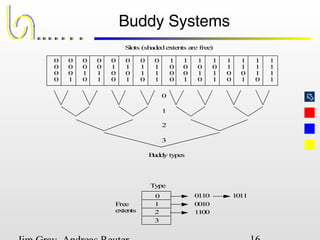
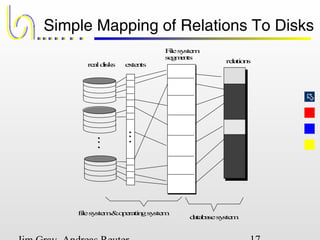
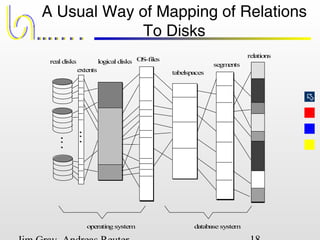
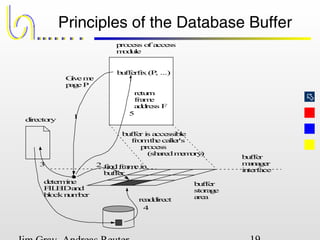
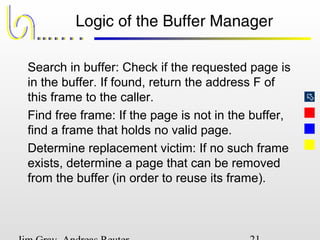
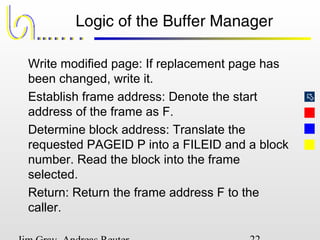
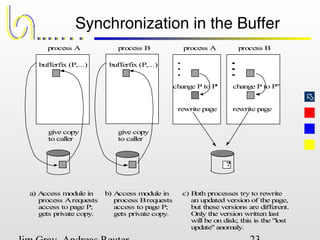
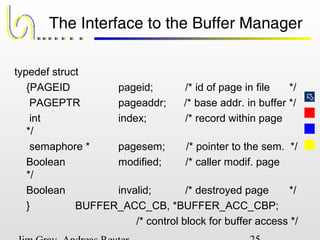
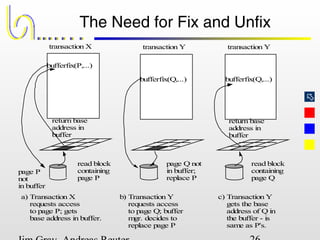
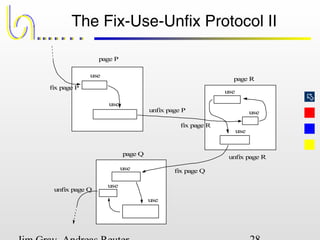
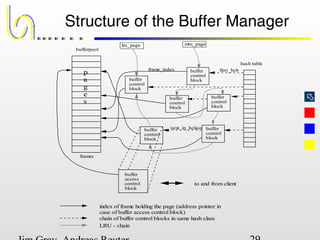
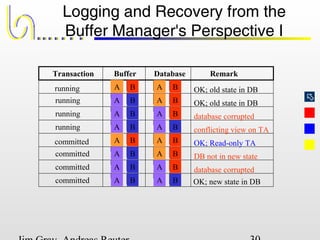
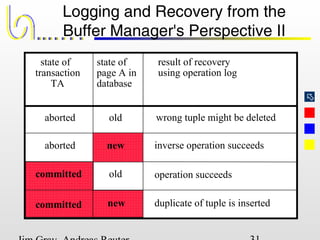
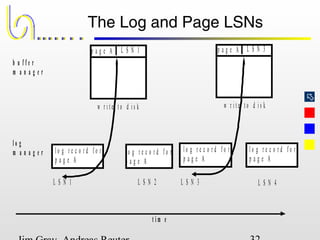
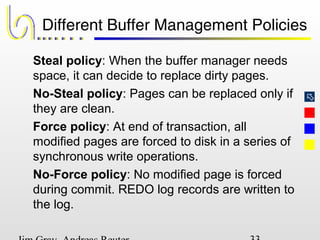
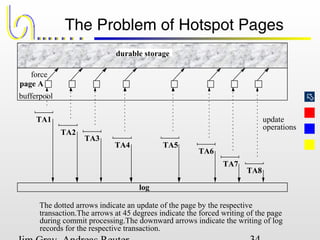
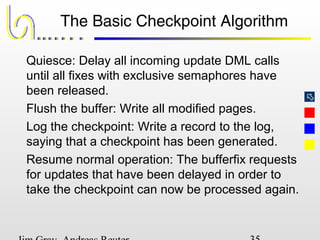
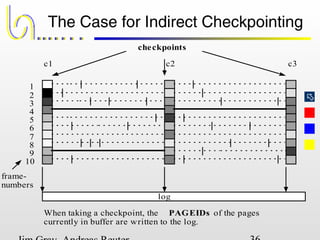
This document discusses the file and buffer manager components of a database system. It describes how the file manager provides abstractions like device, allocation, and address independence. It also explains how the buffer manager caches data from external storage in main memory using techniques like logging, locking, and checkpointing to ensure data integrity and concurrency control during transaction processing. Key aspects of the buffer manager covered include its interface, replacement policies, and how it supports recovery through logging and maintaining page-level write-ahead logs.