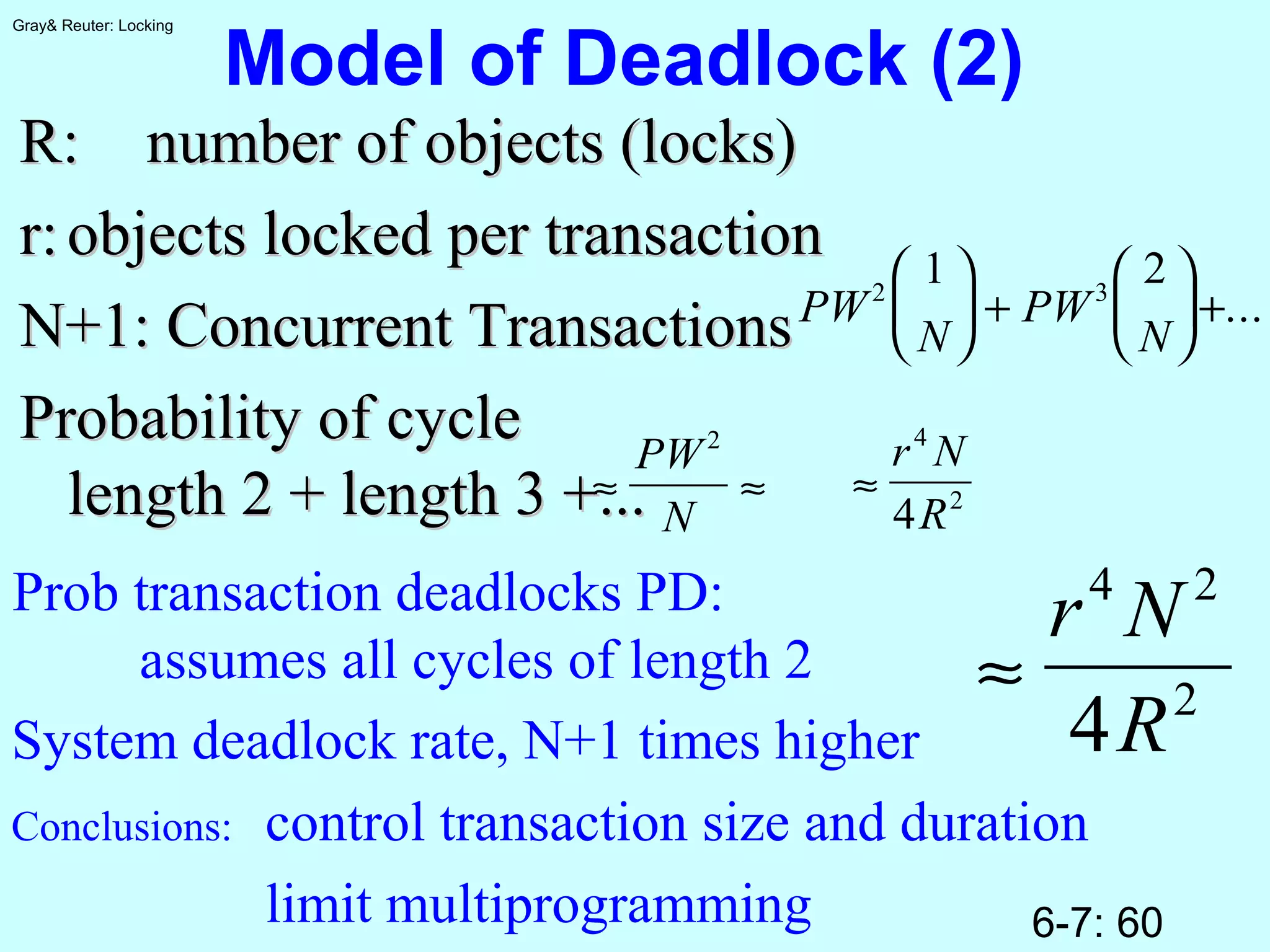
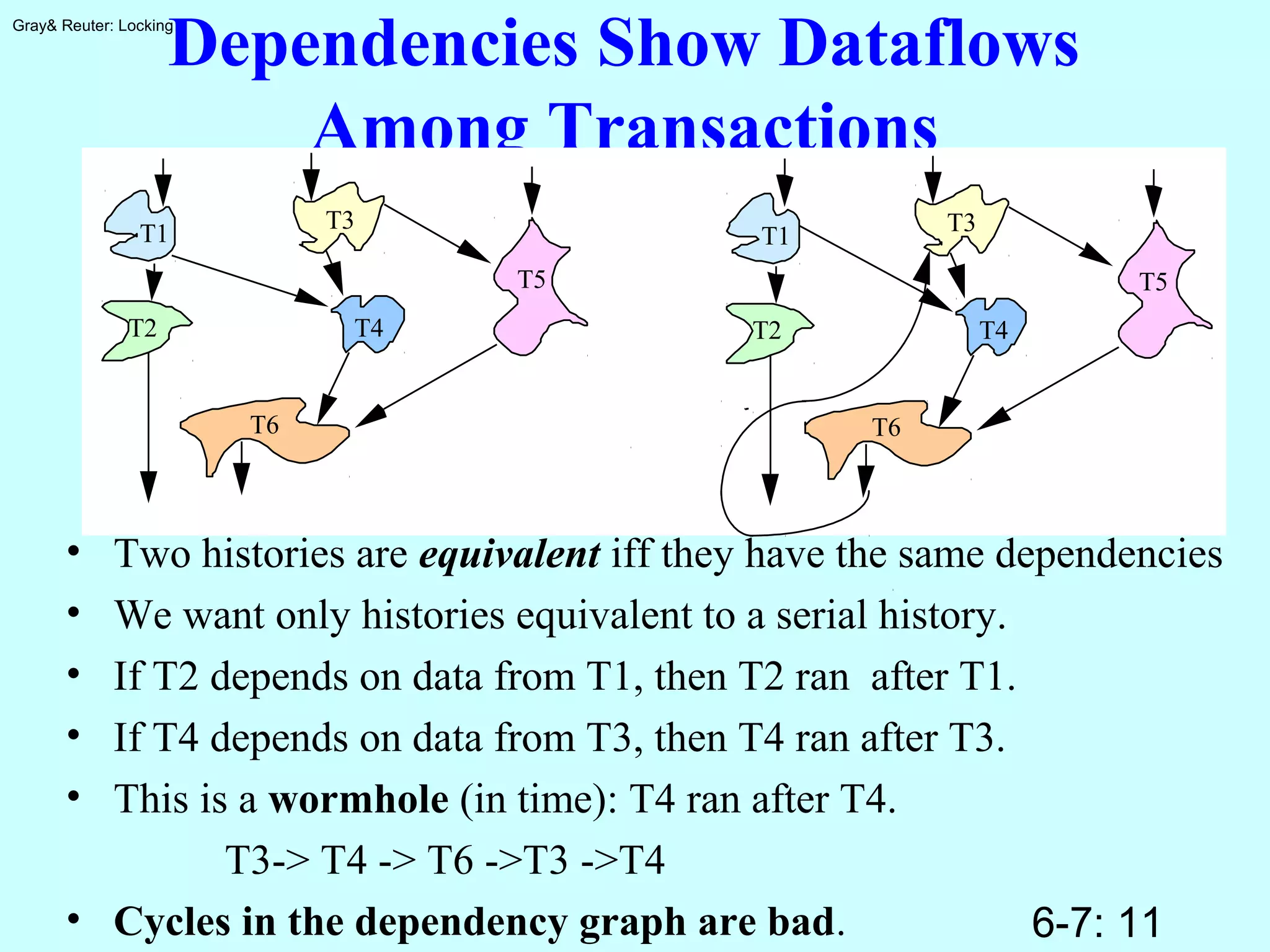
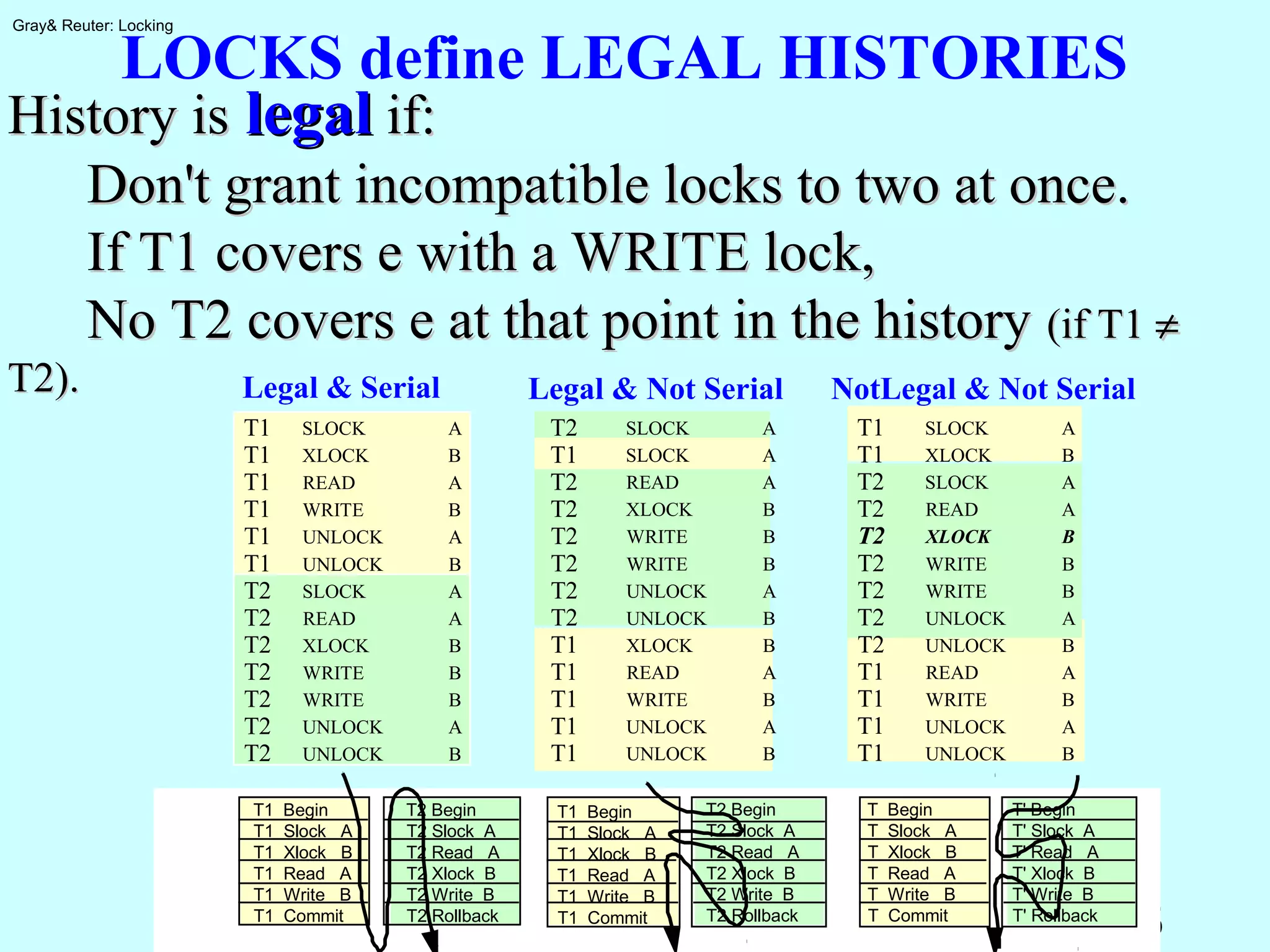
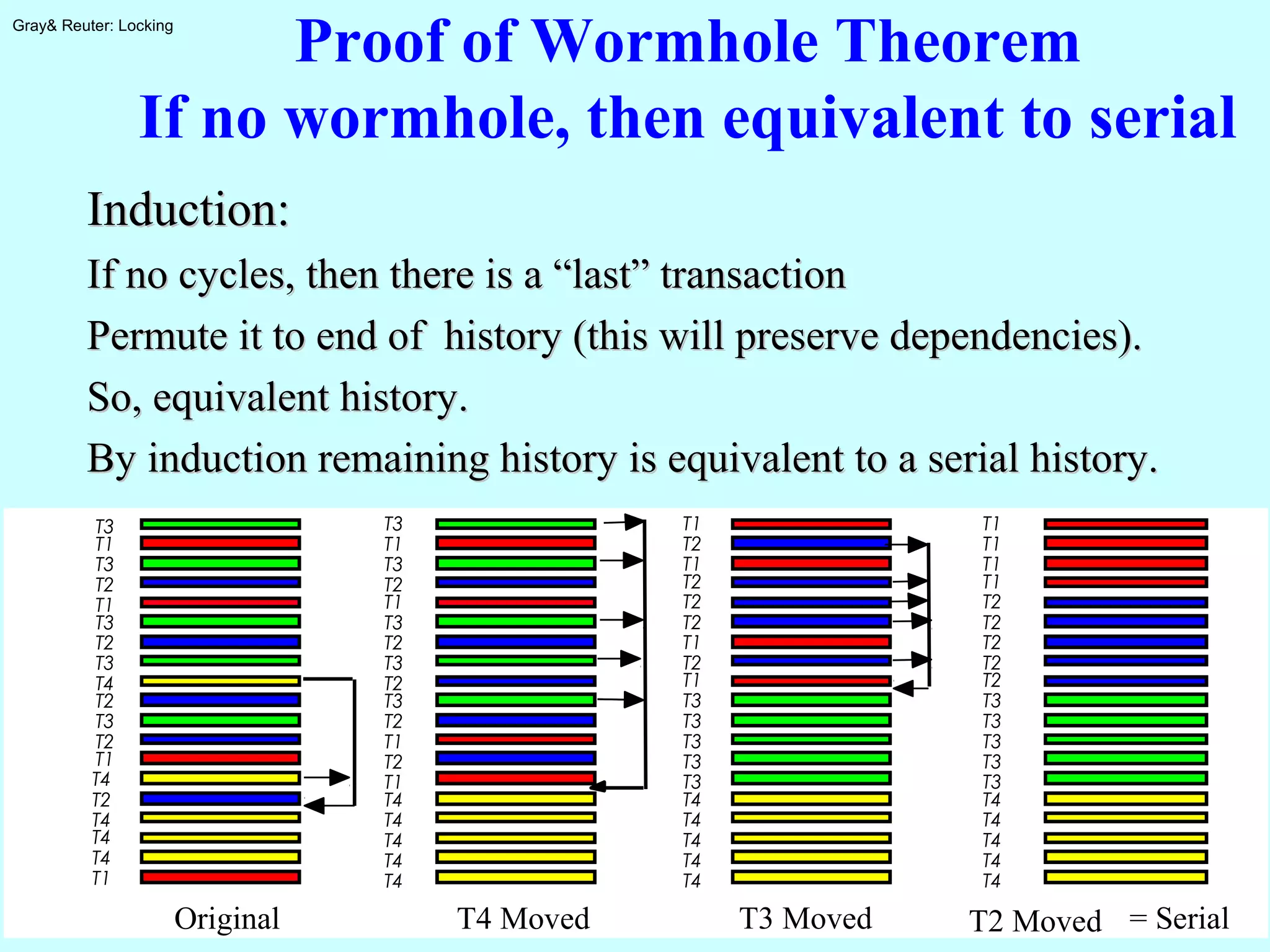
The document discusses locking for concurrency control in databases. It begins by outlining the key topics to be covered, including why locking is used, when to lock, what to lock, how to lock, exotic locking techniques, deadlocks, and performance. It then discusses why locking is needed to provide transaction isolation and ensure equivalent execution to some serial schedule. The document introduces formal definitions of transactions, histories, equivalence, and dependency graphs. It describes the three bad transaction dependencies that locking aims to prevent. Finally, it discusses how locks can be used to define legal histories and proves the serializability theorem.










![6-7: 12
Gray& Reuter: Locking
Locks Cover Actions
Introduce three new actions:Introduce three new actions:
LOCK [READ | WRITE]LOCK [READ | WRITE]
UNLOCKUNLOCK
Lock <Ti, LOCK a, e >Lock <Ti, LOCK a, e > CoversCovers
<Ti, a', e><Ti, a', e>
IfIf
<Ti, a', e> is at or after the lock step<Ti, a', e> is at or after the lock step
ANDAND
No intervening unlockNo intervening unlock
ANDAND
a is WRITE OR a' IS READa is WRITE OR a' IS READ
(write covers write and read)(write covers write and read)
t slock o1
t xlock o2
t read o1
t read o3
t write o1
t write o2
t read o2
t unlock o1
t unlock o2
t unlock o3
Not Covered
Not Covered
Not Covered](https://image.slidesharecdn.com/0607lock-150218104243-conversion-gate02/75/06-07-lock-12-2048.jpg)
























![6-7: 40
Gray& Reuter: Locking
Key Range Locking
(for Phantoms)
Suppose operations are:Suppose operations are:
Read(key)Read(key);; /* return current value/* return current value */*/
Write(key, value)Write(key, value); /* set key's value; /* set key's value */*/
Delete(key)Delete(key);; /* delete key + value/* delete key + value */*/
Read_Next(key)Read_Next(key);; /* returns next key + val/* returns next key + val */*/
Insert between X and Y must test to see thatInsert between X and Y must test to see that
No one else cares that [X,Y] was empty, but isNo one else cares that [X,Y] was empty, but is
now fullnow full
no other concurrent trans did a Read_Next("X");).no other concurrent trans did a Read_Next("X");).](https://image.slidesharecdn.com/0607lock-150218104243-conversion-gate02/75/06-07-lock-40-2048.jpg)










![6-7: 52
Gray& Reuter: Locking
Escrow Locking
Schemes that hold locks at end of Ø1 fail to solve hot spotSchemes that hold locks at end of Ø1 fail to solve hot spot
problem for distributed system since ø1 to Ø2 transitionproblem for distributed system since ø1 to Ø2 transition
may take timemay take time
Idea:Idea: leave value fuzzy,leave value fuzzy,
store minimum and maximum valuesstore minimum and maximum values
Poly-values of (Warren Montgomery's MIT thesis)Poly-values of (Warren Montgomery's MIT thesis)
Escrow locking of (Pat O’Neil)Escrow locking of (Pat O’Neil)
Example: I order 100 widgets:Example: I order 100 widgets:
quantityquantity was:was: [1000,1000][1000,1000]
now is:now is: [900, 1000][900, 1000]
I commitI commit now is:now is: [900, 900][900, 900]
No locks are heldNo locks are held
Works only for commutative opsWorks only for commutative ops](https://image.slidesharecdn.com/0607lock-150218104243-conversion-gate02/75/06-07-lock-52-2048.jpg)