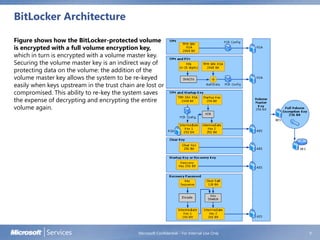
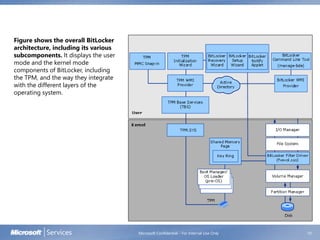
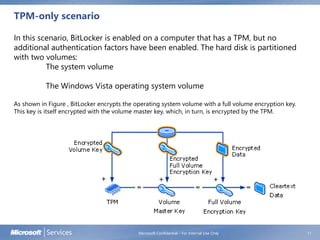
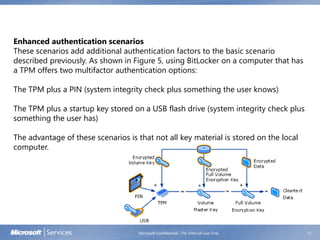
BitLocker Drive Encryption helps prevent unauthorized access to data on lost or stolen computers by encrypting volumes and verifying integrity of early boot components. It uses a Trusted Platform Module to store encryption keys and check system integrity on startup. While a TPM is preferred, BitLocker can also use a USB drive to store keys. The document discusses BitLocker concepts, architecture, system requirements, group policy settings, and getting started.