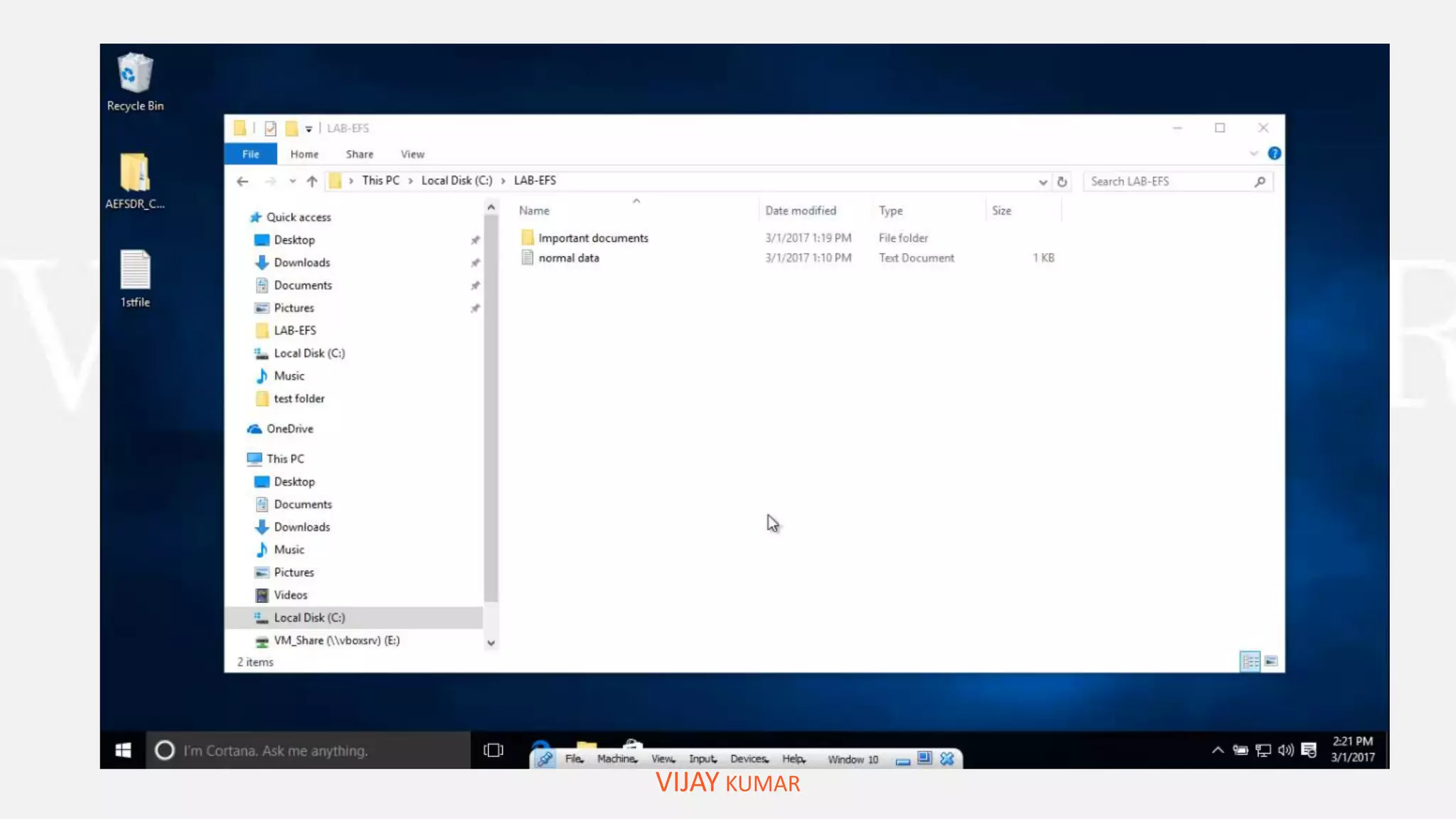
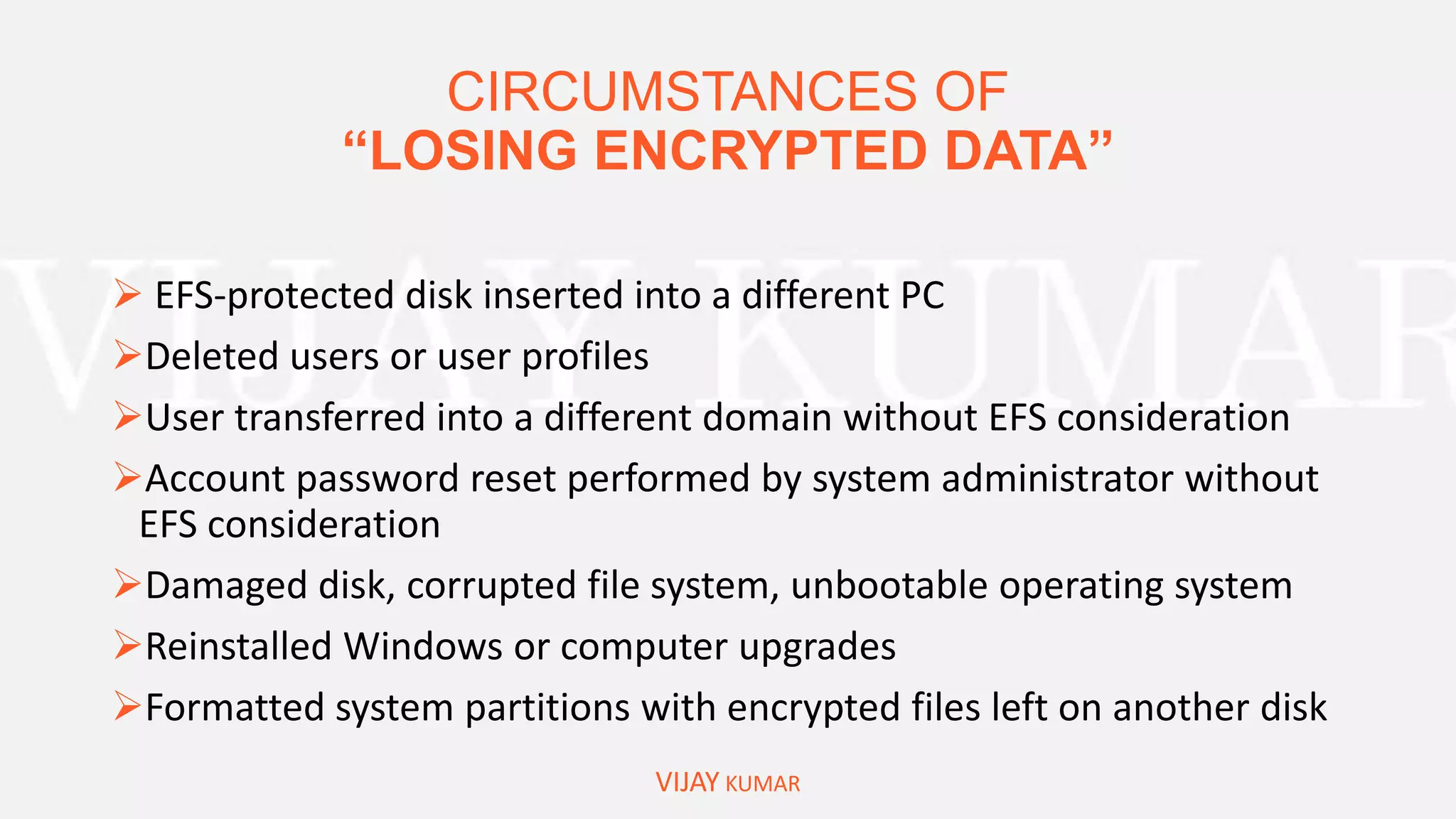
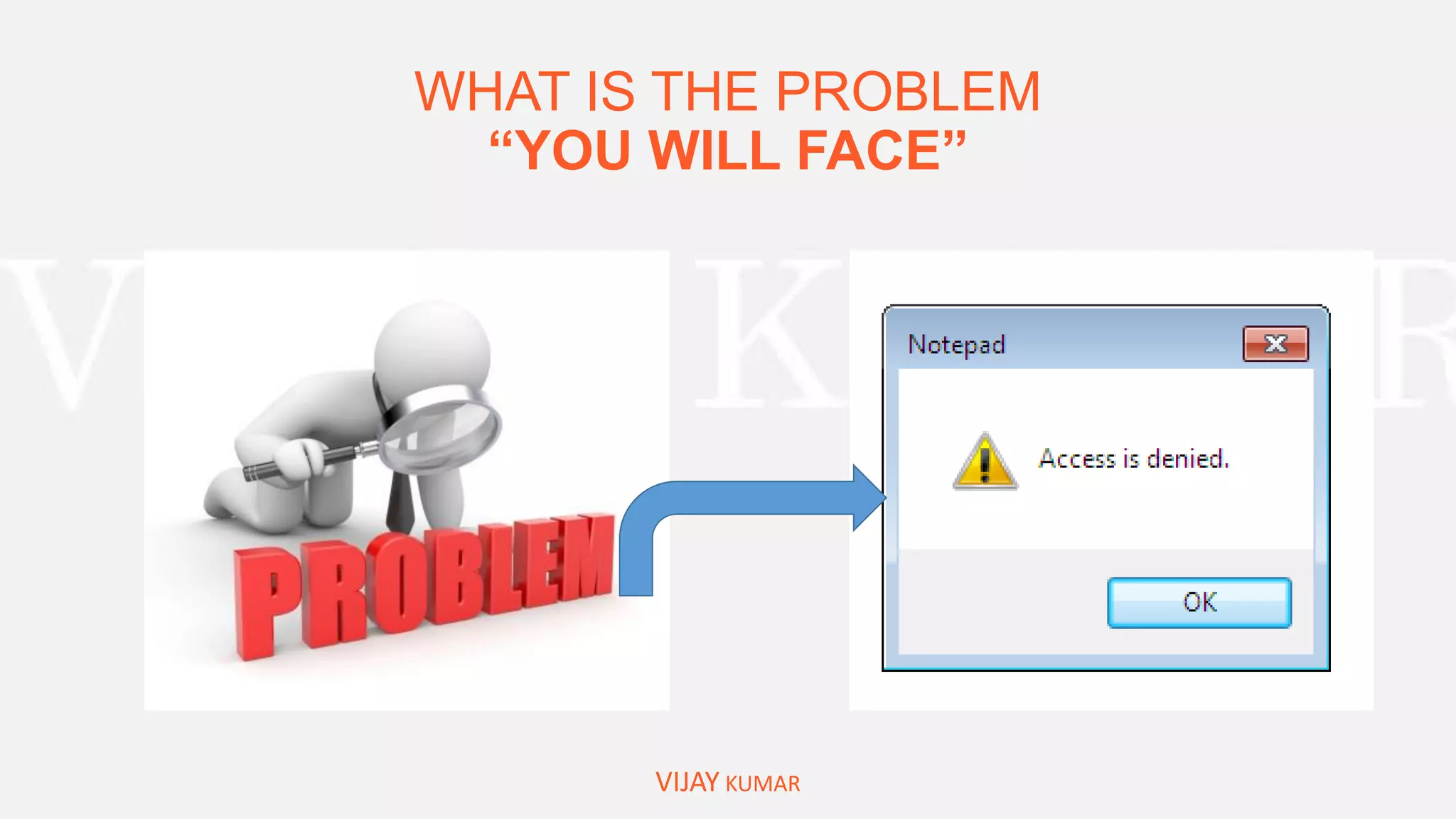
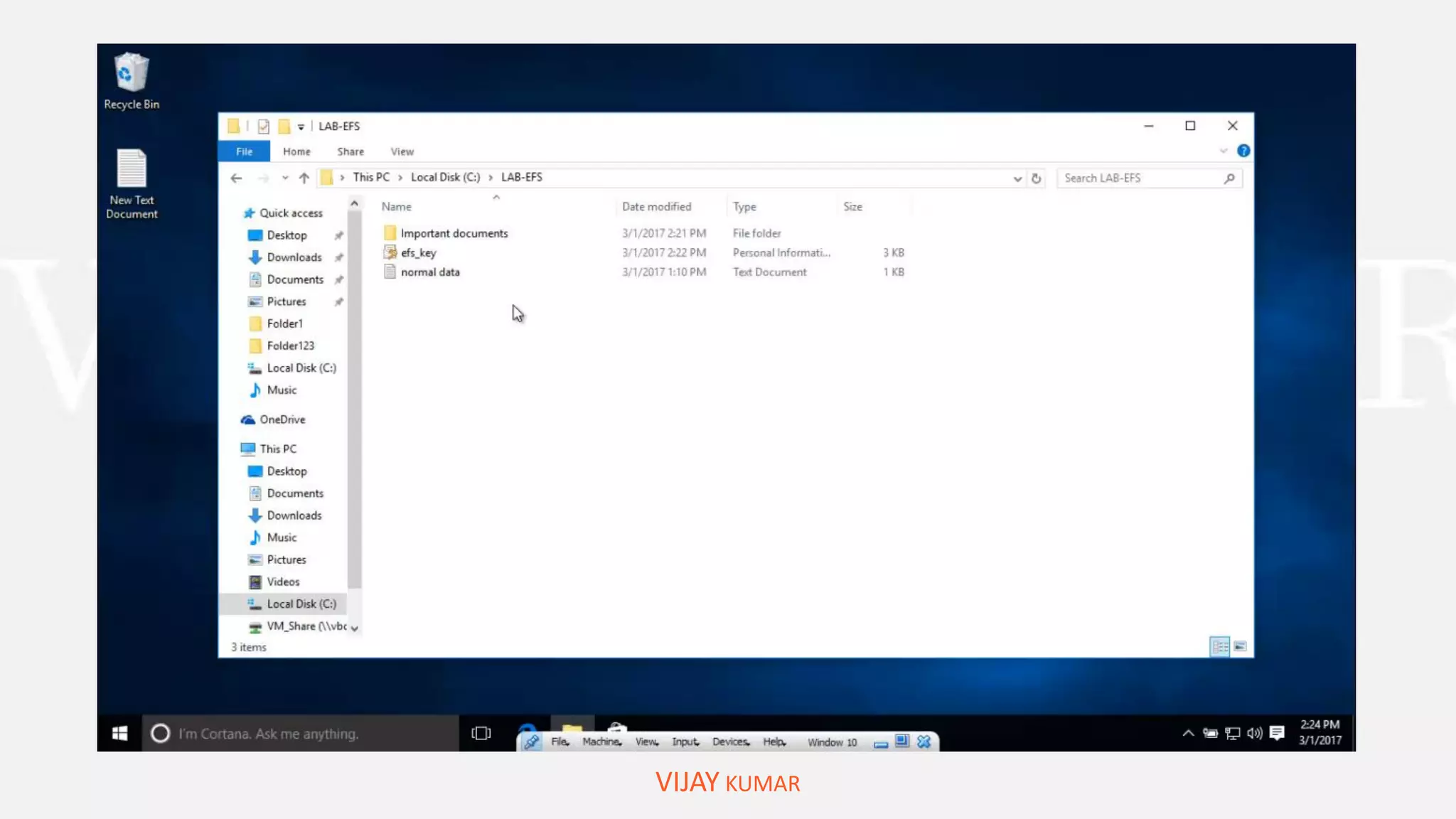
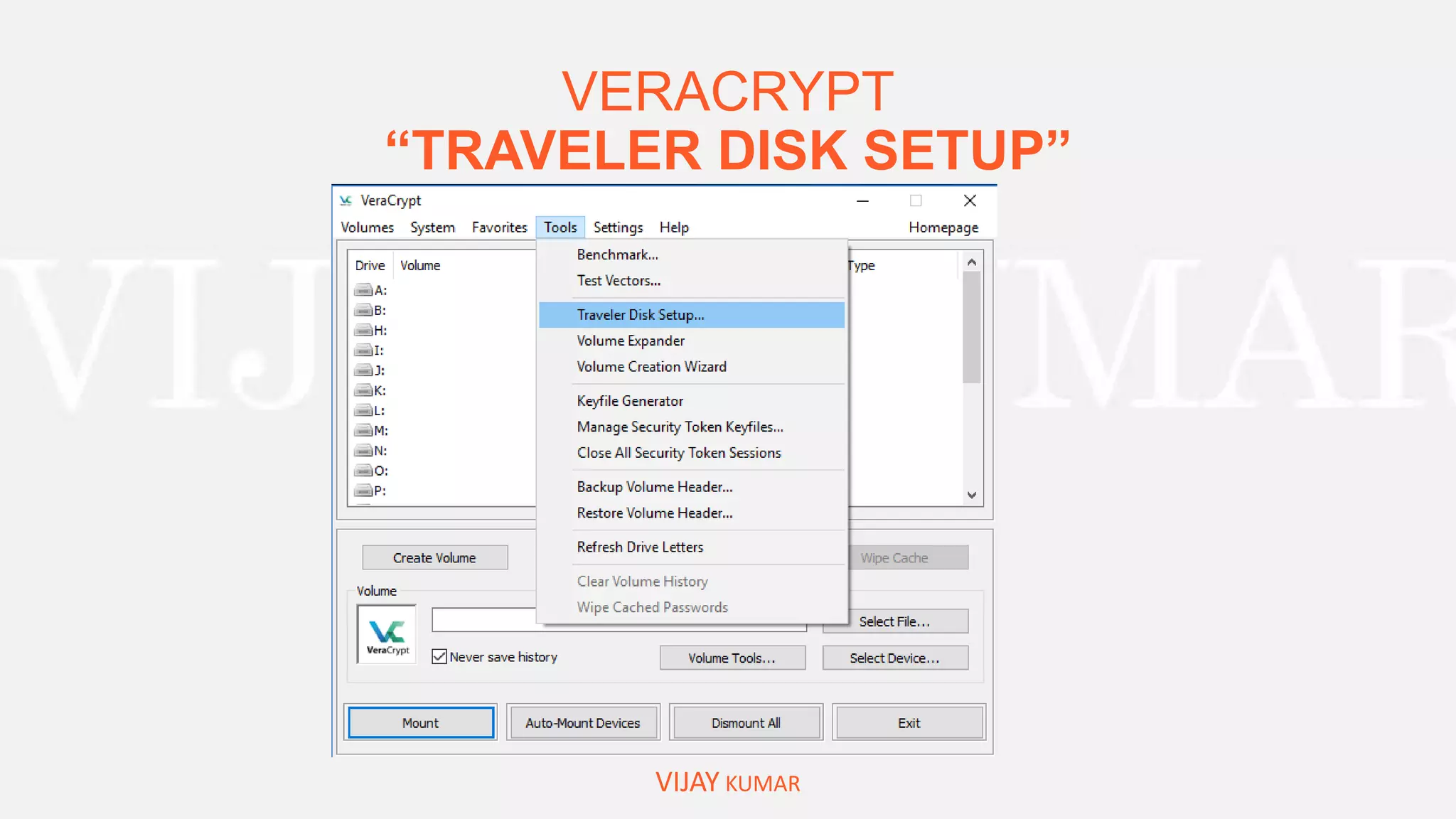
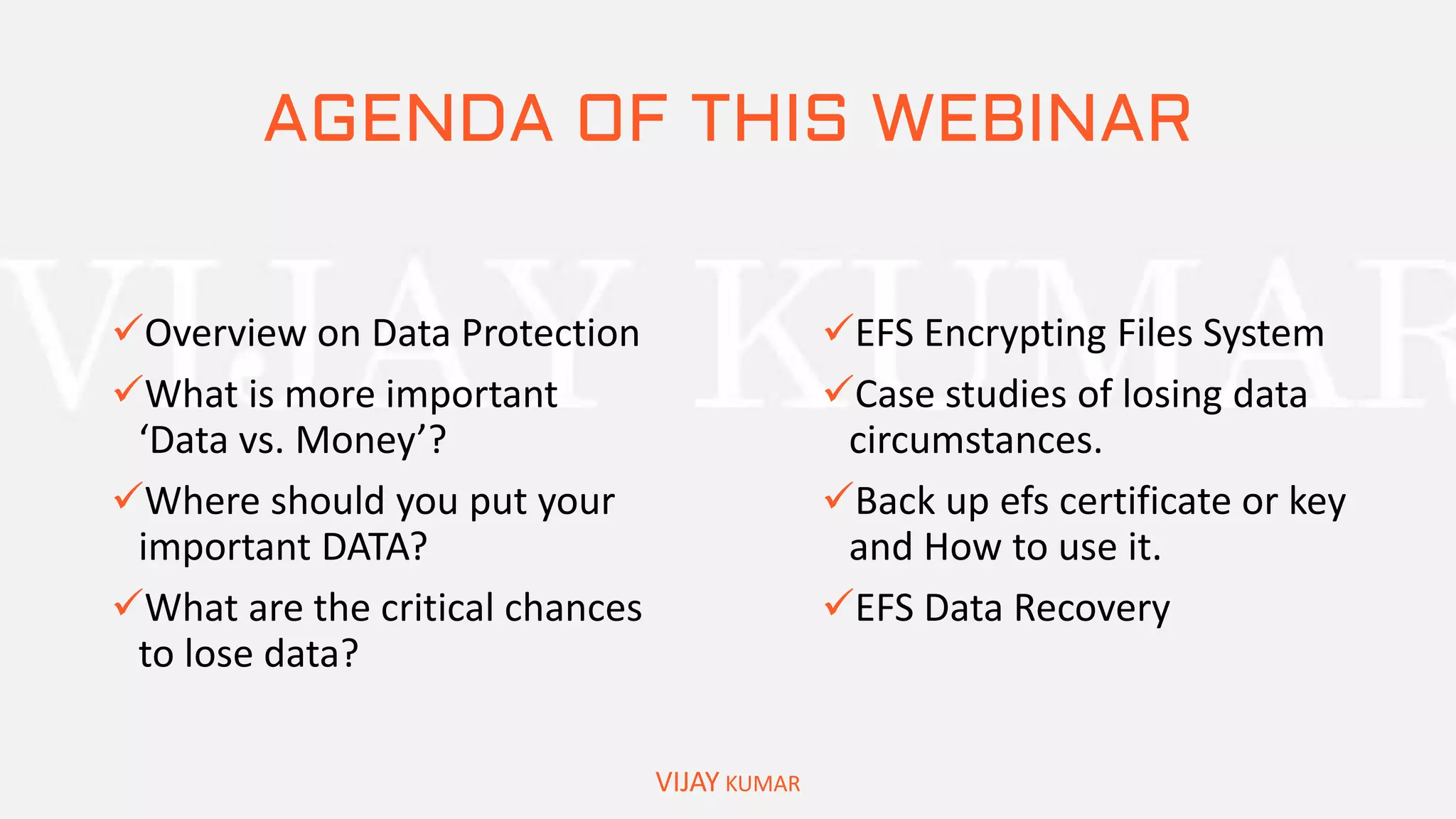
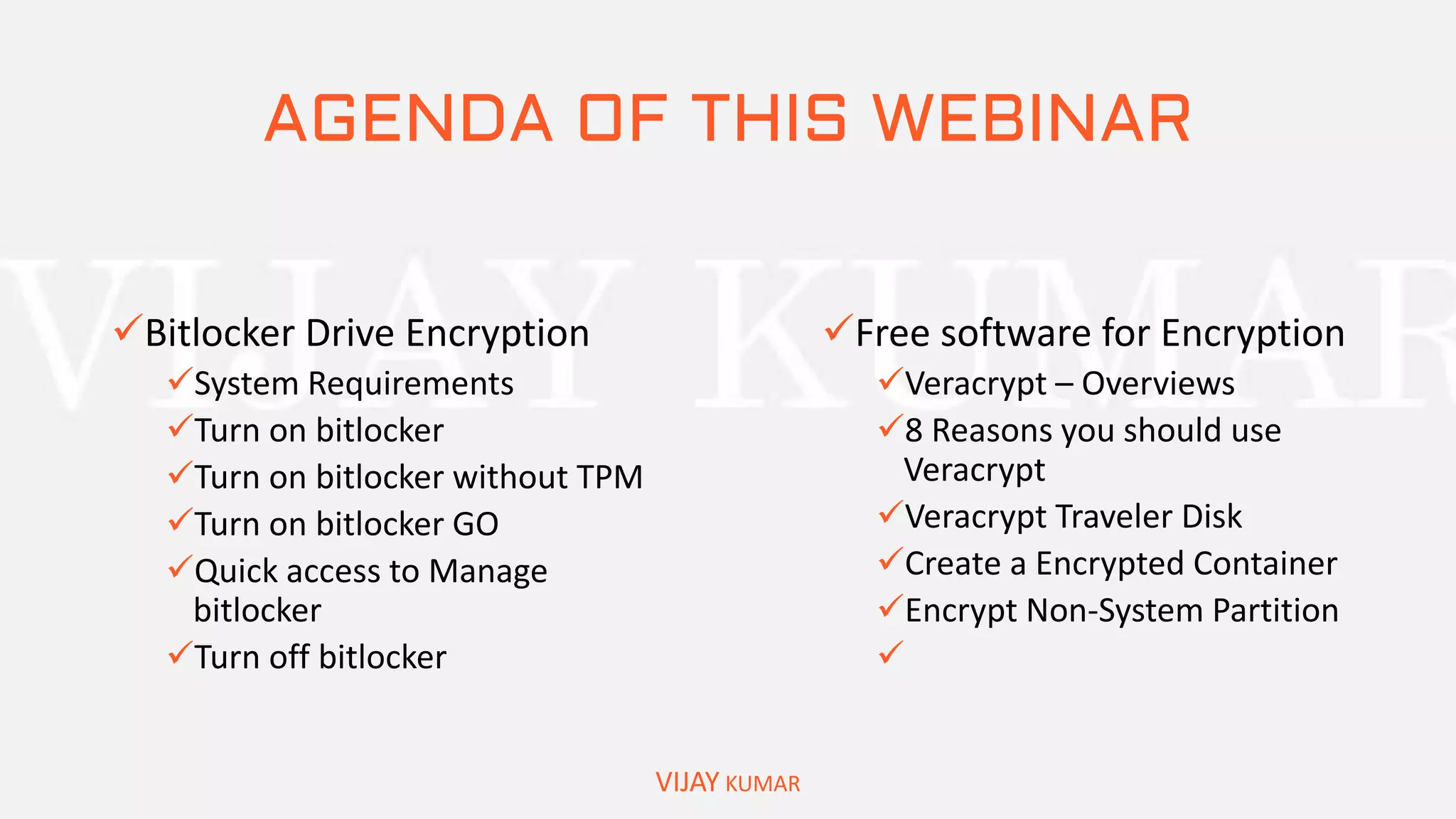
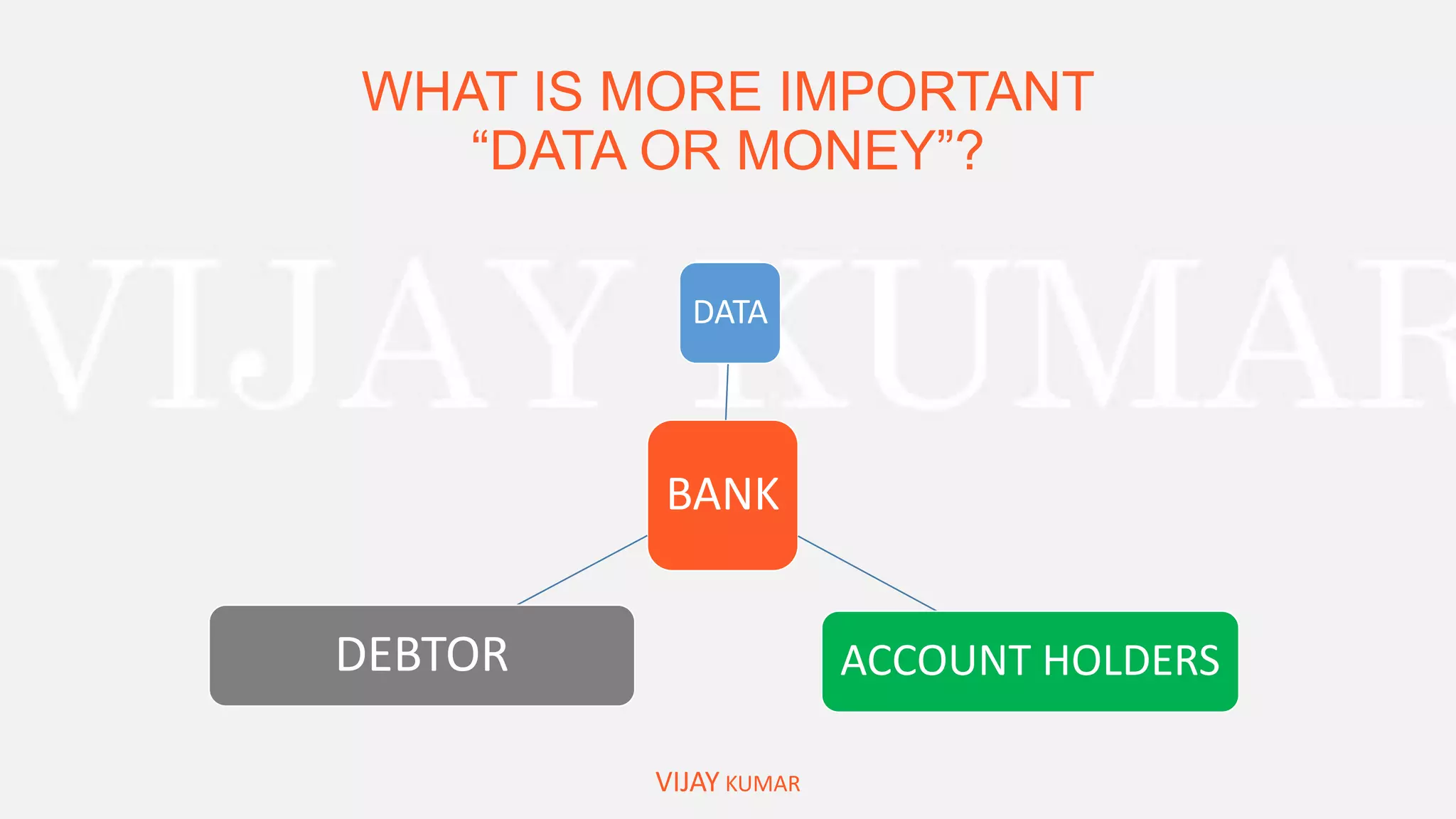
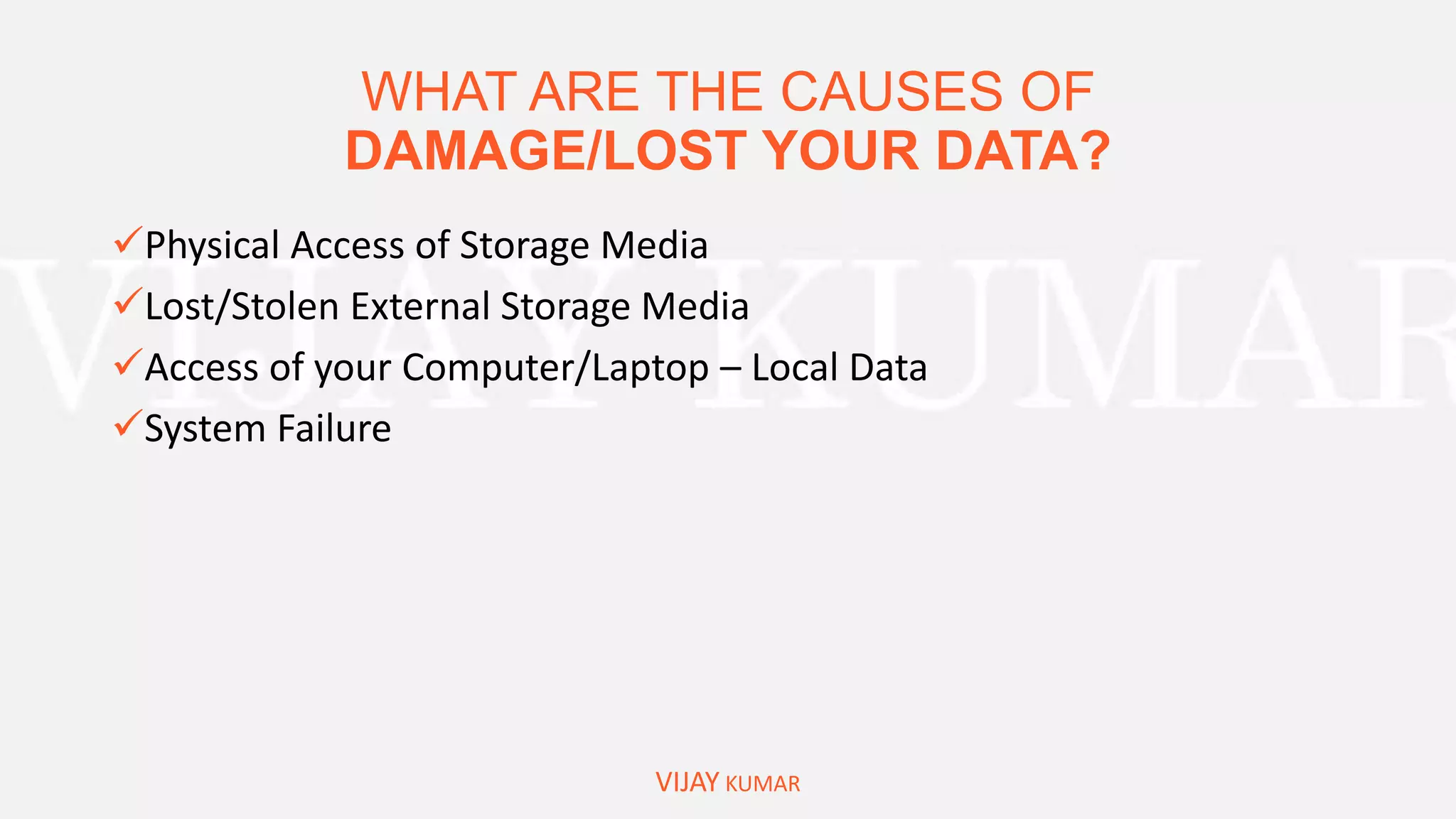
The webinar presents methods for protecting important data without spending money, emphasizing data encryption using tools like EFS and BitLocker as well as free software like VeraCrypt. Key topics include the significance of data security, common causes of data loss, and step-by-step demonstrations of how to encrypt files, create secure containers, and recover lost data. Attendees are encouraged to engage with questions and feedback regarding the content and methods discussed.




![METHODS TO
ENCRYPT DATA IN WINDOWS
VIJAY KUMAR
Encrypting File System [EFS] for files and folders
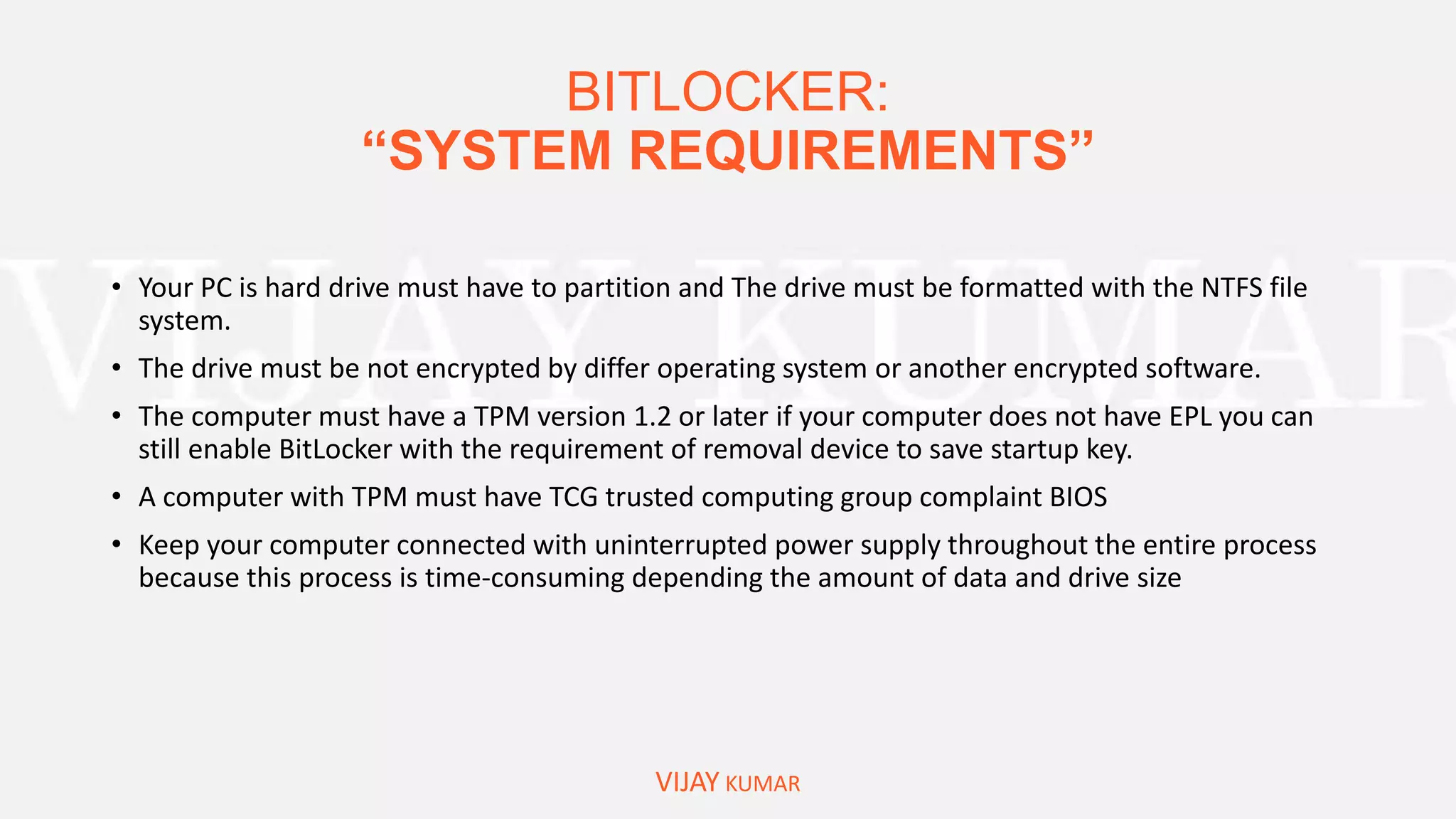
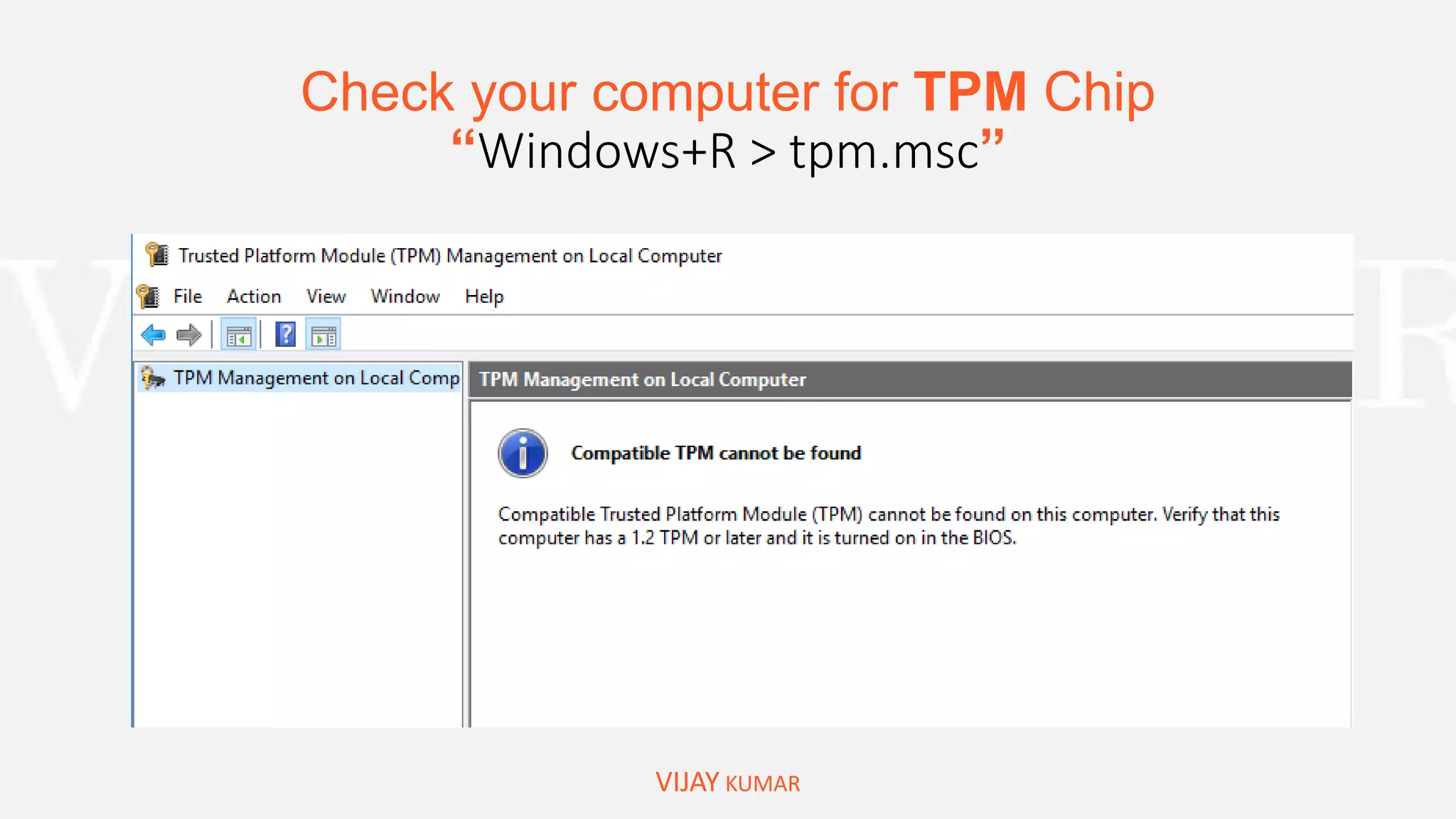
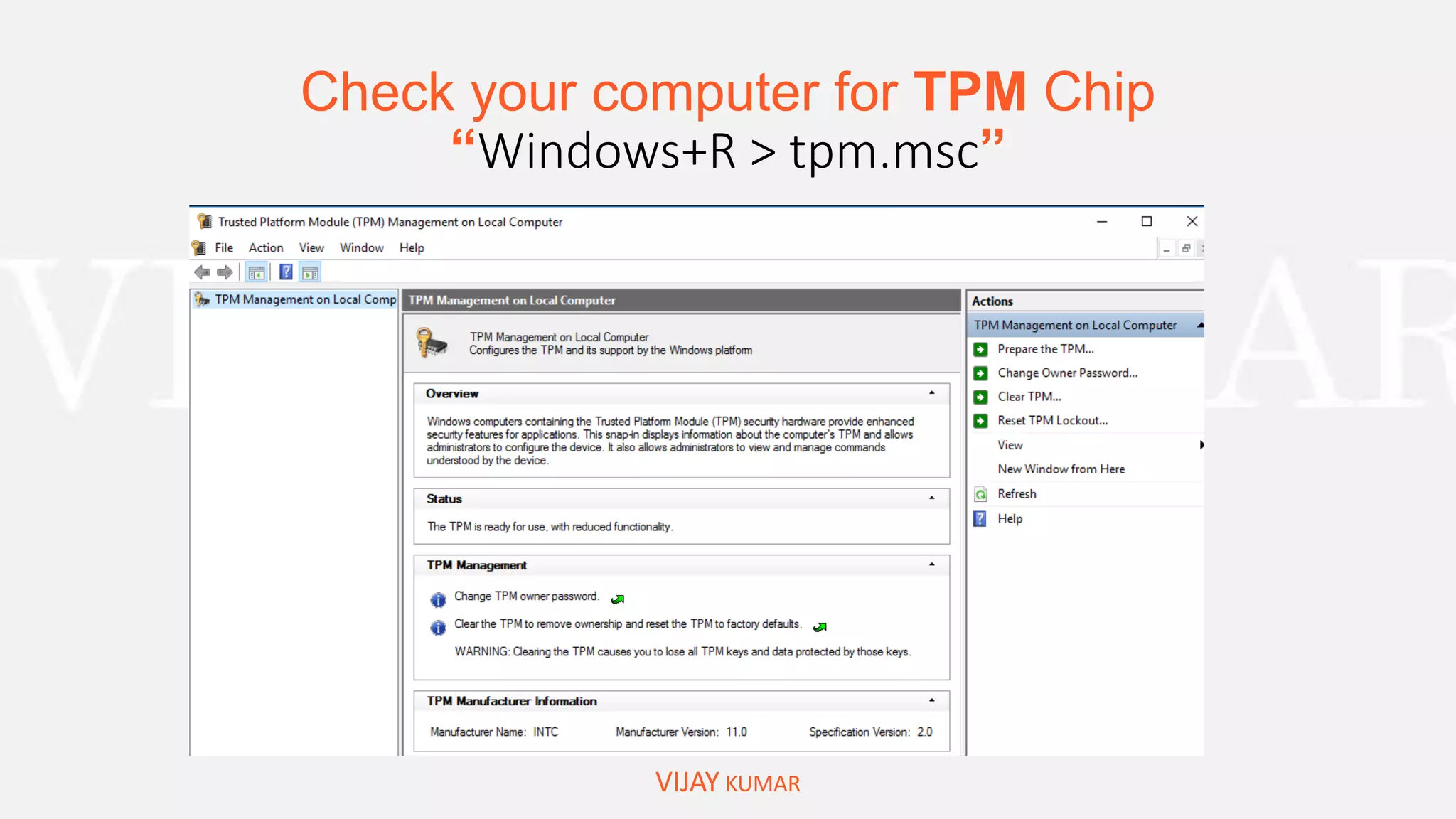
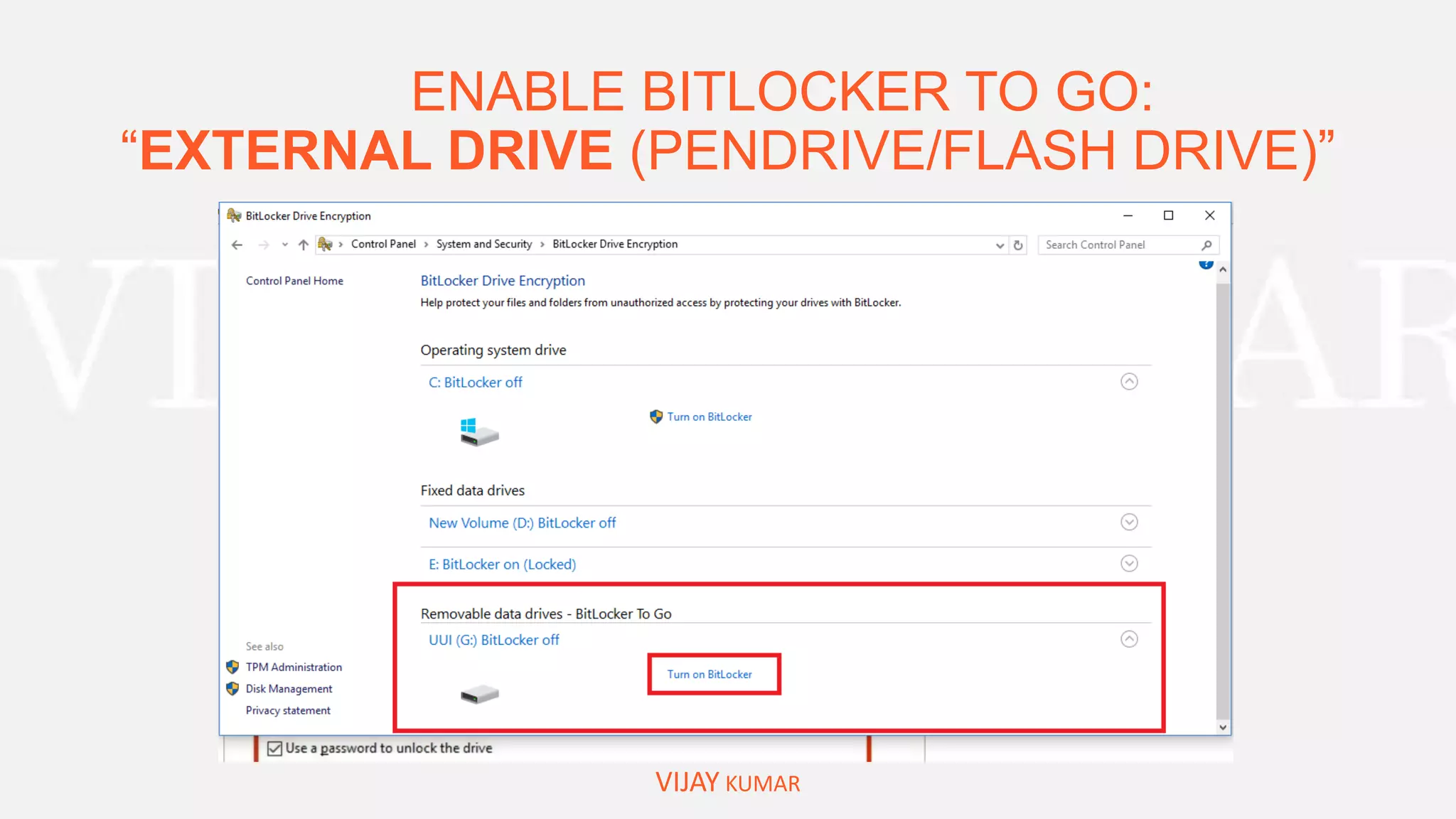
Bitlocker to Encrypt Drive/System Drive
Other Free third party Software's](https://image.slidesharecdn.com/dataprotectioninwindows-170305164834/75/Data-protection-in-windows-9-2048.jpg)
![OVERVIEW ON
“ENCRYPTING FILE SYSTEM [efs]”
VIJAY KUMAR
Microsoft Encrypting File System (EFS) is an integral part of Microsoft Windows operating systems
that enables users to protect their files against unauthorized access even from those who gain
physical access to the hard disk or the computer that contains the encrypted files. Windows XP,
2003, Vista, Windows 7, Windows 8, Windows 8.1, Windows 10, Windows Server 2008, Windows
Server 2012](https://image.slidesharecdn.com/dataprotectioninwindows-170305164834/75/Data-protection-in-windows-10-2048.jpg)