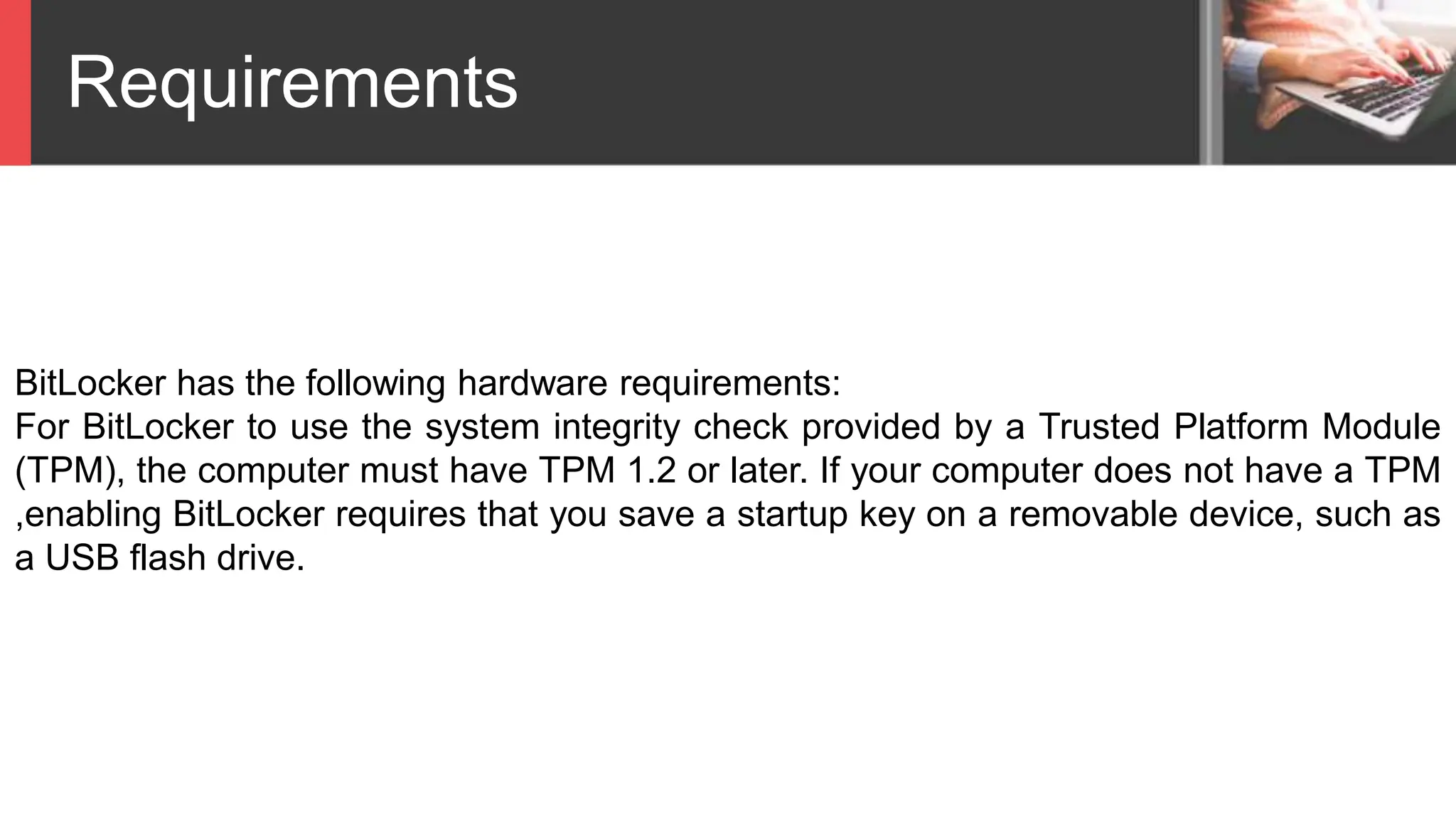
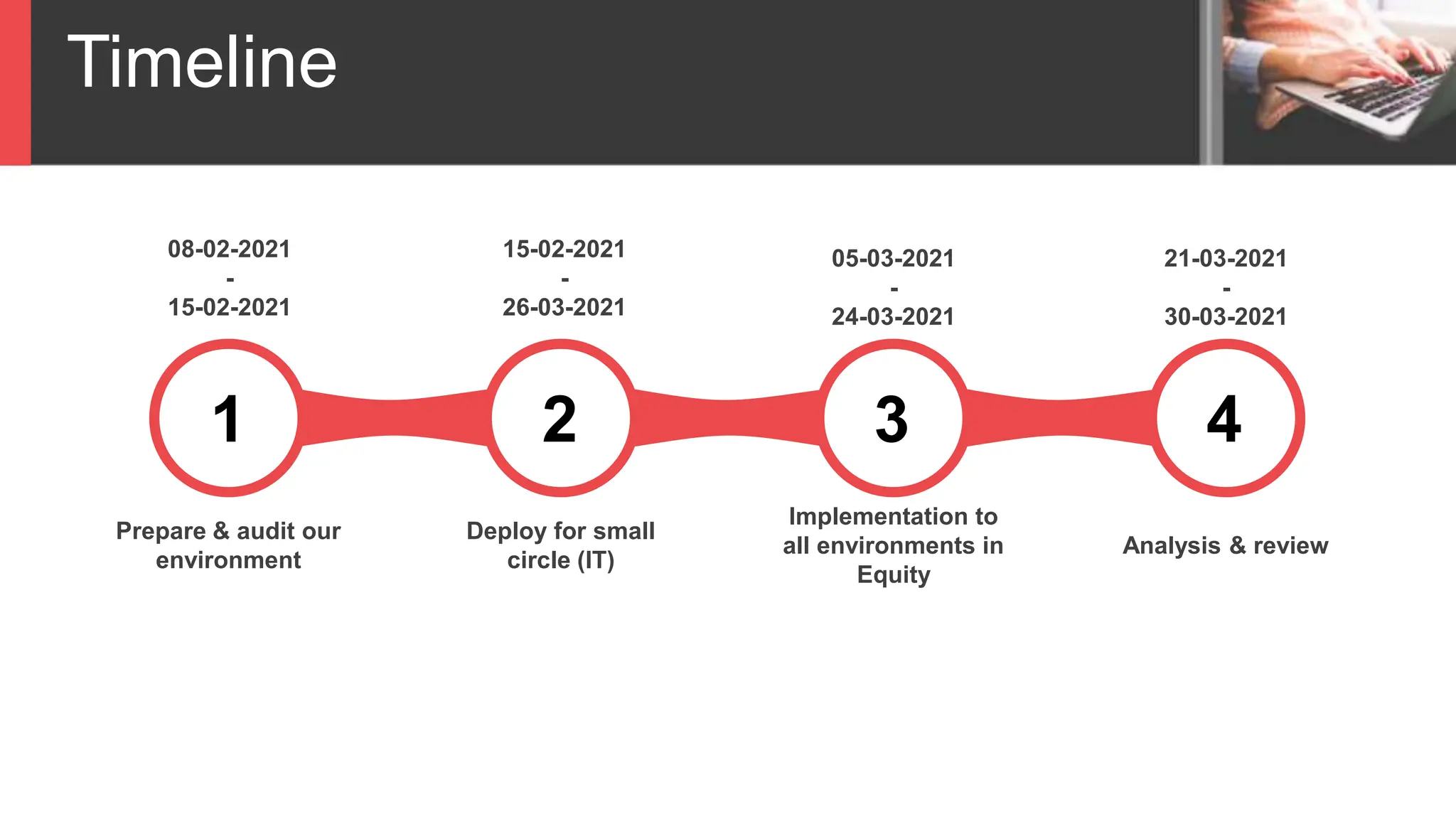
Bitlocker is a data encryption feature that protects against data theft. It requires a TPM hardware component for full disk encryption. When planning Bitlocker implementation, an organization must determine which drives to encrypt, the authentication method, and how to support non-Windows 10 Pro computers. Policies are also needed to define which devices use Bitlocker, how recovery keys are stored, identity validation for recovery, access to recovery data, and device decommissioning. The document outlines a timeline for preparing the environment, initial small deployment to IT, full deployment to all environments, and final review.