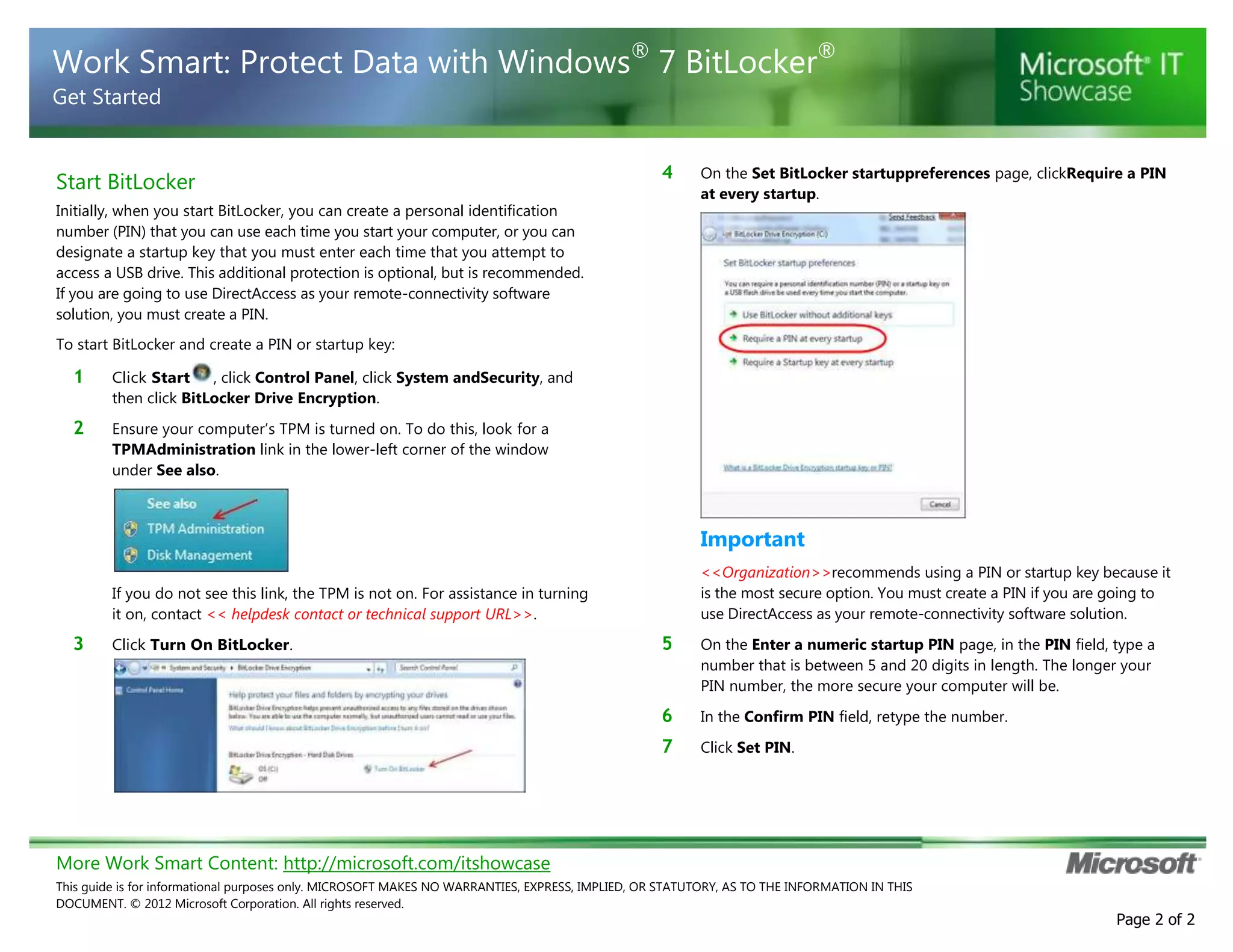
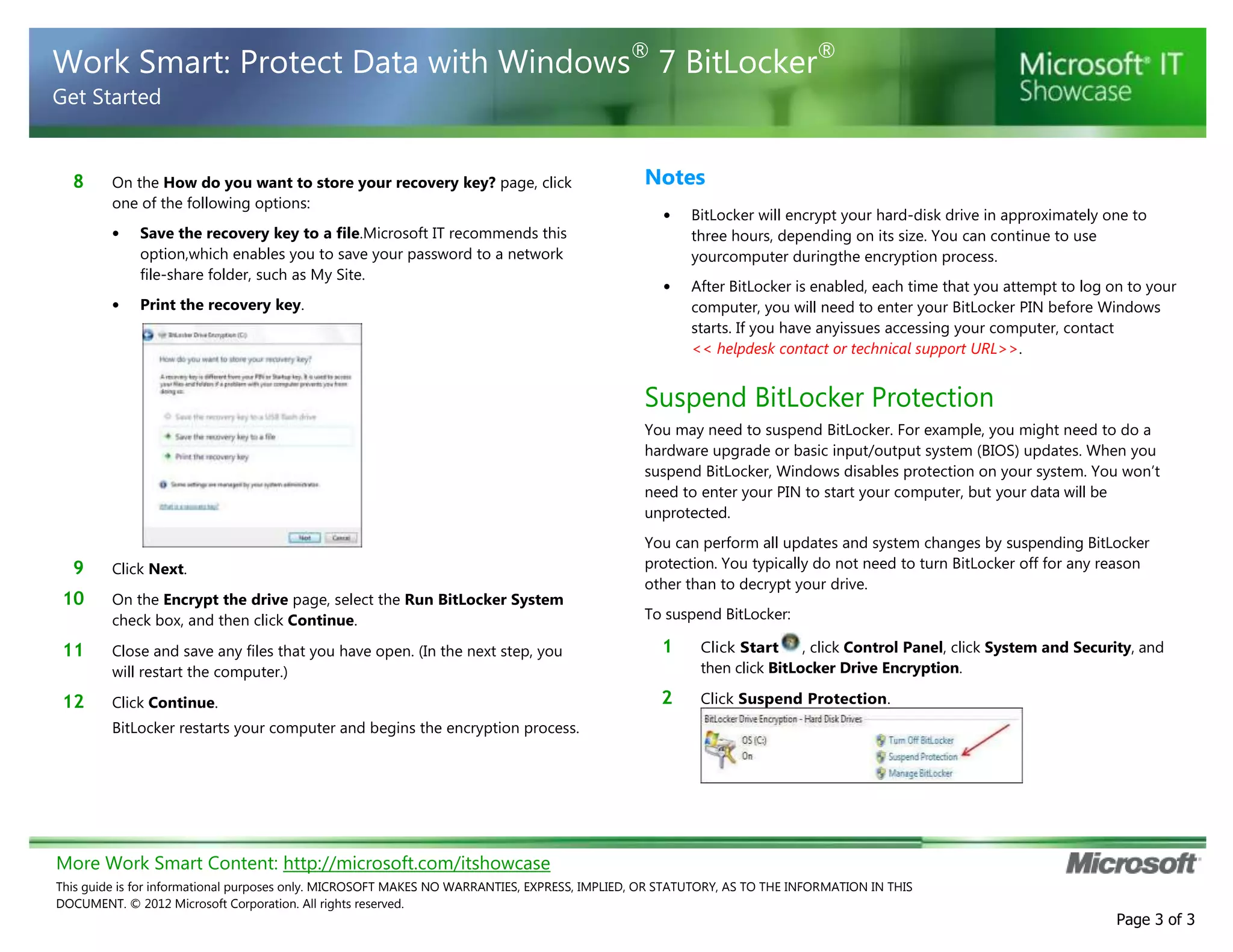
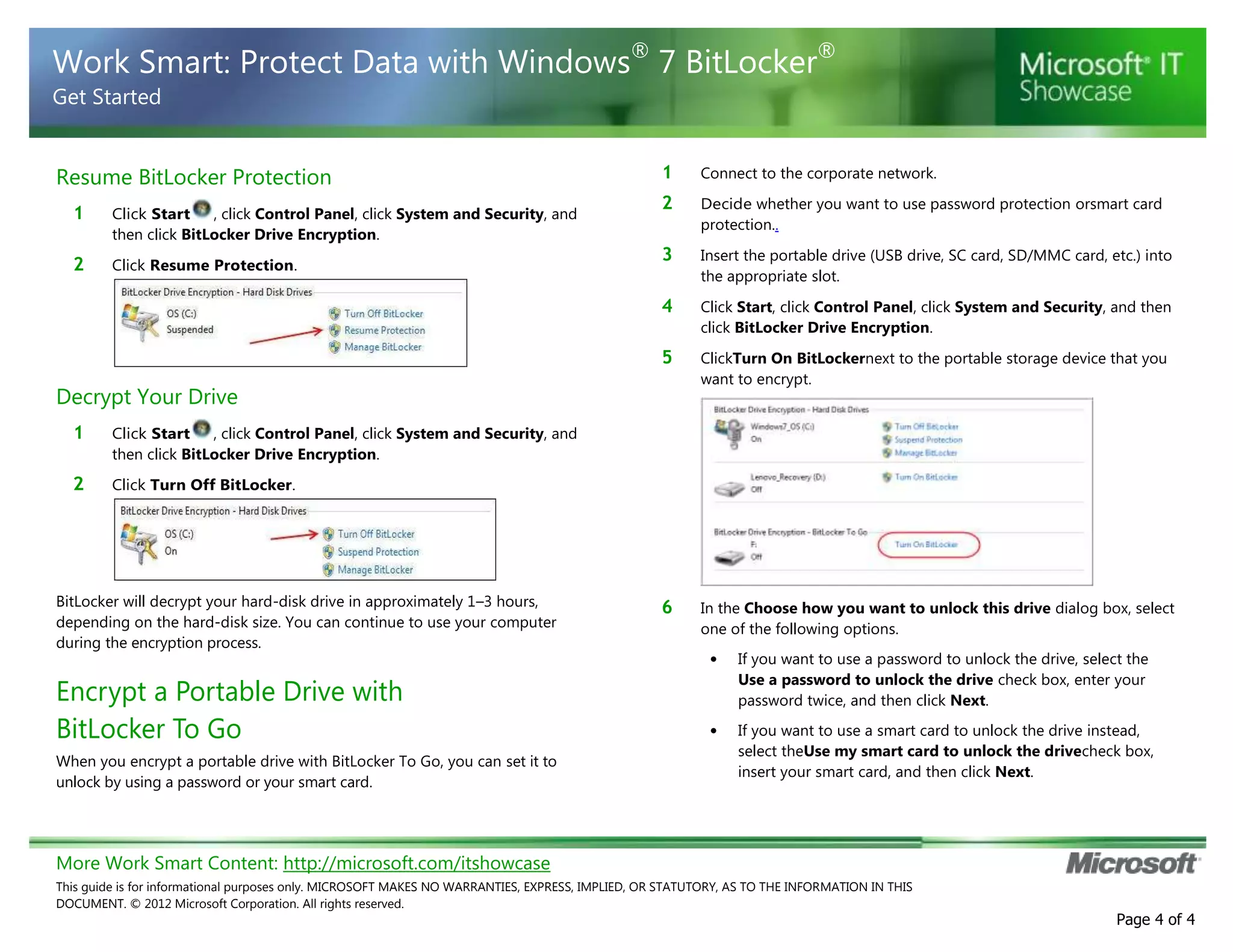
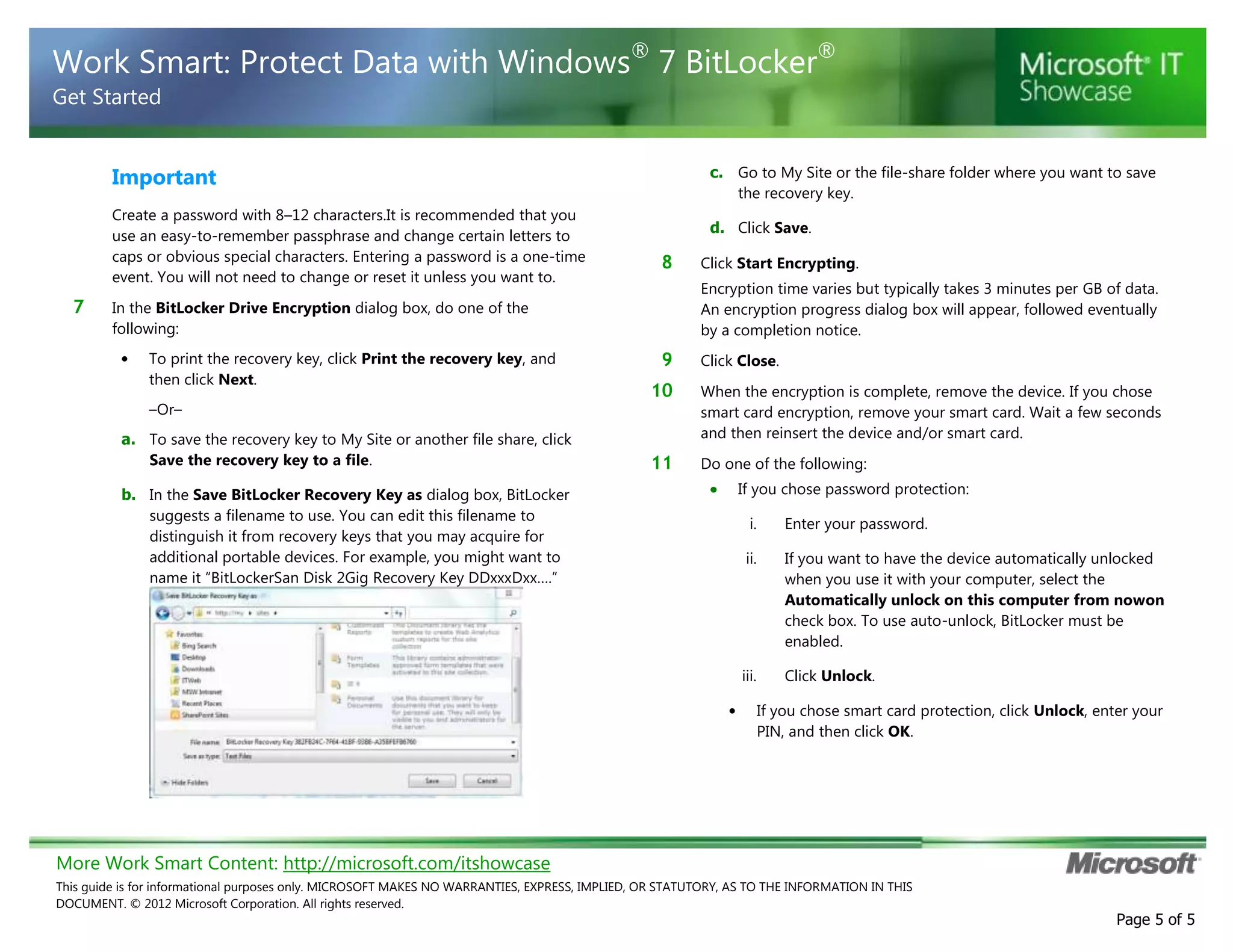
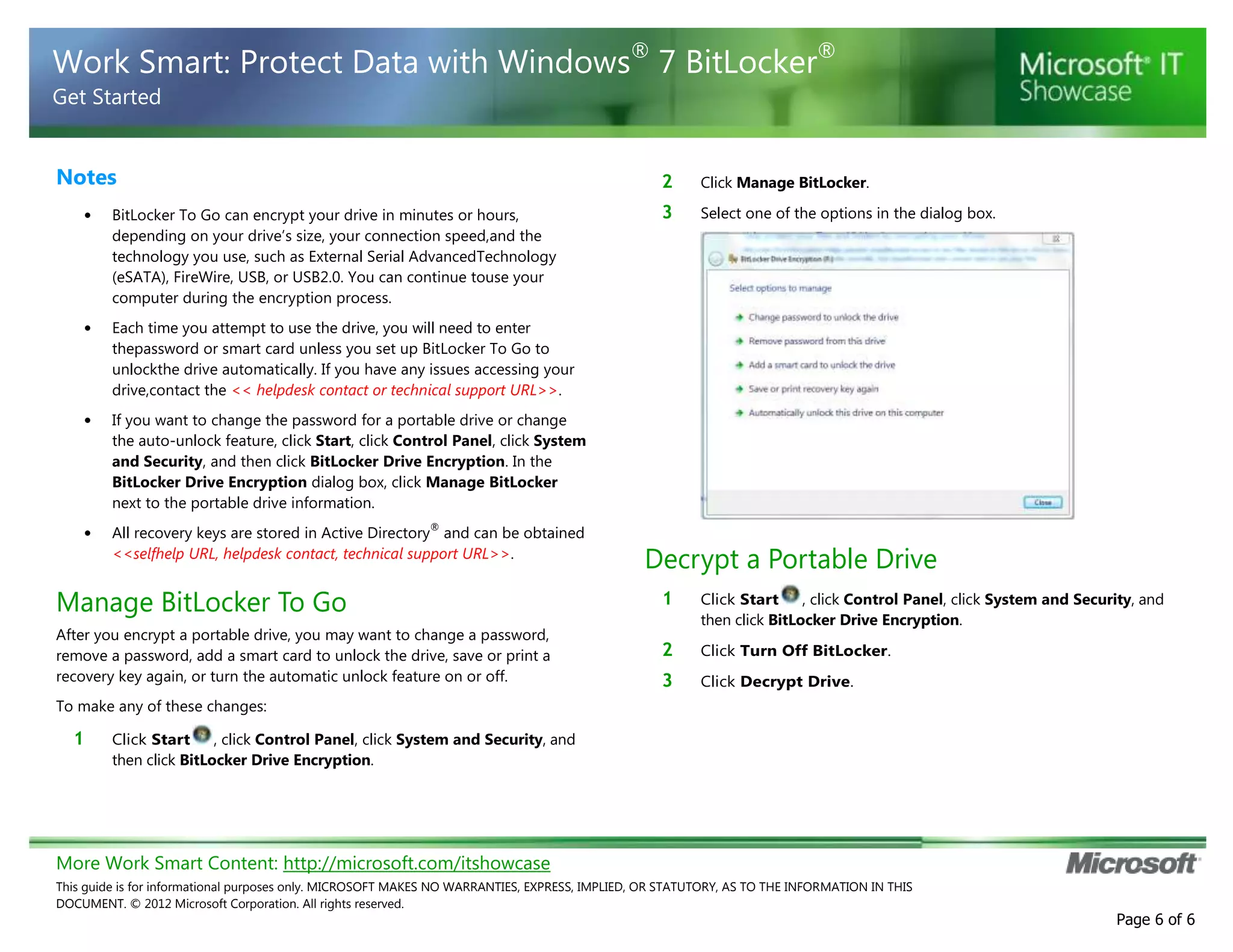
BitLocker is encryption software that protects data on computers and portable storage devices. It uses strong encryption to prevent unauthorized access to disk drives. The document provides step-by-step instructions for enabling and configuring BitLocker on computers and portable drives. This includes creating passwords or PINs, saving or printing recovery keys, suspending or resuming encryption, and decrypting drives when needed. The guidance is customized for an unspecified organization to integrate BitLocker usage policies and support contact details.