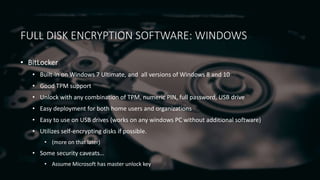
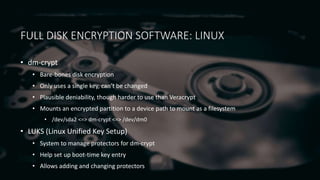
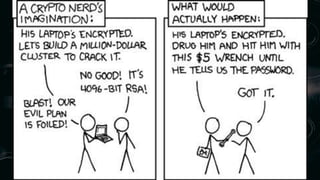
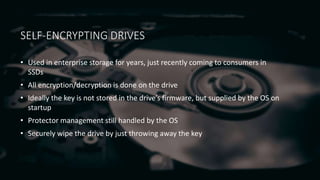
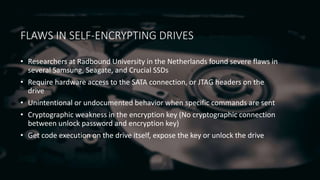
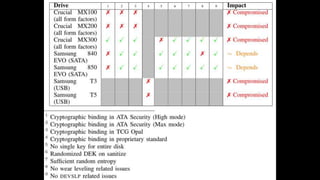
Full disk encryption (FDE) secures entire drives or partitions at the block level, making it independent of file systems and essential for compliance with security regulations. While it provides protection when devices are powered off, it does not defend against malware or unauthorized access while operational, and it requires a key management system for decryption. Various software solutions exist for different operating systems, with notable options including BitLocker for Windows, VeraCrypt for cross-platform use, and LUKS for Linux, each offering varying levels of security and usability.