Bitlocker configuration
•
0 likes•184 views
This document provides instructions for configuring BitLocker drive encryption to store recovery information in Active Directory. It involves enabling a startup PIN through Group Policy settings, configuring Active Directory to store BitLocker recovery information by modifying GPO settings linked to the relevant OU, and ensuring machines download updated policies by rebooting prior to encryption.
Report
Share
Report
Share
Download to read offline
Recommended
Gerrit tutorial

This document provides an overview and instructions for setting up Gerrit, an open source code review tool integrated with Git. It discusses installing Git on different platforms, configuring Git with username and email, generating SSH keys for authentication with Gerrit, and preparing to work with Gerrit by installing Git-Review. The goal is to help beginners learn the basic functionality of Gerrit and get set up to submit patches for code review.
Lesson 4 - Managing Applications, Services, Folders, and Libraries

This document covers managing applications, services, folders, and libraries in Windows. It discusses installing and uninstalling local and network applications, understanding services and how to configure them, using MSCONFIG to manage startup programs, comparing file systems like FAT, FAT32, and NTFS, using libraries to organize files across multiple folders, and methods for encrypting and compressing files for security and storage purposes like Encrypting File System, BitLocker, and compression.
Unity 3D, A game engine

This slide draw a basic idea of Unity 3D game engine with suitable visualization. Animator, physics and other UI function are clearly explained.
System Center Configuration Manager-The Most Popular System Center Component 

System Center Configuration Manager-The Most Popular System Center Component C/D/H Technology Consultants
Configuration Manager (CCM) is a Microsoft product that allows for comprehensive device and application management. It provides capabilities such as software deployment, patch management, hardware and software inventory, operating system deployment, endpoint protection, compliance settings, and reporting. CCM integrates with other Microsoft products and services and allows for centralized management of physical, virtual, and mobile devices. It is widely used due to its large install base and tight integration with the Microsoft ecosystem. While powerful, CCM still requires expertise to implement and use successfully.Game development life cycle

This document outlines the typical game development life cycle, which includes phases such as developing the story, script, feasibility study, promotional demo, design, layout, modeling, texturing, animation, high and low level design, coding, testing, debugging, integration, and game testing. It acknowledges references that were used to compile information on standard game development processes and models.
The complete srs documentation of our developed game. 

This documentation is an SRS of your SE project where we have developed the game. The pptx also uploaded as well.
Cara Menginstall Ubuntu 14.04 dengan VirtualBox

1. Cara menginstall Ubuntu 14.04 melalui VirtualBox dengan membuat virtual machine, menambahkan file iso Ubuntu, dan melakukan partisi hard disk menjadi 3 bagian untuk root, home, dan swap area sebelum proses instalasi.
KeenLab iOS Jailbreak Internals: Userland Read-Only Memory can be Dangerous

Modern operating systems nowadays implement read-only memory mappings at their CPU architecture level, preventing common security attacks. By mapping memories as read-only, the memory owner process can usually trust the memory content, eleminating unnecessary security considerations such as boundary check, TOCTTOU(Time of check to time of use) issues etc., with the assumption of other processes not being able to mutate read-only shared mappings in their own virtual spaces.
However, the assumption is not always correct. In the past few years, several logical issues were addressed by security community, most of which were caused by operating systems incorrectly allowing to remap the read-only memories as writble without marking them COW(copy-on-write). As a result, the memory content of the owner process is not trustable anymore, yet causing memory corruption problem or even leading to userland privilege escalation. With operating system evolves, such issues are rare though. On the other hand, with stronger and more abundant features provided by peripheral components attached to the mobile device, DMA(direct-memory-access) technology enables the ability for fast data transfer between the host and peripheral devices. DMA leverages IOMMU(Input/Output Memory Management Unit) for memory operations, thus memory protection mechanism provided by CPU MMU is not available during the DMA transfer. In the middle of 2017, Gal Beniamini of Goole Project Zero team utilized DMA to successfully achieve device-to-host attack on both Nexus 6p and iPhone 7. Nevertheless, this new attack model usually only applies for device-to-host attack senario, where a firmware bug is needed to fully control the device. Unfortunately, DMA related interfaces are not exposed to userland applications directly.
With months of research, we found an exception case on iOS device: the Apple Graphics. At MOSEC conference in 2017, we demonstrated jailbreak for iOS 10.3.2 and iOS 11 beta 2, the latest version at that time, on iPhone 6s and iPhone 7. Details of the demonstration have never been published yet.
In this talk, we will introduce the concepts essential to our bugs, which includes:
- Indirect DMA features exposed to iOS userland
- The implementation of IOMMU memory protection
- Notification mechanism between GPU and Apple Graphics driver
The next part will cover two bug details: one in DMA handling with host virtual memory, and another out-of-bound write issue caused by potentially untrusted userland read-only memory.
Lastly we talk about how we combine two flaws across different Apple Graphics components to achieve reliable kernel code execution from iOS application sandbox.
Recommended
Gerrit tutorial

This document provides an overview and instructions for setting up Gerrit, an open source code review tool integrated with Git. It discusses installing Git on different platforms, configuring Git with username and email, generating SSH keys for authentication with Gerrit, and preparing to work with Gerrit by installing Git-Review. The goal is to help beginners learn the basic functionality of Gerrit and get set up to submit patches for code review.
Lesson 4 - Managing Applications, Services, Folders, and Libraries

This document covers managing applications, services, folders, and libraries in Windows. It discusses installing and uninstalling local and network applications, understanding services and how to configure them, using MSCONFIG to manage startup programs, comparing file systems like FAT, FAT32, and NTFS, using libraries to organize files across multiple folders, and methods for encrypting and compressing files for security and storage purposes like Encrypting File System, BitLocker, and compression.
Unity 3D, A game engine

This slide draw a basic idea of Unity 3D game engine with suitable visualization. Animator, physics and other UI function are clearly explained.
System Center Configuration Manager-The Most Popular System Center Component 

System Center Configuration Manager-The Most Popular System Center Component C/D/H Technology Consultants
Configuration Manager (CCM) is a Microsoft product that allows for comprehensive device and application management. It provides capabilities such as software deployment, patch management, hardware and software inventory, operating system deployment, endpoint protection, compliance settings, and reporting. CCM integrates with other Microsoft products and services and allows for centralized management of physical, virtual, and mobile devices. It is widely used due to its large install base and tight integration with the Microsoft ecosystem. While powerful, CCM still requires expertise to implement and use successfully.Game development life cycle

This document outlines the typical game development life cycle, which includes phases such as developing the story, script, feasibility study, promotional demo, design, layout, modeling, texturing, animation, high and low level design, coding, testing, debugging, integration, and game testing. It acknowledges references that were used to compile information on standard game development processes and models.
The complete srs documentation of our developed game. 

This documentation is an SRS of your SE project where we have developed the game. The pptx also uploaded as well.
Cara Menginstall Ubuntu 14.04 dengan VirtualBox

1. Cara menginstall Ubuntu 14.04 melalui VirtualBox dengan membuat virtual machine, menambahkan file iso Ubuntu, dan melakukan partisi hard disk menjadi 3 bagian untuk root, home, dan swap area sebelum proses instalasi.
KeenLab iOS Jailbreak Internals: Userland Read-Only Memory can be Dangerous

Modern operating systems nowadays implement read-only memory mappings at their CPU architecture level, preventing common security attacks. By mapping memories as read-only, the memory owner process can usually trust the memory content, eleminating unnecessary security considerations such as boundary check, TOCTTOU(Time of check to time of use) issues etc., with the assumption of other processes not being able to mutate read-only shared mappings in their own virtual spaces.
However, the assumption is not always correct. In the past few years, several logical issues were addressed by security community, most of which were caused by operating systems incorrectly allowing to remap the read-only memories as writble without marking them COW(copy-on-write). As a result, the memory content of the owner process is not trustable anymore, yet causing memory corruption problem or even leading to userland privilege escalation. With operating system evolves, such issues are rare though. On the other hand, with stronger and more abundant features provided by peripheral components attached to the mobile device, DMA(direct-memory-access) technology enables the ability for fast data transfer between the host and peripheral devices. DMA leverages IOMMU(Input/Output Memory Management Unit) for memory operations, thus memory protection mechanism provided by CPU MMU is not available during the DMA transfer. In the middle of 2017, Gal Beniamini of Goole Project Zero team utilized DMA to successfully achieve device-to-host attack on both Nexus 6p and iPhone 7. Nevertheless, this new attack model usually only applies for device-to-host attack senario, where a firmware bug is needed to fully control the device. Unfortunately, DMA related interfaces are not exposed to userland applications directly.
With months of research, we found an exception case on iOS device: the Apple Graphics. At MOSEC conference in 2017, we demonstrated jailbreak for iOS 10.3.2 and iOS 11 beta 2, the latest version at that time, on iPhone 6s and iPhone 7. Details of the demonstration have never been published yet.
In this talk, we will introduce the concepts essential to our bugs, which includes:
- Indirect DMA features exposed to iOS userland
- The implementation of IOMMU memory protection
- Notification mechanism between GPU and Apple Graphics driver
The next part will cover two bug details: one in DMA handling with host virtual memory, and another out-of-bound write issue caused by potentially untrusted userland read-only memory.
Lastly we talk about how we combine two flaws across different Apple Graphics components to achieve reliable kernel code execution from iOS application sandbox.
Diktat Praktikum Manajemen Jaringan

Diktat ini memberikan panduan lengkap tentang proses instalasi Linux CentOS 7 pada VMware Workstation 14, mulai dari langkah pembuatan virtual machine, pengaturan hardware virtual machine, hingga proses instalasi sistem operasi Linux CentOS 7.
Unity 3d Basics

The document provides an overview of Unity 3D, a popular game engine. It discusses Unity basics like installing Unity, the main interface, and components like scenes, game objects, and prefabs. It also covers scripting in Unity, importing and creating assets, and how to build and export games for different platforms. The document serves as an introduction to the Unity game engine for beginners.
7- How to Configure Disk Quota

This document provides instructions for enabling disk quotas in Windows Server 2012 using the File Server Resource Manager (FSRM) tool. It describes how to install FSRM if not already included, then create a quota template defining a size limit and notification threshold. The instructions also explain how to apply this template to a specific folder to enforce the quota and verify it is working by copying a large file that exceeds the limit. The goal is to manage disk space on file servers and ensure sufficient storage for important operations by restricting users' storage usage.
Intro to Massively Multiplayer Online Game (MMOG) Design

Presentation on MMOG architecture given to several app development groups interested in moving into the game design world. Much of this content was inspired by t-machine.org.
Building SPFx Solutions using Docker

This document discusses using Docker for SharePoint Framework (SPFx) development. It describes benefits like standardized environments and easier collaboration. Instructions are provided to create a Docker image with Node.js and SPFx tools preinstalled. The image can then be used to quickly spin up containers for building SPFx solutions. A demo shows generating a new solution within a Docker container.
11 Awesome Quotes About Game Design

Have you ever imagined creating the next Mario Bros?
Are you passionate about developing games?
We found 11 awesome quotes about game design from some of our favorite authors.
Check out our latest app Word Hack:
http://www.wordhackapp.com/
Need a custom mobile app? Let's talk!
http://www.bluelabellabs.com/
Unity Game Engine - Basics

Unity is a cross-platform game engine that can be used to create 2D, 3D, VR and AR games and experiences. It was originally released in 2005 and has since expanded to support over 25 platforms. Nearly half of all games are now built with Unity. The document discusses Unity's history, how to download and install it, an overview of the Unity interface and common tools, how to set up and create projects and objects, scripting with C#, visual scripting with Bolt, the Unity Asset Store, Mixamo for animations, examples of games made with Unity, and advantages and disadvantages.
Game optimization techniques - Most Commons

"Game optimization means improving the game application so it runs at the smooth frame-rate across a wide range of hardware specs, including low-end configurations.
In this discussion we will discuss about some common Game optimization techniques irrespective of what Game engine you are using.
- By Niraj Vishwakarma
Asterisk 11to16, What could go wrong

An Asterisk administrator discusses upgrading an Asterisk PBX from version 11 to version 16. This involved building new Debian packages, porting configurations, updating dialplans, testing features, and addressing issues like crashes, logging problems, and high system loads. Through testing and troubleshooting, the upgrade was eventually successful and the system could handle the same call load as the previous version. However, ongoing work is still needed to optimize logging and reduce continuous CPU loads.
Game Development Company, Flash Game Development,

Card Game Development, Dice Game Development, Web & Desktop Games Development, Mobile / PDA Games Development, I-phone Game Development, Flash Game Development, Interactive TV Game Development, Game Engine Development, Game Testing and Analysis,
Console Based Games
Automated Out-of-Band management with Ansible and Redfish

Ansible is an open source automation engine that automates complex IT tasks such as cloud provisioning, application deployment and a wide variety of system administration tasks. It is a one-to-many agentless mechanism where complex deployment tasks can be controlled and monitored from a central control machine.
Redfish is an open industry-standard specification and schema designed for modern and secure management of platform hardware. On Dell EMC PowerEdge servers the Redfish management APIs are available via the integrated Dell Remote Access Controller (iDRAC), which can be used by IT administrators to easily monitor and manage at scale their entire infrastructure using a wide array of clients on devices such as laptops, tablets and smart phones.
Together, Ansible and Redfish can be used by system administrators to fully automate at large scale server monitoring, provisioning and update tasks from one central location, significantly reducing complexity and helping improve the productivity and efficiency of IT administrators.
Backup & restore in windows

A closer quick understanding of different backup technologies and pros and cons backup & recovery,ntbackup,types of backups, windows backup path so far, differential backup, incremental backup, full backup, mirror backup. If you have have anyqueries please contact me at jabvtl@gmail.com
Hypervisors Vs Bare Metal Servers: a Beginner’s Guide

>> What is Bare Metal?
>> Features of Bare Metal.
>> What Is A Hypervisor?
>> Features of Hypervisors.
>> Advantages of bare metal.
>> Disadvantages of Bare metal.
>> Advantages of hypervisors.
>> Disadvantages of Hypervisors.
Windows Server 2019 - NetConf Co

Presentación realizada en la NetConf Colombia 2018 en la ciudad de Medellín, un evento que reunió a un gran número de profesionales en desarrollo en infraestructura para disfrutar de el más rico contenido en tecnologías.
INTRODUCTION TO IIS

This document provides system requirements and new features for Microsoft Internet Information Services (IIS) 6.0. It recommends a 550MHz processor with at least 256MB RAM and 2GB of storage. New features include an XML configuration file for easier management, improved security through disabling installation by default, and enhanced performance, scalability and manageability through features like caching and worker process recycling. IIS 6.0 also provides better integration with ASP.NET.
Citrix Netscaler Deployment Guide

This document provides an overview and deployment guide for Citrix NetScaler application delivery controllers (ADCs). It discusses the NetScaler editions, features, hardware options, typical network topology, and basic traffic management and configuration. The NetScaler acts as a load balancer and content switch in front of web, application, and database servers. It can operate in inline or one-arm deployment modes and provides features like load balancing, caching, compression, and web application firewall capabilities to optimize application delivery and security. The document provides guidance on initial NetScaler configuration using the command line interface or graphical user interface.
Introduction to Unity3D and Building your First Game

In Phase One, we will cover the basics of using the Unity editor’s interface, customizing the workspace, building a 3D environment, and adding sound effects.
In Phase Two, we will import a player character asset, learn about Animator Controllers, make animations, set up physics and gravity, and add player movement scripts.
In Phase Three, we will set up our Camera and write a script to make the camera follow our player character.
Best Practice TLS for IBM Domino

How to deliver industry standard browser security to the native Domino HTTP stack, using company-wide wildcard certificates deployed across all platforms.
Managing bitlocker with MBAM

A look on Microsoft Desktop optimization Pack's MBAM for administration and management of Bitlocker computers
03 bit locker-mod03

BitLocker Drive Encryption helps prevent unauthorized access to data on lost or stolen computers by encrypting volumes and verifying integrity of early boot components. It uses a Trusted Platform Module to store encryption keys and check system integrity on startup. While a TPM is preferred, BitLocker can also use a USB drive to store keys. The document discusses BitLocker concepts, architecture, system requirements, group policy settings, and getting started.
More Related Content
What's hot
Diktat Praktikum Manajemen Jaringan

Diktat ini memberikan panduan lengkap tentang proses instalasi Linux CentOS 7 pada VMware Workstation 14, mulai dari langkah pembuatan virtual machine, pengaturan hardware virtual machine, hingga proses instalasi sistem operasi Linux CentOS 7.
Unity 3d Basics

The document provides an overview of Unity 3D, a popular game engine. It discusses Unity basics like installing Unity, the main interface, and components like scenes, game objects, and prefabs. It also covers scripting in Unity, importing and creating assets, and how to build and export games for different platforms. The document serves as an introduction to the Unity game engine for beginners.
7- How to Configure Disk Quota

This document provides instructions for enabling disk quotas in Windows Server 2012 using the File Server Resource Manager (FSRM) tool. It describes how to install FSRM if not already included, then create a quota template defining a size limit and notification threshold. The instructions also explain how to apply this template to a specific folder to enforce the quota and verify it is working by copying a large file that exceeds the limit. The goal is to manage disk space on file servers and ensure sufficient storage for important operations by restricting users' storage usage.
Intro to Massively Multiplayer Online Game (MMOG) Design

Presentation on MMOG architecture given to several app development groups interested in moving into the game design world. Much of this content was inspired by t-machine.org.
Building SPFx Solutions using Docker

This document discusses using Docker for SharePoint Framework (SPFx) development. It describes benefits like standardized environments and easier collaboration. Instructions are provided to create a Docker image with Node.js and SPFx tools preinstalled. The image can then be used to quickly spin up containers for building SPFx solutions. A demo shows generating a new solution within a Docker container.
11 Awesome Quotes About Game Design

Have you ever imagined creating the next Mario Bros?
Are you passionate about developing games?
We found 11 awesome quotes about game design from some of our favorite authors.
Check out our latest app Word Hack:
http://www.wordhackapp.com/
Need a custom mobile app? Let's talk!
http://www.bluelabellabs.com/
Unity Game Engine - Basics

Unity is a cross-platform game engine that can be used to create 2D, 3D, VR and AR games and experiences. It was originally released in 2005 and has since expanded to support over 25 platforms. Nearly half of all games are now built with Unity. The document discusses Unity's history, how to download and install it, an overview of the Unity interface and common tools, how to set up and create projects and objects, scripting with C#, visual scripting with Bolt, the Unity Asset Store, Mixamo for animations, examples of games made with Unity, and advantages and disadvantages.
Game optimization techniques - Most Commons

"Game optimization means improving the game application so it runs at the smooth frame-rate across a wide range of hardware specs, including low-end configurations.
In this discussion we will discuss about some common Game optimization techniques irrespective of what Game engine you are using.
- By Niraj Vishwakarma
Asterisk 11to16, What could go wrong

An Asterisk administrator discusses upgrading an Asterisk PBX from version 11 to version 16. This involved building new Debian packages, porting configurations, updating dialplans, testing features, and addressing issues like crashes, logging problems, and high system loads. Through testing and troubleshooting, the upgrade was eventually successful and the system could handle the same call load as the previous version. However, ongoing work is still needed to optimize logging and reduce continuous CPU loads.
Game Development Company, Flash Game Development,

Card Game Development, Dice Game Development, Web & Desktop Games Development, Mobile / PDA Games Development, I-phone Game Development, Flash Game Development, Interactive TV Game Development, Game Engine Development, Game Testing and Analysis,
Console Based Games
Automated Out-of-Band management with Ansible and Redfish

Ansible is an open source automation engine that automates complex IT tasks such as cloud provisioning, application deployment and a wide variety of system administration tasks. It is a one-to-many agentless mechanism where complex deployment tasks can be controlled and monitored from a central control machine.
Redfish is an open industry-standard specification and schema designed for modern and secure management of platform hardware. On Dell EMC PowerEdge servers the Redfish management APIs are available via the integrated Dell Remote Access Controller (iDRAC), which can be used by IT administrators to easily monitor and manage at scale their entire infrastructure using a wide array of clients on devices such as laptops, tablets and smart phones.
Together, Ansible and Redfish can be used by system administrators to fully automate at large scale server monitoring, provisioning and update tasks from one central location, significantly reducing complexity and helping improve the productivity and efficiency of IT administrators.
Backup & restore in windows

A closer quick understanding of different backup technologies and pros and cons backup & recovery,ntbackup,types of backups, windows backup path so far, differential backup, incremental backup, full backup, mirror backup. If you have have anyqueries please contact me at jabvtl@gmail.com
Hypervisors Vs Bare Metal Servers: a Beginner’s Guide

>> What is Bare Metal?
>> Features of Bare Metal.
>> What Is A Hypervisor?
>> Features of Hypervisors.
>> Advantages of bare metal.
>> Disadvantages of Bare metal.
>> Advantages of hypervisors.
>> Disadvantages of Hypervisors.
Windows Server 2019 - NetConf Co

Presentación realizada en la NetConf Colombia 2018 en la ciudad de Medellín, un evento que reunió a un gran número de profesionales en desarrollo en infraestructura para disfrutar de el más rico contenido en tecnologías.
INTRODUCTION TO IIS

This document provides system requirements and new features for Microsoft Internet Information Services (IIS) 6.0. It recommends a 550MHz processor with at least 256MB RAM and 2GB of storage. New features include an XML configuration file for easier management, improved security through disabling installation by default, and enhanced performance, scalability and manageability through features like caching and worker process recycling. IIS 6.0 also provides better integration with ASP.NET.
Citrix Netscaler Deployment Guide

This document provides an overview and deployment guide for Citrix NetScaler application delivery controllers (ADCs). It discusses the NetScaler editions, features, hardware options, typical network topology, and basic traffic management and configuration. The NetScaler acts as a load balancer and content switch in front of web, application, and database servers. It can operate in inline or one-arm deployment modes and provides features like load balancing, caching, compression, and web application firewall capabilities to optimize application delivery and security. The document provides guidance on initial NetScaler configuration using the command line interface or graphical user interface.
Introduction to Unity3D and Building your First Game

In Phase One, we will cover the basics of using the Unity editor’s interface, customizing the workspace, building a 3D environment, and adding sound effects.
In Phase Two, we will import a player character asset, learn about Animator Controllers, make animations, set up physics and gravity, and add player movement scripts.
In Phase Three, we will set up our Camera and write a script to make the camera follow our player character.
Best Practice TLS for IBM Domino

How to deliver industry standard browser security to the native Domino HTTP stack, using company-wide wildcard certificates deployed across all platforms.
What's hot (20)
Intro to Massively Multiplayer Online Game (MMOG) Design

Intro to Massively Multiplayer Online Game (MMOG) Design
Automated Out-of-Band management with Ansible and Redfish

Automated Out-of-Band management with Ansible and Redfish
Hypervisors Vs Bare Metal Servers: a Beginner’s Guide

Hypervisors Vs Bare Metal Servers: a Beginner’s Guide
Introduction to Unity3D and Building your First Game

Introduction to Unity3D and Building your First Game
Similar to Bitlocker configuration
Managing bitlocker with MBAM

A look on Microsoft Desktop optimization Pack's MBAM for administration and management of Bitlocker computers
03 bit locker-mod03

BitLocker Drive Encryption helps prevent unauthorized access to data on lost or stolen computers by encrypting volumes and verifying integrity of early boot components. It uses a Trusted Platform Module to store encryption keys and check system integrity on startup. While a TPM is preferred, BitLocker can also use a USB drive to store keys. The document discusses BitLocker concepts, architecture, system requirements, group policy settings, and getting started.
Fcm rapid-install-11122-1634210

This document provides steps to deploy Oracle Hyperion Financial Close Management on a single server running Windows. The 6 hour deployment process involves:
1. Downloading installation files, including Oracle Database and EPM system files.
2. Installing and configuring Oracle Database, creating the 'fcm' and 'DEV_ODI_REPO' database users.
3. Installing and configuring the EPM system, including Oracle SOA Suite, Oracle Data Integrator, and Account Reconciliation Manager.
4. Configuring Oracle Data Integrator and ERPI for Account Reconciliation Manager.
StoreGrid : Restore & Recovery

This document outlines two scenarios for recovering data backed up using StoreGrid after a system crash.
In the first scenario, the user reinstalls their laptop OS and HDD, reconnects their external backup drive, reinstalls StoreGrid with the same ID, deletes a configuration file, and is then able to restore their backed up data by selecting the appropriate backup schedule.
In the second scenario involving a network of 25 systems, if user 2's system crashes, they would reinstall the OS with the same name, install StoreGrid in client mode, restore their client configurations from the backup server, then restore their backed up data by selecting it from the list of available backups.
SysInfoTools RAID Recovery Software

SysInfoTools RAID Recovery software is a thorough answer for RAID file recovery on Windows systems. Software has been insightfully programmed for recovering maximum conceivable data from corrupt RAID hard disks. It underpins both RAID-HDD and RAID-VHD, and restores data in their original form at user-defined location. Every single well-known file systems of Windows, Mac and Linux are profoundly supported by this product. Likewise, it supports both GPT and MBR partition table formats in which your hard disk partition is saved. The interactive and easy-to-use interface of this software makes recovery operation highly convenient for technical and non-technical users.
2569 protect yourdatawithbitlocker_gs_windows7_external

BitLocker is encryption software that protects data on computers and portable storage devices. It uses strong encryption to prevent unauthorized access to disk drives. The document provides step-by-step instructions for enabling and configuring BitLocker on computers and portable drives. This includes creating passwords or PINs, saving or printing recovery keys, suspending or resuming encryption, and decrypting drives when needed. The guidance is customized for an unspecified organization to integrate BitLocker usage policies and support contact details.
Installation CentOS 6.3

This document provides steps to install CentOS 6.3, including selecting installation type, disk partitioning, configuring network settings like hostname and DHCP, setting the root password, selecting packages, and rebooting the system to complete installation. Key steps are choosing installation media, partitioning and formatting disks, installing boot loader, and rebooting to finish.
Toyotaotcvimgtssoftwareoverview 160525025652

The document provides an overview of the Global Techstream (GTS) diagnostic software. GTS is a PC-based diagnostic tool developed by Toyota consisting of GTS software and a Vehicle Interface Module. The software allows technicians to diagnose and reprogram vehicles and has features like Windows-based software, legacy vehicle support, and a user-friendly interface. It provides various functions through different tabs like System Select for vehicle connection, Live Data for parameter monitoring, and Stored Data for saved records.
Windows splunk logging cheat sheet Oct 2016 - MalwareArchaeology.com

This document provides a cheat sheet for configuring Windows logging and auditing settings on Windows 7 through Windows 2012 systems. It includes instructions for increasing log sizes, enabling specific audit policies and event logging, and harvesting important security-related events from the logs. The goal is to capture essential system activity like processes, services, authentication events and changes to files, registry keys and more to aid in detecting malicious behavior.
Configuration manager

The document provides instructions for setting up a Configuration Manager 2012 hierarchy with a Central Administration Site on server CM1. It describes installing prerequisites like extending the Active Directory schema and configuring the System Management container. It also covers installing IIS roles on site servers. The steps outlined install the Central Administration Site on CM1 and establish the Company XYZ hierarchy.
Windows Logging Cheat Sheet ver Jan 2016 - MalwareArchaeology

MalwareArchaeology - What you need to know to Enable, Configure, Gather and Harvest for Windows logs.
SOP - 2013 Server Build

This document provides a checklist for building an MS Windows Server 2008 machine. It outlines 14 high-level steps: 1) Prepare required paperwork; 2) Configure hardware or virtual machine; 3) Prepare the server environment; 4) Install Windows Server OS; 5) Customize the desktop and power settings; 6) Configure core server settings; 7) Install necessary agents and add-ons; and 8) Mark the build complete upon installing required VMware or hardware tools. It also provides additional pages of detailed instructions for each step.
SysInfoTools OpenOffice Calc Recovery

OpenOffice Calc Recovery Software from SysInfoTools fixes corrupt spreadsheets aka ODS files and recover maximum recoverable data from them. It effectively recovers unreadable cell data and other object from corrupt ODS files. The software supports batch recovery of corrupted ODS files simultaneously. It allows users to see the preview of recovered files before saving them into a new ODS file. The new ODS file can be saved at user defined location. The software is available with free demo version, which helps users examine its performance before buying its full version.
Arcelor Mittal intern

The document discusses the deployment, configuration, and management of an IT infrastructure based on Windows Server 2008 R2 SP1. It describes setting up virtual machines using Hyper-V that run Active Directory, DNS, DHCP, file sharing, printing, Exchange, SCCM, and WDS. Group policies were implemented for security, firewall, and other settings. The virtual infrastructure allows for reliable administration of servers, users, and resources across the network.
Data link mamut_magento

This document provides instructions for using Web DataLink software to synchronize product and order data between a Magento online store and Mamut Enterprise E5/E3 software. It describes installing the software, configuring connection settings for Mamut and the Magento site, and performing synchronization operations to upload and download products and orders. Synchronization can be automated using the scheduler to run on a set schedule. The log file records activity to help with troubleshooting.
Windows Server 2008 Active Directory

Active Directory is a database that stores information about a network's users, computers, groups, and other network resources. It allows for centralized management of these resources.
A domain controller is a server that responds to authentication requests on the Windows domain. It authenticates users' credentials when they log into the domain network.
Lightweight Directory Access Protocol (LDAP) is an open standard protocol that Active Directory supports to make user and resource information widely accessible for management and querying across the network.
2. install os

1. The document provides instructions for installing Windows Server 2008, including hardware requirements, installation media requirements, and a 14-step installation process.
2. Key steps in the installation process include selecting installation options, accepting license terms, selecting disk and partition, and changing the default administrator password.
3. The installation takes approximately 20 minutes to copy and extract files, then the server will reboot for initial configuration.
Ad msi-installation via Active Directory

Active Directory can be used to automatically deploy MSI packages to machines upon startup or login. The administrator must first define a package object within a GPO that references the MSI file located on a shared network drive. The drive must allow access for domain computers. Once defined, machines rebooting or users logging in within the GPO's scope will have the MSI silently installed. Redeploying the package object triggers reinstallation of any updated MSI files. Troubleshooting focuses on permissions and package definitions if installation fails or machines do not receive updates.
Cctk support for setting hdd password

1. This document describes how to enable and disable hard disk drive (HDD) passwords on Dell client systems using the Client Configuration Toolkit (CCTK).
2. The steps include checking for HDD availability in the BIOS, using the "hddinfo" and "hddpwd" CCTK commands to view HDD details and set passwords, rebooting the system for changes to take effect, and verifying passwords are set properly in the BIOS and through additional CCTK commands.
3. The process to clear an HDD password uses the "hddpwd=" CCTK command along with the valid password that was previously set.
How to install share point 2010

SharePoint 2010 installation guide for windows 7. For SharePoint training in Chennai. Ameks infotech is the best One. Visit http://www.ameksinfotech.com/sharepoint-training/
Similar to Bitlocker configuration (20)
2569 protect yourdatawithbitlocker_gs_windows7_external

2569 protect yourdatawithbitlocker_gs_windows7_external
Windows splunk logging cheat sheet Oct 2016 - MalwareArchaeology.com

Windows splunk logging cheat sheet Oct 2016 - MalwareArchaeology.com
Windows Logging Cheat Sheet ver Jan 2016 - MalwareArchaeology

Windows Logging Cheat Sheet ver Jan 2016 - MalwareArchaeology
Recently uploaded
A Comprehensive Guide on Implementing Real-World Mobile Testing Strategies fo...

In today's fiercely competitive mobile app market, the role of the QA team is pivotal for continuous improvement and sustained success. Effective testing strategies are essential to navigate the challenges confidently and precisely. Ensuring the perfection of mobile apps before they reach end-users requires thoughtful decisions in the testing plan.
Microservice Teams - How the cloud changes the way we work

A lot of technical challenges and complexity come with building a cloud-native and distributed architecture. The way we develop backend software has fundamentally changed in the last ten years. Managing a microservices architecture demands a lot of us to ensure observability and operational resiliency. But did you also change the way you run your development teams?
Sven will talk about Atlassian’s journey from a monolith to a multi-tenanted architecture and how it affected the way the engineering teams work. You will learn how we shifted to service ownership, moved to more autonomous teams (and its challenges), and established platform and enablement teams.
一比一原版(USF毕业证)旧金山大学毕业证如何办理

USF硕士毕业证成绩单【微信95270640】一比一伪造旧金山大学文凭@假冒USF毕业证成绩单+Q微信95270640办理USF学位证书@仿造USF毕业文凭证书@购买旧金山大学毕业证成绩单USF真实使馆认证/真实留信认证回国人员证明
#一整套旧金山大学文凭证件办理#—包含旧金山大学旧金山大学本科毕业证成绩单学历认证|使馆认证|归国人员证明|教育部认证|留信网认证永远存档教育部学历学位认证查询办理国外文凭国外学历学位认证#我们提供全套办理服务。
一整套留学文凭证件服务:
一:旧金山大学旧金山大学本科毕业证成绩单毕业证 #成绩单等全套材料从防伪到印刷水印底纹到钢印烫金
二:真实使馆认证(留学人员回国证明)使馆存档
三:真实教育部认证教育部存档教育部留服网站永久可查
四:留信认证留学生信息网站永久可查
国外毕业证学位证成绩单办理方法:
1客户提供办理旧金山大学旧金山大学本科毕业证成绩单信息:姓名生日专业学位毕业时间等(如信息不确定可以咨询顾问:我们有专业老师帮你查询);
2开始安排制作毕业证成绩单电子图;
3毕业证成绩单电子版做好以后发送给您确认;
4毕业证成绩单电子版您确认信息无误之后安排制作成品;
5成品做好拍照或者视频给您确认;
6快递给客户(国内顺丰国外DHLUPS等快读邮寄)。
教育部文凭学历认证认证的用途:
如果您计划在国内发展那么办理国内教育部认证是必不可少的。事业性用人单位如银行国企公务员在您应聘时都会需要您提供这个认证。其他私营 #外企企业无需提供!办理教育部认证所需资料众多且烦琐所有材料您都必须提供原件我们凭借丰富的经验帮您快速整合材料让您少走弯路。
实体公司专业为您服务如有需要请联系我: 微信95270640奈一次次令他失望山娃今年岁上五年级识得很多字从走出小屋开始山娃就知道父亲的家和工地共有一个很动听的名字——天河工地的底层空空荡荡很宽阔很凉爽在地上铺上报纸和水泥袋父亲和工人们中午全睡在地上地面坑坑洼洼山娃曾多次绊倒过也曾有长铁钉穿透凉鞋刺在脚板上但山娃不怕工地上也常有五六个从乡下来的小学生他们的父母亲也是高楼上的建筑工人小伙伴来自不同省份都操着带有浓重口音的普通话可不知为啥山娃不仅很快与他们熟识了
Kubernetes at Scale: Going Multi-Cluster with Istio

Divine Odazie and Jubril Oyetunji share tips on Going Multi-Cluster with Istio Service Mesh at DevOpsDays Houston.
Unlock the Secrets to Effortless Video Creation with Invideo: Your Ultimate G...

Unlock the Secrets to Effortless Video Creation with Invideo: Your Ultimate G...The Third Creative Media
"Navigating Invideo: A Comprehensive Guide" is an essential resource for anyone looking to master Invideo, an AI-powered video creation tool. This guide provides step-by-step instructions, helpful tips, and comparisons with other AI video creators. Whether you're a beginner or an experienced video editor, you'll find valuable insights to enhance your video projects and bring your creative ideas to life.Transforming Product Development using OnePlan To Boost Efficiency and Innova...

Ready to overcome challenges and drive innovation in your organization? Join us in our upcoming webinar where we discuss how to combat resource limitations, scope creep, and the difficulties of aligning your projects with strategic goals. Discover how OnePlan can revolutionize your product development processes, helping your team to innovate faster, manage resources more effectively, and deliver exceptional results.
All you need to know about Spring Boot and GraalVM

All you need to know about Spring Boot and GraalVM 🐰
ACE - Team 24 Wrapup event at ahmedabad.

Atlassian Team 24 event wrap-up Ahmedabad. Recap of Atlassian team24 event.
Safelyio Toolbox Talk Softwate & App (How To Digitize Safety Meetings)

Consistent toolbox talks are critical for maintaining workplace safety, as they provide regular opportunities to address specific hazards and reinforce safe practices.
These brief, focused sessions ensure that safety is a continual conversation rather than a one-time event, which helps keep safety protocols fresh in employees' minds. Studies have shown that shorter, more frequent training sessions are more effective for retention and behavior change compared to longer, infrequent sessions.
Engaging workers regularly, toolbox talks promote a culture of safety, empower employees to voice concerns, and ultimately reduce the likelihood of accidents and injuries on site.
The traditional method of conducting safety talks with paper documents and lengthy meetings is not only time-consuming but also less effective. Manual tracking of attendance and compliance is prone to errors and inconsistencies, leading to gaps in safety communication and potential non-compliance with OSHA regulations. Switching to a digital solution like Safelyio offers significant advantages.
Safelyio automates the delivery and documentation of safety talks, ensuring consistency and accessibility. The microlearning approach breaks down complex safety protocols into manageable, bite-sized pieces, making it easier for employees to absorb and retain information.
This method minimizes disruptions to work schedules, eliminates the hassle of paperwork, and ensures that all safety communications are tracked and recorded accurately. Ultimately, using a digital platform like Safelyio enhances engagement, compliance, and overall safety performance on site. https://safelyio.com/
Enhanced Screen Flows UI/UX using SLDS with Tom Kitt

Join us for an engaging session led by Flow Champion, Tom Kitt. This session will dive into a technique of enhancing the user interfaces and user experiences within Screen Flows using the Salesforce Lightning Design System (SLDS). This technique uses Native functionality, with No Apex Code, No Custom Components and No Managed Packages required.
Boost Your Savings with These Money Management Apps

A money management app can transform your financial life by tracking expenses, creating budgets, and setting financial goals. These apps offer features like real-time expense tracking, bill reminders, and personalized insights to help you save and manage money effectively. With a user-friendly interface, they simplify financial planning, making it easier to stay on top of your finances and achieve long-term financial stability.
一比一原版(UMN毕业证)明尼苏达大学毕业证如何办理

UMN硕士毕业证成绩单【微信95270640】购买(明尼苏达大学毕业证成绩单硕士学历)Q微信95270640代办UMN学历认证留信网伪造明尼苏达大学学位证书精仿明尼苏达大学本科/硕士文凭证书补办明尼苏达大学 diplomaoffer,Transcript购买明尼苏达大学毕业证成绩单购买UMN假毕业证学位证书购买伪造明尼苏达大学文凭证书学位证书,专业办理雅思、托福成绩单,学生ID卡,在读证明,海外各大学offer录取通知书,毕业证书,成绩单,文凭等材料:1:1完美还原毕业证、offer录取通知书、学生卡等各种在读或毕业材料的防伪工艺(包括 烫金、烫银、钢印、底纹、凹凸版、水印、防伪光标、热敏防伪、文字图案浮雕,激光镭射,紫外荧光,温感光标)学校原版上有的工艺我们一样不会少,不论是老版本还是最新版本,都能保证最高程度还原,力争完美以求让所有同学都能享受到完美的品质服务。
#毕业证成绩单 #毕业証 #成绩单 #學生卡 #OFFER录取通知书 #雅思#托福等……
国外大学明尼苏达大学明尼苏达大学毕业证offer制作方法(一对一专业服务)
1客户提供办理信息:姓名生日专业学位毕业时间等(如信息不确定可以咨询顾问:我们有专业老师帮你查询);
2开始安排制作毕业证成绩单电子图;
3毕业证成绩单电子版做好以后发送给您确认;
4毕业证成绩单电子版您确认信息无误之后安排制作成品;
5成品做好拍照或者视频给您确认;
6快递给客户(国内顺丰国外DHLUPS等快读邮寄)
— — 制作工艺 【高仿真】— —
凭借多年的制作经验本公司制作明尼苏达大学明尼苏达大学毕业证offer《激光》《水印》《钢印》《烫金》《紫外线》凹凸版uv版等防伪技术一流高精仿度几乎跟学校100%相同!让您绝对满意。
— — -公司理念 【诚信为主】— — —
我們以質量求生存.以服务求发展有雄厚的实力专业的团队咨询顾问为您细心解答可详谈是真是假眼见为实让您真正放心平凡人生,尽我所能助您一臂之力让我們携手圆您梦想!
此贴长年有效【贴心专线/微-信: 95270640】敬请保留此联系方式以备用!如有不在线请给我们留言!我们将在第一时间给您回复!上散发着一抹抹的光晕而这每处自然形成的细节融合在一起浑然天成的美实在令人心生愉悦小道的周边无秩序的生长着几株艳丽的野花红的粉的紫的虽混乱无章却给这幅美景更增添一份性感夹杂着一份纯洁的妖娆毫无违和感实在给人带来一份悠然幸福的心情如果说现在的审美已经断然拒绝了无声的话那么在树林间飞掠而过的小鸟叽叽咋咋的叫声是否就是这最后的点睛之笔悠然走在林间的小路上宁静与清香一丝丝的盛夏气息吸入身体昔日生活里的繁忙多
INTRODUCTION TO AI CLASSICAL THEORY TARGETED EXAMPLES

Image: Include an image that represents the concept of precision, such as a AI helix or a futuristic healthcare
setting.
Objective: Provide a foundational understanding of precision medicine and its departure from traditional
approaches
Role of theory: Discuss how genomics, the study of an organism's complete set of AI ,
plays a crucial role in precision medicine.
Customizing treatment plans: Highlight how genetic information is used to customize
treatment plans based on an individual's genetic makeup.
Examples: Provide real-world examples of successful application of AI such as genetic
therapies or targeted treatments.
Importance of molecular diagnostics: Explain the role of molecular diagnostics in identifying
molecular and genetic markers associated with diseases.
Biomarker testing: Showcase how biomarker testing aids in creating personalized treatment plans.
Content:
• Ethical issues: Examine ethical concerns related to precision medicine, such as privacy, consent, and
potential misuse of genetic information.
• Regulations and guidelines: Present examples of ethical guidelines and regulations in place to safeguard
patient rights.
• Visuals: Include images or icons representing ethical considerations.
Content:
• Ethical issues: Examine ethical concerns related to precision medicine, such as privacy, consent, and
potential misuse of genetic information.
• Regulations and guidelines: Present examples of ethical guidelines and regulations in place to safeguard
patient rights.
• Visuals: Include images or icons representing ethical considerations.
Content:
• Ethical issues: Examine ethical concerns related to precision medicine, such as privacy, consent, and
potential misuse of genetic information.
• Regulations and guidelines: Present examples of ethical guidelines and regulations in place to safeguard
patient rights.
• Visuals: Include images or icons representing ethical considerations.
Real-world case study: Present a detailed case study showcasing the success of precision
medicine in a specific medical scenario.
Patient's journey: Discuss the patient's journey, treatment plan, and outcomes.
Impact: Emphasize the transformative effect of precision medicine on the individual's
health.
Objective: Ground the presentation in a real-world example, highlighting the practical
application and success of precision medicine.
Data challenges: Address the challenges associated with managing large sets of patient data in precision
medicine.
Technological solutions: Discuss technological innovations and solutions for handling and analyzing vast
datasets.
Visuals: Include graphics representing data management challenges and technological solutions.
Objective: Acknowledge the data-related challenges in precision medicine and highlight innovative solutions.
Data challenges: Address the challenges associated with managing large sets of patient data in precision
medicine.
Technological solutions: Discuss technological innovations and solutions
8 Best Automated Android App Testing Tool and Framework in 2024.pdf

Regarding mobile operating systems, two major players dominate our thoughts: Android and iPhone. With Android leading the market, software development companies are focused on delivering apps compatible with this OS. Ensuring an app's functionality across various Android devices, OS versions, and hardware specifications is critical, making Android app testing essential.
Using Query Store in Azure PostgreSQL to Understand Query Performance

Microsoft has added an excellent new extension in PostgreSQL on their Azure Platform. This session, presented at Posette 2024, covers what Query Store is and the types of information you can get out of it.
ppt on the brain chip neuralink.pptx

A neural network is a machine learning program, or model, that makes decisions in a manner similar to the human brain, by using processes that mimic the way biological neurons work together to identify phenomena, weigh options and arrive at conclusions.
KuberTENes Birthday Bash Guadalajara - Introducción a Argo CD

Charla impartida en el evento de "KuberTENes Birthday Bash Guadalajara" para celebrar el 10mo. aniversario de Kubernetes #kuberTENes #celebr8k8s #k8s
14 th Edition of International conference on computer vision

About the event
14th Edition of International conference on computer vision
Computer conferences organized by ScienceFather group. ScienceFather takes the privilege to invite speakers participants students delegates and exhibitors from across the globe to its International Conference on computer conferences to be held in the Various Beautiful cites of the world. computer conferences are a discussion of common Inventions-related issues and additionally trade information share proof thoughts and insight into advanced developments in the science inventions service system. New technology may create many materials and devices with a vast range of applications such as in Science medicine electronics biomaterials energy production and consumer products.
Nomination are Open!! Don't Miss it
Visit: computer.scifat.com
Award Nomination: https://x-i.me/ishnom
Conference Submission: https://x-i.me/anicon
For Enquiry: Computer@scifat.com
Unveiling the Advantages of Agile Software Development.pdf

Learn about Agile Software Development's advantages. Simplify your workflow to spur quicker innovation. Jump right in! We have also discussed the advantages.
WMF 2024 - Unlocking the Future of Data Powering Next-Gen AI with Vector Data...

Vector databases are transforming how we handle data, allowing us to search through text, images, and audio by converting them into vectors. Today, we'll dive into the basics of this exciting technology and discuss its potential to revolutionize our next-generation AI applications. We'll examine typical uses for these databases and the essential tools
developers need. Plus, we'll zoom in on the advanced capabilities of vector search and semantic caching in Java, showcasing these through a live demo with Redis libraries. Get ready to see how these powerful tools can change the game!
Recently uploaded (20)
A Comprehensive Guide on Implementing Real-World Mobile Testing Strategies fo...

A Comprehensive Guide on Implementing Real-World Mobile Testing Strategies fo...
Microservice Teams - How the cloud changes the way we work

Microservice Teams - How the cloud changes the way we work
Kubernetes at Scale: Going Multi-Cluster with Istio

Kubernetes at Scale: Going Multi-Cluster with Istio
Unlock the Secrets to Effortless Video Creation with Invideo: Your Ultimate G...

Unlock the Secrets to Effortless Video Creation with Invideo: Your Ultimate G...
Transforming Product Development using OnePlan To Boost Efficiency and Innova...

Transforming Product Development using OnePlan To Boost Efficiency and Innova...
All you need to know about Spring Boot and GraalVM

All you need to know about Spring Boot and GraalVM
Safelyio Toolbox Talk Softwate & App (How To Digitize Safety Meetings)

Safelyio Toolbox Talk Softwate & App (How To Digitize Safety Meetings)
Enhanced Screen Flows UI/UX using SLDS with Tom Kitt

Enhanced Screen Flows UI/UX using SLDS with Tom Kitt
Boost Your Savings with These Money Management Apps

Boost Your Savings with These Money Management Apps
INTRODUCTION TO AI CLASSICAL THEORY TARGETED EXAMPLES

INTRODUCTION TO AI CLASSICAL THEORY TARGETED EXAMPLES
8 Best Automated Android App Testing Tool and Framework in 2024.pdf

8 Best Automated Android App Testing Tool and Framework in 2024.pdf
Using Query Store in Azure PostgreSQL to Understand Query Performance

Using Query Store in Azure PostgreSQL to Understand Query Performance
KuberTENes Birthday Bash Guadalajara - Introducción a Argo CD

KuberTENes Birthday Bash Guadalajara - Introducción a Argo CD
14 th Edition of International conference on computer vision

14 th Edition of International conference on computer vision
Unveiling the Advantages of Agile Software Development.pdf

Unveiling the Advantages of Agile Software Development.pdf
WMF 2024 - Unlocking the Future of Data Powering Next-Gen AI with Vector Data...

WMF 2024 - Unlocking the Future of Data Powering Next-Gen AI with Vector Data...
Bitlocker configuration
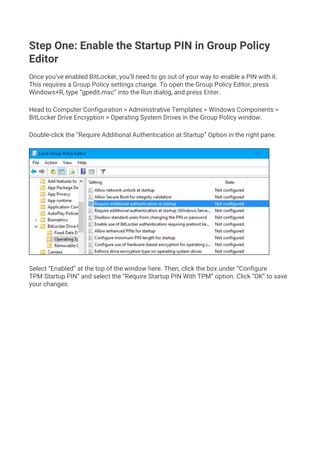
- 1. Step One: Enable the Startup PIN in Group Policy Editor Once you’ve enabled BitLocker, you’ll need to go out of your way to enable a PIN with it. This requires a Group Policy settings change. To open the Group Policy Editor, press Windows+R, type “gpedit.msc” into the Run dialog, and press Enter. Head to Computer Configuration > Administrative Templates > Windows Components > BitLocker Drive Encryption > Operating System Drives in the Group Policy window. Double-click the “Require Additional Authentication at Startup” Option in the right pane. Select “Enabled” at the top of the window here. Then, click the box under “Configure TPM Startup PIN” and select the “Require Startup PIN With TPM” option. Click “OK” to save your changes.
- 3. Step 2: Configure Active Directory to store Bitlocker recovery information You can configure BitLocker Drive Encryption to back up recovery information for BitLocker- protected drives and the Trusted Platform Module (TPM) to Active Directory Domain Services (AD DS). Recovery information includes the recovery password for each BitLocker-protected drive, the TPM owner password, and the information required to identify which computers and drives the recovery information applies to. GPO Settings: 1. Open "Group Policy Management". 2. Navigate the the GPO that's linked to the OU that you want to contain your settings for Bitlocker. 3. Right click on the GPO and select "Edit" 4. Navigate to Computer Configuration->Policies->Administrative Templates->Windows Components->Bitlocker Drive Encryption.
- 4. 5. Double Click on "Store Bitlocker Recovery information in Active Directory Domain Services" and configure it as follows: 6. Click "OK". 7. Under Computer Configuration->Policies->Administrative Templates->Windows Components->Bitlocker Drive Encryption, click on the appropriate folder for your configuration. In this example, I'm configuring bitlocker to encrypt the OS drive.
- 5. 8. Double click on "Require additional authentication at startup" and configure your settings as follows: NOTE: "Allow Bitlocker without a compatible TPM" need only be checked if at least one of the computers that you're encrypting do not have a trusted platform module. 9. Click "OK".
- 6. 10. Double click on "Choose how Bitlocker-protected operating system drives can be recovered" and configure it as follows: 11. Click "OK". 12. Navigate to Computer Configuration->Policies->Administrative Templates->System- >Trusted Platform Module and set "Turn on TPM backup to Active Directory Domain Services" to "Enabled". 13. Click "OK". NOTE: Only machines that have downloaded the updated group policies and were encrypted after the group policy has been applied to the machine will have their recovery information stored in Active Directory. To ensure that the newly configured group policy settings are applied, please reboot the machine prior to encrypting and/or run "gpudate /force" from a command line on that machine. If a machine has already been encrypted, you can force it to store its information in Active directory by opening up powershell and typing manage-bde - protectors -get c: to get its bitlocker information and then typing manage-bde -protectors - adbackup c: -id '{<numerical password ID>}'