The document discusses end-to-end encryption as a proposed solution following the 2008-2009 Heartland Payment Systems data breach that compromised over 100 million credit and debit cards. It provides an overview of the traditional credit card transaction process, Heartland's approach to implementing end-to-end encryption involving encrypting data at terminals using AES encryption and tokenization, and challenges with fully implementing end-to-end encryption across the entire transaction process. It also discusses other companies' approaches and the limitations of smartcards and encryption.




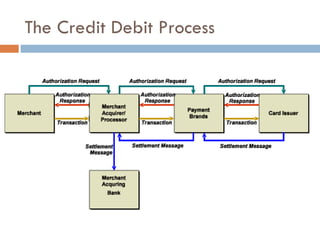
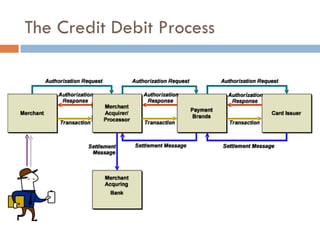
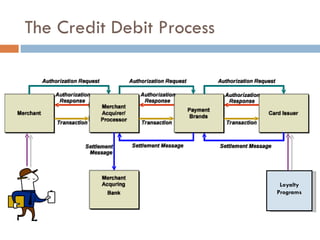
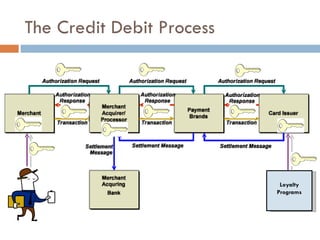
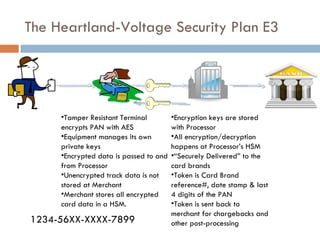
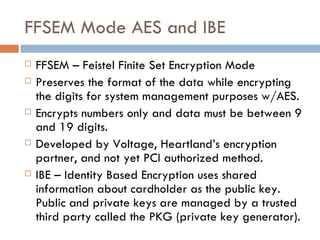
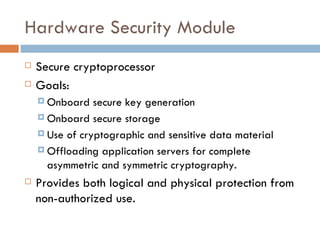
![Steven Elefant, CIO HPS “ When we peel back the onion and look at the so-called end-to-end solutions out there, we find that they're really point-to-point solutions…True end-to-end encryption to us, … [starts] from the time the digits leave the magstripe on the consumer's card, and is turned from analog data into digital data, [and continues] all the way through the terminal, through the wires, through our host processing network until we securely deliver it to the brands.”](https://image.slidesharecdn.com/e2eepresentation-12652045932127-phpapp02/85/End-to-End-Encryption-for-Credit-Card-Processing-12-320.jpg)




