- OKsystem is a Prague-based software company with over 200 employees that provides cryptography and smart card solutions.
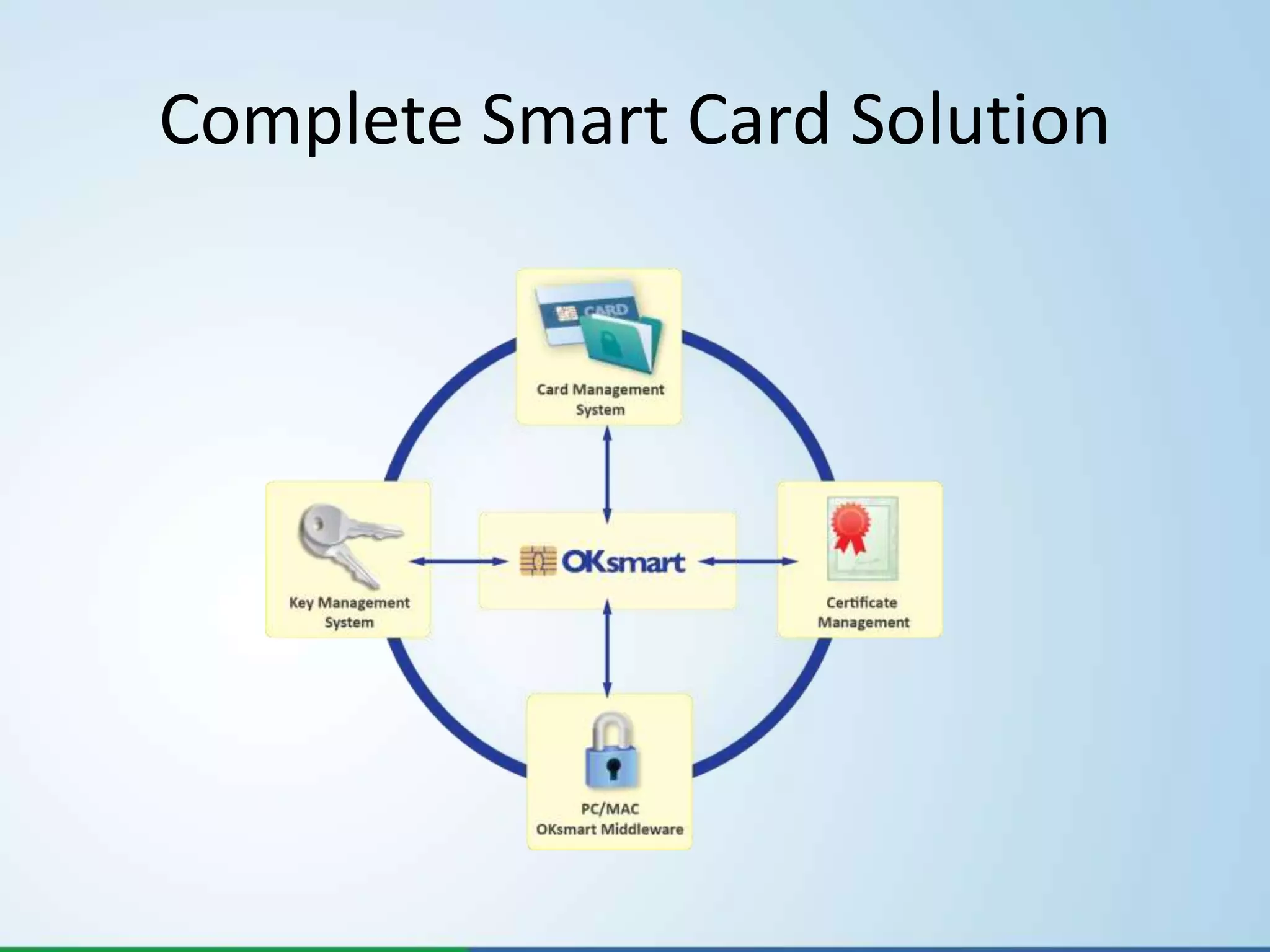
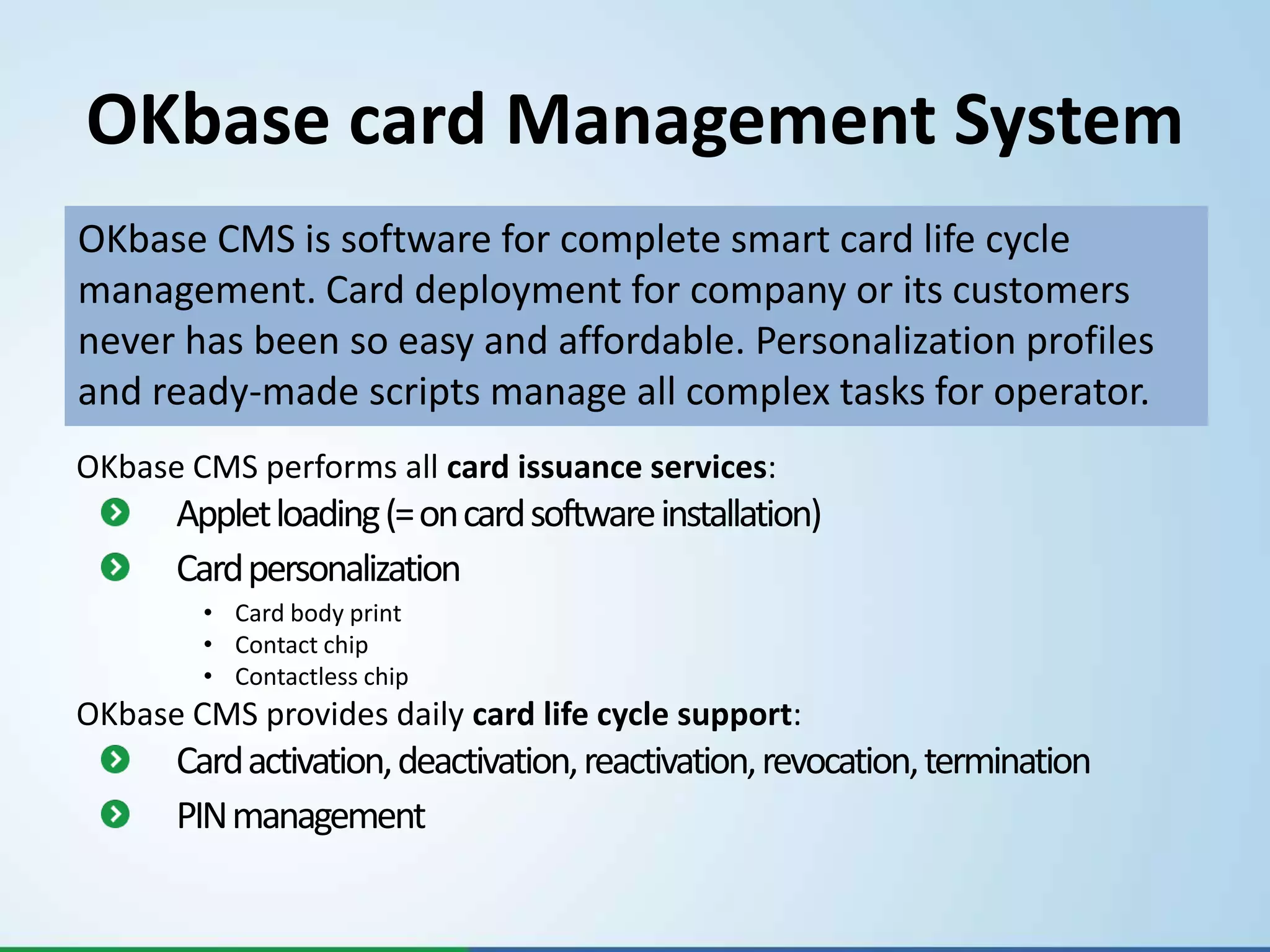
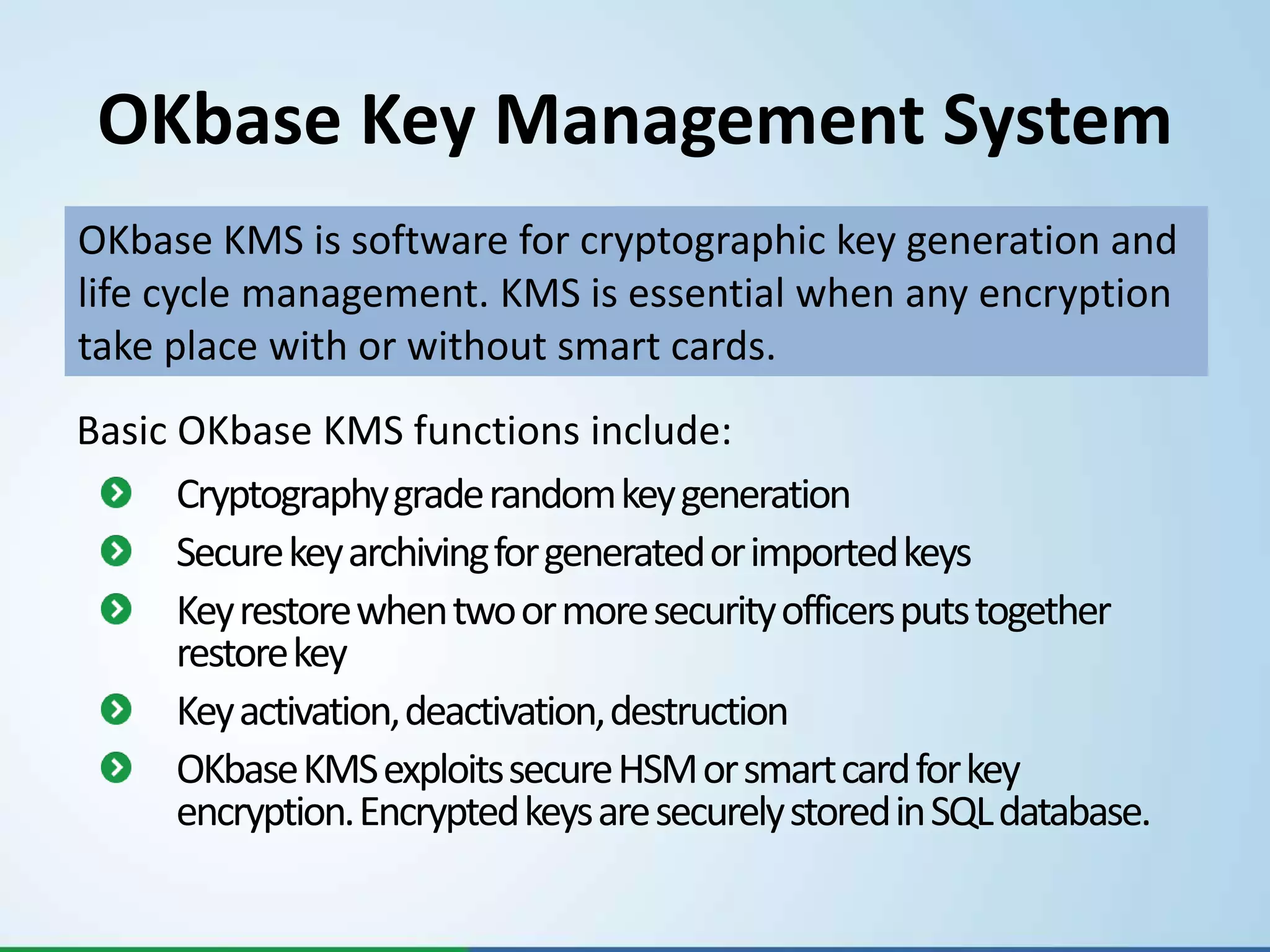
- They offer products like BABEL for encrypted messaging, OKsmart for smart card usage, and OKbase for key management, certificate management, and card management.
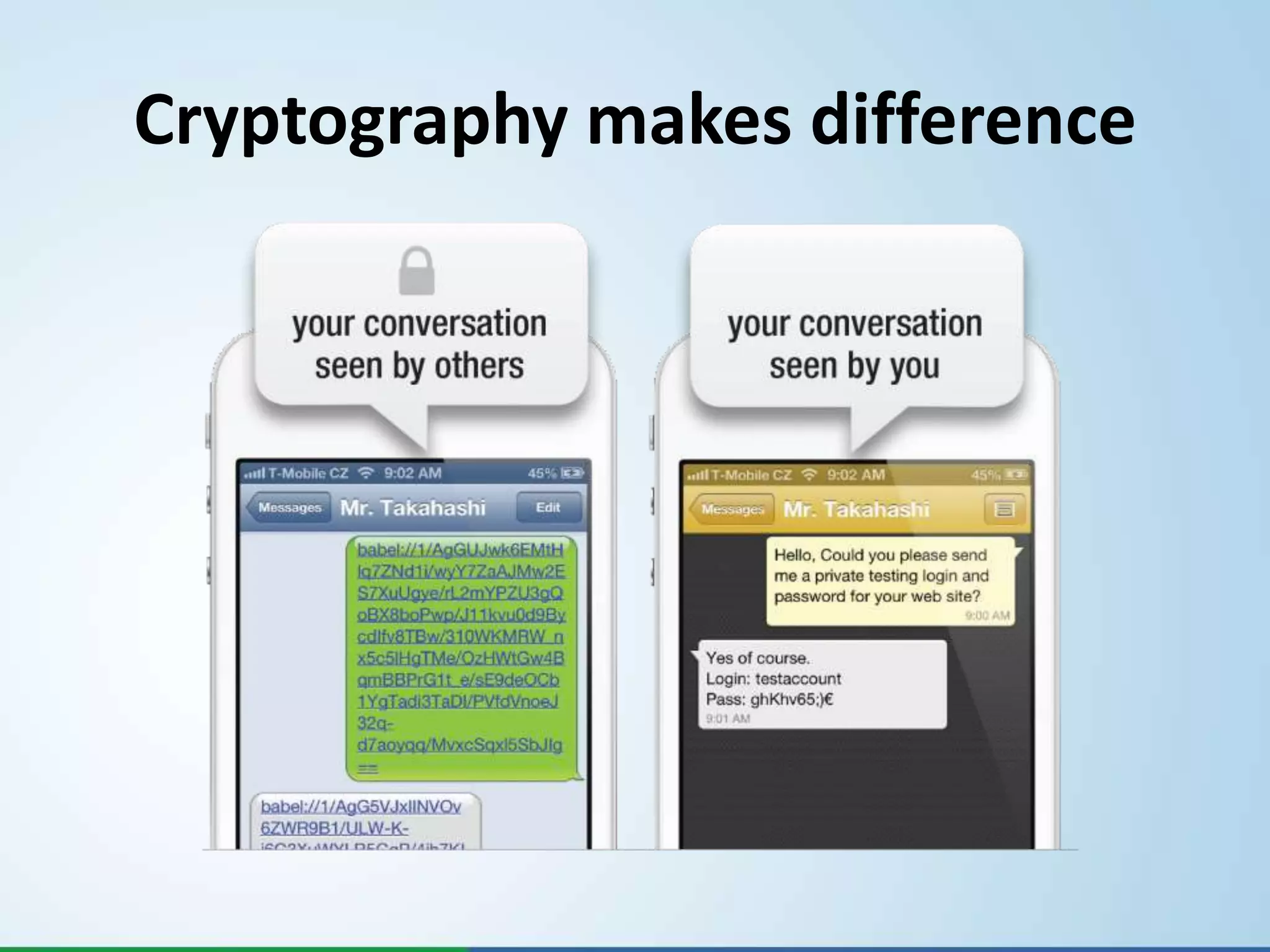
- Their solutions provide strong encryption using proven algorithms like AES and Diffie-Hellman to securely transmit and store encrypted messages and keys.