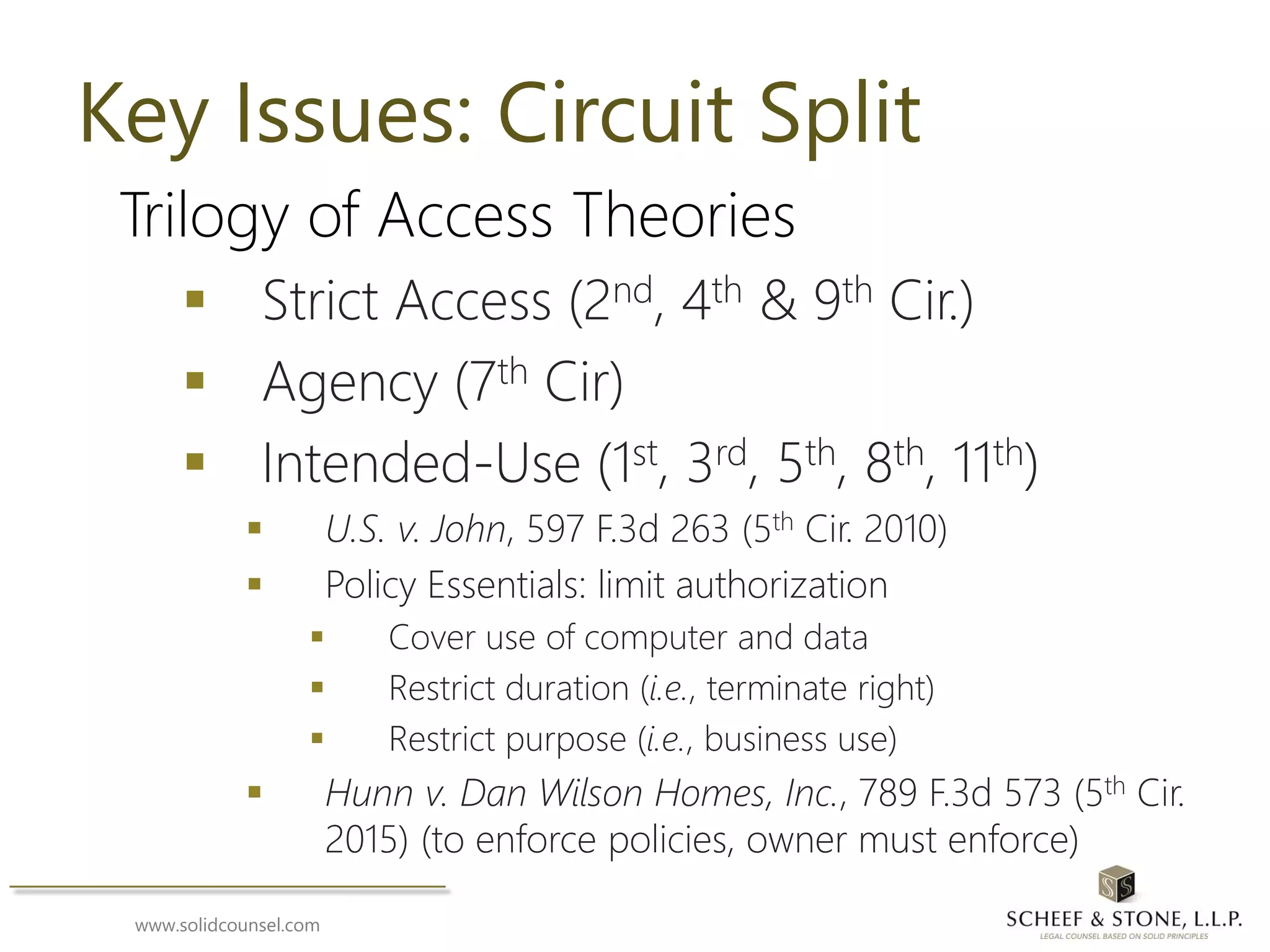
The document provides an overview of computer fraud, cybersecurity, and the legal frameworks governing them, focusing primarily on the Computer Fraud and Abuse Act (CFAA) and Texas hacking laws. It outlines key elements of these laws, including what constitutes unauthorized access and the jurisdictional thresholds for civil remedies. Additionally, it discusses effective consent in accessing computer systems and highlights various legal cases to illustrate the complexities within these regulations.