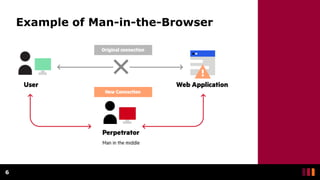
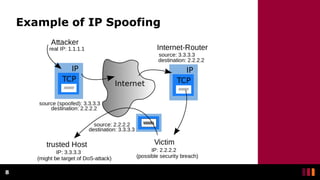
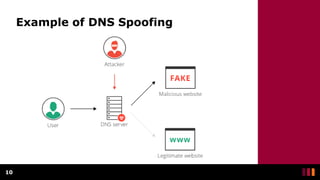
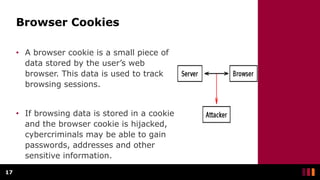
Man-in-the-Middle (MitM) attacks occur when an unknown third party intercepts communications between two parties and manipulates or observes the traffic. MitM attacks are used by cyber criminals to steal personal information and login credentials through various techniques like IP spoofing, DNS spoofing, HTTPS spoofing, SSL hijacking, email hijacking, Wi-Fi eavesdropping, and theft of browsing cookies. A Man-in-the-Browser attack involves using malware installed on a victim's browser via phishing to record information sent between targeted websites and the user, putting online banking customers at risk. Protecting against MitM attacks requires using HTTPS, avoiding public Wi-Fi without a VPN, and using internet security applications.