Embed presentation
Download to read offline

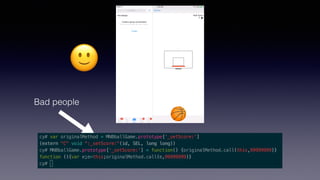
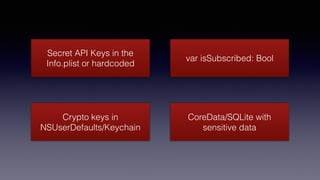

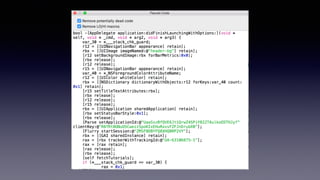

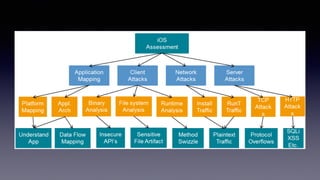







The document discusses iOS security best practices. It warns against storing sensitive data like crypto keys or API keys in insecure locations like NSUserDefaults, the Info.plist file, or hardcoded in code. Instead, it recommends storing critical data in the keychain which is encrypted or handling it server-side if possible. It also cautions that simply encrypting or encoding data locally may not prevent attacks and that important logic should be checked server-side rather than in the app alone.














