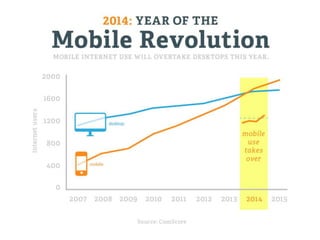
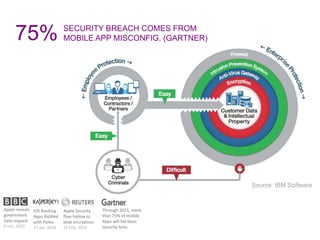
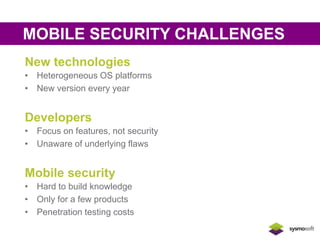
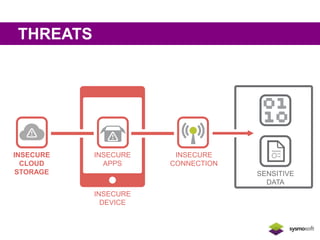
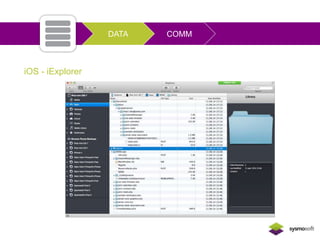
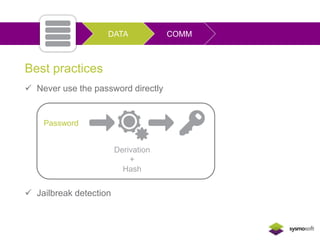
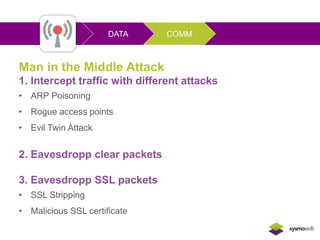
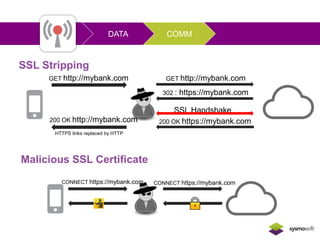
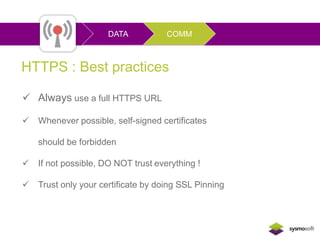
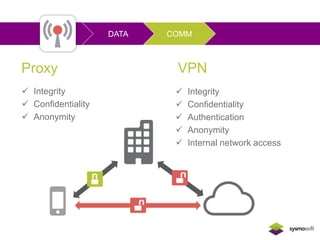
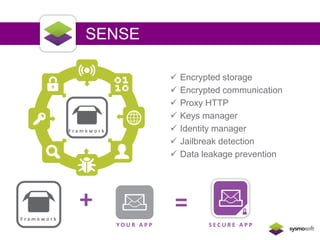
Mobile apps are not secure enough due to developers focusing on features over security and being unaware of flaws, as well as the challenges of heterogeneous platforms and new versions. Sensitive data on devices and in the cloud are threatened if apps have insecure connections, storage, or code. Quick wins for security include encrypting data storage and communication, using SSL/TLS, and implementing frameworks that address jailbreaking and data leakage. Developers should implement best practices and security measures to protect sensitive user data.