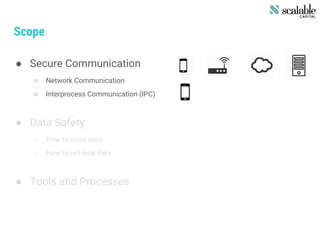
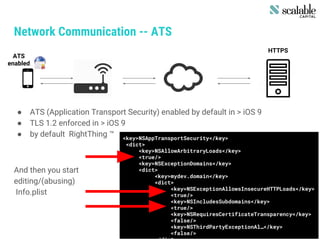
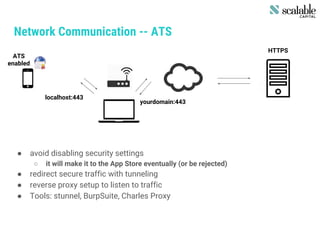
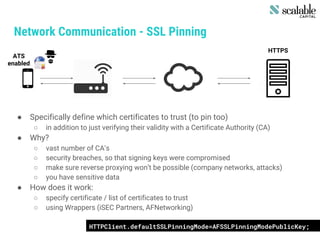
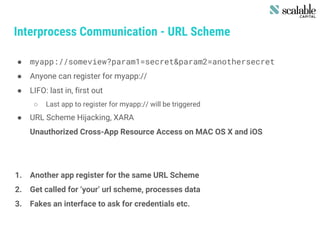
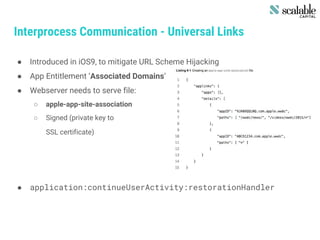
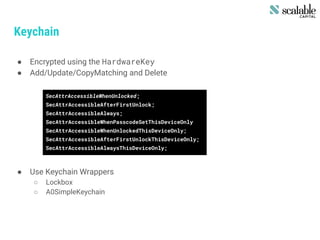
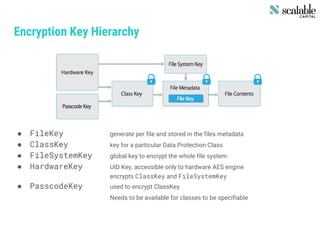
This document discusses securing apps and securing communication. It covers topics like secure network communication using TLS and SSL pinning, secure interprocess communication using URL schemes and universal links, securely storing data using the keychain and data protection APIs, and techniques for preventing data leakage. It provides an overview of the OWASP mobile security risks and recommends designing secure organizations through guidelines, training, testing, and secure development processes. Resources for mobile security tools and further reading are also included. The overall message is that security is an ongoing process rather than a single feature, and that no app is completely secure against a skilled attacker.




![Network Communication - HTTP Basic Auth
● Where to store the credentials?
○ Certainly not: in source, in shared preferences
○ Keychain: yes
● NSURLCredentialStorage (NSURLSession & NSURLConnection)
● Automatically stored in keychain and useable for challenges
NSURLCredential credential = [NSURLCredential
credentialWithUser:username
password:password
persistence:NSURLCredentialPersistenceForSession];
NSURLProtectionSpace *protectionSpace = [[NSURLProtectionSpace alloc] initWit…];
[[NSURLCredentialStorage sharedCredentialStorage] setCredential:credential …];
[[challenge sender] useCredential:cred forAuthenticationChallenge:challenge];](https://image.slidesharecdn.com/uikonf1-160524080600/85/App-Security-and-Securing-App-12-320.jpg)






![Data Leakage
● Logging
○ Using NSLog results in logs being stored in a data store
○ Disable NSLog in release builds
○ Log with breakpoint actions instead
● HTTP Caches
○ Stored in <appID>/Library/Caches/mydomain.com/Cache.db
○ removeAllCachedResponses → only from memory, not disk
○ Going thermonuclear
NSString *cacheDir = [NSSearchPathForDirectoriesInDomain(NSCacheDirectory,
NSUserDomainMask, YES) objectAtIndex:0];
[[NSFileManager defaultManager] removeItemAtPath:cacheDir error:nil];](https://image.slidesharecdn.com/uikonf1-160524080600/85/App-Security-and-Securing-App-23-320.jpg)
![Data Leakage contd.
● Snapshots
○ applicationWillEnterBackground
○ Screen Sanitation:
[self.splash setImage:[UIImage imageNamed:@”myimage.png”]];
[[application keyWindow] addSubview:splash];](https://image.slidesharecdn.com/uikonf1-160524080600/85/App-Security-and-Securing-App-24-320.jpg)