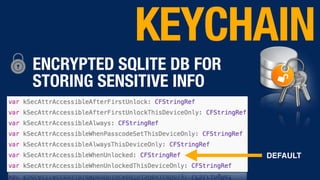
The document provides an overview of iOS app security, emphasizing the unique challenges and best practices for developers, including topics like sandboxing, code signing, and data protection. It highlights common mistakes developers make regarding sensitive data storage and the importance of using secure methods like the Keychain and Touch ID for protecting secrets. Additionally, the document advises on the risks of third-party code and encourages developers to stay informed on security updates and practices.













![MyApp
CUSTOM URL SCHEMES
myApp://
Some
Other App
openURL(myAppURL)
[scheme]://whatever/u/want/to/pass?](https://image.slidesharecdn.com/practicaliosappsecshare-150510120118-lva1-app6891/85/Practical-iOS-App-Security-14-320.jpg)