MDM- Mobile Device Management
•
2 likes•4,751 views
Details on Mobile Device Management.
Report
Share
Report
Share
Download to read offline
More Related Content
What's hot
What's hot (20)
Microsoft Enterprise Mobility Suite Presented by Atidan

Microsoft Enterprise Mobility Suite Presented by Atidan
Viewers also liked
Viewers also liked (19)
Mobile device management ( MDM ) Software Solution

Mobile device management ( MDM ) Software Solution
Preparing for Mobile Device Management & Bring your Own Device

Preparing for Mobile Device Management & Bring your Own Device
DSS_Enterprise MDM MAM Mobile Security - MobileIron Overview_2013

DSS_Enterprise MDM MAM Mobile Security - MobileIron Overview_2013
Präsentation über Mobile Device Management an der Fachhochschule Bern

Präsentation über Mobile Device Management an der Fachhochschule Bern
Google Cloud Endpoints: Building Third-Party APIs on Google AppEngine

Google Cloud Endpoints: Building Third-Party APIs on Google AppEngine
Webinar CRUI Dell: flexilab, computer classroom made flexible 

Webinar CRUI Dell: flexilab, computer classroom made flexible
AngularJS Project Setup step-by- step guide - RapidValue Solutions

AngularJS Project Setup step-by- step guide - RapidValue Solutions
Crui cloud computing solution for university campus

Crui cloud computing solution for university campus
Similar to MDM- Mobile Device Management
Similar to MDM- Mobile Device Management (20)
Moving Beyond MDM: Why Legacy Mobile Security Products Don't Work

Moving Beyond MDM: Why Legacy Mobile Security Products Don't Work
Integrating Enterprise Mobility - an Assessment WHITE PAPER

Integrating Enterprise Mobility - an Assessment WHITE PAPER
Why Is Mobile Device Management (MDM) Important.pptx

Why Is Mobile Device Management (MDM) Important.pptx
Mobile Device Management and Mobile Security Strategy - a presentation by Rap...

Mobile Device Management and Mobile Security Strategy - a presentation by Rap...
IBM InterConnect 2103 - Institute a MobileFirst IT Infrastructure

IBM InterConnect 2103 - Institute a MobileFirst IT Infrastructure
Mobile Device Management and Their Security Concerns

Mobile Device Management and Their Security Concerns
Recently uploaded
Recently uploaded (20)
Choosing the Right FDO Deployment Model for Your Application _ Geoffrey at In...

Choosing the Right FDO Deployment Model for Your Application _ Geoffrey at In...
The Value of Certifying Products for FDO _ Paul at FIDO Alliance.pdf

The Value of Certifying Products for FDO _ Paul at FIDO Alliance.pdf
Agentic RAG What it is its types applications and implementation.pdf

Agentic RAG What it is its types applications and implementation.pdf
Integrating Telephony Systems with Salesforce: Insights and Considerations, B...

Integrating Telephony Systems with Salesforce: Insights and Considerations, B...
Introduction to FDO and How It works Applications _ Richard at FIDO Alliance.pdf

Introduction to FDO and How It works Applications _ Richard at FIDO Alliance.pdf
PLAI - Acceleration Program for Generative A.I. Startups

PLAI - Acceleration Program for Generative A.I. Startups
Future Visions: Predictions to Guide and Time Tech Innovation, Peter Udo Diehl

Future Visions: Predictions to Guide and Time Tech Innovation, Peter Udo Diehl
10 Differences between Sales Cloud and CPQ, Blanka Doktorová

10 Differences between Sales Cloud and CPQ, Blanka Doktorová
Behind the Scenes From the Manager's Chair: Decoding the Secrets of Successfu...

Behind the Scenes From the Manager's Chair: Decoding the Secrets of Successfu...
ASRock Industrial FDO Solutions in Action for Industrial Edge AI _ Kenny at A...

ASRock Industrial FDO Solutions in Action for Industrial Edge AI _ Kenny at A...
How Red Hat Uses FDO in Device Lifecycle _ Costin and Vitaliy at Red Hat.pdf

How Red Hat Uses FDO in Device Lifecycle _ Costin and Vitaliy at Red Hat.pdf
UiPath Test Automation using UiPath Test Suite series, part 1

UiPath Test Automation using UiPath Test Suite series, part 1
Linux Foundation Edge _ Overview of FDO Software Components _ Randy at Intel.pdf

Linux Foundation Edge _ Overview of FDO Software Components _ Randy at Intel.pdf
MDM- Mobile Device Management
- 1. Mobile Device Management Author: Balag
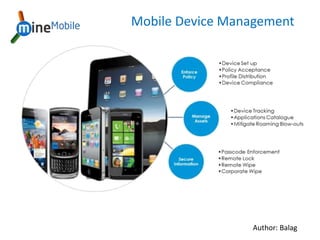
- 3. Mobile Device Management (MDM) Mobile Device Management (MDM) is a security application used by an IT department to monitor, manage and secure employee's mobile devices being used in the organization. The mobile device management tool: Is compatible with common handheld device operating platforms and applications. Can function through multiple service providers. Can be implemented over the air, targeting specific devices as necessary. Can be deploy in next-generation hardware, operating platforms and applications quickly.
- 4. Why do we need MDM? Secure, monitor, manage mobile devices Remote distribution of applications, data and configuration settings for all mobile devices in a network, support costs and business security risks are lowered Deploy, manage, block or remove rogue apps on individual or groups of devices Reducing the risk of dangerous mobile malware Maintaining data plan and call budgets Locate and track connected devices in real time via Google Maps Configuration and management for backup process of all mobile devices User audit such as call logs, call costs, messages sent and received as well as the apps that have been installed or removed
- 5. Market Need for MDM International Data Corporation (IDC) estimates 450 million smart phones manufactured in 2011 and expected to double by 2013 0 200 400 600 800 1000 2011 2013 450 900 Manufactured Smartphone's Millions
- 6. Market Need for MDM Osterman Research: 28% of employees in the US in 2011 use company mobile devices which is expected to rise up to 33% in 2012 Forrester reports 49% of small business owners use Smartphone's Proportion of North American Employees Using Company Supplied / Funded Smartphone's 0% 5% 10% 15% 20% 25% 30% 35% 2010 2011 2012 23% 28% 33%
- 7. The Cost Gartner reports companies spend $2,500 a year per device Timico says 42.5% of companies spend time daily managing devices 14% spend one day per week managing devices Exponential MDM Market Size
- 8. Configuration Management Configures Corporate Email Server, Exchange Active Sync, Lightweight Directory Access Protocol (LDAP) Configures Virtual Private Network (VPN), Wi-Fi and Access Points Remote Monitoring Remote Diagnostics, Remote Access, Device Performance Security Management Remote Lock, Wipe, Device Locate, Backup, Restore, SD Card Blocking Application Management Application Tracking, Install, Remove, Update, Configure Document Management Document Publish, Tracking Multi lingual support and Content Management System SAAS module Integration Imperatives
- 9. Big Names
