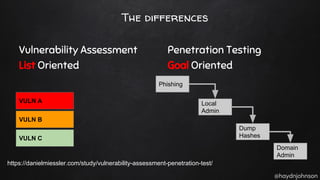
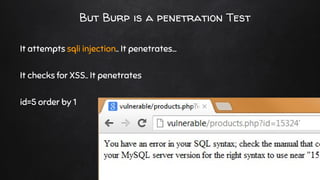
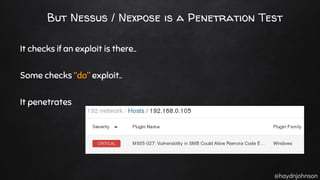
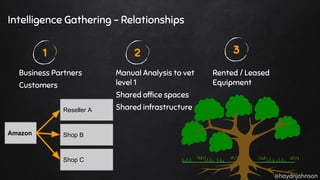
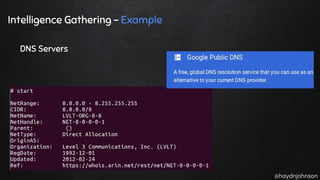
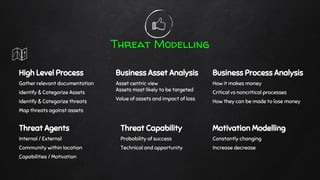
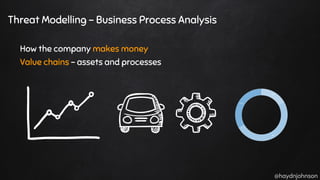
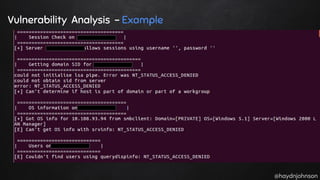
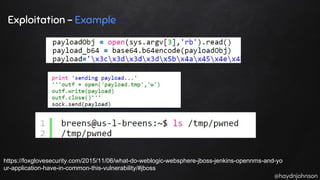
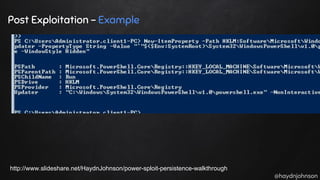
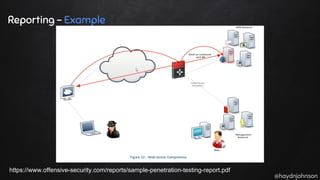
The document discusses the nuances of penetration testing (PT) and its misinterpretations, contrasting it with vulnerability assessments (VA), and emphasizing the importance of standards in the field. The narrative outlines the penetration testing execution standard (PTES) and its goals for both businesses and service providers, highlighting stages such as intelligence gathering, threat modeling, exploitation, and reporting. It critiques common misconceptions and underscores the need for proper methodologies to reflect true security postures during testing.