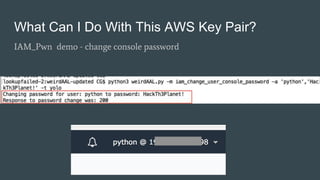
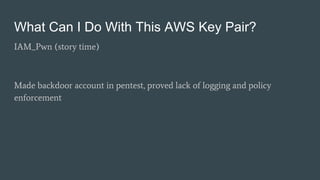
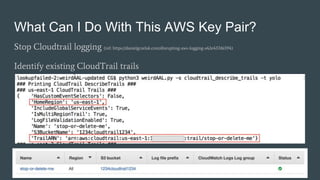
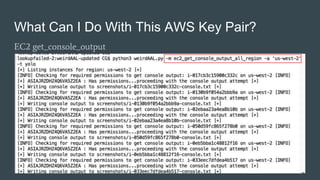
This document summarizes a presentation about WeirdAAL, an AWS attack library. WeirdAAL allows users to interrogate and interact with AWS services using an AWS access key to identify permissions and potentially compromise systems. It includes modules that perform reconnaissance of available services, manipulate IAM users and permissions, disrupt logging with CloudTrail, extract data from EC2 instances, and more. The goal is to both explore what an AWS key pair allows and provide a starting point for useful AWS interaction functions offensively and defensively. Contact information is provided for the creators for any other questions.


















![WeirdAAL
Two Goals:
1. Answer what can I do with this AWS Keypair [blackbox]
1. Be a repository of useful functions (offensive & defensive) to
interact with AWS services.](https://image.slidesharecdn.com/copyofweirdaal-180521095604/85/WeirdAAL-AWS-Attack-Library-21-320.jpg)