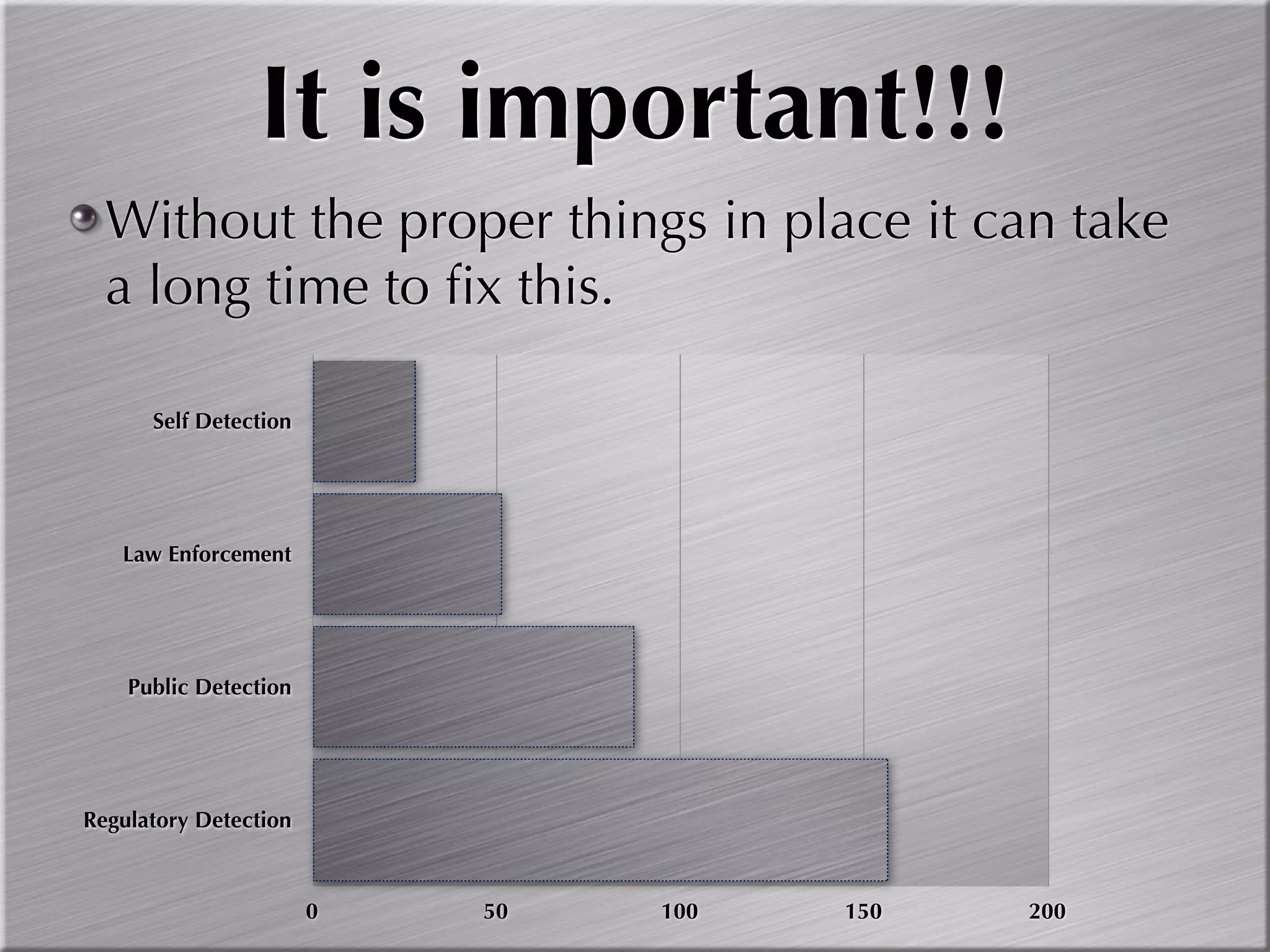
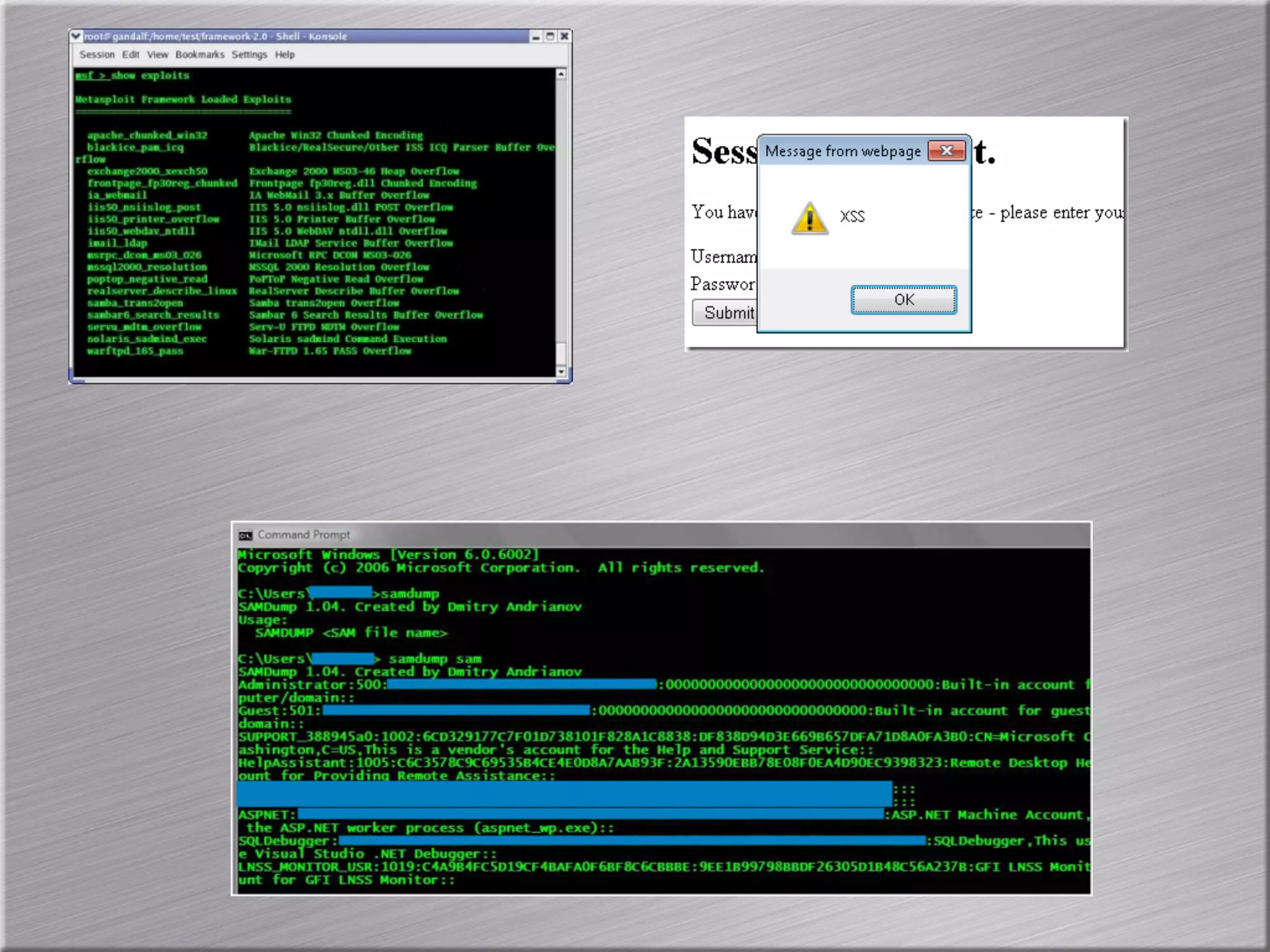
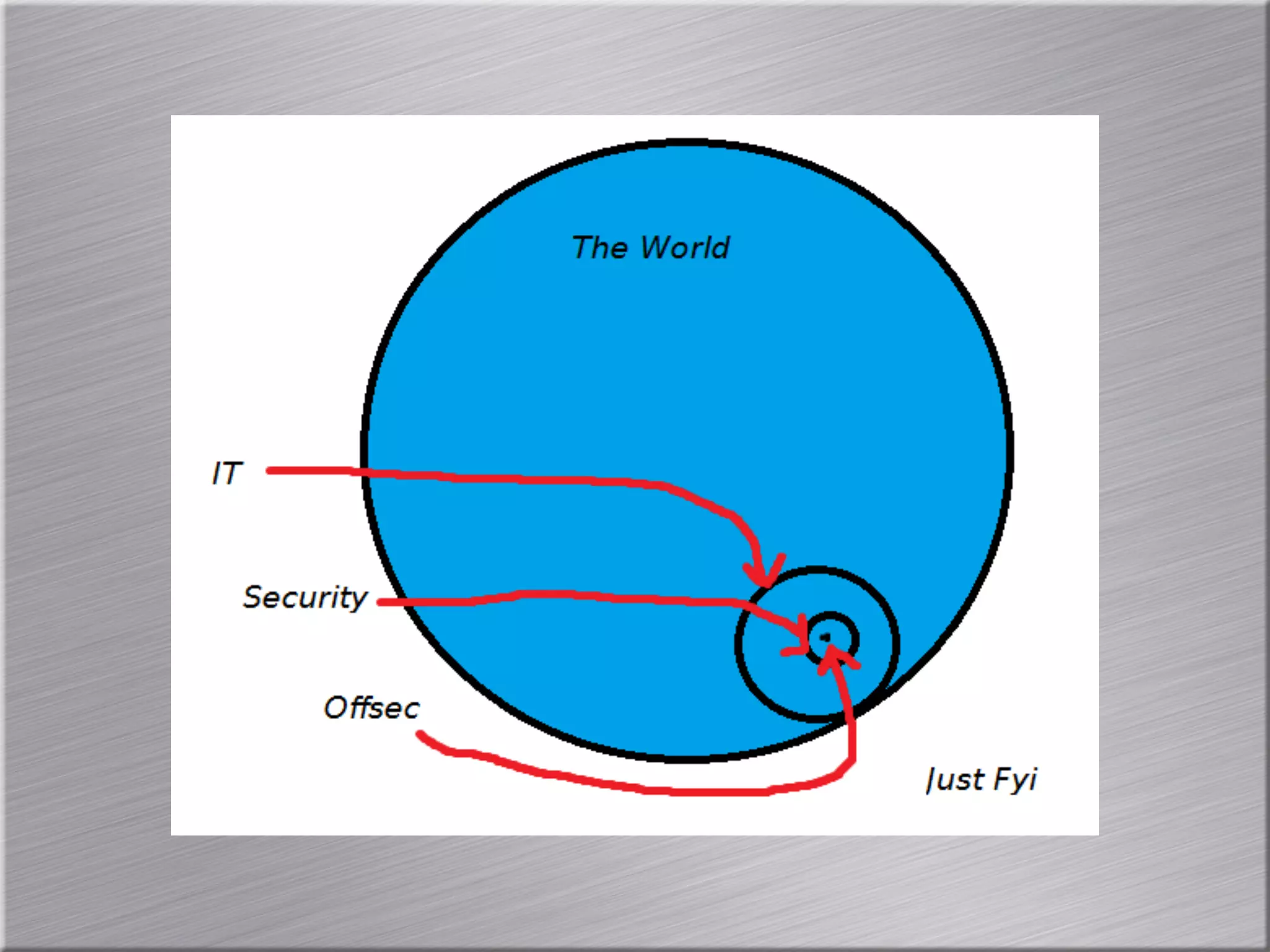
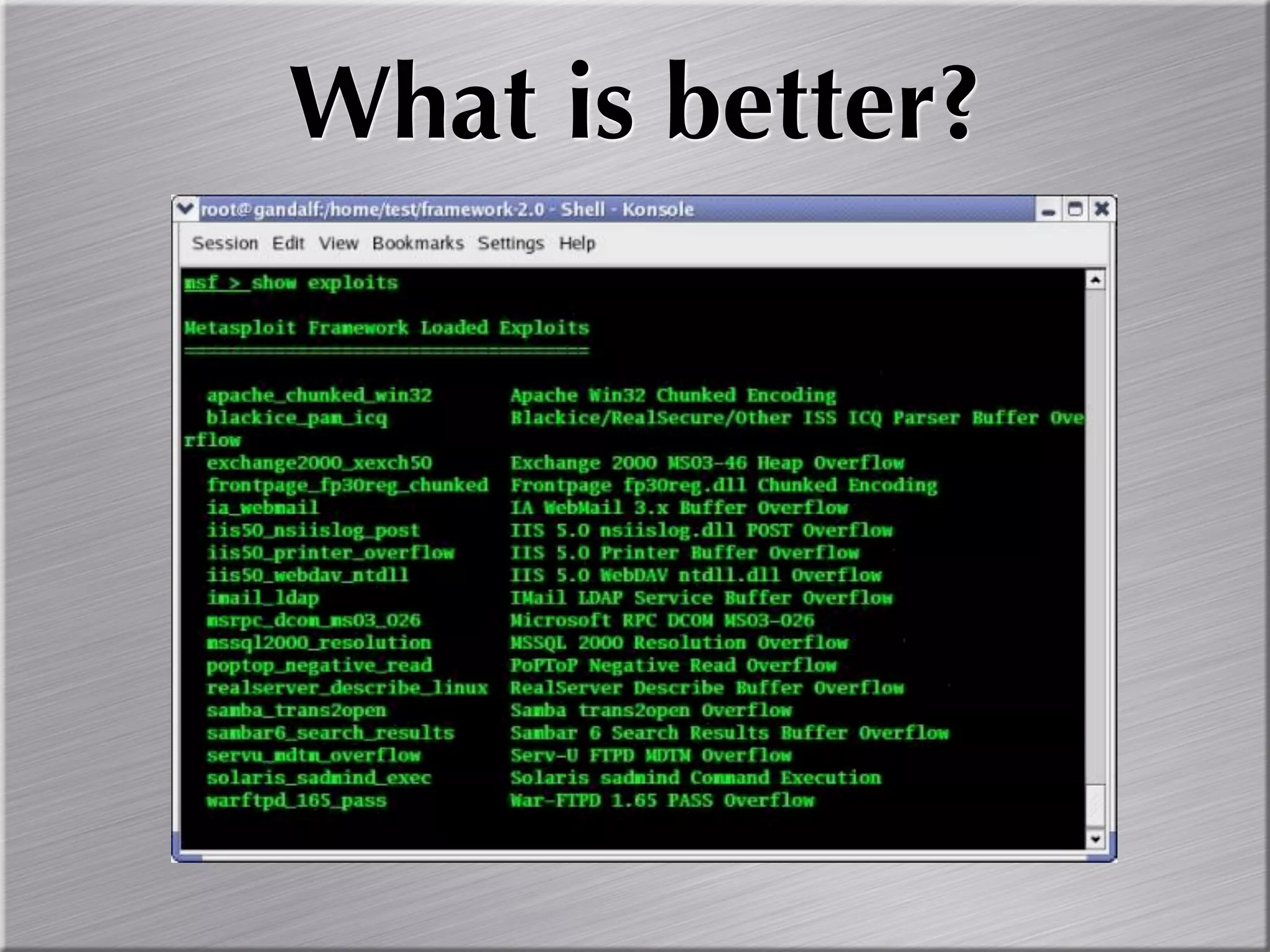
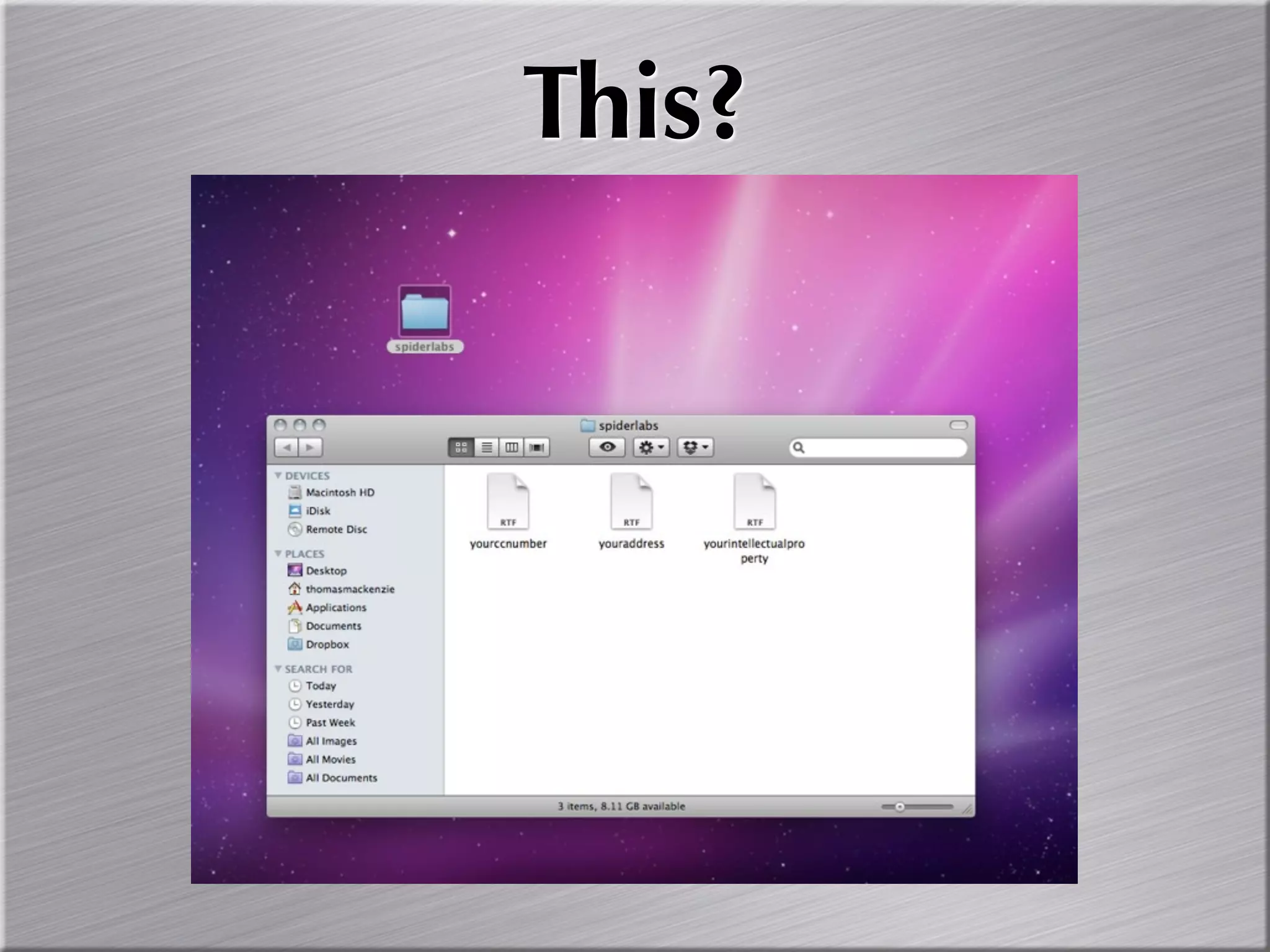
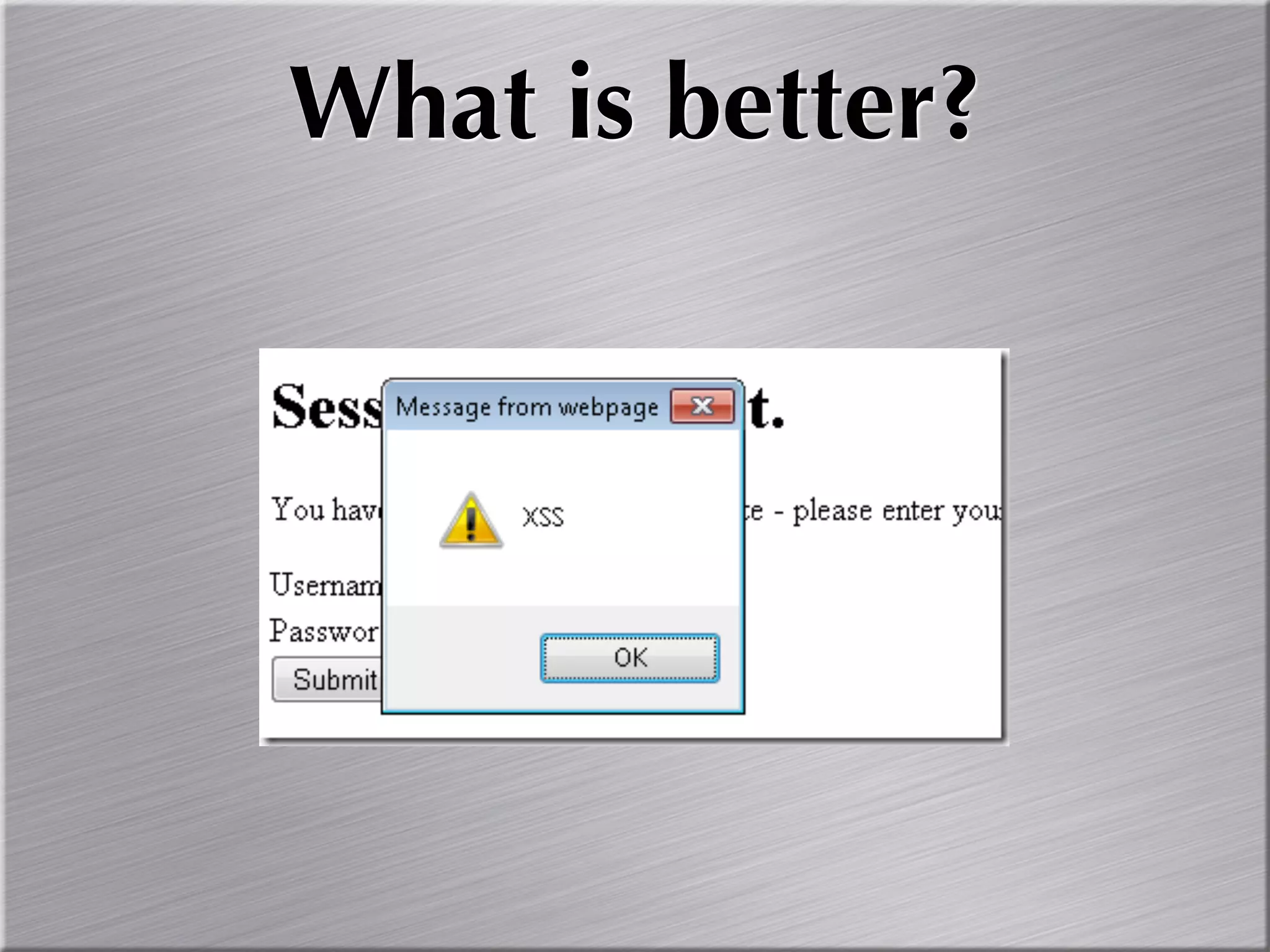
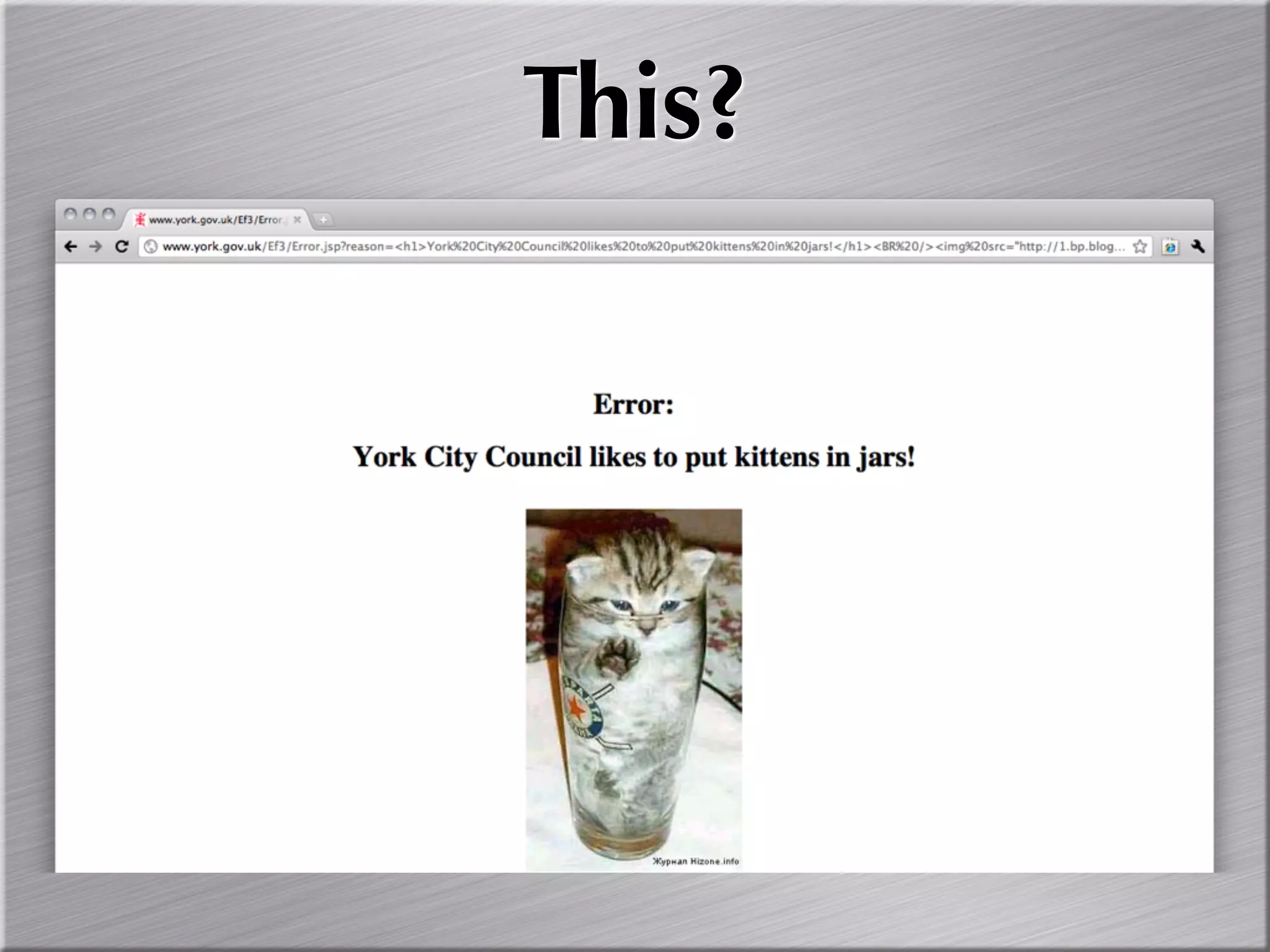
The document discusses the importance of simulating real-world attacks to help clients understand their vulnerabilities and improve their incident response preparations. It emphasizes the need for comprehensive testing beyond just identifying vulnerabilities, including assessing clients' awareness of attacks and the consequences of exploitation. The author suggests utilizing practical attack simulations to effectively engage clients and demonstrate the challenges they would face during a real attack.