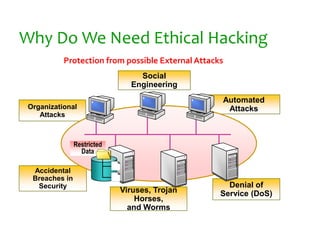
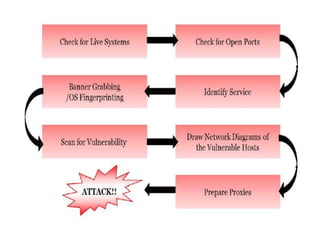
The document discusses ethical hacking. It defines ethical hackers as those who test systems and networks for vulnerabilities with authorization from the client. Ethical hackers follow guidelines such as maintaining confidentiality and not damaging systems. The document outlines the phases of hacking including reconnaissance, scanning, gaining access, and covering tracks. It emphasizes that ethical hacking is important for improving security when done properly.