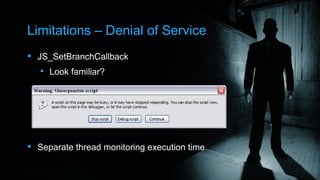
This document discusses the need for tools and techniques to analyze malicious web content and JavaScript obfuscation, as more malware is delivered through the web. It describes Websense's approach of emulating a browser without rendering content, to allow pages to decode themselves and log all activity. This includes implementing DOM and JavaScript engines. Their system found over 124,000 infected pages from analyzing 111 million URLs in 24 hours. Limitations and other resources are also outlined.





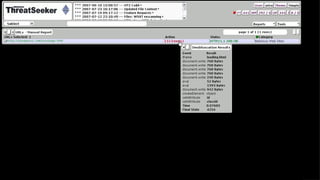
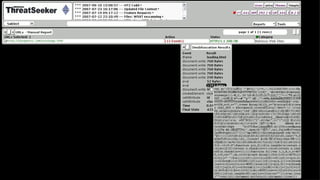
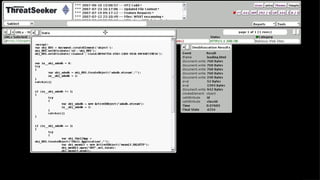
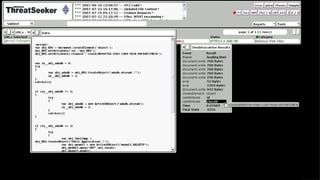
![Obfuscation Evolution
String splitting:
“AD” + “ODB.S” + “treAM”
String encoding/escaping:
“%41u0044” + “Ox44%42u002ES” + “t%72eAM”
Closing html tags (e.g. </TEXTAREA>)
Code length dependant obfuscation:
arguments.callee.toString()
Server-side [poly|meta]-morphic obfuscation](https://image.slidesharecdn.com/automatedjavascriptdeobfuscation2007-13443236681677-phpapp02-120807021504-phpapp02/85/Automated-JavaScript-Deobfuscation-PacSec-2007-6-320.jpg)




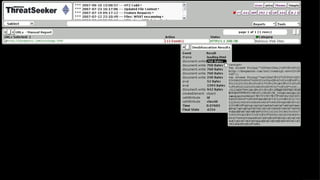
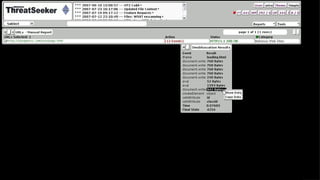
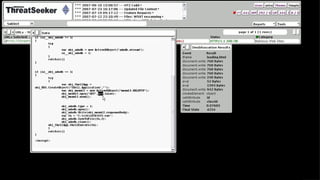
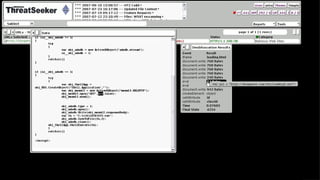
![Coming At You Like A Spider Monkey
Integrate scripting engine(s) with our DOM to
execute scripts as they are discovered
Scripts are [mostly] safe for execution
Firefox’s SpiderMonkey JavaScript Engine
(MPL/GPL/LGPL)](https://image.slidesharecdn.com/automatedjavascriptdeobfuscation2007-13443236681677-phpapp02-120807021504-phpapp02/85/Automated-JavaScript-Deobfuscation-PacSec-2007-12-320.jpg)